A Hacker’s Guide to Subdomain Enumeration

Reading Time: 5 Minutes
updated 12/05/2024
What is subdomain enumeration?
So, what is subdomain enumeration, and what is its purpose of it, from a hacker’s perspective?
There are different ways of enumerating or discovering subdomains for a given domain. As we know, enumeration is the key when it comes to hacking; enumerating subdomains leads to discovering many untouched surfaces having vulnerabilities.
Subdomain enumeration is the process of finding subdomains of a particular Domain Name. From a hacker’s perspective, understanding how to get more hidden subdomains a company has, will significantly differ and get more coverage than others, especially when you are performing Bug Bounty or Penetration Testing. It is about the techniques used and the mindset of the Red Team when performing this first step.
From a hacker’s perspective:
The hostname(s) of resources can provide valuable information to narrow the scope of an attacker’s task by providing information about available machines and resources. The underlying space of network (IP) addresses is sparsely populated (and IP: port combinations even more so), so narrowing down the addresses at which the organization hosts machines significantly reduces the preparatory work necessary to locate machines, map the topology, and launch an attack.
For example, the presence of the name ssh.company.com in the DNS provides hints of machines that probably host an SSH daemon. In the first instance, it is reasonable to suppose that the daemon runs on its default port, significantly reducing attack overhead and advancing to the stage of probing for vulnerabilities. By contrast, scanning the large IP ranges of an organization is slower, more time-consuming, and more likely to trigger early alerts in firewalls and IDS devices of port scan attempts.
So, there are 2 ways of performing subdomain enumeration, Passive and Active. Each technique has its downside and upside, so we will attempt to show you how to ultimately get the maximum results when you perform subdomain enumeration using some recommended tools.
After all, it’s not about the tools, it’s the technique you use, on top – that will elevate you more than others.
There are numerous methods for performing subdomain enumeration, but we will demonstrate the correct approach and thoroughly evaluate it. Subsequently, we will assess three tools that you could employ for subdomain enumeration, ultimately determining the most effective approach with proper techniques.
See Also: A Practical Guide to Hacking Techniques for finding Top Bugs.
The Bug Bounty Hunting Course
Prerequisites:
- API KEYS of Passive DNS source (PassiveTotal, Shodan, VirusTotal, Censys)
- A VPS (Virtual Private Server)
- VPN (Clean IP Address to Avoid IP Blacklisting)
- Amass, Sublist3r, and Assetfinder tools are designed to enumerate subdomains using OSINT.
- Domain validator (isup Checking alive hosts)
- SecLists or FuzzDB for subdomain Brute Force “/Discover/DNS”
- API KEYS of Passive DNS source.
Passive subdomain enumeration is a technique to query passive DNS datasets provided by sources (PassiveTotal, Shodan, VirusTotal, Censys) to obtain the subdomains of a particular target.
- A VPS (Virtual Private Server)
Using VPS is recommended to keep away from horrific net connection however additionally in case you acting subdomain enumeration can reveal a lot of domains which increases the bandwidth. Bandwidth is the amount of data that can get moved from the server to the receiver. If your ISP plan has restricted bandwidth feasible you can’t compete successfully results.
- VPN (Virtual Private Network)
It’s not required if you are using VPS but keep in mind that sometimes before you start to perform subdomain enumeration, you need to check your IP if has a bad reputation from previews scans. You can find more using intelligence search engines like ipqualityscore and mxtoolbox.
- Amass, Sublist3r, and Assetfinder tools are designed to enumerate subdomains using OSINT.
There are a lot of tools that can you perform passive DNS scans. Many of those perform only passive scans, but there are also active reconnaissance (subdomain Brute forcing) techniques that are proven beneficial.
- Domain validator (isup Checking alive hosts)
Is highly flexible and is made to work in different situations. It can parse output files from multiple tools collectively. It removes similar subdomains and false positives and provides you only subdomains that are alive. This can help you to save time for other things you need to do.
To do this by typing: isup.sh <target-list>
- SecLists or FuzzDB for subdomain Brute Force “/Discover/DNS”
An efficient Brute-Forcing attack typically involves a barrage of requests, and guesses to gain access or reveal information that may be otherwise hidden.
There are obvious challenges to brute-forcing, effective recon which helps you discover new attack surfaces, and new subdomains. The wordlist technique is less effective in the case of domains that don’t use common or popular subdomain extensions, so for that reason, you need to keep updating those wordlists, although from your experience as a hacker you can create your custom wordlist to detect the maximum result. We need to have a strong and potential script that will automate work and return a list of subdomains.
AssetFinder:
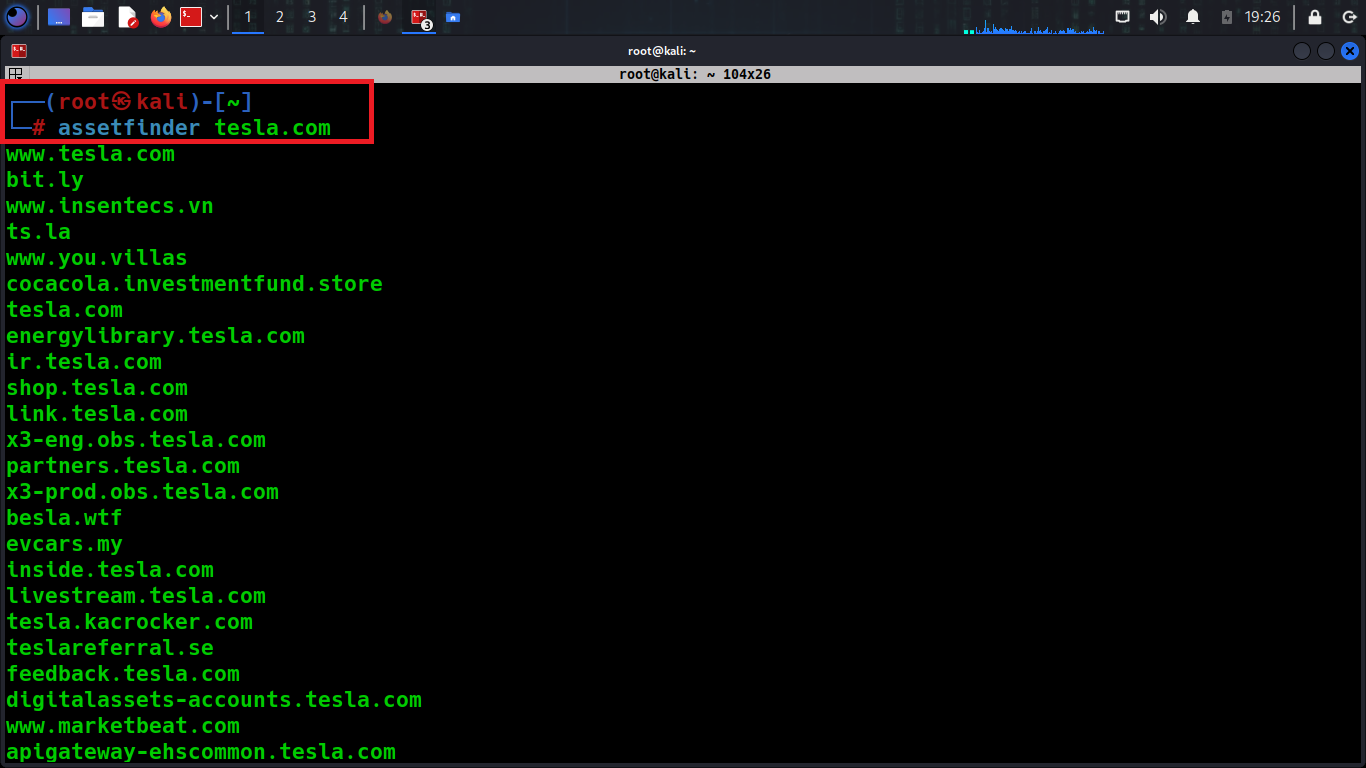
Is a simple and smart script for information gathering for subdomains, and leverages many publicly available data sources to help you during your asset discovery process. It does so by building a list of subdomains related to a domain, sourced from popular data sources such as crt.sh, certspotter, HackerTarget, ThreatCrowd, Wayback Machine, and more, all of which give AssetFinder multiple data sources to fetch data from.
./assetfinder <domain>
Sublist3r:
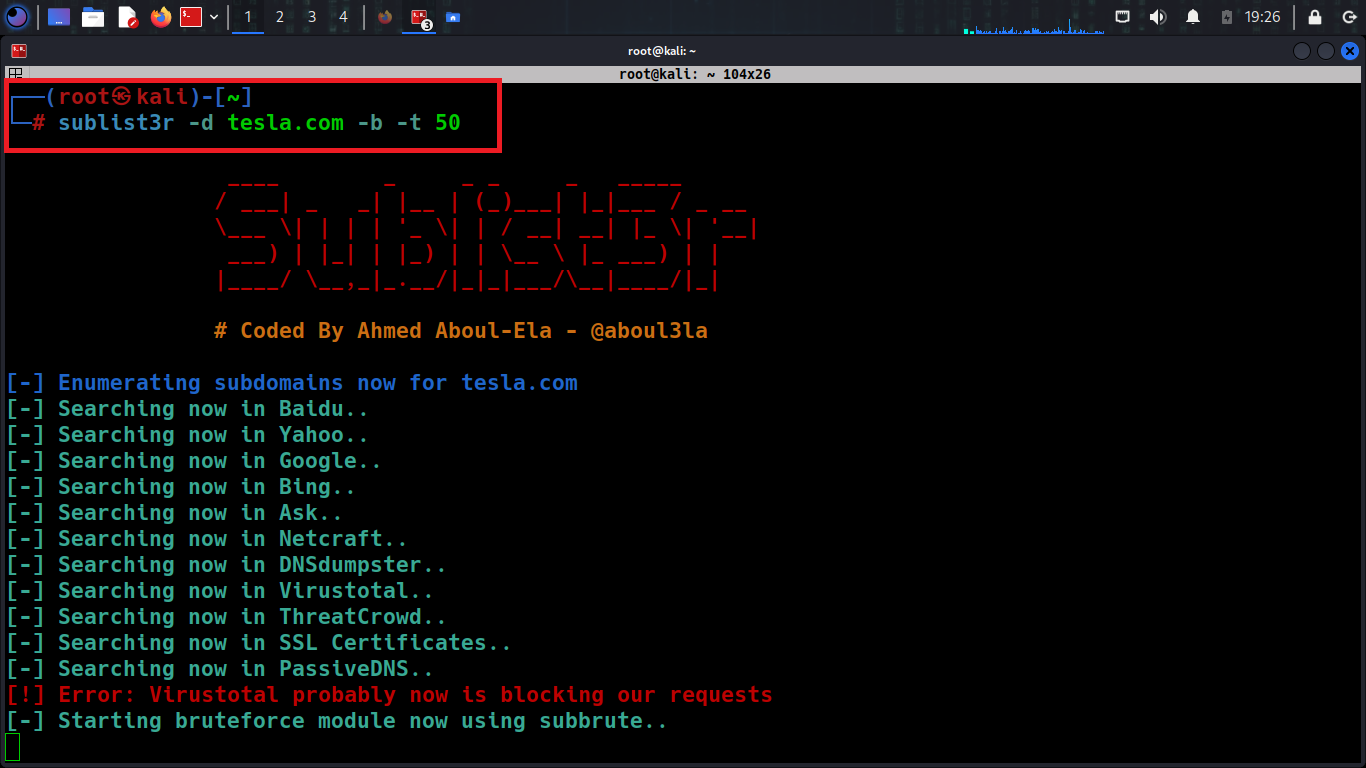
Is a tool designed to enumerate subdomains of websites using OSINT techniques to help penetration testers and bug bounty hunters to collect and gather subdomains for the domain that are targeting? Using many search engines such as Yahoo, Bing, Google, Baidu, Ask, Netcraft, Virus Total, TheatCrowd, DNSdumpster and ReverseDNS, SSL Certificates. Also, it has brute force mode using an integrated tool named Subbrute.
Subbrute is a DNS meta-query spider that enumerates DNS records and subdomains by using an extensive wordlist.
python3 sublist3r.py –d <domain> -b –t 50
Amass:
The beauty of the baud is for gathering information on the attack surface of targets in multiple dimensions. You have this level of quality across so many features all in one place. Amass performs network mapping of attack surfaces and external asset discovery using open source information gathering and active reconnaissance techniques.
OSINT Techniques
Amass works in a unique way in that all its functionality is broken into models that are called subcommands:
Intel: Collect intelligence on the target in order to determine your starting point.
Enum: Perform enumeration and mapping of your target to determine possible attacks avenues.
OAM Tools
oam_subs: Analyze collected OAM assets
oam_track: Analyze collected OAM data to identify newly discovered assets
oam_viz: Analyze collected OAM data to generate files renderable as graph visualizations
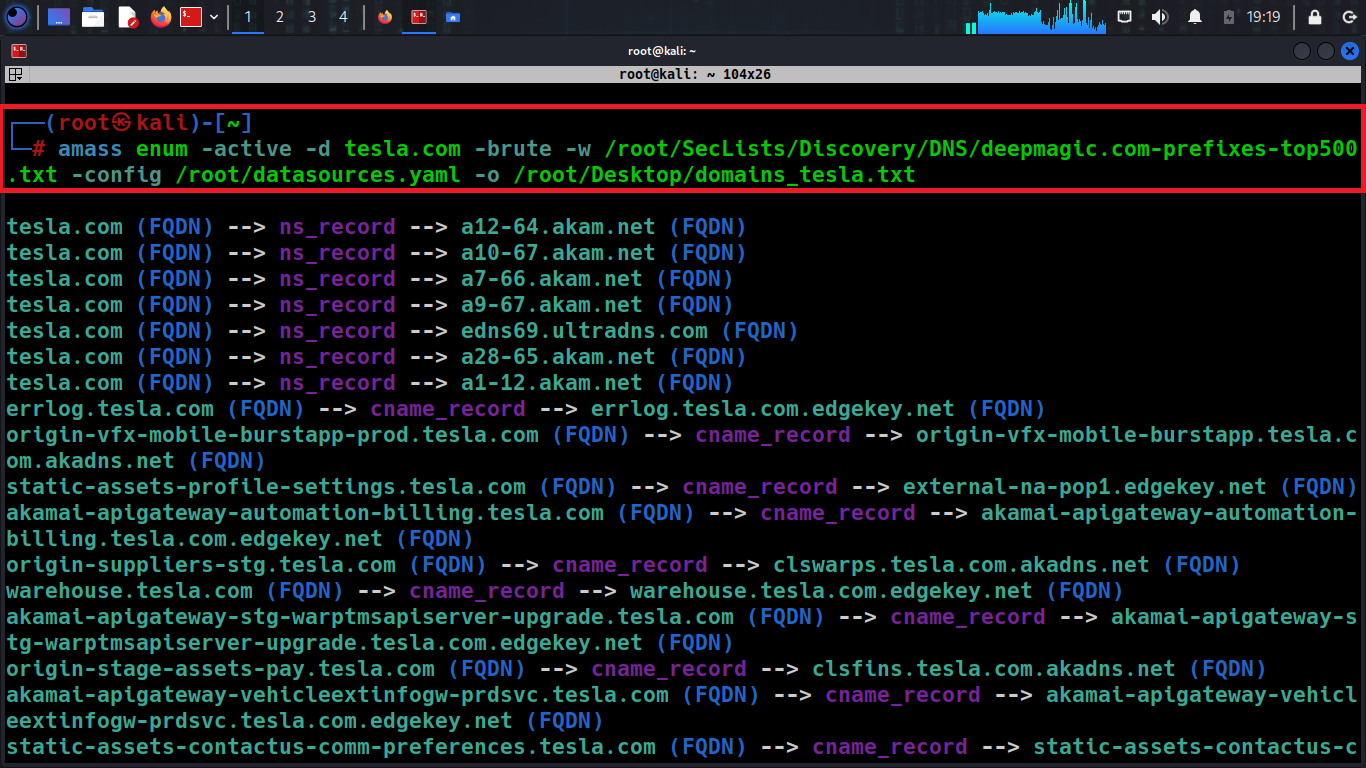
amass enum -active -d -brute -w /location/wordlist -config /location/datasources.yaml -o /location/
*location ➡ follow your local computer location path
*You can choose a valid wordlist based on the scenario after: -brute -w [wordlist location]
You can see the example on the above screenshot.
See Also: Offensive Security Tool: Nucleimonst3r
Analyzing and Reporting Test Results
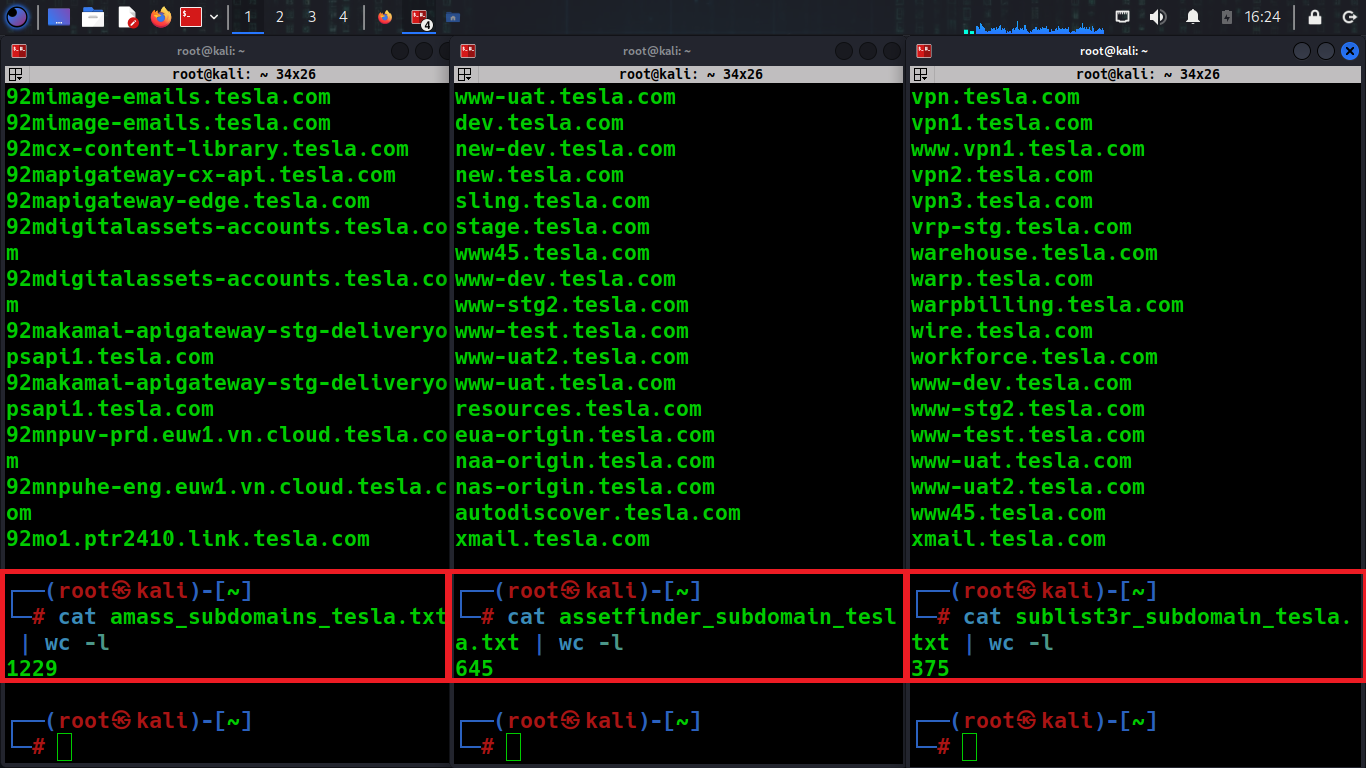
After we have performed subdomain enumeration and tested those tools we noticed that all results have been compiled in a sheet to give you a global and synthetic review of each tool the time for execution, the number of subdomains discovered, the command used, and also wordlist used we have used to perform Brute-force subdomain enumeration.
Before jumping to the next step we need to check which form those IPs are alive (UP) using isup command.
./isup.sh <target_list.txt>
Also we will show you, how to actually compare them using sort command, getting the results from the sublist3r_domains.txt and amass_domains.txt and compare them for example by doing this:
sort -u sublister_subdomains.txt amass_subdomains.txt > final_subdomains.txt
By doing this we have already sorted both results from subdomains remove duplicates and save them into new one final subdomains file, saving time for recon process and more quality results.
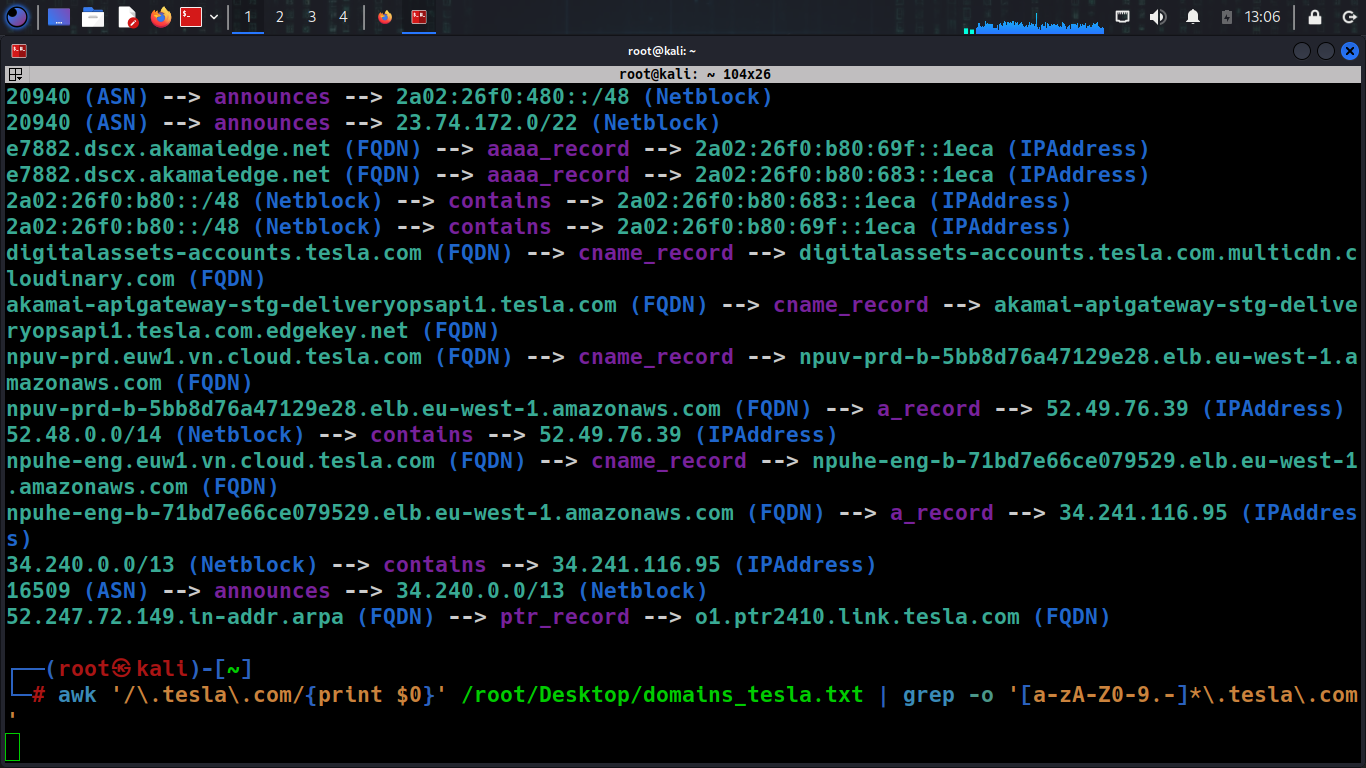
To filter out the results from Amass, you need to retrieve only subdomains.
awk '/.tesla.com/{print $0}' /location/amass_subdomain.txt | grep -o '[a-zA-Z0-9.-]*.domain.com' > /location/amass_subdomains_list.txt
Tools
| Type | Tool | Pro | Cons | Programming Language |
| Active/Passive | Amass | Provides more subdomains than any other tool | Slower than most tools | GO |
| Passive | Assetfinder | It doesn’t need any API key to get a decent amount of subdomains. | It could support more sources to be the most complete tool. | GO |
| Passive | Sublist3r | It’s Faster than most tools. | The brute force module has very limited features. | Python |
Following the screenshot below to examine which tool brings more results in the recon process, about the target:
We spend a lot of hours reviewing tools to find the right way for subdomain enumeration with limited speed and high-quality results.
| Source | Speed | Quantity | DNS Speed | DNS Quality | |
| Amass | ★★★★★ | ★★☆☆☆ | ★★★★★ | ★★★★★ | ★★★☆☆ |
| Assetfinder | ★★★☆☆ | ★★★★★ | ★★★☆☆ | – | – |
| Sublist3r | ★★☆☆☆ | ★★★☆☆ | ★★☆☆☆ | – | – |
Conclusion
In conclusion, we hope you understand from our writeup that it is not just about the tools but also the way you configure them. Such as the APIs being added, the Passive / Active techniques, and what you do with the final results, which is combining all the subdomains gathered from different tools, sorting them, and removing the duplicates. This will give you a great advantage over other competing security researchers since Subdomain Enumeration is the first thing you do to unmask an infrastructure’s layout.
We hope that this write up has taught you something new. If you enjoyed it, the best way that you can support us is to share it! If you’d like to hear more about us, you can find us on LinkedIn, Twitter, YouTube.
Are you a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]