Albert Gonzalez and the ‘Get Rich or Die Trying’ Crew who stole 130 million credit card numbers

Reading Time: 6 Minutes
Other names – Nicknames used by Albert Gonzalez:
- 201679996
- cumbajohny
- j4guar17
- kingchilli
- segvec
- soupnazi
- stanozlolz
- UIN 476747
Early Start
Gonzalez born to Cuban parents in 1981, and attended South Miami High School in Miami, Florida. At a young age he was already setting up computers for other families in his Miami neighborhood.
By the time he was 14 years old, he managed to hack into NASA, which resulted in a visit by the FBI at his high school but, that, didn’t hold him back from what he was about to do years later. His natural-born talent in hacking eventually lured him into using his hacking skills for money.

Credit: Illustrations by Francesco Bongiorni
As long as Albert started high school, he started neglecting his homework and his grades started plummeting because he would simply ”live” in the world of programming chat rooms at night, where he gave himself his first nickname: ‘Soupnazi’, after the sitcom Seinfeld’s restaurateur.
His love affair with computers grew in the high-school where he was the leader of a group of computer nerds who found liberation through their expert knowledge of computers.
After he discovered IRC, he joined chat rooms with hackers where the discussions were in the terms of how-to hack the Internet security, etc. He was spending hour after hour learning and sharing tips with his friends on hacking.
At his point, Albert wasn’t trying to get money for his skills, as he was exploring picking locks in the network security, he was also trying to “show” to the straight-world programmers that he was better than them.
He was considered the alpha-male along with his friends and he was the one to give directions and others will follow.
In 1999, he graduated from high school, and a few months later he would visit one of his online friends, named Stephen Watts. The two of them spent time together as they were sharing the same passions for computer programming and hacking. Stephen would later become one of his partners in crime.
From a college dropout to the leader of ShadowCrew
Albert during his freshman year, taught himself, by reading software manuals, how to hack into Internet service providers for free broadband. But after that, he discovered that he could do more, and he co-opted the credentials of managers and executives, learning more about the systems’ architecture.
Albert dropped out of Miami College in his first semester, after being bored by his entry-level computer courses and moved to New York where landed two jobs, one in a dot-com firm that went bust and then at Siemens, but left after the company moved out of New York.
In 2002, unemployed and in need of money he became one of the leaders of ShadowCrew, a forum where cybercriminals exchanged services, from selling credit card numbers and social security cards to computer crimes.
First arrest and living a double life
In 2003, Albert got arrested in New York after a plainclothes N.Y.P.D. detective, found him withdrawing cash from multiple phony credit cards he had.
The law enforcement officials would soon discover that Albert was more than a cashier, but the moderator of the ShadowCrew forum.
After a couple of interviews, Gonzalez agreed to help the government so he could avoid prosecution, and he was recruited as an informant for Operation Firewall, a federal cybercrime task force.
At the same time, he was studying the agents he worked with, realizing how little they understood about computers to have any real impact on cybercrime.
His work for the government only encouraged his criminal behavior and in his mind his value to the federal force reinforced just how special his skills were.
As he was working with the agents for months on end, the agents developed a close bond with him by working together, but in later words answering if he was more loyal to them than his hacker friends, “This distinction is very important . . . my loyalty has always been to the black-hat community”.

Credit: Francesco Bongiorni
In October 2004, while he was getting insights on how the law enforcement officers were working, he helped them arrest dozens of members of the ShadowCrew forum. Then they urged him to move back to his hometown, Miami, for his own safety (it wasn’t difficult for the ShadowCrew members to found out who the snitch was because Albert was one of the leaders in the forum and he did not get prosecuted )
Return to Miami
In late 2004, Albert returned to Miami and he was already exploring the vulnerability of corporate wireless networks.
Just as data security wasn’t taken into much consideration by companies in the late 1990s as they rushed to get online, the same can be said for many firms that’d taken no security measures for the eagerly adopted WIFI in the early 2000s.
Wardriving
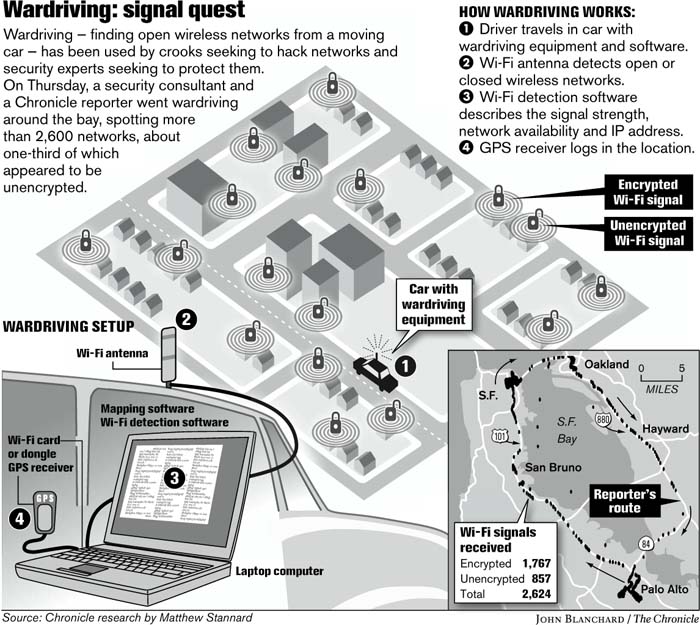
Wardriving. Source: Chronicle research by Matthew Stannard
Albert was intrigued by the possibilities of the technique known as “wardriving”: where hackers would sit in a car or van in the parking lots of stores with their laptops and high power radio antennae and dig through companies’ vulnerable WIFI networks. Within minutes a skillful hacker could get into a billion-dollar business server.
Albert was ready to start his ‘Get Rich or Die Trying’ Crew, after the 50 Cent album and movie, along with an old friend of his (hack-buddy from IRC chat rooms), Christopher Scott who was willing to put the work and Stephen Watts.
Scott managed to steal 400K card accounts from BJ’s Wholesale Club and DSW using the ‘wardriving’ technique and then passed the card numbers to Albert.
Criminal Lifestyle
He, Albert, aided another investigation and he became a paid informant in the Secret Service office in Miami in early 2006.
His lifestyle was insane, he was buying himself new cars, condos and often stayed in luxury hotel suites in Miami. He spent thousands on restaurants, clubs, drugs, and also threw a 75$K birthday party for himself. He was also taking trips to New York to visit his friend Watt’s – who was working by day in the I.T department of Morgan Stanley.
He would be working for the service during the day, and then come home to manage his ongoing crime “business” of selling stolen card information.
Scott and Albert were setting up multiple hackers who were under investigation by the Service, by selling them databases of stolen information of companies of whom the breaches were being investigated.
Wanting a new challenge
In the middle of 2007, Albert was tired of working for the services, he was not showing up on time, and the agents began talking for cutting him loose and eventually did.
He was also tired of wardriving and wanted a new challenge, the new challenge was the promising technique called SQL injection, the technique that will later use to compromise corporation data.
SQL is the programming language that enables most commercial Websites to communicate with their associated databases. A hacker who learns how to manipulated SQL queries could’ve penetrated any company at the time, Albert liked the idea that he didn’t need to be outside of any store to do it like wardriving, he could do it from anywhere.
Their technique was a combination of SQL injection to deploy backdoors on several corporate networks and then to launch packet sniffing attacks like, ARP spoofing, which allowed them to intercept payment data and then follow the chain of network vulnerabilities to made their way into the corporate servers of the parent company.
Stephen and Patrick wrote code that his handlers could use in their undercover operations
They had thought through every angle, chaining 20 encrypted IP address proxies to obscure their own location.
Albert and Patrick would now review lists of Fortune 500 companies to find their targets. Then find out what kind of computer systems a firm used and they would swing by one of its retail stores to scope out the terminals at the checkout counters. After hacking into corporate databases through company websites, they used malware which they tested against dozens of Antivirus programs to make sure its presence wouldn’t be detected, and then download the credit-card data in small, well-timed data to avoid alerting a victim’s server administrator. After that, they will erase their digital footprints as they exited the system and installed invisible backdoors to provide them future access.
By the end of 2007, Gonzalez and his crew were estimated that they’d breached more than 50 million credit card accounts by hacking into Target, OfficeMax, Barnes & Noble, TJX, and many other companies.
In many cases, the data were simply there for taking, unprotected without encryption.
Albert would then proceed and assemble an international cartel with the help of a Ukrainian, Maksym Yastremskiy, for selling the credit card accounts across America, Europe, and Asia.
He proceeds with setting up dummy companies in Europe, and to collect the payments and launder the money, he opened WebMoney and e-gold accounts which weren’t strictly regulated.
Soon he would be joined up with two European hackers who were onto something massive, to break into American card-payment processors, important cash arteries.
Gonzalez’s very purpose of doing these crimes was at first monetary because the service’s salary wasn’t enough, but he already created the snowball and he wanted, but couldn’t quit.
He later admitted that his intentions were not only for the cash but he also wanted to help out a friend and hacker who had family and financial problems, his friend was Patrick Toey who help him to break into the corporate networks.
Being tailed by the Secret Service and Arrest in Miami
In the spring of 2008, when Albert and Toey were on their way back from a recon mission in Miami, they became suspicious when a sports car followed them for a while, they were agents of the Secret service following him, but he managed to escape and drove back to his condo.
Albert, along with Stephen got arrested in May of 2008 by federal agents in the luxury hotel they were living at the time, in Miami. The agents found a pistol, two laptops, and 25K dollars in cash. He later admitted that he buried in the backyard of his parent’s house, a barrel with 1 million dollars in cash also.
The way Albert got exposed and the damages in numbers
The agents had been tipped off after Maksym Yastremskiy, Albert’s Ukrainian card-hawker, was arrested in July 2007. After examining his laptop, they found out millions of stolen card numbers, programs used to hack into corporate enterprises, and logs of encrypted chats with Albert stored on Maksym’s hard drives. Once they managed to decrypt the chat logs with Albert, they manage to tie Maksym with Albert.
Patrick Toey was also arrested in his condo in Miami, and despite being Albert’s best friend, he took into consideration his life more than his friendship with Albert, and cooperated with the authorities. His cooperation was cited highly crucial in bringing down Albert’s operation and, he therefore received a sentence of five years, despite facing a maximum of 22.
Upon arresting Albert, the federal agents began connecting the dots after they opened his computers and they were astounded by the scope of the operation their “trusted” informant was running.
The government indicted 11 members of the Crew that Albert was running in his worldwide “enterprise” and estimated that the scheme cost its corporate victims (banks etc.) 200$ million. They stated that it was impossible to quantify the full vastness of the crime because of the enormous impact on so many businesses, banks, and millions of people.
Sentences
Stephen Watts pleaded guilty for writing the code that proved to be the key for Albert’s operation but he continues to insist that he never knew that it was being used for illegal purposes, he also said that he made no money from the crimes.
The prosecution argued about that and the judge agreed, sentencing Stephen to two years in prison and ordering him to pay a share of the 180 million damages.
Albert showed remorse for his crimes, he admitted that “he never thought the impact of his actions on the millions of people affected” and he was deeply sorry for his actions that had so many consequences.
Albert pleaded guilty and cooperated fully with the authorities as soon as he realized that Patrick had turned state’s witness.
For his cooperation, he avoided life in prison and he was sentenced in 2010 to 20 years, which is the longest punishment for a computer crime in history.
In his last words before going to prison: “I blame nobody but myself,” “I’m guilty of not only exploiting computer networks but exploiting personal relationships, particularly one that I had with a certain government agency who believed in me. This agency not only believed in me but gave me a second start in life, and I completely threw that away”.
Accounting for the time servers and good behavior, he is expected to be released from prison in 2025.
References:
⦿ https://www.smh.com.au/technology/get-rich-or-die-tryin-soup-nazi-hackers-motto-20090820-erbh.html
⦿ http://content.time.com/time/business/article/0,8599,1917345,00.html
⦿ https://careersincybersecurity.com/famous-hackers-and-their-groups-albert-gonzalez-and-his-get-rich-or-die-trying-crew/
⦿ https://www.independent.co.uk/news/world/americas/hacker-s-high-life-brought-end-20-year-sentence-1929312.html
⦿ https://www.nytimes.com/2010/11/14/magazine/14Hacker-t.html
⦿ https://www.wired.com/2010/03/tjx-sentencing/
⦿ https://www.rollingstone.com/culture/culture-news/sex-drugs-and-the-biggest-cybercrime-of-all-time-241836/
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]









