Analyzing Microsoft’s NBNS and BOOTP Protocols with Wireshark for Red Teaming

Reading Time: 3 Minutes
Introduction
Wireshark, a potent network protocol analyzer, is crucial to have in the arsenal of red teamers’ collection when it comes to network packet sniffing. This tool allows us to dissect and understand the inner workings of network traffic, providing invaluable insights for exploiting vulnerabilities. In this article, we’ll focus on two key services: BOOTP (Bootstrap Protocol) and NBNS (NetBIOS Name Service). Those are not very much known to many and hopefully show you how you can use them when you perform your Red Team engagements if it has to do with Internal Pentesting or Local Network enumeration techniques taking advantage of vulnerable such components by design that can be forgotten.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Understanding NBNS and BOOTP
NBNS
NBNS stands for “NetBIOS Name Service,” which is a protocol used in older Windows-based networking environments to translate NetBIOS names (computer names) into IP addresses. NetBIOS (Network Basic Input/Output System) is a networking protocol that allows applications on different computers to communicate within a local area network (LAN). It was commonly used for file sharing, printer sharing, and other network-related functions.
BOOTP
BOOTP is an older protocol that uses a static address assignment process. BOOTP, an acronym for Bootstrap Protocol, served as a precursor to DHCP (Dynamic Host Configuration Protocol) and played a pivotal role in streamlining the process of assigning IP addresses to devices within a network. This protocol revolutionized network configuration by automating the allocation of IP addresses, thereby enhancing efficiency and reducing the manual intervention required for network setup.
See Also: Offensive Security Tool: Nucleimonst3r
Capturing Traffic
Wireshark is a free and open-source packet analyzer that allows users to capture and analyze the data traveling back and forth on a network in real time. Here’s how you can use these filters and techniques in the context of NBNS and BOOTP to obtain sensitive intel info:
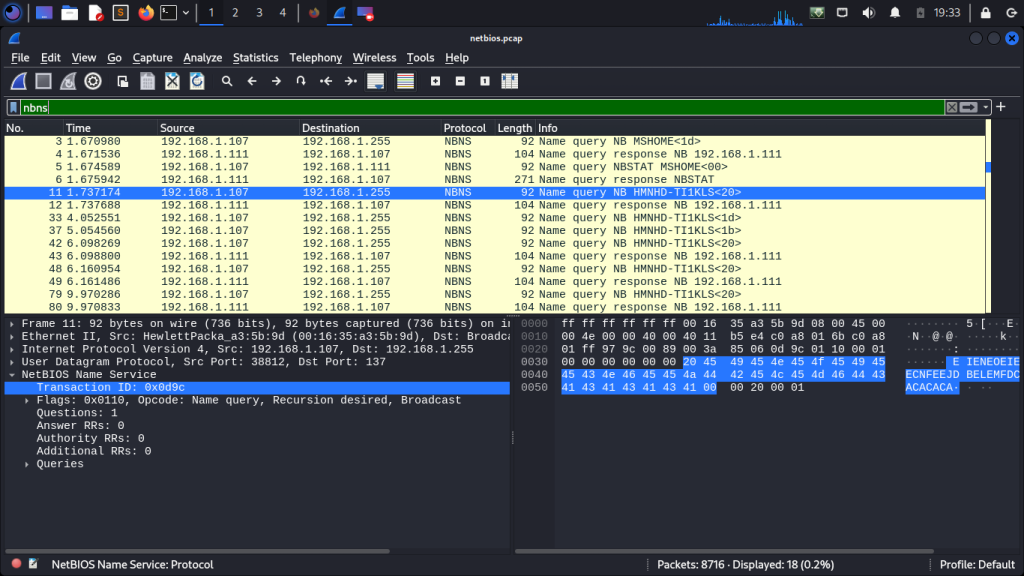
Launch Wireshark and start capturing network traffic on the local network interface. Apply filters to specifically capture NBNS
NBNS vulnerabilities can be leveraged by Red Teamers to engage in NetBIOS name poisoning or spoofing attacks. By employing these strategies, attackers can redirect network traffic or initiate man-in-the-middle attacks, compromising the security and integrity of the targeted system. Very important to check whenever you are performing internal network assessments.
NBNS Spoofing can be implemented through Metasploit Framework by using a variety of modules that can capture the negotiated authentication challenge for protocols such as SMB and HTTP. For capturing the password hash over SMB.
See Also: Reverse Engineering-Hacking Tools
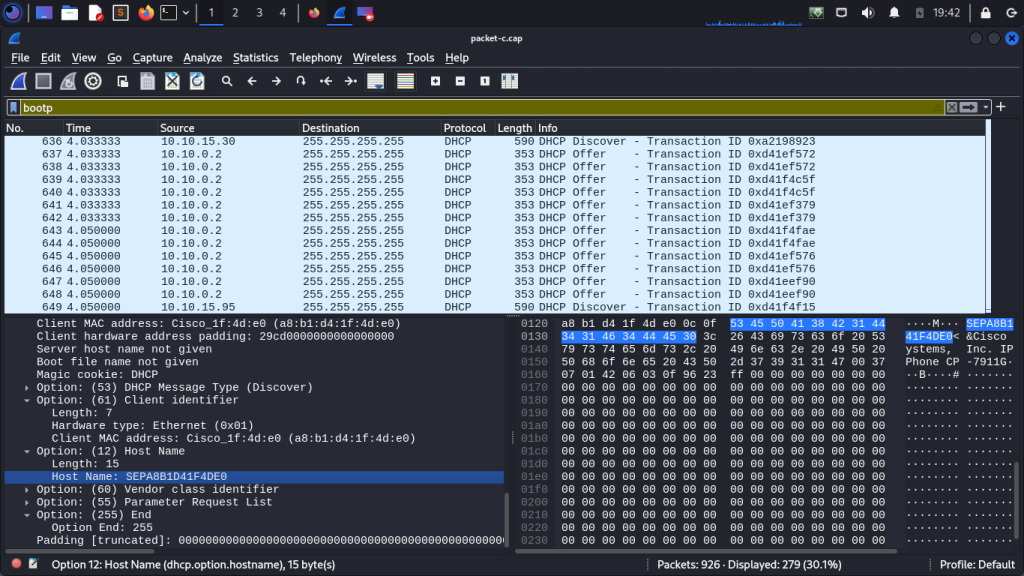
Doing the same as before, launch Wireshark and start capturing network traffic on the local network interface. Apply filters to specifically capture BOOTP.
This is a packet capture from a router. We were troubleshooting DHCP packet flows. The router saw the DHCP Discover and Sent an Offer. We never saw the DHCP acknowledgment. In the adjacent core stacked switching, we were running “debug IP DHCP server packets” and we only saw discovered packets from IP phones up to the router.
Last Thoughts
We hope we successfully showed how to break down the techniques and filters utilized from this perspective, and showcased that Wireshark’s strength lies in its ability to capture, analyze, and filter network traffic by leveraging precise filters as shown earlier. Red teamers can intercept and scrutinize BOOTP and NBNS communications. This level of granularity is essential for identifying vulnerabilities, unauthorized devices, and potential weak points in a network’s defenses.
We hope that this write up has taught you something new. If you enjoyed it, the best way that you can support us is to share it! If you’d like to hear more about us, you can find us on LinkedIn, Twitter, YouTube.
Are you a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]