Breaking Down Active and Passive Reconnaissance

Reading Time: 8 Minutes
Introduction
In military strategy, reconnaissance, or “recon,” refers to the initial scouting operations carried out to gather essential intelligence on enemy positions, strengths, weaknesses, and the landscape of the battlefield. This preparatory phase is critical in forming strategies that maximize an army’s chances of success while minimizing risks. Similarly, in cybersecurity, reconnaissance is the foundational phase in offensive security where security experts and attackers gather information about a target—whether a system, network, or organization—to develop an informed strategy for penetrating defenses. This step is as pivotal in digital security as it is in traditional warfare; in offensive security, it is essential to “know the lay of the land” before proceeding with an attack.
Reconnaissance is one of the most critical phases in Offensive Security. In penetration testing or Bug Bounty Hunting, reconnaissance refers to scoping out a target system, network, or organization in preparation for an attack. Through this preparatory phase, security professionals or attackers may thoroughly understand the target environment and enumerate certain vulnerabilities or weak points that may be exploited. Without good reconnaissance, any attack would be a shot in the dark and far less likely to succeed.
The dominant types of reconnaissance, are active and passive reconnaissance: techniques that can gather valuable data such as the list of open ports, running services, internal structure of the network, or publicly available information about a target. Active reconnaissance means contacting a target directly since one is taking more risks of being discovered, while passive reconnaissance implies gathering information noiselessly for the target from public sources or network traffic.
It finds its significant role in penetration testing, Bug Bounty Hunting, vulnerability assessments, and even large-scale cyber-attacks. In all these, reconnaissance should help any given penetration tester to understand the architecture and the weaknesses of a target system. To the attacker, this phase provides some key foundational elements necessary for more sophisticated exploits by helping them find entry points into a system or network.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
What is Reconnaissance in Cyber Security?

Reconnaissance, sometimes referred to as “recon”, is generally known as the information-gathering phase, and is considered the initial step in Hacking. The activity involves the structured collection of data about a target to comprehend its structure, weaknesses, and defenses. This stage is carried out by attackers, ethical hackers, and security professionals, who collect information publicly and privately, analyze the target’s digital footprint, and determine how to proceed with the attack or test.
Reconnaissance is similar to scouting in warfare: one wouldn’t launch an offensive without understanding the lay of the land, the enemy’s defenses, and the routes to penetrate them. Similarly, in cybersecurity, success depends on knowing where the potential access points are and how to exploit them. Whether in penetration testing or bug bounty hunting, reconnaissance always starts the process.
Keep in mind that Reconnaissance makes up about 90% of the hacking process, with only 10% dedicated to execution.
Goals of Reconnaissance:
Finding Weaknesses: Reconnaissance identifies weaknesses in the target’s security posture, such as exposed services, unpatched software, or misconfigurations that can be exploited.
Finding the Entry Point: Attackers or ethical hackers seek entry points, such as open ports, exposed applications, or misconfigured devices, to gain unauthorized access to a system or network. These vectors are crucial for infiltrating and escalating privileges within the system.
Acquiring Intelligence: Reconnaissance aggressively gathers intelligence on the security measures implemented by the target, such as firewalls, intrusion detection systems (IDS), or encryption mechanisms. Understanding these defenses allows attackers or testers to strategize methods to bypass or disable them.
Mapping Network Architecture: Another key objective is mapping the target’s network architecture by identifying hosts, devices, services, and network segmentation. This gives a clear view of the target’s digital layout, helping identify vulnerable or less protected areas.
Retrieving a Target’s Historical State: Conducting recon allows you to trace the origins of a target, even if a website or system has undergone significant updates over the years. By going deeper into historical data, such as archived versions of a website, you can uncover the state of the system when it first went online. This historical context often reveals forgotten details—small traces or “breadcrumbs” left by developers during the initial phases of development. These traces can lead to sensitive information, such as early configuration files, internal paths, or hints about the technologies and methodologies initially used. Tools like the Wayback Machine are invaluable for this type of web history analysis, but the principle applies beyond websites. Historical snapshots of hosts, IP addresses, and other assets, like CRMs, can also provide valuable insights into the evolution of a target and potential overlooked security gaps.
Public Information Enumeration: Often, a wealth of information about a target is already in the public domain. From DNS records, social media profiles, and employee email addresses to press releases, valuable data can be gathered without direct contact with the target. This is especially useful for passive reconnaissance.
Passive Reconnaissance Techniques
Definition and Main Features
Passive reconnaissance is information gathering where an individual or entity collects data about a target system, network, or organization without directly engaging with the target. Unlike active reconnaissance, which involves probing a system (e.g., port scanning), passive reconnaissance relies on indirect means to gather publicly available information. This reduces the chance of detection, making it a suitable technique for cybercriminals and ethical hackers who want to learn without alerting the target, however, it may come with inaccuracies, such as outdated information or dead links.
The main characteristic of passive reconnaissance is that it remains undisclosed. The target is unaware that data is being gathered because there is no direct engagement or change in normal operations. Passive recon doesn’t trigger security defenses, like intrusion detection systems (IDS) or firewalls, making it extremely stealthy.
Common Passive Reconnaissance Methods
Passive reconnaissance can be performed through several methods, usually involving publicly available data or information retrieved indirectly.
Common methods include:
- Open-Source Intelligence (OSINT): OSINT collects and analyzes publicly available sources like websites, blogs, social media, and online databases. Attackers and ethical hackers use it to gather information on a target’s employees, operations, technologies, and assets.
- Example: Email Harvesting – An attacker might use tools or search engines to scrape email addresses from a company’s website, LinkedIn profiles, or other platforms to use in a targeted phishing campaign.
- DNS Queries: DNS queries allow attackers or ethical hackers to map out a target’s online infrastructure by resolving domain names to IP addresses, and identifying servers, services, and locations without direct interaction.
- Example: A tester querying DNS records might identify mail, web, and DNS servers, revealing misconfigurations or unpatched software.
- WHOIS Lookups: WHOIS lookups retrieve a domain’s registration details, including owner contacts, registrar, registration date, and expiration, helping attackers or security professionals find weaknesses.
- Example: WHOIS records might reveal that a company’s domain is about to expire, making it vulnerable to domain hijacking or social engineering.
- Website Footprinting: Studying a website’s structure and metadata, such as robots.txt or sitemap.xml files, provides information about backend technologies and potential vulnerabilities.
- Example: A penetration tester could find sensitive directories by reviewing a target’s robots.txt file, which may contain critical files.
- Search Engine Dorking: This technique uses advanced search operators to locate sensitive data unintentionally exposed online, such as admin panels, passwords, and configuration files.
- Example: A hacker might use a query like “site:example.com intext:confidential” to find confidential documents exposed to the public using Google’s search engine.
- Job Listings Analysis: Job listings analysis involves examining job postings from a company to learn about the technologies and software used in their environment. Job ads often disclose the technical skills required, giving insights into the company’s infrastructure.
- Example: A penetration tester finds a job listing from the target company on a job site, which mentions that the company is looking for an “experienced AWS administrator,” suggesting that the company uses Amazon Web Services as part of its cloud infrastructure.
Passive Reconnaissance Tools
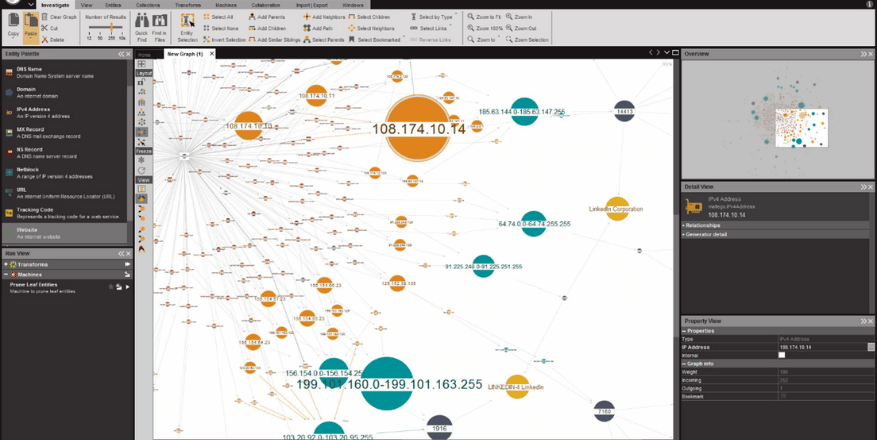
Maltego Scan
Tools for passive reconnaissance help automate the process of gathering information without triggering security alerts. Some popular tools include:
- Maltego: A powerful OSINT tool for visual link analysis, showing relationships between domains, IP addresses, emails, and social media profiles.
- Example: Maltego is often used to map a company’s digital footprint by correlating various data points.
- Shodan: A search engine for finding Internet-connected devices like routers, servers, webcams, and IoT devices. It helps locate publicly exposed systems and vulnerabilities.
- Example: Ethical hackers use Shodan to find publicly accessible servers and IoT devices with weak security configurations.
- theHarvester: A passive reconnaissance tool that collects email addresses, subdomains, IPs, and employee names from search engines and social media platforms.
- Example: An ethical hacker may use theHarvester to find employee emails for phishing simulations or social engineering attacks.
- WHOIS Lookup Tools: Tools that provide domain registration information such as owner details, contact info, and important dates (creation/expiration).
- Example: Useful for identifying the entity behind a domain or finding out administrative contacts in a company’s domain registration.
- Recon-ng: A web reconnaissance framework that automates data collection from public sources such as LinkedIn, Twitter, and DNS records.
- Example: Often employed in gathering comprehensive information about a company’s employees, subdomains, or IP ranges.
- Amass: A reconnaissance tool that performs both passive and active information gathering to discover subdomains, IP addresses, and network infrastructure associated with a target. It helps map a target’s external network footprint, making it essential for building a target’s asset profile.
- Example: A penetration tester uses Amass to gather and confirm subdomains for a target, revealing parts of the attack surface through passive and active recon methods.
Advantages of Passive Reconnaissance:
Undetectable: Since it doesn’t interact with the target system, it is nearly impossible to detect.
Low Risk: No direct requests to the target mean no chance of triggering security alarms or being blacklisted.
Bandwidth consumption: Since no direct requests are aimed at the target, no congestion in traffic will affect any target, making it ideal for a complete stealth operation without disruption of any running services on the target.
Useful for Initial Assessment due to speed: It’s ideal for gaining an overview of a target’s online presence without jeopardizing the mission in a very fast way, getting real results in minutes.
Disadvantages of Passive Reconnaissance:
Limited Depth of Access: It only collects publicly available information, potentially missing internal vulnerabilities.
Incomplete Data: Passive reconnaissance tends to provide broad but shallow insights, lacking the detailed technical data obtained through active methods. A lot of expired links or data are outdated or no longer exist, but they are still there in traces.
Reliance on Public Data: It depends heavily on what information is publicly exposed, which may not always be enough for successful penetration testing or attacks. Also, it depends on the sources you are using to fetch this information which can limit the results from one source to another.
Active Reconnaissance Techniques
Definition and Main Features
Active reconnaissance is an intense, intrusive investigation used to gather intelligence from a target system or network. Unlike passive reconnaissance, which involves collecting publicly available information without interacting with the target, active reconnaissance involves direct communication with the target system to identify potential vulnerabilities, open services, and network configurations. This process often requires sending packets or data queries to the target, which may trigger responses or alerts, potentially exposing the reconnaissance activity. Key characteristics of Active Reconnaissance include:
Direct Interaction: Active reconnaissance involves direct engagement with the target, such as scanning open ports or querying services, making it more invasive than passive methods.
Higher Chance of Detection: Since active reconnaissance sends requests to the target system, it’s more likely to be detected by firewalls, intrusion detection systems (IDS), or other security tools. The target’s defense mechanisms may log or block the reconnaissance activity, and conducting this without proper authorization could lead to legal consequences but also give you an inaccurate result where they are blocked.
More Valuable Insights: Although riskier, active reconnaissance provides more detailed information about the target, including real-time data on running services, network configurations, and system vulnerabilities. It is essential in the later stages of penetration testing or attack preparation. The accuracy is valid in comparison to the passive recon method, as there are no false positives in this case.
Common Active Reconnaissance Methods
Active reconnaissance involves several techniques to collect accurate and actionable data about a system or network. The most common methods include:
- Port Scanning: This method identifies open ports on a target system or network. Open ports represent entry points that can be exploited if linked to vulnerable services or misconfigured security settings.
- Example: A penetration tester uses a tool like Nmap to scan the target’s ports and discovers port 22 (SSH) is open, indicating a Secure Shell service is running. If the SSH service is outdated or poorly configured, it may be vulnerable to brute-force attacks or software exploits.
- Ping Sweeps: A technique involving the sending of ICMP (Internet Control Message Protocol) requests (ping requests) to multiple IP addresses within a network to see which hosts are active.
- Example: A penetration tester uses Nmap to perform a ping sweep on a network range (e.g., 192.168.1.1-254). The scan reveals that IPs 192.168.1.10 and 192.168.1.20 respond, indicating that these devices are active and might be reachable for further recon or attack.
- Network Mapping: Network mapping is the process of discovering the structure of a network, including routers, firewalls, and other devices, by analyzing how data travels through the network. This can help attackers or testers understand the target’s infrastructure and identify weak points for further exploitation.
- Example: A tester uses Traceroute to map out the path to the target server. The tool shows several intermediate routers and firewalls, which could potentially be targeted if they are misconfigured or vulnerable.
- Service Banner Grabbing: A method that sends queries to open ports and services to extract identifying information, known as a “banner,” which often includes details about the software version, service type, or operating system.
- Example: By performing banner grabbing on a web server running on port 80, an ethical hacker might discover the server is running an outdated version of Apache, which is vulnerable to known exploits.
- Vulnerability Scanning: Vulnerability scanning is the process of automatically detecting known vulnerabilities in a target system or network. Tools compare the system’s configuration and software versions against a database of vulnerabilities to highlight weaknesses.
- Example: A penetration tester runs a scan with Nessus, which reveals that the target system is running an outdated version of Apache vulnerable to a directory traversal attack.
- Brute Force Authentication Testing: Brute force authentication testing involves repeatedly attempting different combinations of usernames and passwords to gain access to a system. It is used to exploit weak login credentials.
- Example: A tester uses Hydra to target the SSH login page of a server. After several attempts, the tool successfully guesses a weak password and gains unauthorized access to the system.
- DNS Enumeration: DNS enumeration is the technique of querying DNS servers to gather information about domain names, subdomains, and IP addresses associated with a target network. This can help attackers locate hidden services or other potential entry points.
- Example: A penetration tester uses the tool dig to perform a DNS query on a target domain and discovers several subdomains, including admin.target.com, which might host a sensitive administrative login page.
See Also: Offensive Security Tool: Upload_Bypass
Tools for Active Reconnaissance
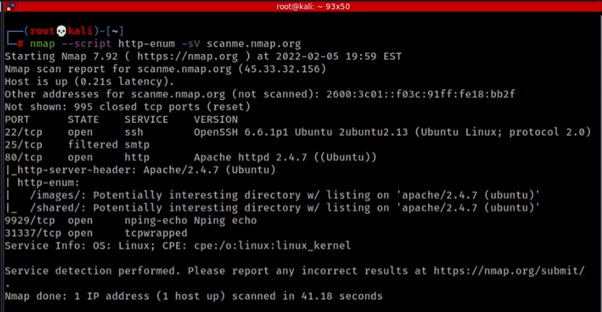
Enumeration and service detection using Nmap
There are several powerful tools for active reconnaissance. These tools allow ethical hackers and attackers to gather detailed information about their target, providing insights into vulnerabilities, running services, and network topology.
- Nmap: The industry-standard tool for port scanning, service detection, and network mapping. It allows users to perform various types of scans, from simple ping sweeps to advanced stealth scans like SYN scans that aim to evade detection by security systems.
- Example: An ethical hacker uses Nmap to scan a target network for open ports, identify running services, and perform service version detection to find outdated software.
- Metasploit: A comprehensive penetration testing framework that includes reconnaissance features like service enumeration and vulnerability scanning. It can be used to perform banner grabbing, service discovery, and in some cases to exploit known vulnerabilities.
- Example: After identifying an open port running a vulnerable service using Nmap, a penetration tester uses Metasploit to further explore the service and potentially exploit it.
- Nikto: A web server scanner that checks for common vulnerabilities, outdated software, and misconfigurations.
- Example: Commonly used for vulnerability assessments of web servers, looking for exploitable configurations.
- DirBuster: A directory brute-forcing tool that discovers hidden directories and files on a web server.
- Example: Employed to find sensitive directories or admin pages that aren’t publicly listed.
- OWASP ZAP: A web application vulnerability scanner that helps identify security issues such as SQL injection and XSS.
- Example: Used by security testers to scan web apps for vulnerabilities and test their defenses.
- Traceroute: A command-line tool that traces the path data packets take from your system to a target, identifying hops and devices along the way.
- Example: Commonly used to map network paths and identify devices between a source and target.
- Amass: A reconnaissance tool that performs both passive and active information gathering to discover subdomains, IP addresses, and network infrastructure associated with a target. It helps map a target’s external network footprint, making it essential for building a target’s asset profile.
- Example: A penetration tester uses Amass to gather and confirm subdomains for a target, revealing parts of the attack surface through passive and active recon methods.
Advantages and Disadvantages of Active Reconnaissance
Advantages:
- More Significant Knowledge: Active reconnaissance provides in-depth and current information about a target system or network, enabling more accurate vulnerability assessments and strategic attack planning.
- System-Level Information: Techniques like port scanning and banner grabbing provide knowledge of the actual services and software running on a system, including their versions, configurations, and vulnerabilities.
- Real-Time Feedback: Active reconnaissance returns immediate results, such as whether a port is open or closed, or what version of the software is running, enabling penetration testers to act quickly on discovered vulnerabilities.
Disadvantages:
- High Chance of Detection: Since active reconnaissance involves direct interaction with the target system, it is more likely to be detected by security tools like firewalls, intrusion detection systems, and intrusion prevention systems. This increases the likelihood of the target becoming aware of the reconnaissance activity. However, an experienced ethical hacker can find ways to bypass these measures.
- Legal Implications: Unauthorized active reconnaissance can lead to serious legal consequences. Probing systems or networks without permission violates laws like the Computer Fraud and Abuse Act (CFAA), making it crucial for ethical hackers to obtain proper authorization before performing active reconnaissance.
- May Trigger Active Defenses: Active reconnaissance can sometimes trigger automated defense mechanisms, such as blocking the attacker’s IP address or alerting network administrators to potential threats.”
Legal and Ethical Considerations

Reconnaissance, both passive and active, is a critical part of Offensive Security. But it’s just as important to understand the legal and ethical limits when engaging in these activities.
Why Consent and Legal Boundaries Matter:
- Consent is key when doing any form of recon, especially active reconnaissance. Actively probing systems without permission could land you in legal trouble, violating laws like the Computer Fraud and Abuse Act (CFAA) in the U.S., the GDPR in Europe, or similar laws elsewhere.
- Ethical hackers doing penetration tests need written consent from the organizations they’re testing or an NDA (Non-Disclosure Agreement). This consent protects both sides: the testers can legally check the systems, and the organization’s assets stay safe.
- Without permission, even small things like scanning ports or looking up DNS info could be seen as illegal hacking and might result in serious legal penalties.
The Ethics of Active Reconnaissance:
- Active reconnaissance means interacting directly with the target, which raises ethical concerns, especially if done without the target’s knowledge or approval.
- Ethical hackers follow strict guidelines—they’re transparent, don’t cause harm, and stick to the rules their clients set. But attackers, ignore these boundaries and use active recon to find weaknesses they can exploit for harmful reasons.
Comparing Active vs. Passive Reconnaissance

Stealth:
- Passive Reconnaissance is stealthier because it involves gathering information from public sources, like DNS records, social media, or public web pages, without interacting with the target’s systems. The target remains unaware that any reconnaissance is taking place.
- Active Reconnaissance, on the other hand, directly engages with the target’s systems, using techniques like port scanning or vulnerability probing. This interaction creates network traffic, which could be logged or trigger alarms in intrusion detection systems (IDS) or firewalls, making it far less stealthy.
Risk:
- Passive Reconnaissance poses low risk because it avoids direct contact with the target’s infrastructure, making detection very unlikely. However, the downside is that the data collected may be less detailed or outdated.
- Active Reconnaissance is riskier because it engages with the target network, often triggering security defenses. While it provides more detailed information, it comes with a higher likelihood of being detected and potentially blocked or blacklisted. In legal terms, unauthorized active recon could expose you to criminal liability.
Data Detail:
- Passive Reconnaissance gathers surface-level data, like domain information, employee details, subdomains, and exposed technologies (via sources like WHOIS, social media, and DNS lookups). However, it cannot provide real-time data about the internal state of systems (e.g., open ports or services).
- Active Reconnaissance goes much deeper, offering real-time insights into the target network’s status—such as open ports, running services, firewall configurations, and live vulnerabilities. Tools like Nmap and Metasploit are essential for this type of detailed discovery.
Reconnaissance techniques are foundational to Offensive Security, providing essential information about targets—whether for legitimate security testing or malicious attacks. Both Passive and Active Reconnaissance play distinct and complementary roles in intelligence gathering.
- Passive Reconnaissance is crucial for laying the groundwork without alerting the target. It allows attackers or pen-testers to map out potential attack surfaces using public data. However, it provides only surface-level information.
- Active Reconnaissance is vital for deepening understanding, as it interacts with the target’s systems to discover real-time vulnerabilities and weaknesses. But, it comes with a higher risk of detection and legal consequences if done without permission.
Ethical considerations are critical, especially in the world of active reconnaissance, which can blur the lines between testing and malicious activity. The legality of reconnaissance always depends on obtaining proper consent and staying within the bounds of laws and regulations.
Ultimately, the combination of passive and active methods gives security professionals a comprehensive view of the target’s environment, making both techniques essential for effective penetration testing and cyber defense.
As a bug bounty hunter, Pentester, or Security Researcher involved in Offensive Security, we recommend knowing both techniques but also understanding their advantages and disadvantages. Passive techniques are faster because they get the information ready, active reconnaissance, on the other hand, could take time depending on how big the scope is, but it will offer greater results and be more accurate, so patience is key to conducting both and knowing when to use each depending on the methodology you follow.
We hope that this article has taught you something new. If you enjoyed it, the best way that you can support us is to share it! If you’d like to hear more about us, you can find us on LinkedIn, Twitter, YouTube.
Are you a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]