Deep Dive to Fuzzing for Maximum Impact

Reading Time: 6 Minutes
Fuzzing, the Art of Finding Zero Days
Fuzzing, also known as fuzz testing, brute-forcing, or fuzzing, is a software testing technique used to find vulnerabilities and bugs in software applications by providing unexpected, invalid, or random data inputs to the application. This technique is particularly effective for uncovering security vulnerabilities, memory leaks, and other types of software defects that might not be easily identified through traditional testing methods.
The history of fuzz testing
Based on fuzzing.info, Professor Barton Miller coined the term “FUZZ” during the 1980s. While connected to a UNIX system through a dial-up network amidst a storm, Miller detected significant signal interference that eventually led to a system crash. Subsequently, he tasked his students with simulating this incident using a fuzz generator, bombarding UNIX systems with noise to assess their susceptibility to crashing.
Fuzzing Testing: Under the Hood
Fuzz testing is like sending a system random, messed-up messages on purpose to see if it breaks. For example, it could throw weird letters into a web request to check how a website handles it. Fuzzing can indeed be applied to both web applications and software applications.
Let’s break down how it can be used for each type
Web Applications
Fuzzing can be employed to test the security and robustness of web applications. It involves sending various types of malformed and unexpected input to different parts of the application, such as input fields, URLs, headers, and forms. By doing so, fuzzing tools attempt to trigger errors, crashes, or security vulnerabilities like injection attacks (SQL injection, cross-site scripting, etc.), buffer overflows, and more.
Some common types of Fuzzing Techniques used for Web Applications
– Input Fuzzing: Injecting malformed or unexpected input into text fields, URLs, and other input sources.
– Protocol Fuzzing: Testing the behavior of web protocols (HTTP, HTTPS) by sending invalid or unexpected protocol data.
– DOM Fuzzing: Generating random or malformed HTML, JavaScript, or other web content to identify browser or DOM-related vulnerabilities.
Software Applications
Fuzzing can also be applied to standalone software applications, regardless of whether they are web-based or not. The goal remains the same to identify vulnerabilities and bugs by providing unexpected inputs that might trigger crashes or security weaknesses. This can be particularly useful for finding memory-related issues like buffer overflows and resource leaks.
Some common types of Fuzzing Techniques used for Software Applications
– File Format Fuzzing: Sending malformed files or inputs to applications that process various file formats (e.g., images, documents) to trigger parsing errors.
– API Fuzzing: Testing the application’s APIs (Application Programming Interfaces) by providing invalid or unexpected input parameters.
– Network Protocol Fuzzing: Sending malformed or unexpected data over network protocols to test the application’s response.
In both cases, automated fuzzing tools are often used to streamline the process, as manual testing with random inputs can be inefficient and time-consuming. Fuzzing tools generate a large number of test cases with different inputs, which helps to increase the chances of discovering vulnerabilities.

SALE: Benefit from discounted prices on our Courses from 24/11 to 06/12.
The Bug Bounty Hunting Course
Top 10 Tools based on our opinion for Web App testing
dirb: is a web content scanner and directory brute-forcer. It’s designed to discover hidden resources and directories on web servers. It provides customizable wordlists, HTTP methods, and user-agent settings for fuzzing.
gobuster: is another directory and file brute-forcing tool. It supports both file and directory brute-forcing and is known for its speed and efficiency. Gobuster allows customization of wordlists, extensions, and HTTP request headers.
FFUF: is a web application security testing tool and fuzzer. The name stands for “Fuzz Faster U Fool.” It’s designed to help security researchers and penetration testers discover potential vulnerabilities and security issues in web applications.
Burp Suite: A comprehensive web vulnerability scanner and proxy tool for detecting security flaws in web applications.
WFuzz: A web application vulnerability scanner and fuzzer that aids in discovering weaknesses by sending various malformed inputs.
OWASP Amass: A reconnaissance tool that helps discover and map out the external attack surface of a web application.
Watobo: is an open-source web application security tool designed for security professionals and testers. It offers features like proxy functionality for capturing and analyzing web traffic, automated scanning for common vulnerabilities, manual testing with a user-friendly interface, session management, and payload generation.
DirBuster: is a web application security tool used for directory and file brute-forcing. It helps security professionals and penetration testers discover hidden or unlinked directories and files on a web server.
Sqlmap: A specialized tool for automating the process of detecting and exploiting SQL injection vulnerabilities in web applications.
Hydra: This tool is a proof of concept code, to give researchers and security consultants the possibility to show how easy it would be to gain unauthorized access from a remote to a system. There are already several login hacker tools available, however, not many either support more than one protocol to attack or support parallelized connects.
See Also: Offensive Security Tool: Headerpwn
Top 10 Tools for Fuzzing based on our opinion for software testing techniques that involves feeding unexpected or random inputs to a program to identify vulnerabilities:
AFL (American Fuzzy Lop): is a widely used and highly effective fuzzing tool. It uses genetic algorithms to find vulnerabilities in target programs. It has been responsible for uncovering numerous security issues in various software projects.
honggfuzz: is a powerful and efficient fuzzing tool that focuses on fast input generation and crash detection. It supports various types of fuzzing, including coverage-based fuzzing and intelligent evolutionary fuzzing.
Radamsa: is a generative fuzzer that creates mutations of input files to test programs. It’s known for its simplicity and ability to quickly generate a wide range of test cases.
Peach Fuzzer: Peach Fuzzer is a versatile fuzzing platform that supports various types of fuzzing techniques, including smart mutation and generation-based fuzzing. It’s designed to be adaptable to different types of target applications.
Spike: is a fuzzer developed by Immunity Inc. It’s particularly useful for testing network protocols and software components that communicate over the network.
Sulley: is a Python-based fuzzing framework that allows you to define custom protocols and message formats for fuzzing. It’s highly extensible and suitable for complex protocol testing.
PeachPy: is another fuzzing tool from the Peach project. It focuses on protocol and file format fuzzing, allowing you to craft specific test cases for various applications.
WinAFL: is a fork of AFL designed specifically for fuzzing Windows applications. It supports a variety of coverage-guided fuzzing techniques and is especially useful for targeting Windows-based vulnerabilities.
Fuzzilli: is a JavaScript engine fuzzer that targets web browsers. It generates highly complex and mutated JavaScript code to test the browser’s scripting engine for vulnerabilities.
zzuf: is a lightweight fuzzer that’s useful for testing command-line utilities. It can fuzz various inputs, such as files and standard input, to uncover crashes and potential vulnerabilities.
See Also: Reverse Engineering-Hacking Tools
The benefits of Fuzzing
Fuzzing Techniques offer several significant benefits when it comes to software testing and security assessment. Here are some of the key advantages of using fuzzing:
Automated Testing: Fuzzing can be highly automated, allowing testers to generate a large number of test cases quickly. This makes it an efficient way to test software applications for various inputs and scenarios.
Discovery of Unknown Vulnerabilities: Fuzzing can uncover previously unknown vulnerabilities and bugs that might not be identified through traditional testing methods. It simulates real-world scenarios that could expose weaknesses in the software.
Diverse Input Testing: Fuzzing provides a wide range of inputs, including invalid, unexpected, and random data. This helps expose boundary conditions and corner cases that might not be considered in other testing approaches.
Early Detection: Fuzzing can detect vulnerabilities early in the development lifecycle DevOps, making it easier and less expensive to fix issues before they reach production.
Efficient Security Assessment: Fuzzing is particularly effective at identifying security vulnerabilities, such as injection attacks, buffer overflows, and privilege escalation issues.
Regression Testing: Fuzzing can be used for ongoing testing as software evolves. It helps ensure that new code changes or updates don’t introduce new vulnerabilities or regressions.
Cost-Effective: Fuzzing can be a cost-effective testing approach, especially when compared to manual testing for a wide range of input scenarios.
Scalability: Fuzzing can be scaled up to test applications with a large number of input points, making it suitable for complex and interconnected software systems.
Realistic Scenario Simulation: Fuzzing simulates real-world scenarios where inputs can be unpredictable. This can mimic how attackers might interact with the software, making it more likely to uncover vulnerabilities that could be exploited.
Objective Results: Fuzzing generates objective results by automatically identifying crashes and errors, reducing the reliance on tester subjectivity.
Improved Software Quality: By identifying and fixing vulnerabilities and bugs early in the development process, fuzzing contributes to improved overall software quality and reliability.
Reduced Attack Surface: Fixing vulnerabilities discovered through fuzzing reduces the potential attack surface of the software, enhancing its security posture.
Complementary Testing: Fuzzing complements other testing methods, such as static analysis, dynamic analysis, and penetration testing, to provide a more comprehensive assessment of the software’s security and stability.
Continuous Testing: Automated fuzzing can be integrated into continuous integration and continuous deployment (CI/CD) pipelines to ensure that new code changes are automatically tested for vulnerabilities.
Community Contribution: Fuzzing can be leveraged by security researchers and open-source projects to contribute to the identification and mitigation of vulnerabilities in widely used software.
Overall, fuzzing is a powerful technique that can uncover a wide range of vulnerabilities and defects in both side web applications and software applications, making it an essential part of modern software development and security practices.
Wordlists
Fuzzing can be performed manually or with the help of automated tools. Wordlist dictionaries and tools like Crunch play a crucial role in generating meaningful and targeted inputs for fuzzing.
For proper use of fuzzing techniques, wordlist dictionaries are collections of words and phrases, and characters that can be used as inputs during fuzzing. These wordlists can be generic or specific to certain applications, languages, or scenarios. They provide a wide range of input variations to test various parts of an application.
Some commonly used Wordlist Dictionaries include:
– SecLists: A collection of various security-related wordlists for different purposes, such as passwords, usernames, directories, etc.
– RockYou: A well-known password wordlist containing millions of passwords that have been leaked in data breaches.
– PayloadsAllTheThings: is a popular open-source repository on GitHub that contains a comprehensive collection of payloads, exploits, and various techniques for different types of security testing, including web application security, penetration testing, and exploitation.
Wordlist Generation Tools:
Wordlist generation tools automate the process of creating custom wordlists based on specific criteria. These tools are particularly useful for tailoring fuzzing inputs to target a specific application or context.
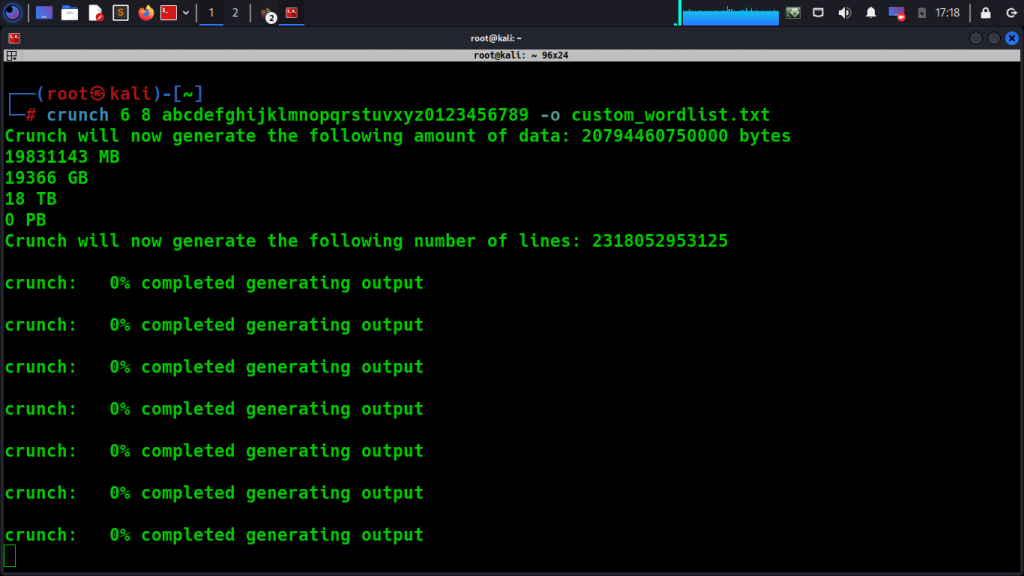
– Crunch: Crunch is a popular wordlist generation tool that allows users to create custom wordlists with various options. It can generate wordlists of specific lengths, include specific character sets, and apply rules to generate complex patterns.
For example, you can use Crunch to generate a wordlist containing all possible combinations of lowercase letters and numbers with a length of 6 to 8 characters:
crunch 6 8 abcdefghijklmnopqrstuvwxyz0123456789 -o custom_wordlist.txt
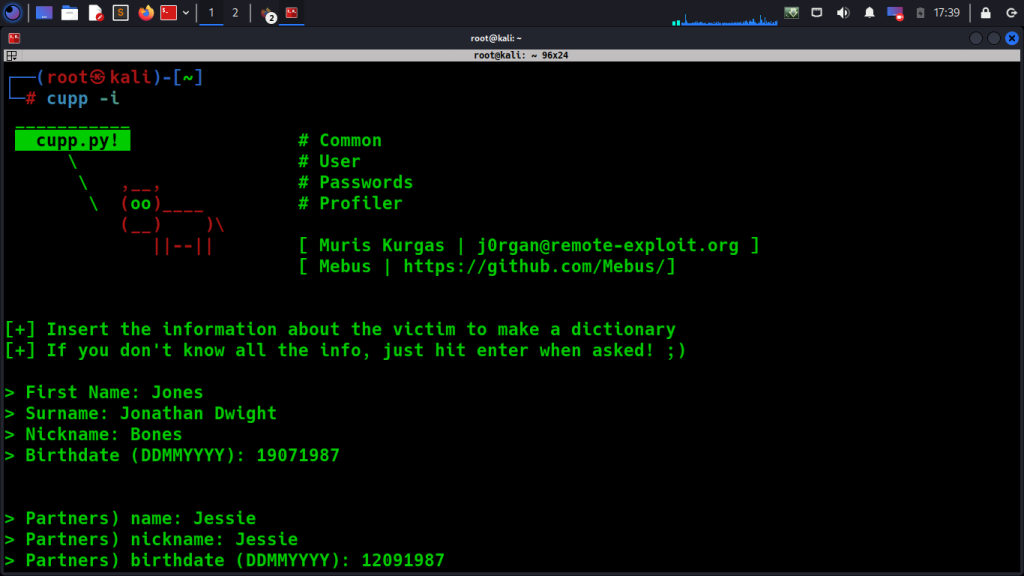
– Cupp: Common User Passwords Profiler (Cupp) is a tool that generates custom wordlists based on personal information about a target, such as their name, date of birth, and other details.
For instance, you can create a wordlist using Cupp based on the target’s first name, last name, and birthdate:
python3 cupp.py -i
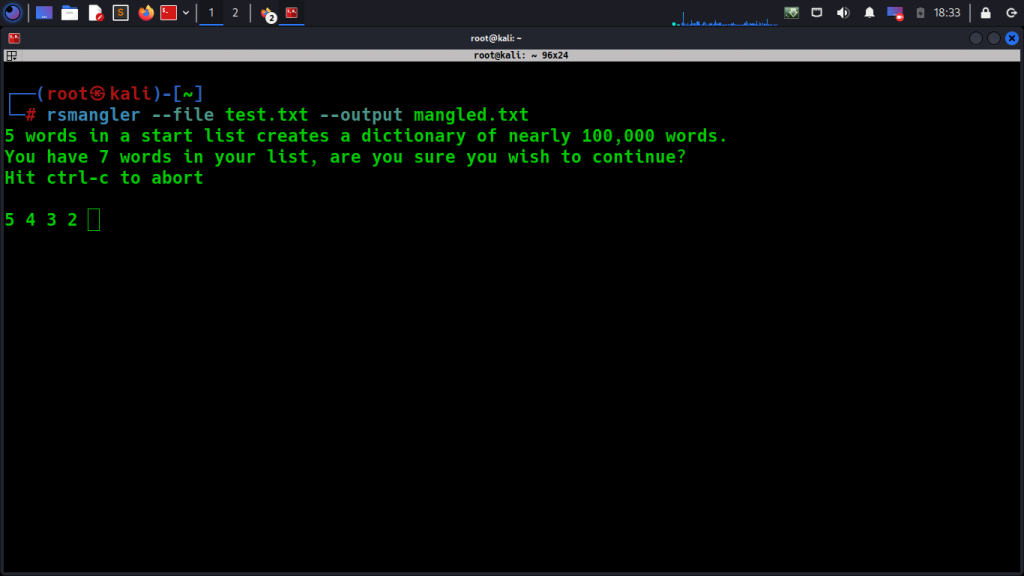
– RSMangler: is a tool designed to create wordlists by applying various word mangling rules to a base wordlist. It can transform words by adding common suffixes, prefixes, or modifying characters in different ways.
An example of using RSMangler to apply basic mangling rules to a wordlist:
python3 RSMangler.py -i base_wordlist.txt -o mangled_wordlist.txt
Combining these wordlist dictionaries and wordlist generation tools with automated fuzzing frameworks (like AFL, Radamsa, or Peach Fuzzer) enhances the efficiency of discovering software vulnerabilities. These tools help testers simulate a wide range of input scenarios, uncovering unexpected behaviors and potential security weaknesses that may not be immediately apparent through traditional testing methods.
Last Thoughts
In conclusion, fuzzing is an invaluable process in the realm of cybersecurity and software development. It serves as a robust methodology for uncovering bugs, vulnerabilities, and potentially zero-day exploits. The utility of fuzzing cannot be overstated, as it plays a pivotal role in enhancing the security of software applications, operating systems, and networked environments.
Efficient Vulnerability Identification through Fuzzing
One of the primary advantages of fuzzing is its ability to efficiently identify vulnerabilities in a systematic and automated manner Various techniques are used to generate a wide range of input data, testing the boundaries of software components to find unexpected behaviors. This proactive approach allows organizations to preemptively patch and mitigate vulnerabilities before malicious actors can exploit them, thereby reducing the risk of cyberattacks.
Time vs. Comprehensive Coverage
However, it’s important to acknowledge that fuzzing can be a time-consuming process. The transparent volume of possible input combinations and permutations can make it challenging to find bugs, especially in complex software ecosystems. This time investment is necessary to ensure comprehensive coverage and the discovery of even the most obscure vulnerabilities.
Contrasting Cybersecurity Dynamics of Pentesters and Hackers
Additionally, it’s worth distinguishing between penetration testing (pentesting) and the activities of real hackers. Pentesters are hired professionals who operate within a defined scope and timeframe, typically focusing on known vulnerabilities and predefined attack vectors. Behind this endeavor, you’ll find a select group of exceptionally dedicated companies and individuals who are driven by an unwavering passion. We’re committed to delivering not just the results you’ve paid for but exceeding your expectations with our capabilities and efforts. They follow a structured approach and are limited by the constraints set by their clients. On the other hand, real hackers, often motivated by financial gain or malicious intent, may spend days, months, or even years probing systems, searching for that unique vulnerability that could grant them unauthorized access.
The key difference lies in the objectives and constraints of these two roles. Pentesters aim to identify and remediate vulnerabilities proactively, whereas hackers may exploit them for nefarious purposes. Hackers are not bound by ethical or legal boundaries, and their motivations can vary widely. This contrast underscores the importance of proactive security measures, including fuzzing, to bolster defenses and reduce the likelihood of malicious exploitation.
In essence, fuzzing is a critical part of a robust cybersecurity strategy, aiding in the discovery and remediation of software, and web vulnerabilities. While it may be time-intensive, its proactive nature helps organizations stay one step ahead of potential attackers. By investing in fuzzing and other security testing methodologies, executing a comprehensive lifecycle approach that encompasses both the discovery and swift remediation of vulnerabilities. To achieve this, it is imperative to assemble a dedicated team of experts specializing in offensive security, working in tandem with another team well-versed in defensive measures, commonly referred to as the “blue team.” This collaborative effort ensures a proactive and responsive defense strategy, effectively identifying and addressing potential weaknesses in the digital infrastructure, thereby safeguarding the organization against evolving threats.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]