Essential Skills Every Hacker Should Master

Reading Time: 8 Minutes
Introduction
With increased dependence on digital systems and the Internet, the surface of cyber threats and attacks expands. The high threat level further underscores the role played by hackers—not only as adversaries but as security defenders. Ethical hackers lead the charge in identifying and addressing vulnerabilities that can cause data breaches, financial losses, and even national security risks.
The objective of this article is to provide a comprehensive overview of the essential skills every hacker must master to excel in the field of offensive security. Whether you are an aspiring ethical hacker looking to enter the industry or an experienced professional seeking to sharpen your skills, understanding the core competencies required is crucial. By mastering these skills, you can effectively identify, analyze, and neutralize potential threats, thereby contributing to a safer and more secure digital world.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Scripting and Programming
Proficiency in scripting and programming languages is a cornerstone for any hacker.
Here’s a closer look at the essential languages and why they are critical:
Python
- Overview: Bash is the default shell for Unix-based systems like Linux, which are widely used in hacking environments.
- Practical use: Bash scripting is vital for automating system tasks, managing files, and executing command sequences efficiently. It is particularly useful for creating scripts that automate repetitive tasks, thereby saving time and reducing errors.
Bash
- Overview: Bash is the default shell for Unix-based systems like Linux, which are widely used in hacking environments.
- Practical use: Bash scripting is vital for automating system tasks, managing files, and executing command sequences efficiently. It is particularly useful for creating scripts that automate repetitive tasks, thereby saving time and reducing errors.
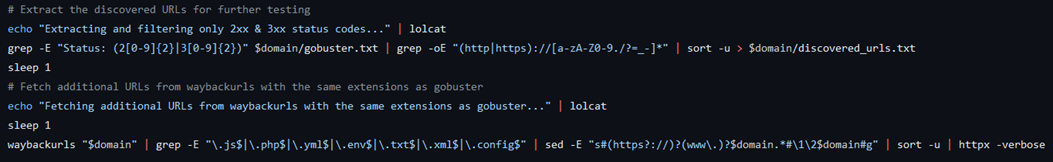 Example of Bash Script, Snipped Code from BHEH tool SecretOpt1c
Example of Bash Script, Snipped Code from BHEH tool SecretOpt1c
JavaScript
- Overview: JavaScript is the go-to language for web development, making it essential for understanding and exploiting web applications.
- Practical use: Proficiency in JavaScript allows hackers to manipulate web pages, identify and exploit client-side vulnerabilities such as Cross-Site Scripting (XSS), and craft sophisticated web attacks. Understanding JavaScript is also crucial for developing and debugging web-based payloads.
SQL
- Overview: SQL (Structured Query Language) is the standard language for interacting with databases, making it crucial for both web and data-driven hacking.
- Practical use: Knowledge of SQL is essential for identifying and exploiting SQL injection vulnerabilities, one of the most common and dangerous types of web application vulnerabilities. Hackers use SQL to manipulate database queries, extract sensitive information, and gain unauthorized access to databases. Mastery of SQL allows hackers to craft precise injection attacks, bypass authentication mechanisms, and even alter or delete data within a database.
Networking
Understanding of Networking Protocols and Concepts
A deep understanding of networking protocols and concepts is essential for any hacker. This includes a comprehensive grasp of TCP/IP, DNS, subnetting, packet analysis, and configuring firewalls and VPNs.
TCP/IP (Transmission Control Protocol/Internet Protocol):
- Overview: TCP/IP is the foundational suite of communication protocols used for the internet and other networks. Understanding how data is transmitted across networks, how connections are established and terminated, and the nuances of data encapsulation and packet structure is crucial.
- Practical Use: Knowledge of TCP/IP helps in analyzing and manipulating network traffic, identifying vulnerabilities in network protocols, and crafting custom packets for attacks such as TCP SYN flood and IP spoofing.
UDP (User Datagram Protocol):
- Overview: UDP is a simpler, connectionless protocol compared to TCP, used for applications where speed is critical and error correction is less important.
- Practical Use: Understanding UDP is important for analyzing network traffic in real-time applications like video streaming, gaming, and VoIP, and for exploiting vulnerabilities in protocols that use UDP.
Identifying Internal and External IP Addresses:
- Overview: IP addresses are critical identifiers used to locate devices on a network. Internal IP addresses (private) are used within a local network, while external IP addresses (public) are used on the broader internet. Understanding how to identify and differentiate between these IP addresses is fundamental for network configuration, reconnaissance, and planning attacks or defenses.
Internal IP Addresses:
- Definition: IP addresses are critical identifiers used to locate devices on a network. Internal IP addresses (private) are used within a local network, while external IP addresses (public) are used on the broader internet. Understanding how to identify and differentiate between these IP addresses is fundamental for network configuration, reconnaissance, and planning attacks or defenses.
- Identification: Internal IP addresses can be identified using tools like ipconfig on Windows, ifconfig or ip addr on Linux, or through router configurations. These IPs are assigned by DHCP servers within the local network.
- Practical Use: Knowing internal IPs helps hackers map out the network topology, identify potential targets within the network, and conduct lateral movement during an attack.
External IP Addresses:
- Definition: External IP addresses are routable on the internet and are assigned by ISPs. They are used to identify devices on a global scale.
- Identification: External IP addresses can be identified by querying online services like whatismyip.com, using the curl ifconfig.me command in a terminal, or checking the WAN status on a router’s web interface.
- Practical Use: Knowing external IPs helps hackers determine the entry points into a network from the internet, conduct reconnaissance, and plan attacks like DDoS or port scanning.
DNS (Domain Name System)
- Overview: DNS translates domain names to IP addresses, enabling users to access websites using human-readable names. Understanding DNS is critical for recognizing and exploiting vulnerabilities like DNS spoofing and DNS cache poisoning.
- Practical Use: Hackers use DNS knowledge to redirect traffic, intercept communications, and perform reconnaissance on targets.
Subnetting
- Overview: Subnetting involves dividing a network into smaller, manageable sub-networks. It is important for efficient IP address allocation and network management.
- Practical Use: Proficiency in subnetting allows hackers to understand network topologies, identify potential targets within a network, and avoid detection by staying within certain IP ranges.
Packet Analysis
- Overview: Packet analysis involves examining data packets transmitted over a network to diagnose network issues or detect malicious activity.
- Practical Use: Tools like Wireshark enable hackers to capture and analyze network traffic, identify suspicious packets, and uncover vulnerabilities in network protocols.
Configuring Firewalls and VPNs
- Overview: Firewalls control incoming and outgoing network traffic based on predetermined security rules, while VPNs (Virtual Private Networks) provide secure communication channels over the internet.
- Practical Use: Understanding how to configure and bypass firewalls and VPNs is essential for network security testing. Hackers often need to test firewall rules and VPN configurations to identify weaknesses and potential entry points.
Web Protocols (HTTP/HTTPS):
HTTP Methods:
- Overview: HTTP methods such as GET, POST, PUT, and DELETE are used to perform various actions on web servers. Each method serves a specific purpose in web communication.
GET: Used to retrieve data from a server.
POST: Used to send data to a server to create or update resources.
PUT: Used to update or create a resource on a server.
DELETE: Used to delete a resource on a server.
- Practical Use: Understanding these methods is crucial for web application testing, including finding vulnerabilities such as insecure direct object references, parameter tampering, and cross-site scripting (XSS).
Linux Proficiency
Operating Systems
Mastery of Linux, particularly distributions tailored for security testing like Kali Linux and Parrot OS, is a fundamental skill for any hacker. These distributions are designed to provide a comprehensive suite of tools for penetration testing, digital forensics, and security research.
Kali Linux:

Kali Linux OS Interface 2024
- Overview: Kali Linux is a Debian-based distribution that comes pre-installed with hundreds of tools used for penetration testing and security research.
- Key Features: It includes tools for network analysis, web application testing, database assessment, password attacks, and more. Kali supports live booting from USB, which is useful for testing on different hardware without installation.
Parrot OS:
- Overview: Parrot OS is another Debian-based distribution focused on security, privacy, and development.
- Key Features: It includes tools for penetration testing, digital forensics, reverse engineering, and anonymous web browsing. Parrot OS is known for its lightweight nature and ease of use.
Command-Line Interfaces
- Overview: The command line is the primary interface for interacting with Linux. Proficiency in using command-line interfaces (CLI) is crucial for efficiently managing and operating Linux systems.
- Key Commands: Important commands include ls, cd, cp, mv, rm, chmod, chown, ps, kill, grep, find, and tar. Mastery of these commands enables effective file management, process control, and system navigation.
File Systems and Permissions
- Overview: Understanding the Linux file system hierarchy, file types, and permissions is essential for system security and management.
- Key Concepts: This includes knowledge of directories like /etc, /usr, /var, /home, and /tmp, and file permission management using chmod, chown, and chgrp.
Shell Scripting
- Overview: Writing shell scripts in Linux automates tasks, manages system operations, and creates custom hacking tools.
- Key Skills: Knowledge of scripting languages like Bash and Python is crucial. Understanding how to write scripts that interact with system commands, handle user input, and perform automated tasks can significantly enhance productivity.
See Also: Offensive Security Tool: Upload_Bypass
Ethical Hacking Tools Proficiency
Proficiency with a range of ethical hacking tools is essential for performing effective penetration testing and vulnerability assessments. These tools are designed to identify, exploit, and document security weaknesses in systems and applications.
Here’s an expanded look at some of the most critical tools and their applications:
Metasploit
Metasploit is one of the most widely used penetration testing frameworks. It provides a comprehensive suite of tools for discovering, exploiting, and validating vulnerabilities.
Key Features:
- Exploitation Modules: Metasploit includes hundreds of pre-built exploit modules for various vulnerabilities, making it easier to test and demonstrate security flaws.
- Payloads: It offers customizable payloads for delivering exploits and establishing control over compromised systems.
- Auxiliary Modules: These modules perform functions such as scanning, sniffing, and brute-force attacks.
- Meterpreter: A powerful payload that provides an interactive shell and numerous post-exploitation features.

Mastering Browser Exploitation Sophisticated Attacks with Metasploit and BeEF Framework – A Patreon exclusive episode from our Patreon page
Nmap (Network Mapper)
Nmap is a versatile and powerful network scanning tool used to discover hosts, services, and vulnerabilities within a network.
Key Features:
- Host Discovery: Identifies live hosts on a network using techniques like ICMP echo requests and TCP SYN scans.
- Port Scanning: Determines open ports on a host, which can indicate potential entry points for attacks.
- Service and Version Detection: Identifies running services and their versions to pinpoint vulnerabilities.
- OS Detection: Determines the operating system of a target machine.
- Scripting Engine: Allows for the execution of custom scripts to detect specific vulnerabilities and gather more detailed information.
Wireshark
Wireshark is a leading network protocol analyzer that allows users to capture and interactively browse the traffic running on a computer network.
Key Features:
- Packet Capture: Captures network packets in real-time for detailed analysis.
- Protocol Decoding: Supports hundreds of protocols, providing detailed information about each packet.
- Filters: Allows for the application of filters to isolate specific types of traffic or packets of interest.
- Statistics: Provides various statistical tools to analyze network traffic patterns and identify anomalies.
Burp Suite
Burp Suite is a comprehensive platform for web application security testing. It includes tools for performing automated and manual testing.
Key Features:
- Intercepting Proxy: Captures and modifies HTTP/S traffic between the browser and web servers.
- Scanner: Automatically scans web applications for common vulnerabilities like SQL injection, XSS, and CSRF.
- Intruder: A powerful tool for automating customized attacks, such as brute-force and fuzzing.
- Repeater: Allows for manual testing by repeating and modifying individual HTTP requests.
- Extensibility: Supports plugins to extend its functionality, including integrations with other tools and custom scripts.
Additional Tools
Hydra
- Overview: A fast and flexible password-cracking tool that supports numerous protocols.
- Practical Use: Used to perform brute-force attacks against various services, such as HTTP, FTP, and SSH, to test the strength of passwords.
Aircrack-ng
- Overview: A suite of tools for auditing wireless networks.
- Practical Use: Used to capture and analyze wireless traffic, crack WEP and WPA-PSK keys, and perform packet injection attacks.
Nikto
- Overview: An open-source web server scanner that detects various types of vulnerabilities.
- Practical Use: Used to scan web servers for outdated software, misconfigurations, and common security issues.
OpenVAS
- Overview: An open-source vulnerability scanner that identifies security issues in systems and applications.
- Practical Use: Used to perform comprehensive vulnerability assessments and generate detailed reports on security weaknesses.
Continuous Learning
Building the Hacker Mindset:
To become a true hacker, you must adopt a unique mindset, thinking creatively and differently. While you can study Cyber Security officially, Offensive Security and hacking are not typically taught due to concerns over misuse. Learning to hack isn’t about configuring firewalls; it’s quite the opposite. Embracing the hacker mentality requires significant effort to understand this mindset and the powerful capabilities it brings. Always remember to use these skills ethically, and it does take a certain type of people that become one.
Staying Updated
In the rapidly evolving field of hacking, continuous learning is not just beneficial—it’s essential. Staying current with new vulnerabilities, emerging security trends, and the latest hacking tools ensures that hackers can effectively protect systems and exploit weaknesses.
Importance of Staying Current
New Vulnerabilities:
- Overview: Cyber threats are constantly evolving, with new vulnerabilities discovered daily. Staying informed about these vulnerabilities is critical to mitigating potential risks.
- Practical Use: Ethical hackers who stay updated can quickly identify and respond to new threats, ensuring that their security measures remain effective against the latest exploits.
Security Trends:
- Overview: The cybersecurity landscape is shaped by trends such as shifts in attack vectors, advancements in defensive technologies, and changes in regulatory requirements.
- Practical Use: Understanding these trends helps hackers anticipate future challenges, adapt their strategies, and implement cutting-edge security practices.
New Hacking Tools:
- Overview: New tools and techniques are continually developed to exploit vulnerabilities and improve security testing methods.
- Practical Use: Familiarity with the latest tools enables hackers to enhance their skill set, automate complex tasks, and improve the efficiency and effectiveness of their assessments.
Understanding CVEs and Vulnerability Details:
- Overview: CVEs (Common Vulnerabilities and Exposures) are standardized identifiers for publicly known cybersecurity vulnerabilities. Each CVE entry includes an identification number, a description of the vulnerability, and references to advisories and patches. Understanding CVEs is crucial for assessing the security posture of systems and prioritizing remediation efforts.
Interpreting CVE Entries:
- Structure: A typical CVE entry includes a unique identifier (e.g., CVE-2024-12345), a description of the vulnerability, its impact, and references to patches or mitigations.
- Severity: CVEs often include a CVSS (Common Vulnerability Scoring System) score, which quantifies the severity of the vulnerability based on factors like exploitability and impact.
Practical Use:
- Vulnerability Assessment: Hackers use CVEs to identify and understand known vulnerabilities in target systems. This helps in crafting specific exploits or determining if existing exploits are available.
- Penetration Testing: During penetration tests, ethical hackers use CVE databases to ensure they cover all known vulnerabilities in the scope of their assessment.
- Exploit Development: Understanding the details of a CVE can aid in developing custom exploits or modifying existing ones to bypass security measures.
Resources for Continuous Learning
To stay updated, hackers should regularly engage with various educational resources. These resources provide valuable information on the latest developments in cybersecurity:
Blogs:
- Krebs on Security: Written by cybersecurity expert Brian Krebs, this blog provides insights into major security breaches, vulnerabilities, and trends.
- Dark Reading: Offers news and analysis on a wide range of security topics, from vulnerabilities to advanced threat defense.
- Schneier on Security: Bruce Schneier’s blog covers broad security issues, providing deep insights and expert opinions.
- Black Hat Ethical Hacking: Our website includes blogs that cover offensive security issues, write-ups, articles and the latest news.
Screenshot demonstrating a part from a BHEH article “Post-Exploitation Techniques: Maintaining Access, Escalating Privileges, Gathering Credentials, Covering Tracks” . This example shows a Meterpreter session established on a target system.”
Forums:
- Hack The Box (HTB): A platform that includes forums where users discuss challenges, share knowledge, and collaborate on penetration testing exercises.
- Reddit: Subreddits like r/netsec and r/hacking are valuable for discussions, news, and learning resources related to cybersecurity.
- Stack Overflow: A go-to resource for programming and scripting questions, which is crucial for developing and troubleshooting hacking tools.
Security Conferences
- DEF CON: One of the world’s largest hacker conventions, featuring talks, workshops, and competitions on various cybersecurity topics.
- Black Hat: A leading information security conference that provides technical training and deep dives into the latest vulnerabilities and defenses.
- RSA Conference: Focuses on both current and future trends in cybersecurity, offering sessions from industry leaders and experts.
Engaging with the Hacker Community
Actively participating in the hacker community is a valuable way to stay informed and improve skills. Engaging with others fosters knowledge sharing, collaboration, and professional growth:
GitHub:
- Overview: GitHub is a platform for collaborative software development, hosting numerous open-source projects, including many related to cybersecurity.
- Practical Use: Hackers can contribute to or learn from repositories containing tools, scripts, and educational resources. Engaging with projects on GitHub helps in understanding new techniques and tools.
Twitter/X
- Overview: Twitter is a dynamic platform where many cybersecurity experts and organizations share real-time updates, news, and insights.
- Practical Use: Following prominent security researchers, organizations, and hashtags (e.g., #infosec, #cybersecurity) keeps hackers informed about the latest developments and trends.
- Overview: Reddit hosts a variety of communities focused on cybersecurity, offering discussions, resources, and advice.
- Practical Use: Subreddits like r/netsec, r/hacking, and r/AskNetsec provide platforms for asking questions, sharing knowledge, and discussing current security issues and techniques.
Discord Servers:
- Hacker101 Discord: A community associated with HackerOne, offering support, discussions, and challenges for security researchers.
- Black Hat Ethical Hacking Discord: Our community focused on offensive security, offering support, discussions and updates on the latest trends and tools.
- Null Byte Discord: A community focused on ethical hacking and cybersecurity, offering tutorials, advice, and collaboration opportunities.
- Practical Use: Joining Discord servers enables hackers to engage with a community of like-minded individuals, share knowledge, and collaborate on projects. These servers often provide real-time support and updates on the latest trends and tools.
Practical Steps for Continuous Learning
Hands-On Practice:
Regularly participate in Capture The Flag (CTF) competitions, labs, and other hands-on activities that challenge and improve your hacking skills. Participating in bug bounty programs allows hackers to practice their skills on real-world systems, earn rewards, and gain recognition within the cybersecurity community.
Courses and Certifications:
- BHEH Courses: We offer comprehensive courses such as our Offensive Security and Ethical Hacking Course, and our Bug Bounty Hunting Course. These courses cover a wide range of topics, from learning Linux and reconnaissance techniques to executing attacks and mastering post-exploitation strategies. Our courses are designed to provide you with the practical skills and theoretical knowledge needed.
- Certified Ethical Hacker (CEH): Provides foundational knowledge in ethical hacking and security testing.
- Offensive Security Certified Professional (OSCP): Offers advanced training in penetration testing and requires a rigorous hands-on exam.
The Bug Bounty course description from BHEH
Bug Bounty Programs
Participating in bug bounty programs allows hackers to practice their skills on real-world systems, earn rewards, and gain recognition within the cybersecurity community.
Platforms:
- HackerOne: Connects hackers with companies to find and report security vulnerabilities.
- Bugcrowd: Provides a marketplace for security researchers to participate in bug bounty programs.
- Synack: Offers a platform for vetted security researchers to find vulnerabilities in enterprise-level systems.
Online Learning Platforms
- Overview: PortSwigger’s Web Security Academy offers free, interactive labs that teach web security concepts. The labs cover a wide range of topics, from SQL injection to cross-site scripting (XSS).
- Practical Use: These labs provide hands-on experience with real-world vulnerabilities, helping you develop and refine your web application security skills.
- Overview: In addition to CTF challenges, HTB offers an Academy with structured learning paths and courses focused on various aspects of penetration testing and cybersecurity.
- Practical Use: The interactive labs and exercises allow you to apply your knowledge in realistic scenarios, enhancing your practical skills.
From scripting and programming in languages like Python, Bash, JavaScript, and SQL to understanding networking protocols and mastering Linux, these skills form the foundation of effective hacking. Proficiency with ethical hacking tools like Metasploit, Nmap, Wireshark, and Burp Suite is essential for conducting thorough penetration testing and vulnerability assessments. Additionally, continuous learning through daily reading, hands-on practice, and engaging with the hacker community ensures you stay current with emerging trends and techniques.
By committing to continuous learning and skill development, you can significantly contribute to creating a safer and more secure digital world, staying ahead of potential threats, and advancing your career.
The pursuit of excellence in ethical hacking demands a blend of technical proficiency, practical application, and continuous learning. Embrace these principles to make a meaningful impact in the world of offensive security.
We hope that this write up has taught you something new. If you enjoyed it, the best way that you can support us is to share it! If you’d like to hear more about us, you can find us on LinkedIn, Twitter, YouTube.
Are you a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]