Red Team Tactics to uncover hidden Secrets on Websites

Reading Time: 4 Minutes
Introduction
Many companies already have a lot of security layers that can make it more difficult to bypass them. From a defensive perspective, this is great you may think.
Starting from Cloudflare WAF, then to the next-generation firewall, their combination makes it more difficult for the attacker to get into the network of a company using commercial techniques and tools.
Hacking it’s not about how much expensive is the tool or the machine, it’s about the time you spent and the experience you have with how things work.
Forex trade companies, banks, and similar companies they at risk, using many API Keys from payment solutions providers to give you more solutions for payment transition, keys may leak from any organization in numerous ways.
Developers of each company add secrets into their code for many reasons. The secret could be a unique identifier that authenticates requests associated with your project for usage and billing purposes.
Properly transferring secrets to a web application using a secret vault software can be complicated, and it can also make debugging difficult in later stages. In those cases, firewalls, will never stop hackers to find API keys, access tokens, authorizations, JSON Web Token, etc.
Secrets are highly valued, but can also be dangerous in the wrong hands. In most cases developers forgot even after the production stage has finished removing the label name and password, giving the ability to the attacker to know the source of the API key and easily perform a callback success. If no label exists, the attacker has challenges finding the source of that API to perform the necessary actions correctly.
That’s why offense is always the best defense, by performing penetration testing to find and fix the vulnerabilities before the bad guys do.
Prerequisites
SecretFinder: is a python script based on Linkfinder, to discover sensitive data such as API keys, access tokens, and authorization JSON Web Token in JavaScript files using jsbeautifier in combination with a large list of regular expressions that are responsible to search for and identify sensitive information within JavaScript files.
Hakrawler: Fast and simple web crawler to quickly discover endpoints and link gathering from JavaScript files.
Burp Suite: is a dynamic web application security tool developed by PortSwigger, used by many penetration testers and bug bounty hunters, providing you good reporting capabilities.
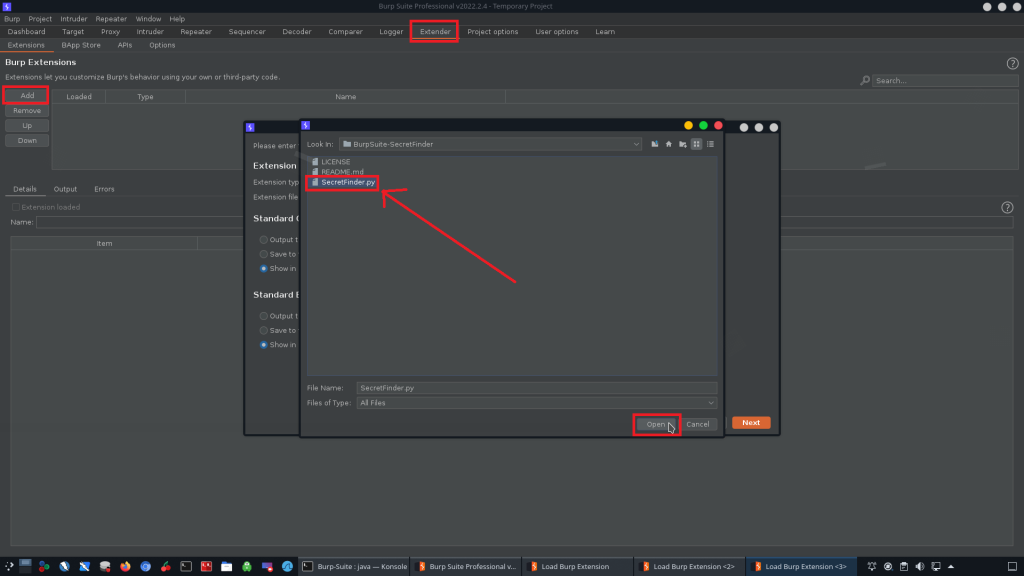
The Role at this example we will show, how to add the SecretFinder extension into the Burp Suite as an add-on tool, by doing that you have a better view of the scope. Manage and analyze vulnerabilities easily in one place.
Note: Make sure to setup a Jython runtime environment that allows you to enable adding the extension.
- Visit Jython and download the latest version Jython standalone JAR file.
- In Burp Suite, go to Extender ➡️ Options. Under the section Python Environment, click Select file. Navigate to the saved location and click on the download Jython JAR file.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Technical part:
In this scenario, we will see how to use Hakrawler, which is a tool written in GO to perform fast web crawler for gathering URLs and JavaScript endpoints combined with SecretFinder to detect secrets.
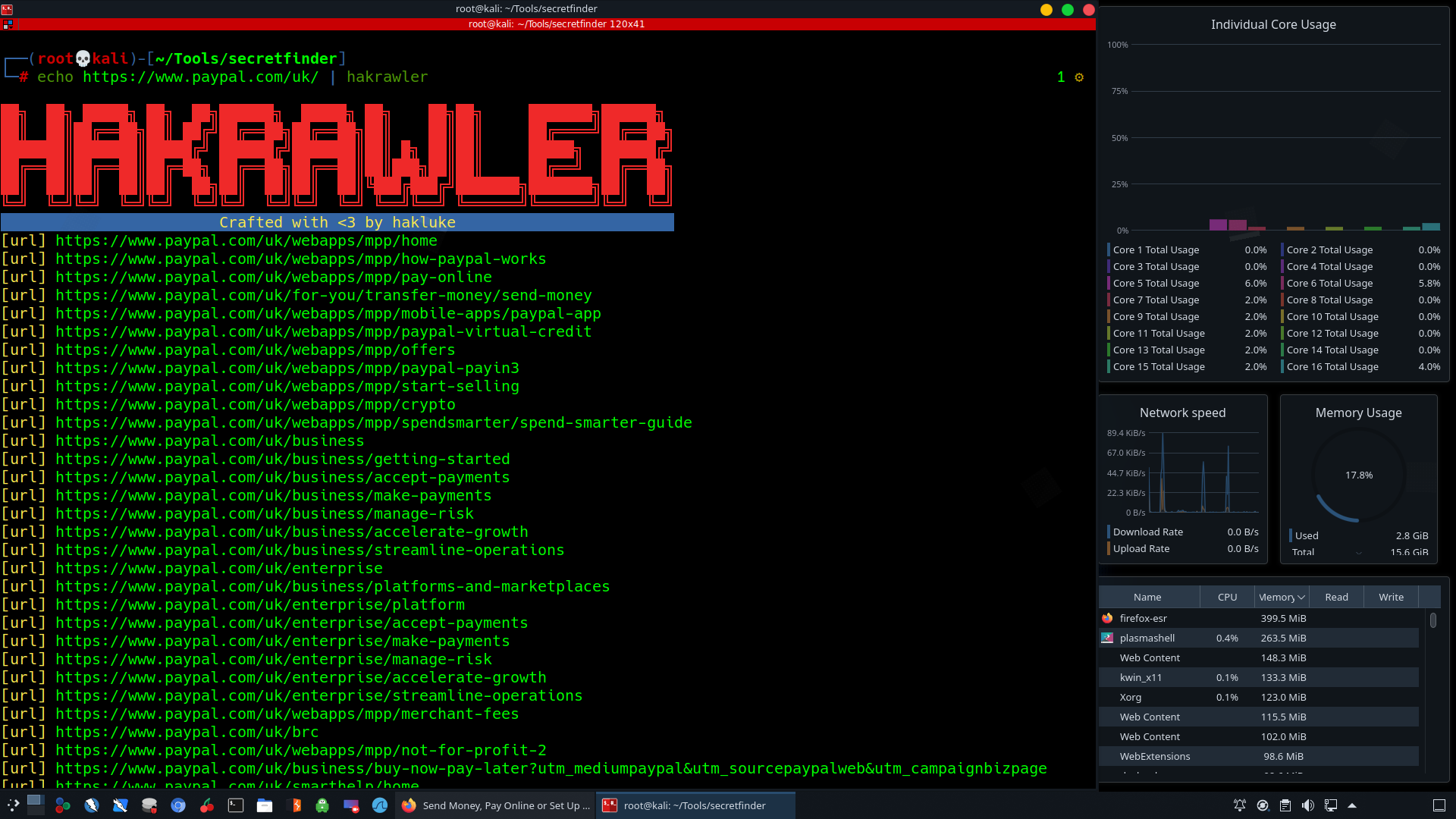
Hakrawler performing web crawler for gathering URLs and JavaScript’s.
echo https://www.paypal.com/uk | hakrawler
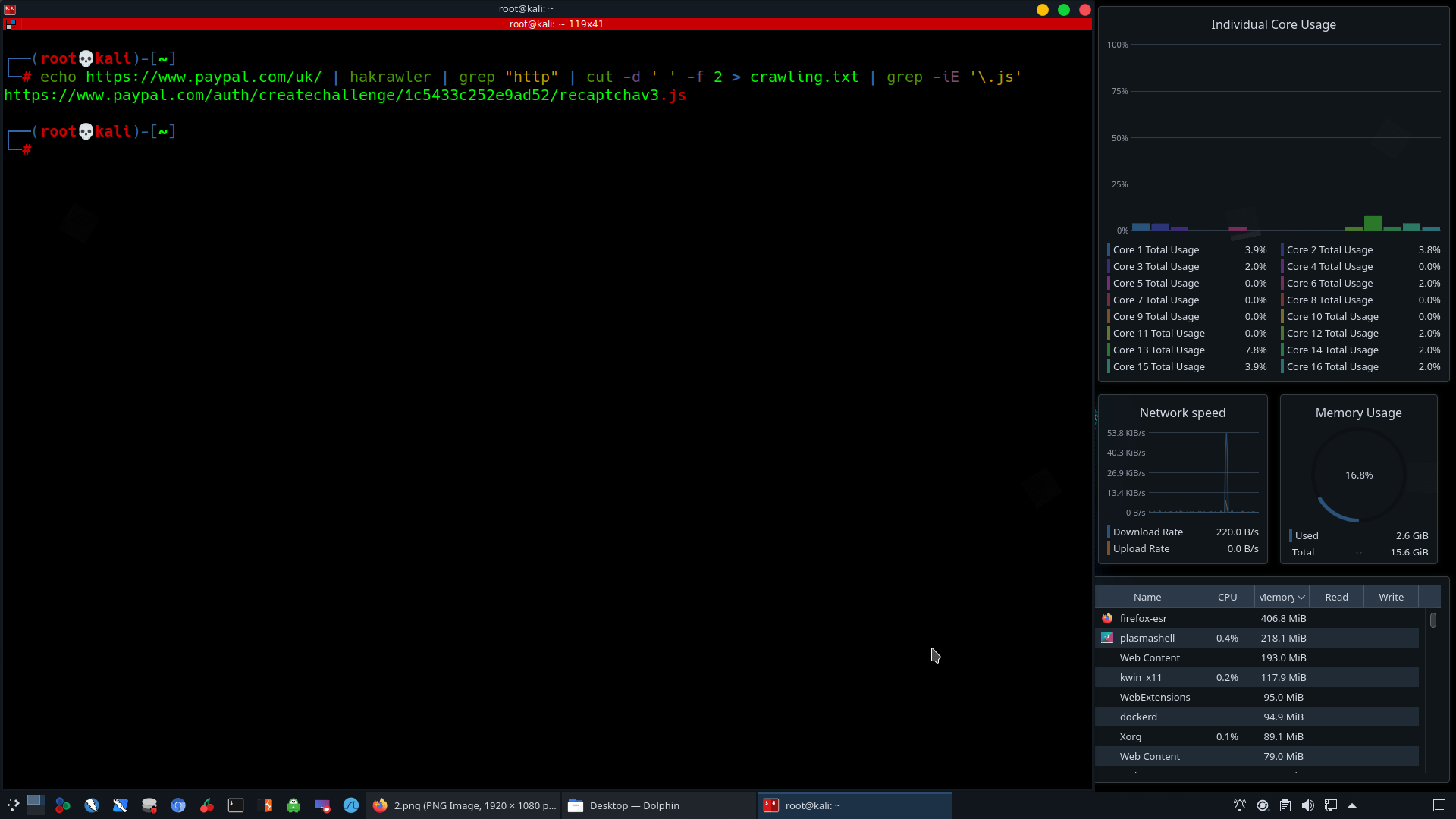
One-Liner command to gather JavaScript links.
echo https://www.paypal.com/uk | hakrawler | grep “http” | cut –d ˈ ˈ –f 2 > crawling.txt | grep –iE ˈ\\.jsˈ
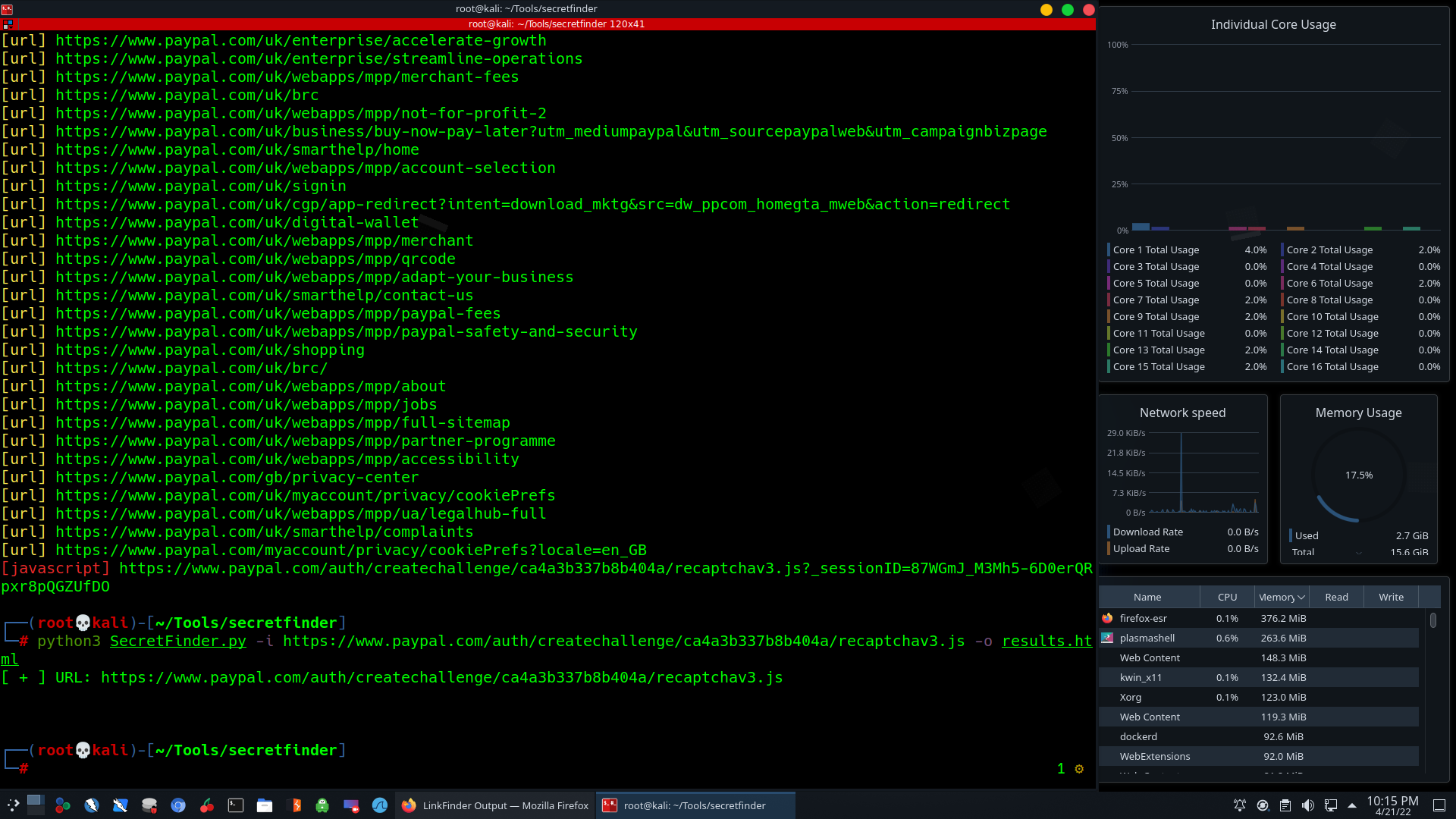
Performing SecretFinder script to discover sensitive data in JavaScript links.
python3 SecretFinder.py –i <target_url_link> -o results.html
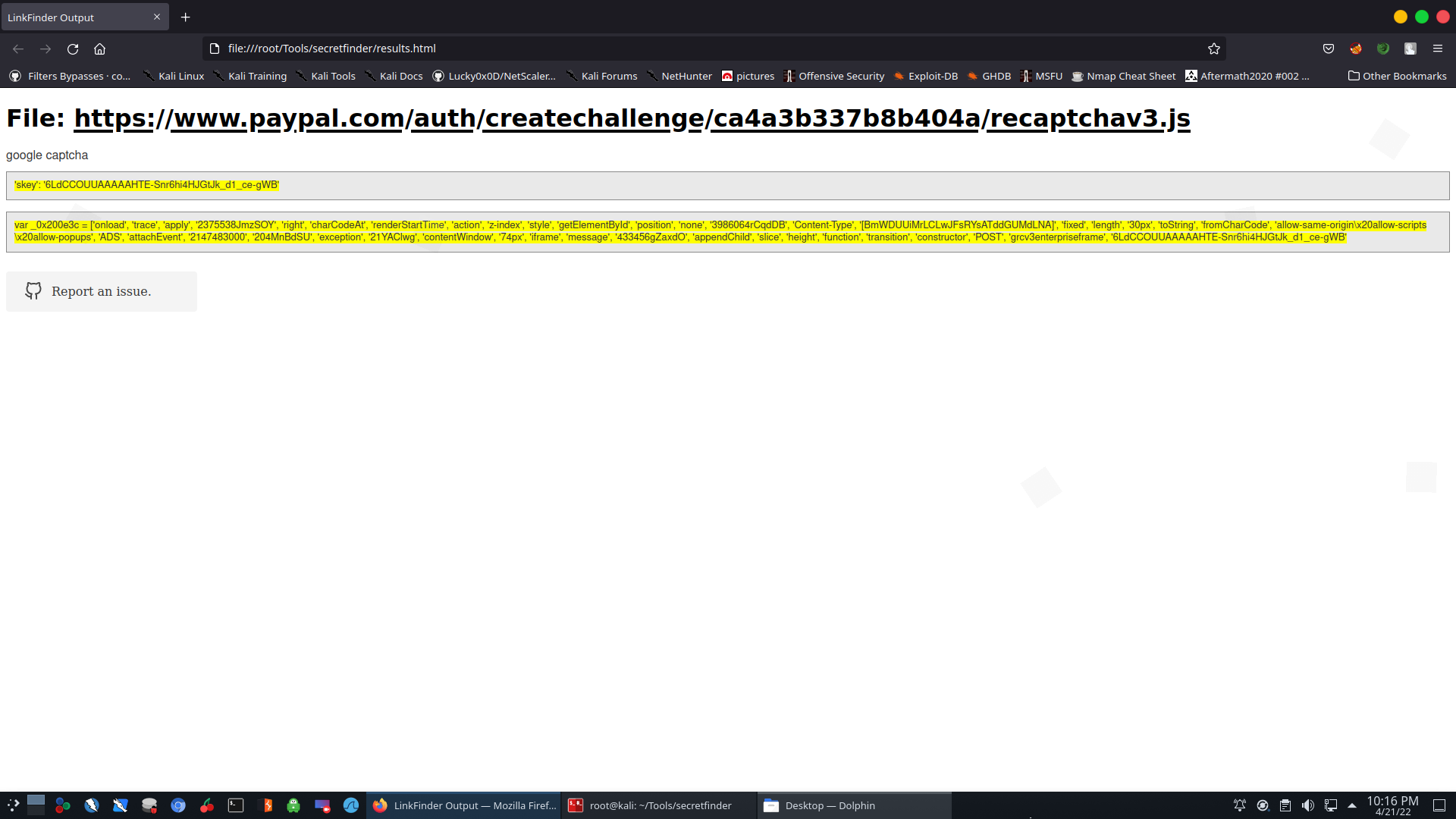
SecretFinder, you can add it easily into your Burp Suite Pro extension tools to discover juicy information about API key/tokens from HTTP response using regular expressions. Saving tons of tedious efforts for inspecting the whole lot of files manually.
Conclusion:
In conclusion, SecretFinder is a great tool that saves tons of time and effort to detect secret keys/tokens but it’s not enough to run the tool. You need first to have JavaScript links, using web crawling techniques for example hakrawler, with customized one-liner code to filter the result, bringing you the juicy stuff actively. By doing this you have a clear picture of JavaScript links to scan for secrets using SecretFinder. Although SecretFinder contains different regular expressions to look into your target manually for a specific result. Also, you have the ability to edit SecretFinder.py and add regular expressions you want to build from your experience.
At the end of the day, it doesn’t matter what tool or method you will use, but the critical thinking on how to approach the target.
Note: Watch this writeup in live demonstration by joining our Patreon Channel below:
Disclaimer
The content of this article is provided for educational purposes only. The information and tools discussed are intended to demonstrate security testing techniques and should only be used in a lawful and ethical manner. The authors and publishers of this article are not responsible for any misuse of the information provided. Readers are advised to seek proper authorization before attempting any security testing.
We hope that this write up has taught you something new. If you enjoyed it, the best way that you can support us is to share it! If you’d like to hear more about us, you can find us on LinkedIn, Twitter, YouTube.
Are you a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]