Darkside hacker group, the group that provides ransomware as a service

Reading Time: 6 Minutes
Introduction
DarkSide hacker group provides ransomware as a service, and it is believed to be responsible for the Colonial Pipeline cyberattack, the biggest US gas pipeline, which was temporarily shut down its operations for several days due to the attack.
DarkSide is one of many increasingly professionalized groups of digital extortionists.
DarkSide group
DarkSide is a ransomware-as-a-service (RaaS) and offers its affiliates a percentage of the profits.
It presents an example of modern ransomware, operating with a more advanced business model. These modern ransomware attacks usually are done by several groups who collaborate and split the profits.
It is believed that the DarkSide group is based in Eastern Europe, likely Russia. Unlike other hacking groups responsible for high-profile cybercrimes, it is not believed to be state-sponsored.
Experts in the field who tracked DarkSide activities said it appears to be composed of veteran cyber criminals with a focus on making money from their targets.
“They’re very new but they’re very organized,” Lior Div, the chief executive of Boston-based security firm Cybereason said.
Their site on the dark web hints at their past crimes, claiming that they previously made millions from extortion. It also features a Hall of Shame-style gallery of leaked data from victims who haven’t paid up their ransom, disclosing stolen documents from more than 100 companies across the US and Europe.
Targets
Based on the group’s Tor leak sites, the DarkSide group determines whether to pursue a target by looking at their financial records. The financial information gathered is also used to determine the amount of the ransom to demand, a typical ransom could be anywhere between 200K and 2 million US dollars.
According to Trend Micro reports, the most targeted country, with more than 500 detections was the US, followed by Belgium, France, and Canada. Also, according to McAfee, the most attacked countries In terms of the number of devices impacted per million devices are Israel with 1573.28, Malaysia with 130.99, Belgium with 106.93, etc., the list consists of 25 affected countries which also includes countries like Italy, Ukraine, and Peru.
Notably, the group avoids victimizing companies in a Commonwealth of Independent States (CIS) countries by using a part of their ransomware execution code that checks the geolocation of potential victims. This could be a clue to where DarkSide criminals are residing. Additionally, they do not target schools, non-profit organizations, and healthcare centers Organizations.
As of June 2021, based on the leaked sites, there were at least 90 victims affected by the DarkSide attacks. In total, more than 2TB of stolen data are currently being hosted on DarkSide sites and 100% of victims’ stolen files are leaked.
History of Attacks
The Timeline of DarkSide activity is compiled from publicly available reports:
- August 2020: DarkSide introduces its ransomware.
- October 2020: DarkSide donates US$20,000 stolen from victims to charity.
- November 2020: DarkSide establishes its RaaS model. The group invites other criminals to use its service. A DarkSide data leak site is later discovered.
- November 2020: DarkSide launches its content delivery network (CDN) for storing and delivering compromised data.
- December 2020: A DarkSide actor invites media outlets and data recovery organizations to follow the group’s press center on the public leak site.
- March 2021: DarkSide releases version 2.0 of its ransomware with several updates.
- May 2021: DarkSide launches the Colonial Pipeline attack.
The attack on the Colonial Pipeline was unprecedented at the time as it caused the biggest US gas pipeline to be temporarily shut down its operations for several days. The Colonial Pipeline was the main pipeline supplying 45% of fuel to the East coast of the US.
DarkSide successfully extorted about 75 Bitcoin (around US$5 million at the time). After the attack, Darkside announces it is apolitical and will start vetting its targets (possibly to avoid raising attention to future attacks).

US Colonial pipeline
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
Mechanism of attacks – ransomware
The group uses common, legitimate tools (Cobalt Strike, Mimikatz, Metasploit, etc.) throughout the attack process to remain undetected.
Initial Access
To gain initial access, the group uses various tactics such as phishing, remote desktop protocol abuse, and exploiting known vulnerabilities.
Throughout the reconnaissance and gaining entry phases multiple tools are used for specific purposes:
- PowerShell: for reconnaissance and persistence
- Metasploit Framework: for reconnaissance
- Mimikatz: for reconnaissance
- BloodHound: for reconnaissance
- Cobalt Strike: for installation
Lateral movement and privilege escalation
In general, this is a key discovery phase in the modern ransomware process where the goal is to identify all critical data (file targets, locations for the exfiltration, and encryption process) within the victims’ organization.
The goal of the DarkSide threat actors in the lateral movement is to gain access to Domain Controller (DC) or Active Directory, which will be used to steal credentials, escalate privileges, and any other valuable assets for the exfiltration.
Eventually, using the DC network share to deploy the ransomware to connected devices.
Data Exfiltration
It’s the last step before the ransomware is dropped on the system.
This is the riskier step in the process of ransomware execution. That’s why data exfiltration is more likely to alert the victim organization’s security department.
Tools used by DarkSide for the data exfiltration :
- 7-Zip: a utility used for archiving files in preparation for exfiltration
- Rclone and Mega client: tools used for exfiltrating files to cloud storage
- PuTTy: an alternative application used for network file transfer
The attackers then use various leak sites on the Tor network to host the stolen data.
Execution
The ransomware then gets executed and performs various actions. It checks that the victim is not located in a CIS country, stores the ransom note, and executes a PowerShell command to install and operate itself along with deleting the shadow copies from the network.
It uses two encryption techniques depending on the targets’ operating system (Linux or Windows), a ChaCha20 stream cipher with RSA-4096 for Linux and a Salsa20 with RSA-1024 for Windows machines.
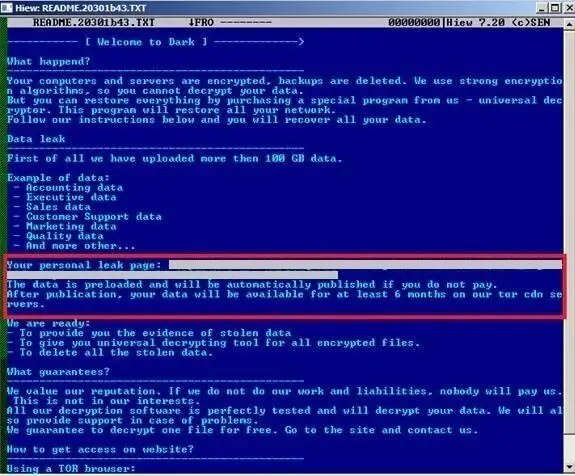
A sample ransom note from DarkSide’s ransomware:
Conclusion:
After the Colonial Pipeline attack, DarkSide released a statement on one of its leak sites clarifying that the group did not wish to create problems for society and that its goal was simply to make money.
After the attacks, the group went silent, presumably for all the attention it caused but likely reemerged as a group that called themselves BlackMatter around September 2021.
Since November 2021, the US State Department has offered a reward of up to 10 million dollars for anyone who has information that will help identify or locate the DarkSide members and a reward of up to 5 million dollars for information leading to the arrest or conviction of any party that attempted or participate in the DarkSide ransomware attacks.
These kinds of attacks remind us those threat actors are always a step ahead regarding cybersecurity. Offensive security needs to be implemented now more than ever.
Offensive security solutions include testing your company against such attacks.
Testing your company’s infrastructure against ransomware attacks and setting up backup plans are essential tools to survive on the Internet “jungle”, where hackers are waiting to take advantage of every small opportunity for their profit.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
References:
⦿ Who are DarkSide Hacker Group?
⦿ The US Puts a $10M Bounty on DarkSide Ransomware Hackers
⦿ Cyber attack on US fuel pipeline operator blamed on DarkSide, a ‘Robin Hood’ criminal gang
⦿ What We Know About the DarkSide Ransomware and the US Pipeline Attack – TrendMicro
⦿ DarkSide (hacker group) – Wikipedia









