Xbox Underground

Reading Time: 6 Minutes
David Pokora, from being an enthusiastic Xbox gamer to be the leader of Xbox-Underground, a gaming hacker group that hacked into gaming companies’ software and even tried to sell their own Xbox One, years before the Xbox One console was even available for selling.
Early Years
Long before the Xbox was even released, in 1995, at just 3 years old, David Pokora, was mastering first-person shooter games on his parent’s computer. He fell in love with gaming and became fascinated with the idea of the “magical” control that he was able to exercise playing video-games.
He was living with his family in Mississauga, a city in Ontario, Canada. He took some coding lessons throughout elementary school, creating basic programs and he was seen as a “born programmer”. Programming captured his attention ten years later during a family trip in a village in Poland. A place without WIFI and little else to do, he started learning Visual Basic (.NET programming). The experience of learning without access to the Internet made him hooked with programming, upon returning to his home he was flawless and ready to learn more.
As David was already diving into the waters of programming, his parents bought him his first Xbox. He spent countless hours playing his favorite game, that was Halo. As time passed, he wanted to learn more about the console, and he managed to find a hacker community who hacked into Xbox, tweaking its functionalities.

David Pokora - Image Credit: wired.com
Microsoft’s “kindergarten security.”
The hackers reverse-engineer the console and sniff data of communication between the processor, RAM, and the flash memory chip.
Cryptography expert, Bruce Schneier, called the discovery “kindergarten security.” Microsoft left the decryption key for booting the machine in the available memory area, this allowed downloading self-made programs on Xbox, making it transfer music, running Linux, and emulating other game consoles like Nintendo, the only necessary thing was to reflash the console.
As soon as he found out what he could do, David started tweaking things to his beloved Halo. He started chatting with hacker communities on IRC, learning things from how to change the physics of the game to fill out landscapes with digitized water or change the blue sky to rain.
The holy grail of Xbox hackers.
In 2005, the second generation of Xbox, Xbox-360, was released without the ridiculous security flaws of the previous version, ending the happy days for hackers who could no longer run code that was not approved by Microsoft. The only workaround at the time was a piece of equipment called the Xbox 360 development kit, known as Dev-kits.
Dev-kits are machines that were used by Microsoft developers to build the Xbox, they looked like regular consoles but they contained inside tools for game development, including debugging tools. This meant that in the hands of a hacker, a dev-kit could be used to manipulate the Xbox’s software and run code like an authorized programmer.
The dev-kits were extremely hard to find, Microsoft was sending them only to verified game development companies. In the mid-2000s some bankrupt companies were dumping the dev-kits in the recycling centers. This is where Rowdy Vav Cleve, a technology manager in California, and member of the hacker group Team Avalaunch found out about a nearby waste recycling center that was selling Xbox DVDs cheaply. Upon purchasing some equipment along with some motherboards, he installed one of the motherboards on his Xbox 360 and he was more than surprised when it booted the machine and the debug mode was activated. He stumbled upon the holy grail for all Xbox hackers.
He then persuaded the manager of the recycling center to purchase all the Xbox equipment from the trash. He stored some of the equipment in his house, sell to some buyers he trusted, and distributed some to his friends.
One of his trusted buyers was the 16 years old then David Pokora, who also help Van Cleve to sell some of the equipment acquired. He was able to make friendships with some of his customers, including a guy named Justin May, who lived in Delaware.
Pokora, as soon as he acquired his dev-kit, started cracking the new Halo 3 for hours every day, while his school grades were degrading, but on his mind, the only education that mattered was programming using the dev-kit.

Xbox 360 Devkits - Image Credit: old_engineer
He met Anthony Clark in a hackers’ forum, 18 years old hacker, who would be working together with David creating a tool for hacking Halo 3, adding unique abilities to the main character of the game. They received compliments from professional programmers when they posted online their work for Halo 3.
This was just the start of a darker story.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
By 2009, they use PartnerNet, (was a test environment for Xbox Live, and the only way to connect to it was via a whitelisted Xbox 360 dev-kit that they already had) to steal unreleased gaming software, including a Halo 3 map which they shared with friends. The next time they hacked to steal software they laughed when they notice a message left from Bungie engineers on the main screen: “Winners Don’t Break Into PartnerNet.” They saw no reason to stop playing with them because in their mind they didn’t do it for the riches but their love for the Xbox.
JTAG hack and the money opportunity
JTAG stands for The Joint Test Action Group, it was an industry body in the 80s that recommended the addition of contacts to all the printed circuit boards. The JTAG hack was named after them because of a weakness in the motherboard of the until then (2009), invulnerable Xbox 360, where a special modchip was able to attach to a secret set of contacts on the motherboard, managing to negate the security of the console.
When the news of the hack broke, many people hurried to get their Xbox JTAGed, but Pokora and Clark thought about the opportunity to earn money from it.
They managed to crack the Call of Duty series and make mods into the game where the players could possess superpowers like flying, running at light speed, etc. They then proceed to create the “mod lobby”, a place on Xbox live where players with JTAGed consoles participated in online deathmatches, etc.
They would charge up to 100$ per hour for a single player and then for an extra amount of money they offered the so-called “infections”, in which players could have their “superpower” abilities remain also to the standard games which were not hacked. Microsoft tried to sabotage their efforts by scanning the players’ console for the JTAG hack and then ban them.
However, David and Clark found a workaround for this, and for their efforts, they were able to earn thousands of dollars per day. David was enjoying the benefits of his success, he was known as Xenomega in the hacking forums, and he was still living with his parents but spend many nights at luxurious hotels and restaurants with his girlfriend.
Epic Games hack
In 2010, a 14 years old Australian hacker named Dylan Wheeler and his American friend under the nickname Gamefreak managed to get a password list of public forums by Epic Games. Dylan found a password of a personal account of an employee in the IT department of Epic Games. Having established themselves in the Epic network, the two hackers needed extra help. Dylan, who knew David from the forums, ask David to help them to pull down the Halo cards from a half-open network of ParterNet and to crack a secure private network where the company stores its sensitive data, by far the more illegal action David did but his curiosity prevailed and he agreed to help him with some basic rules such as not using any credit card information and not leaking any personal information about Epic customers.

Dylan Wheeler - Image Credit: wired.com
Due to the huge amount of data they found, they enlisted to their group, another hacker named Sanadodeha “Sonic” Nesheiwat, from New Jersey, who downloaded a copy of Gears of War 3 and a lot of private information of the Video Games that Epic Games was developing and send them to David.
David shared the game with several of his friends, including his distributor, Justin May.
Within days, a copy of the game in the form of torrent appeared in forums. The news about the leaked Gears of War 3 resulted in an FBI investigation who the hacker group found out by reading Epic emails.
Sanadodeh Nesheiwat - Image Credit: wired.com
See Also: Reverse Engineering-Hacking Tools
The investigation though, subsided as the company made no visible effort to block the hackers as it seemed that they couldn’t determine the method of entry and the FBI was unable to find them.
The young hackers continued carelessly to hack into other companies-organization through their access to Epic Games. They hack into Scaleform, a middleware company that was providing technology equipment to Epic Games and then they hack their way into Zombie Studios, developer of Spec Ops games where they found tunnels for remote access to customers and US military companies.
They‘d given to their group the name ‘Xbox Underground’ after a suggestion from Wheeler to instill fear in the people that were trying to find them.
Complications into the hacker group and the newly joined members
David was too absorbed by their access to the forbidden gaming software to listen to any of the advice/warnings that his fellow hackers and friends. They were constantly warning him about being arrested for going too deep but he refused to acknowledge the danger.
He kept stealing preliminary software, including an early copy of Call of Duty: Modern Warfare 3.
David continued hacking and he managed to download a database but he was still proud of how little he cared about making money. In his own words “We could sell them for bitcoins that are not tracked with the right approach. There are fifty thousand lungs.”
In 2010, Justin May got arrested in a Gaming convention in Boston for trying to download gaming software source code. Pokora though trusted Justin, and in 2011, they both made a deal with an Xbox-dev-guy player to sell him some of their stolen pre-released games. Their close relationship caused problems in the hacker group because of the past of Justin, where he got caught in 2010.
In 2012, they added two highly skillful hackers, Austin “AAmonkey” Alcala, a high school student in Indiana, and Nathan “animefre4k” Leroux who lived in Maryland, to help them hack into the Zombie studios network.

Nathan Leroux - Image Credit: wired.com
Pentagon’s Apache Helicopter Simulator and Durango mess
The hacker group stumbled across a tunnel between Zombie studios and a server of the US Army. On the server, they found a simulator for AH-64D Apache helicopter, that Zombie studios were developing under a contract with the Pentagon.
They also managed to steal documents from Microsoft servers for an early version of Durango, the next-generation Xbox, now known as Xbox One. They didn’t sell the documents to a Microsoft competitor, but they assembled and sell copies of the Durango console by using ready-made components and managed to find sellers to sell them to for 5000 dollars. One of the Durango’s never arrived at the customer, this led to a complaint and rumors begun between the members that the FBI took it and was looking for them.
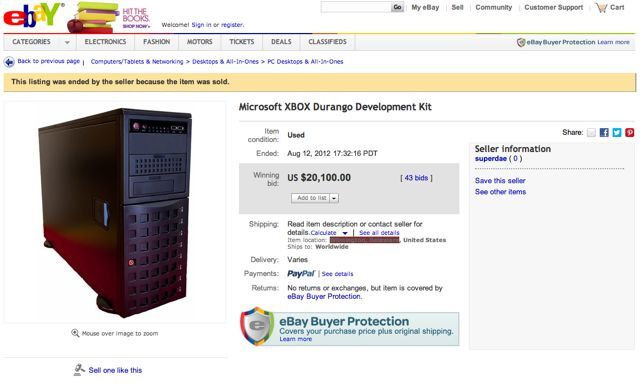
Wheeler then, driven by the glory of becoming the top Xbox hacker, placed a bid auction on eBay for the non-existed console. The bid exceeded 20 thousand dollars before eBay canceled the auction, declaring it fraudulent. Pokora was furious with Wheeler for causing an enormous spike in media attention and broke off his relations with Wheeler.
Durango Xbox One Prototype listed on eBay auction - Image Credit: theregister.com
In the next weeks some of the members of the group disappeared without a trace and the rumors about the FBI looking for them along with a suspicion that there was a mole among them, increased the anxiety between the group.
See Also: Offensive Security Tool: OpenRediWrecked
Things got complicated among the group
David focused on Horizon, an Xbox cheat service he created. He split up with Clark because of disagreements in their Call of Duty ‘services’. Clark began then selling virtual currency for FIFA on the black market.
Wheeler after his mess with the eBay auction, continued alone on his way of doing things. At the end of 2012, the FBI raid Santodeha Nesheiwat’s home in New Jersey. He posted the warrant online and Wheeler goes crazy about hiring a hitman to kill the judge who signed the warrant.
After the 2011 leak of Gears of War, the US federal prosecutors started building the case against the hacker group, the leading investigator was Edward McAndrew.
They needed to speed up their actions due to Wheeler’s dangerous behavior, and in February 2013, they raided Wheeler’s home in Perth and took all of his equipment and hard disks, but they didn’t arrest him.
In 2013, Edward McAndrew filed a closed indictment on several counts against Pokora, Neshivevat, and Leroux for crimes like fraud using electronic means, identity fraud, and conspiracy to steal commercial secrets. The case is based on pieces of evidence from an informant, called ‘person A’. According to many sources, the informant named ‘person A’ was Justin May, who didn’t comment when he asked if he was the insider. He was at the time being on a trial for stealing millions of dollars of equipment from Cisco and Microsoft.
The end is near
Without knowing anything about the case, Pokora continued his illegal actions. This time, he cooperated with Alcala, who told him that he knew a guy willing to steal the real prototypes of Durango(Xbox One) from Microsoft campus in Redmond, named Armand. Armand had already taken out one Durango for his personal use a year earlier where he used a cloned RFID card to enter the Microsoft campus.

Microsoft Headquarters in Redmond - Image Credit: https://commons.wikimedia.org/wiki/User:Coolcaesar
In September of 2013, Armand passed into the building where the Durango prototypes were stored and after a thrilling couple of hours, he managed to squeeze two consoles into his backpack. He then sent the stolen consoles to Pokora and Alcala. A couple of weeks later Armand was hired by Microsoft for a position in the quality assurance department. It took no long before he was identified by investigators from a camera outside the campus of Microsoft as he was seen leaving the building the day where the consoles were stolen.
Until the end of 2013, Pokora was hacking Xbox 360 games for his cheat engine Horizon.
In March 2014, David needed a new bumper for his car but the seller wasn’t shipping to Canada so he agreed to meet his friend Justin May in Delaware, Wilmington, where Justin lived. He visited him with his father and it was the first time that he met Justin in person after years of collaboration in their hacking endeavors.
Arrest and Charges
He eventually runs out of luck when passing the Border Guard building on his way to the US. The officer while scanning his passport saw that David had a warrant on his name for illegal hacking activities.They arrested him on the spot and little did he know that he was about to be held in custody for eight months under several chargers of conspiring to steal intellectual property up to 1 billion dollars.
In April 2014, David agreed to a proposed plea bargain and helped the affected companies to identify and mitigate the vulnerabilities he, and his group exploited.
Nathan Leroux was arrested also in March 2013, in Wisconsin during a raid in his home by the FBI. Unlike David, he was released on bail and he was living with his parents during the trials, but a couple of months later he decided to cut off the police tracker from his foot and ran away to Canada. Border Police then surrounded him on his way to cross the borders but he had only one option left in his mind, so he decided to stab himself multiple times. Doctors managed to save his life and as soon as he was released from the hospital, they transported him back to his home.
Pokora, Neshivevat, and Leroux admitted their guilt to the charges and received similar sentences. Pokora and Neshivevat received 18 months in prison and 2 years for Leroux.
Life after prison
David who was 26 years old at the time of his release, after a couple of months of worries about his mental health, that maybe prison affected his brain permanently. He had a hard time assembling his CV because the FBI seized all of the computers, he owned before his arrest and most of the software he created was gone.
He eventually brought his life together, met a girl, and then attended the University of Toronto.
Leroux, after his release, went back to Madison, Wisconsin, and continued working for his previous employer a company named Human Head Studios, a gaming software company that shut down its operations after the release of Rune 2 in 2019.
Neshivevat was in his early thirties after his release and wasn’t that successful as the other two group members. He was fighting with drug addiction and was arrested again at the end of 2017 for violating a probationary period for using opiates. He then successfully departed from the rehabilitation center and started building his life again.
Closing Thoughts
David Pokora knows that he will remain forever a hacking persona in the gaming world. His love and passion for gaming drove him to learn more about gaming software development but the promising money from the cheat engines and curiosity about hacking into the gaming software companies lured him into the wrong path.
Nowadays, the gaming industry has been more secure than ever but the infinite cycle of hacking and patching will continue forever as security is an ongoing process in today’s digital world. Finding the vulnerabilities on a company’s network or systems as quickly as possible can mitigate the risks of the attack spreading to other organizations, companies, or even to the company’s network.
Assessing the security policies every quarter and performing scheduled security testings/scannings should be a top priority for any company independent from the industry.
We hope that this write up has taught you something new. If you enjoyed it, the best way that you can support us is to share it! If you’d like to hear more about us, you can find us on LinkedIn, Twitter, YouTube.
Are you a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]


 Sanadodeh Nesheiwat - Image Credit: wired.com
Sanadodeh Nesheiwat - Image Credit: wired.com