Integrating Metasploit with BeEF Framework for advanced post-exploitation attacks

Reading Time: 5 Minutes
Introduction
Metasploit of course is one of the most used tools by Red Teamers and pentesters, BeEF (The Browser Exploitation Framework Project) is also one of the most sophisticated tools that allow you to perform browser-based attacks. Combining both of them allows you to have one of the most powerful ways to perform MitM (Man in the middle) attacks combining Social Engineering real-time attacks but also elevating it, and integrating Metasploit so you can run post modules and elevate your attacks to get a shell on those endpoints, enhancing and maximizing the way you conduct your assessments.
We at BHEH have decided to help you understand how to configure both of them by writing this guide which provides a comprehensive overview of how to integrate BeEF Framework with Metasploit on Kali Linux, enhancing the capabilities of both tools for more effective penetration testing.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
How to configure both so you can load the modules from within BeEF
BeEF (Browser Exploitation Framework) is an open-source application that allows a Red Teamer or Ethical Hacker to assess the actual security posture of a target environment by exploiting vulnerabilities within web browsers but also using Social Engineering attacks and scenarios on real humans and employees in real-time. On the other hand, Metasploit is a powerful tool used for developing and executing exploit code against a remote target machine. The integration of these two frameworks allows for a more comprehensive security testing regimen by combining the client-side attack vectors with the network-level exploits.
*Note: If you are using Kali Linux it’s already installed, and you can skip the step 1 and step 2.
See Also: Offensive Security Tool: Pypykatz
Step 1: Installing BeEF Framework
To install BeEF on a Linux system, you can clone it directly from its GitHub repository. This ensures you have the most recent version of the tool.
sudo apt-get update
sudo apt-get install git
git clone https://github.com/beefproject/beef.git
cd beef
./install
Once installed, you can run BeEF using the following commands:
cd beef
./beef
Step 2: Installing Metasploit
Installing Metasploit can be achieved via the package provided by Rapid7, which simplifies the installation process through an automated script.
cd ~
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall
chmod 755 msfinstall
sudo ./msfinstall
After installation, you can launch Metasploit by typing:
msfdb init
msfconsole
Step 3: Integrating BeEF with Metasploit
Configuring BeEF
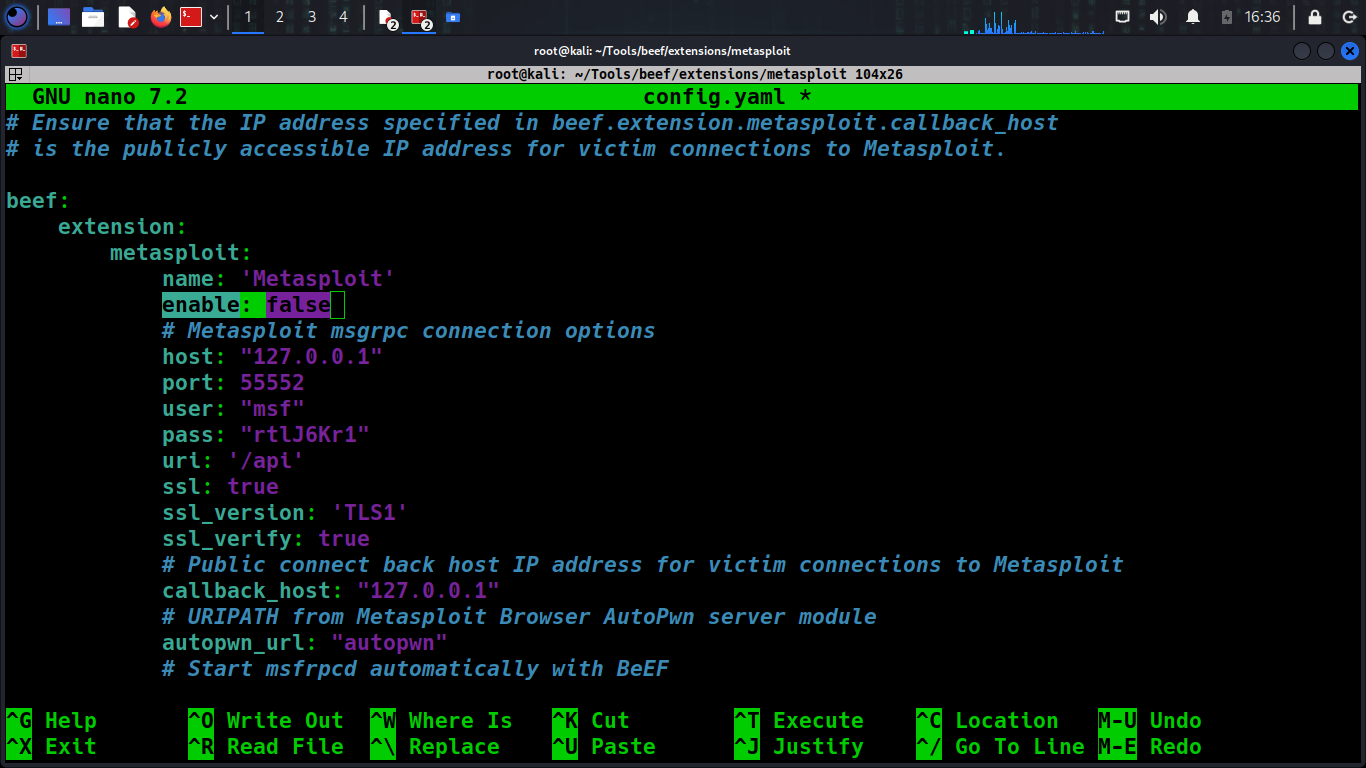
Integration requires configuring BeEF to communicate with Metasploit. Modify the BeEF configuration file:
nano ~/Tools/beef/extensions/metasploit/config.yaml
Look for the beef.integration.metasploit section, and make sure it is set as follows:
config.yaml
beef:
integration:
metasploit:
enable: true
host: "127.0.0.1"
port: 55552
user: “msf”
pass: “rtlJ6Kr1”
uri: "/api"
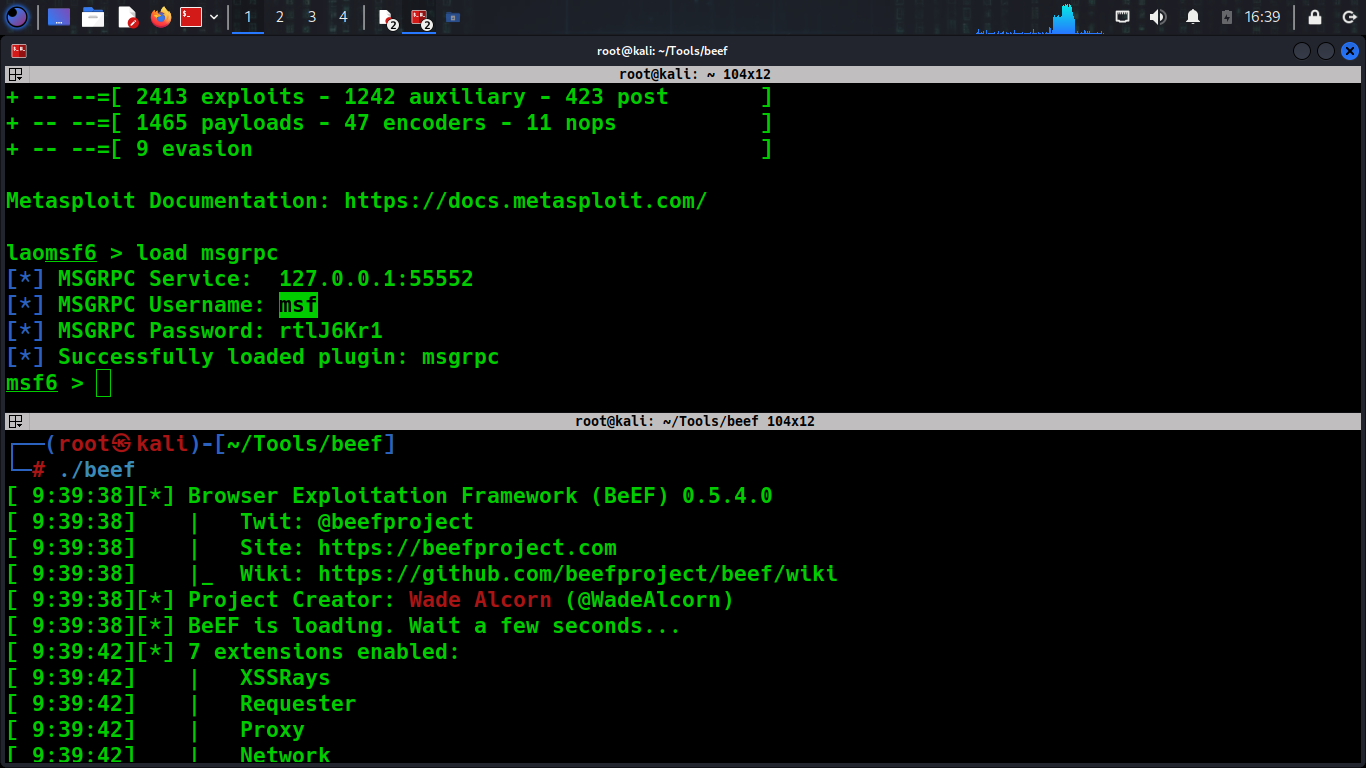
Step 4: Launching an Attack
With both frameworks integrated, you now can launch sophisticated attacks that combine browser-based vulnerabilities and network exploits. Here is a basic scenario:
Hook a Browser – Use BeEF to hook a browser visiting a malicious webpage.
Execute Commands – From BeEF’s interface, choose a command module that leverages Metasploit exploits to obtain shell and persistency so even if the user closes their browser you are able to still gain access to their machines through a meterpreter shell.
Exploitation– Use Metasploit through BeEF to exploit the hooked browser or pivot to other systems on the network.
Conclusion
Integrating BeEF with Metasploit on a Linux system allows you, as a Red Teamer to elevate your attack vectors and in a more sophisticated manner. This setup allows for a wider range of attack simulations, from client-side browser exploits to server-side network penetrations, providing a comprehensive environment for penetration testing.
Remember, the use of these tools should be conducted ethically and only in environments where you have explicit permission to test. This guide aims to educate and empower Red Teamers, Pentesters, and Ethical Hackers to improve their capabilities within the scope agreed with your client.
We hope that this write up has taught you something new. If you enjoyed it, the best way that you can support us is to share it! If you’d like to hear more about us, you can find us on LinkedIn, Twitter, YouTube.
Are you a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]