Jeff Foley – OWASP Amass Founder

Reading Time: 5 Minutes
Introduction
Jeff Foley, also known as Caffix in the cybersecurity realm, boasts over two decades of experience encompassing research, development, offensive security assessments, and specialized expertise in attack surface management. His journey into the realm of information security started with a fascination for the Internet during his university years.
Over time, his career path evolved from network programming and telecommunications to pioneering cyber warfare capabilities for the Air Force Research Laboratory. This transition led to a profound realization – the critical need for organizations to comprehend and safeguard their attack surfaces.
Jeff’s commitment to addressing this gap culminated in the creation of the Amass project, a flagship initiative within the OWASP community.

Jeff Foley - LinkedIn
Early life and education – The journey to information security
During Jeff’s university years, he initially aspired to pursue a career in chemistry. However, his fascination with the Internet led him to change his focus to network programming and telecommunications. While working as a network administrator at his university, he automated his tasks to such an extent that he had free time. Upon discussing this with his assistant director, he was introduced to the need for security policies enforcement and violation detection.
Jeff took on the challenge and discovered various policy violations. This experience showed him the feasibility and importance of automation in monitoring and enforcing security policies, sparking his interest in information security.
His first full-time job was in developing cyber warfare capabilities for the Air Force Research Laboratory, including projects related to evading intrusion detection with network reconnaissance tools in the early 2000s.
As his career progressed, Jeff shifted towards roles in red teaming, penetration testing, and vulnerability assessment due to the growing attention and demand in the field.
Addressing customers lack of Security Awareness for their attack surface
Jeff’s transition from research and development to security assessments exposed him to the alarming lack of awareness among commercial customers about their attack surface, internet exposure, and reachable assets, which contrasted with his experiences in the military sector.
Jeff Foley’s expertise in red teaming and open-source intelligence led to a niche focus on helping organizations understand their attack surface and vulnerabilities.
By combining open-source intelligence with adversary emulation, they provided customers with a clearer picture of their security risks. This approach allowed organizations to prioritize risks intelligently, focusing on assets that were not only vulnerable but also discoverable and exploitable.
The missing piece in many organizations’ security strategies
He also noticed a troubling trend in which many organizations had stale and poorly maintained asset inventories.
Some companies bypassed proper procedures to quickly deploy assets online, leading to discrepancies between their inventory records and the actual attack surface, even companies with mature security programs were affected by these issues.
He recognized that addressing the discoverability of assets could significantly reduce their exploitability, a crucial missing piece in many organizations’ security strategies.
While organizations often focused on vulnerability management and threat actor monitoring, they tended to overlook the importance of understanding what was discoverable and reachable in their attack surface.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
The birth of AMASS
The Amass project, which is currently a flagship OWASP project, began as Jeff Foley’s personal initiative.
Amass
The inception of the Amass project was driven by the imperative need to bridge a conspicuous gap within the realm of security, particularly concerning the comprehension of an organization’s attack surface.
Jeff, while assisting organizations in the labor-intensive tasks of attack surface mapping and asset discovery, soon realized the inefficiency of manual processes. He recognized that automation was the key to making this procedure more streamlined and effective, prompting him to embark on the journey of creating a dedicated tool.
Jeff’s quest for an adequate solution revealed that while interactive tools like Maltego were excellent for some purposes, they were not well-suited for background processes aimed at gathering comprehensive information about a target’s attack surface. Recognizing this gap, he made it his mission to develop a tool capable of providing a holistic view of an organization’s attack surface.
Initially, Jeff developed this tool for his personal use, but he soon recognized the broader community’s need for such a robust asset discovery and attack surface mapping tool. In 2017, he decided to make it freely available to the public, offering a valuable resource to others grappling with similar challenges in the realm of cybersecurity.
you can’t be protecting things if you don’t know they’re there
A defining characteristic that sets Amass apart from other tools is its unwavering commitment to automation and recursive enumeration. Amass follows a cyclic process, continually discovering information, feeding it back into the data pipeline, and reevaluating the newfound data to furnish the most comprehensive and current depiction of an organization’s attack surface. This meticulous approach includes storing its discoveries in a database, ensuring that prior knowledge is leveraged in ongoing engagements. By doing so, Amass achieves enhanced consistency and diminishes inconsistencies between tool executions, thereby simplifying data management and facilitating its effective utilization.
See Also: Recon Tool: fetchmeurls
Amass: Automating Asset Discovery and Enhancing Attack Surface Understanding
Amass offers a seamless experience by providing real-time streaming output during its operation, offering valuable insights as it uncovers information. This dynamic output includes data sources, names, associated IP addresses, and ASNs (Autonomous System Numbers) where assets are discovered. This succinct summary empowers users to swiftly grasp the extent of an organization’s online presence.
Amass’s functionality can be categorized into five key subcommands or functions:
Intel Subcommand: This component requires some degree of manual or interactive involvement. It serves as the repository for capabilities or features that necessitate human analysis before their inclusion in the automated process.
Enumeration Subcommand: At the core of Amass, this function is dedicated to the discovery and enumeration of assets. It represents the most actively developed aspect of the tool, continuously evolving to enhance its capabilities.
Database Access: Amass facilitates user access to a comprehensive collection of asset details, enabling the tracking of changes across different tool executions.
Tracking: This feature empowers users to compare distinct snapshots of information, effectively highlighting what is new or altered in an organization’s attack surface.
Visualization: Amass includes a visualization feature, allowing users to visually represent assets, simplifying the identification of outliers or unconventional assets within an organization’s structure.
The overarching objective of Amass is to streamline and automate the asset discovery process while ensuring that the findings are readily usable for security professionals. Its mission is to deliver an all-encompassing and automated solution that enhances users’ comprehension of their attack surface.
Amass endeavors to minimize the need for human intervention, aiming for a TurnKey approach that enables users to harness its findings efficiently and effectively. By doing so, it empowers security practitioners to bolster their cybersecurity posture with a comprehensive understanding of their digital footprint.
See Also: Offensive Security Tool: Nginxpwner
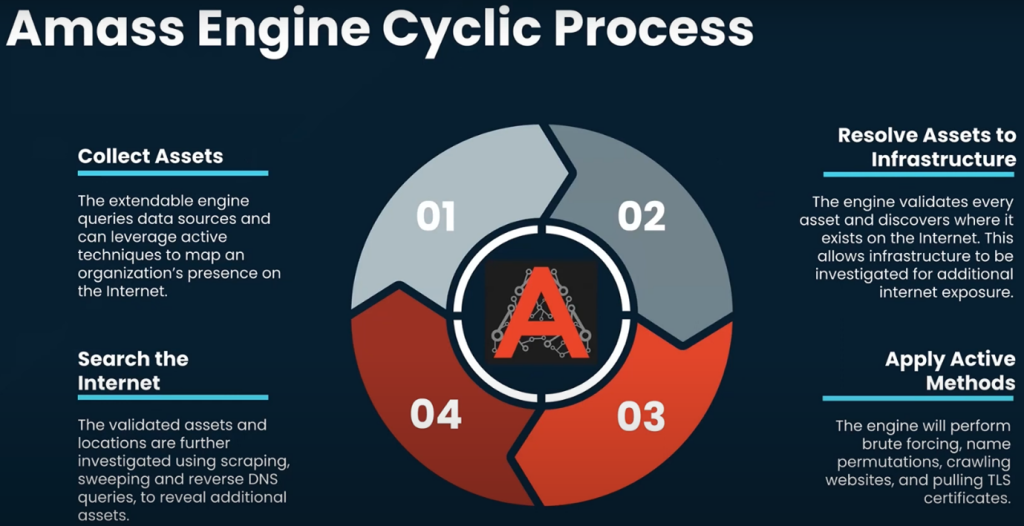
The Cyclic Process of Amass
The Amass process is a cyclic, multi-step approach to comprehensively map an organization’s attack surface. It begins by gathering data from various sources about the target organization or domain. After validating this information, the tool identifies where these assets exist online. Active methods, like brute-forcing and web crawling, are then employed to uncover additional assets, providing new starting points for enumeration.
Amass also offers a visualization feature to help users view assets graphically, making it easier to spot outliers. This iterative process continually updates the view of the attack surface, enhancing its accuracy and thoroughness. While it can be time-consuming, this approach ensures a deep understanding of an organization’s online presence, making it valuable for blue teamers and security professionals.
AMASS 4.0
OWASP Amass recently underwent a significant release, version 4.0, which introduced a flexible and open data model to represent collected information more effectively using the Open Asset Model (OAM), and Asset Database.
Building upon the foundational principles of the OAM, it now offers a more comprehensive perspective by not only encompassing digital and physical assets but also by delving deeper into the intricate web of relationships among different asset types, mirroring real-world connections.
One notable feature in this update is the introduction of concurrent data access, allowing users to analyze data while it is still being collected, which it was not available on previous versions. It also has the ability to print various types of asset data, such as fully qualified domain names (FQDNs). While the tool’s primary focus is on visual data inspection, future data manipulation tools are set to be available in a separate repository known as “oam tools”.
An example of the output of AMASS 4.0
In terms of flexibility, Amass 4.0 allows users to query the collected data using SQL statements, empowering them to extract specific information tailored to their unique requirements. Additionally, the tool offers the possibility of inserting external data into the OWASP Amass database.
What’s next for AMASS?
The development of the Open Asset Model (OAM) marks the beginning of a promising journey for OWASP Amass, with a clear vision for its future growth and expansion. The primary focus is on evolving the OAM to encompass a wide array of asset types and their intricate relationships within the internet landscape, ultimately striving for a comprehensive representation of the digital attack surface.
One of the pivotal upcoming developments on the horizon is the creation of the Amass collection engine. This engine is specifically engineered to keep pace with the expanding OAM and efficiently collect data for newly introduced asset types. The dynamic nature of the internet demands an agile toolset, and the Amass collection engine is poised to fulfill this need.
Crucially, community involvement is paramount in shaping and expanding the OAM to ensure that it emerges as a universally accepted standard for describing and communicating attack surfaces. Jeff underscores the significance of predictability, consistency, and a common understanding when dealing with attack surface data, all of which the OAM aspires to provide
The overarching objective is to enhance communication and understanding of exposed assets on the internet, making it easier for security professionals to work collaboratively and address attack surface concerns effectively.
Professional career
Jeff in the last five years is solely focused on attack surface management. He is currently the Vice President of Attack Surface Protection at Zero Fox and previously held roles at Citigroup, National Grid, Northrop Grumman while also having served time in the Air Force research laboratory.
Jeff Foley VP, Attack Surface Protection at ZeroFox
Jeff also serves as an adjunct professor. His decision to step into this role is rooted in the invaluable support he received from academic mentors during the early stages of his career. Jeff’s aim is to pay forward that support by assisting today’s students as they aspire to establish themselves in the field of cybersecurity.
He served as an adjunct professor at SUNY Polytechnic Institute in New York from 2019 to June 2022, teaching Penetration Testing, Cloud Computing, and Security classes. Recently, he assumed a new role as an adjunct professor at Utica University in New York, where he teaches his area of expertise, which is Attack Surface Management.
Closing thoughts
Jeff Foley has carved a path of innovation and commitment in the field of information security. His journey, from network programming to pioneering cyber warfare capabilities, culminated in the creation of the Amass project, a flagship initiative in the OWASP community. Amass’s automation-driven approach to asset discovery and attack surface mapping has revolutionized the industry, offering vital insights into organizations’ online presence.
As OWASP Amass continues to evolve, Jeff’s vision for a comprehensive representation of the digital attack surface remains steadfast. His impact extends to academia, where he serves as an adjunct professor, paying forward the support he received during his formative years. In essence, Jeff Foley’s journey embodies innovation, automation, and community collaboration, advancing cybersecurity and fostering a safer digital landscape for all.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]