Major Cyber Attacks that shaped 2024

Reading Time: 6 Minutes
Introduction
In this article, we examine the most significant cyberattacks of 2024, highlighting their causes, consequences, and the insights they provide into the evolution of cyber threats.
Key takeaways:
2024 left an enduring mark on the cybersecurity world, with attacks becoming more relentless and sophisticated than ever before, while the year also witnessed a significant surge in Common Vulnerabilities and Exposures (CVEs). As we move into 2025, reflecting on these developments is essential to prepare for what lies ahead.
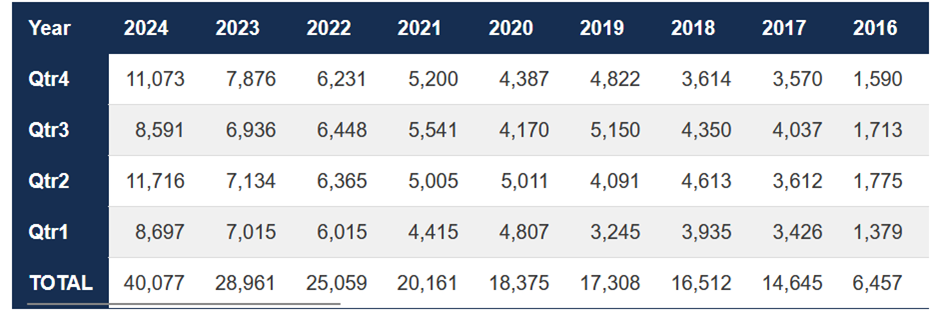
In 2024, 44,077 vulnerabilities were disclosed, marking a 33% increase from the 33,096 CVEs disclosed in 2023—an increase of over 11,000 vulnerabilities in just one year.
Total Number of vulnerabilities by Year - source: www.cve.org
Cyberattacks skyrocketed in 2024, with an average of 1,673 weekly attacks per organization—a 44% increase from 2023. The education sector experienced the most significant rise, with a 75% year-over-year increase, surpassing 3,574 weekly attacks due to its high volume of personal data. The healthcare sector saw a 47% increase, as cybercriminals abandoned self-imposed prohibitions on targeting medical services. Meanwhile, the hardware and semiconductor industries faced a staggering 179% increase, driven by AI demand and supply chain vulnerabilities. FakeUpdates (SocGholish) led the malware rankings, leveraging a network of compromised websites to trick users into downloading malicious software.
Key statistics:
- 1,673 weekly attacks per organization globally (44% increase from 2023).
- 75% increase in attacks on the education sector, surpassing 3,574 weekly attacks.
- 47% increase in healthcare attacks, with ransomware actors increasingly targeting medical institutions.
- 179% rise in attacks on hardware and semiconductor companies, driven by AI demand and supply chain vulnerabilities.
- Infostealer infections surged by 58%, affecting 19% of organizations.
- 5,200+ companies’ data leaked on ransomware sites, despite the decline of LockBit and ALPHV.
- Email-based attacks accounted for 68% of all incidents, with HTML attachments used in 61% of malicious emails.
Noteworthy Cybersecurity Incidents
Ransomware attack at Change Healthcare
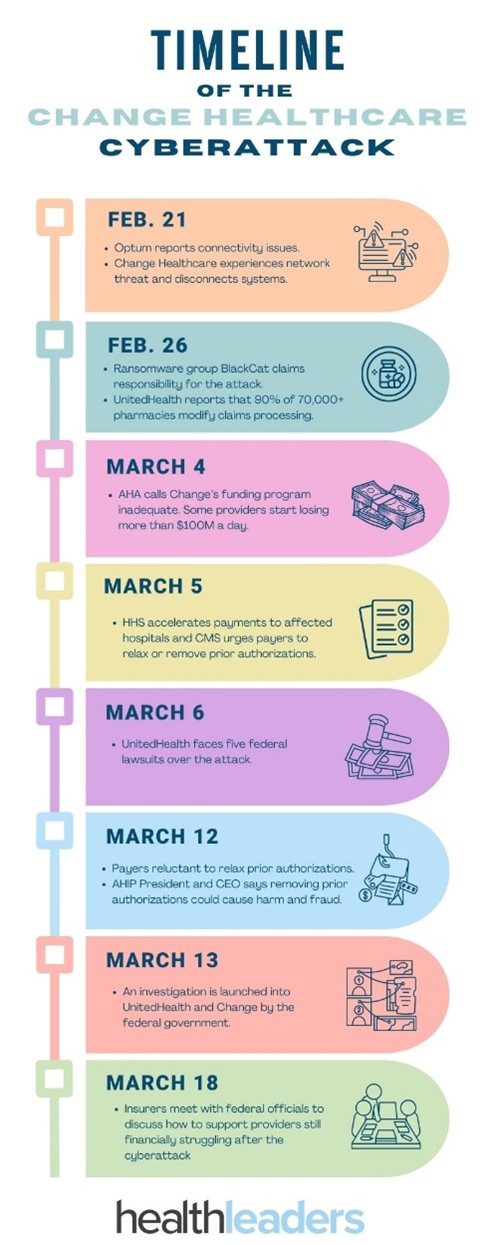
In February 2024, Change Healthcare, a subsidiary of UnitedHealth Group and one of the largest health data processors in the U.S., suffered a devastating ransomware attack by the ALPHV/BlackCat gang. The breach caused widespread outages across the healthcare sector, halting billing systems, delaying insurance claims, and affecting services at military pharmacies worldwide. UnitedHealth initially misattributed the attack to nation-state actors but later confirmed it was ransomware.
A timeline of the Change Healthcare attack - source: healthleadersmedia.com
The company paid a $22 million ransom to regain access to stolen data, but the attackers disappeared, and the data remained compromised. A rogue ALPHV affiliate later formed a new extortion group, RansomHub, and demanded a second ransom, leaking portions of sensitive patient data as proof.
A fake law enforcement seizure notice posted on BlackCat’s dark web leak site soon after receiving a ransom payment of $22 million. - source: techcrunch.com
By January 2025, UnitedHealth confirmed that the breach impacted 190 million Americans, making it the largest healthcare data breach in U.S. history. The stolen data included medical records, diagnoses, medications, test results, and financial information. Investigations revealed that attackers exploited a single compromised account without multi-factor authentication (MFA), exposing significant security lapses within Change Healthcare’s systems. The breach led to Congressional hearings, state lawsuits, and a $10 million bounty from the U.S. government for information on the attackers, demonstrating the increasing risks ransomware poses to critical infrastructure.
See Also: The Bug Bounty Hunting Course
A Practical Guide to Hacking Techniques for finding Top Bugs.
CrowdStrike Windows Outage
While ransomware crippled critical healthcare infrastructure, the CrowdStrike outage demonstrated how a single software failure could bring down global operations, revealing another layer of cyber risk.
In July 2024, a flawed content update from CrowdStrike, a leading cybersecurity software provider, caused the crash of over 8.5 million systems worldwide, impacting thousands of organizations, including hundreds of Fortune 1000 companies.
Dubbed the CrowdStrike glitch, the incident led to an estimated $5 billion in losses globally, with insurers facing around $1.5 billion in payouts under business interruption, cyber, and system failure coverages. One of the most notable cases was Delta Airlines, which experienced the disruption of 7,000 flights and inconvenience to 1.3 million passengers over five days, resulting in a reported loss of $500 million. In response, Delta filed a lawsuit against CrowdStrike, accusing the company of issuing untested updates that caused catastrophic outages. CrowdStrike acknowledged the faulty update but argued that Delta’s claims were exaggerated and blamed the airline’s outdated IT infrastructure for its prolonged recovery.
Multiple blue screens of death caused by a faulty software update on baggage carousels at LaGuardia Airport, New York City - source: wikipedia.com
The event exposed significant gaps in cyber risk management and the growing systemic risks of aggregated cyber dependencies. It exposed vulnerabilities in supply chain cybersecurity, as many organizations were unprepared for the cascading failures caused by a single point of failure. The CrowdStrike outage underscored the fragmentation of the cybersecurity market, the challenge of assessing cyber risk concentrations, and the insufficiency of cyber insurance models in addressing rapidly evolving threats. With emerging technologies such as AI, quantum computing, and cloud computing introducing new risks, the incident served as a wake-up call for businesses to adopt more comprehensive cyber risk assessments and strengthen their incident response capabilities.
NHS Cancels Operations Following Ransomware Incident
Qilin released 394.1 GB of what's claimed to be Synnovis data on June 21 on their Telegram channel.
In June 2024, Synnovis, a critical laboratory services provider for the NHS in South East London, fell victim to a ransomware attack orchestrated by the Russian-speaking Qilin group. The attack, which began on June 3, caused widespread disruption to pathology services at major hospitals, including Guy’s and St Thomas’ NHS Foundation Trust and King’s College Hospital NHS Foundation Trust. These hospitals declared a critical incident on June 4 as essential services like blood transfusions, swab analysis, and diagnostic tests were significantly impacted. Healthcare staff were forced to revert to manual, paper-based methods, slowing down critical processes and delaying care for many patients. In the first week alone, over 800 planned operations and 700 outpatient appointments were rescheduled. On June 10, an urgent appeal for O blood-type donors was issued, as the hospitals struggled to efficiently match blood for transfusions.
The situation escalated when, on June 21, Qilin published nearly 400GB of stolen patient data on the dark web and Telegram. The leaked information included patient names, NHS numbers, and detailed descriptions of blood tests, along with confidential business records outlining agreements between NHS hospitals and Synnovis. Qilin claimed the attack was a retaliatory response to the UK government’s involvement in an unspecified war, though this motive was met with skepticism by cybersecurity experts. NHS England, supported by the National Cyber Security Centre (NCSC), confirmed the authenticity of the data breach and warned affected individuals of potential identity misuse. By June 27, the number of postponed medical activities had surged to over 1,000 canceled operations and 3,000 outpatient appointments.
After months of disruption, NHS England announced on October 11, 2024, that all pathology and blood testing services had returned to normal operations. Despite the restoration of services, the attack revealed critical weaknesses in NHS supply chain security, demonstrating how third-party compromises can disrupt essential medical services. The attackers’ use of a double extortion tactic—stealing and publishing sensitive data to increase ransom pressure. NHS England’s response, which included activating business continuity protocols and enhancing collaboration with the NCSC, provided a foundation for recovery.
See Also: Recon Tool: fetchmeurls
US Telecom Attacks
In September 2024, U.S. officials revealed that Salt Typhoon, a Chinese state-sponsored hacking group, had successfully infiltrated the networks of nine major U.S. telecommunications companies, including Verizon, AT&T, T-Mobile, Spectrum, Lumen, Consolidated Communications, and Windstream. The attackers targeted core network infrastructure, including Cisco routers, which are integral to routing vast amounts of U.S. internet traffic. Investigations indicated that the attackers had maintained access for months, potentially years, before being discovered. Their primary objective appeared to be espionage, specifically collecting intelligence from government officials and high-profile individuals. Among the compromised data were metadata from calls and text messages, such as IP addresses, phone numbers, and timestamps, primarily from individuals in the Washington, D.C. metro area. Alarmingly, reports later confirmed that the Salt Typhoon attackers accessed audio recordings of calls made by key political figures, including staff from Kamala Harris’ 2024 campaign, as well as Donald Trump and J.D. Vance.
The attackers leveraged known vulnerabilities in network devices, including those associated with Microsoft Exchange ProxyLogon exploits and compromised Cisco equipment, to infiltrate these critical systems. Once inside, they deployed tools like SparrowDoor backdoors, custom Mimikatz versions, and the Demodex rootkit to escalate privileges and maintain persistence. The breach also compromised systems used for CALEA (Communications Assistance for Law Enforcement Act) requests, which U.S. law enforcement agencies rely on for court-authorized wiretaps. This raised serious concerns regarding national security, as it exposed sensitive intelligence operations and potentially jeopardized counterintelligence efforts. In response, the White House announced plans to ban China Telecom’s remaining U.S. operations and investigate TP-Link routers for potential involvement. The FCC also introduced stricter regulations requiring telecom companies to bolster their network defenses.
By December 2024, Verizon and AT&T confirmed that they had successfully expelled Salt Typhoon from their systems and had contained the malicious activity. T-Mobile also disclosed that attackers attempted lateral movement through its network but were blocked by internal defenses. Cybersecurity experts highlighted the breach as one of the most significant state-sponsored intrusions into U.S. telecommunications infrastructure. This breach reinforced the strategic importance of telecom networks for cyber-espionage while revealing persistent national security weaknesses.
Internet Archive Hacked
JavaScript alert shown on Archive.org - source: BleepingComputer.com
In October 2024, the Internet Archive experienced two significant cybersecurity incidents, compromising sensitive user data and critical internal systems. The first breach was discovered on October 9, when visitors to the Wayback Machine were greeted with a JavaScript alert announcing that the site had been compromised. Investigations revealed that 31 million user records had been stolen, including email addresses, screen names, and bcrypt-hashed passwords. The attackers exploited vulnerabilities in an exposed GitLab configuration file, which had been publicly accessible since at least December 2022. This file contained an authentication token that granted access to the organization’s source code and database management systems, allowing the attackers to extract 7TB of data. Concurrently, the site also faced a DDoS attack attributed to the pro-Palestinian hacktivist group SN_BlackMeta. While unrelated to the data breach, the simultaneous attacks overwhelmed the platform, taking archive.org and openlibrary.org offline for extended periods.
Less than two weeks later, on October 20, the Internet Archive suffered a second breach when attackers exploited another set of unrotated authentication tokens to access its Zendesk email support platform. The attackers sent messages to users who had previously submitted removal requests to the Archive, warning that their data was compromised. The exposed records included over 800,000 support tickets—some containing personal identification documents uploaded by users when requesting content removal from the Wayback Machine. Despite repeated warnings from security researchers about the exposed tokens, the Internet Archive failed to rotate its credentials in time, leaving the Zendesk API vulnerable. These breaches, driven more by “cyber street cred” than financial motives, exposed critical lapses in the Archive’s security practices, including poor credential management and delayed incident response.
See Also: Offensive Security Tool: Nucleimonst3r
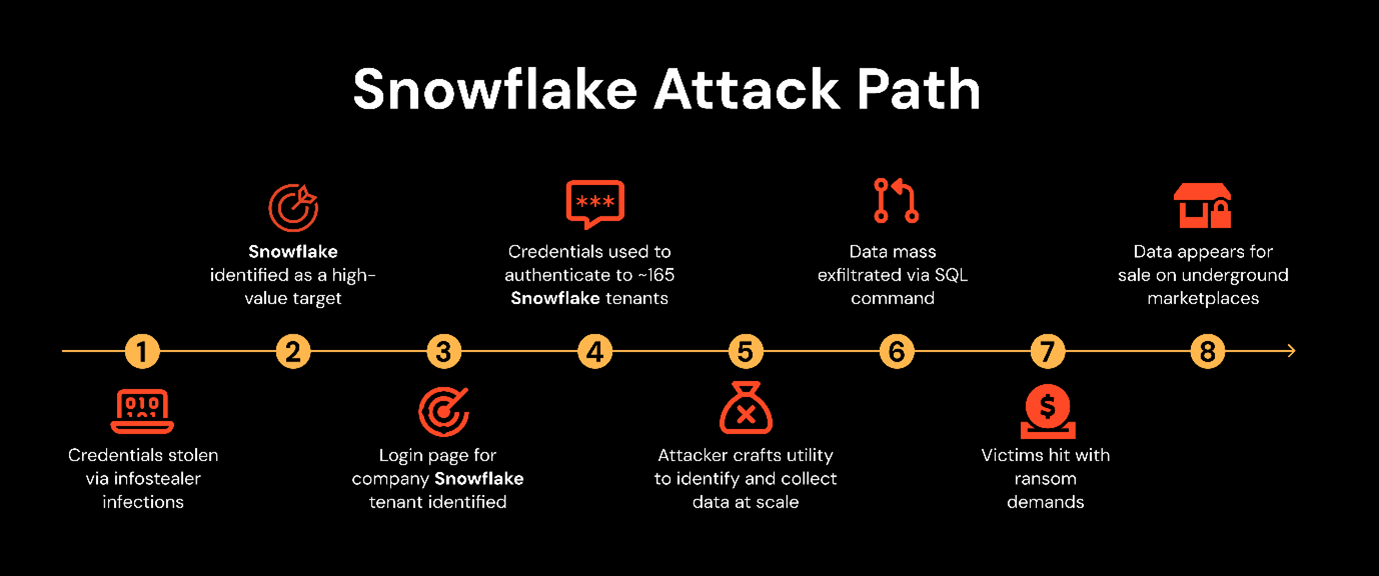
The SnowFlake data theft attacks
Attack path traversed in the attacks on Snowflake customers - source: pushsecurity.com
In May 2024, Snowflake, a prominent cloud data warehousing platform, suffered a large-scale data breach impacting 165 customer organizations worldwide. The attack was attributed to UNC5537, a financially motivated group linked to Scattered Spider and ShinyHunters. The attackers exploited compromised credentials obtained from historical infostealer malware infections dating back to 2020. These credentials, many of which were sourced from malware variants like VIDAR, RISEPRO, REDLINE, and RACOON STEALER, provided access to customer accounts that lacked multi-factor authentication (MFA). By leveraging these login details, the attackers infiltrated numerous Snowflake customer environments, exfiltrating terabytes of sensitive data. High-profile victims included AT&T, Ticketmaster, and Santander Bank, with stolen data including call records of 109 million AT&T customers, personal information of 30 million Santander customers, and 560 million Ticketmaster records. The attackers demanded ransoms ranging from $300,000 to $5 million, while also attempting to sell the data on dark web forums and Telegram channels.
Mandiant’s investigation revealed that 80% of compromised accounts had previously appeared in infostealer malware dumps, with valid, unchanged credentials being a key enabler of the breach. Additionally, Snowflake customers failed to enforce MFA on local logins, leaving accounts susceptible to simple credential-based attacks. The attackers conducted SQL-based reconnaissance using a custom tool called FROSTBOTE, which allowed them to enumerate users, access session data, and exfiltrate sensitive datasets across multiple environments in a matter of minutes. The compromised data varied significantly, from financial details at LendingTree and Truist Bank to student records from the Los Angeles Unified School District.
Snowflake and Mandiant later confirmed that the breach was not due to a direct compromise of Snowflake’s core infrastructure, but instead stemmed from poor credential hygiene and weak access controls within customer environments. The Snowflake breach served as a wake-up call for the industry, emphasizing the critical need for MFA, regular credential rotation, and better identity management practices to protect cloud-based data platforms from similar attacks in the future.
Mass Exploitation of Ivanti Zero-Day Vulnerabilities
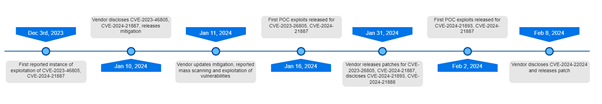
In January 2024, a series of zero-day vulnerabilities affecting Ivanti Connect Secure (ICS) and Policy Secure appliances were disclosed, leading to widespread exploitation by suspected Chinese state-sponsored hackers. The vulnerabilities, including CVE-2023-46805 (authentication bypass) and CVE-2024-21887 (remote code execution), allowed attackers to gain unauthorized access to vulnerable Ivanti systems. By mid-January, multiple cybersecurity firms observed a surge in mass scanning and exploitation attempts, with thousands of organizations compromised before patches were available. Further vulnerabilities were discovered later, including CVE-2024-21893 (server-side request forgery), CVE-2024-21888 (privilege escalation), and CVE-2024-22024 (XXE vulnerability), indicating an ongoing, large-scale attack campaign against Ivanti customers.
Major Events Timeline of Ivanti Vulnerabilities - source: securityintelligence.com
Threat actors leveraged custom webshells such as FRAMESTING, WIREFIRE, and CHAINLINE to establish persistence, steal authentication tokens, and execute arbitrary commands. A particularly advanced Perl-based backdoor, dubbed DSLog, was found implanted in compromised systems, enabling covert remote access. The Ivanti Integrity Check Tool (ICT) was also manipulated by attackers to hide traces of compromise, complicating detection efforts. Security researchers advised organizations to run external forensic tools and collect disk/memory images before remediation to ensure full threat actor eviction. The Ivanti breaches underlined the critical risks posed by vulnerabilities in remote access solutions, reaffirming the need for rapid patching, strong network segmentation, and continuous threat monitoring to defend against nation-state cyber operations.
Cybersecurity Forecast for 2025
Cyberattacks in 2025 will become more automated, scalable, and convincing as AI-powered tools enhance phishing, social engineering, and cyber espionage. Attackers will use large language models (LLMs) and deepfakes to create realistic scams, bypass identity verification, and automate vulnerability exploitation. Disinformation campaigns will also escalate, with AI generating fake news, synthetic social media profiles, and deepfake videos to manipulate public perception.
As cybercriminals integrate AI into every stage of their operations, the risk of AI-driven attacks becoming mainstream will grow.
To counter these threats, security teams will turn to AI-driven automation, transitioning toward semi-autonomous security operations. AI will assist in real-time threat detection, risk prioritization, and automated response, helping defenders keep up with faster, more sophisticated cyberattacks. Organizations that fail to integrate AI into their defenses will struggle against increasingly advanced threats. In 2025, cybersecurity will be a race between attackers leveraging AI for offense and defenders using AI to protect critical systems.
Closing thoughts
The cyberattacks of 2024 illustrated the growing complexity and scale of modern threats, from ransomware crippling healthcare systems to nation-state espionage targeting critical infrastructure. As attackers refine their tactics and integrate AI into their operations, organizations must adapt quickly by strengthening identity security, enforcing multi-factor authentication, and leveraging AI-driven defenses.
Proactive cybersecurity must become the norm. Regular penetration testing must become a core security practice, helping organizations identify vulnerabilities before attackers do and strengthen their defenses against evolving threats. The coming year will test the resilience of global cybersecurity efforts, making proactive threat intelligence, rapid incident response, and AI-assisted security operations more critical than ever.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]