Operation OpRussia – Anonymous attacks on Russia

Reading Time: 5 Minutes
Introduction
Originating in 2003 on 4chan, Anonymous is a decentralized international activist and hacktivist collective and movement known for its various cyberattacks against several governments, government agencies, and corporations whose mission is to combat establishment hypocrisy and corruption.
In late 2021, anticipating the military build-up near the Russia-Ukraine border, they acted to propagate peace plans to end the war in Donbas (the armed conflict between Ukraine and Russia started in 2014) by defacing various government websites in China, as the United Nations Network on Migration website.

Composite of homepage and Anonymous hack on UN Network on Migration website. (migrationnetwork.un.org screenshots)
Operation OpRussia
On February 24, 2022, 5 days after Vladimir Putin ordered the invasion of Ukraine, Twitter accounts associated with Anonymous declared that they will launch a ‘cyber operation’ called “OpRussia” against the Russian Federation.
#Anonymous is currently involved in operations against the Russian Federation. Our operations are targeting the Russian government. There is an inevitability that the private sector will most likely be affected too. While this account cannot claim to speak for the whole (con)
— Anonymous (@YourAnonNews) February 24, 2022
Operation Russia has possibly been Anonymous’s largest campaign to date, in terms of both scale and scope.
OpRussia Operation Attacks
- Attacks on RT.com, several other Russian TV channels, and Defense Ministry website
A few hours after the Anonymous collective called to action against Russia, its member have taken down the website of Russian propaganda RT news and also attacked the servers of the Russian Defense Ministry.
The #Anonymous collective has leaked the database of the Russian Ministry of Defense website. #Ukraine
— Anonymous (@YourAnonOne) February 25, 2022
Anonymous hacked into Russian TV channels, featuring Ukrainian Music and national symbols.
Someone hacked into Russian state TV channels. They feature Ukrainian music and national symbols. 🇺🇦
Internet users suspect that this may be another action by the hacker group #Anonymous, which declared a cyber war to Russia in connection with the attack on #Ukraine. pic.twitter.com/XaoclymVTs
— BECZKA ✌️ (@beczka_tv) February 26, 2022
JUST IN: #Russian state TV channels have been hacked by #Anonymous to broadcast the truth about what happens in #Ukraine. #OpRussia #OpKremlin #FckPutin #StandWithUkriane pic.twitter.com/vBq8pQnjPc
— Anonymous TV 🇺🇦 (@YourAnonTV) February 26, 2022
The website of the Kremlin (Kremlin.ru) was also unreachable the day of the attacks.
- Tetraedr emails leaked
They also leaked 200GB of emails from the Belarusian weapons manufacturer Tetraedr, which provided logistical support for Russia in the invasion of Ukraine.
#Anonymous leaks around 200GB of emails from Belarusian weapons maker Tetraedr. This company provided logistical support to Vladimir Putin in his invasion of #Ukraine.#OpRussia #StandWithUkraine pic.twitter.com/GvYXYRDhMB
— Anonymous (@LatestAnonPress) February 26, 2022
See Also: So you want to be a hacker?
Offensive Security Courses
- Russian Space Research Institute hack
On March 3rd, hacktivists from a group named “v0g3lSec” breached the website of the Russian Space Research Institute (IKI). The website was defaced after breaching one of its subdomains.
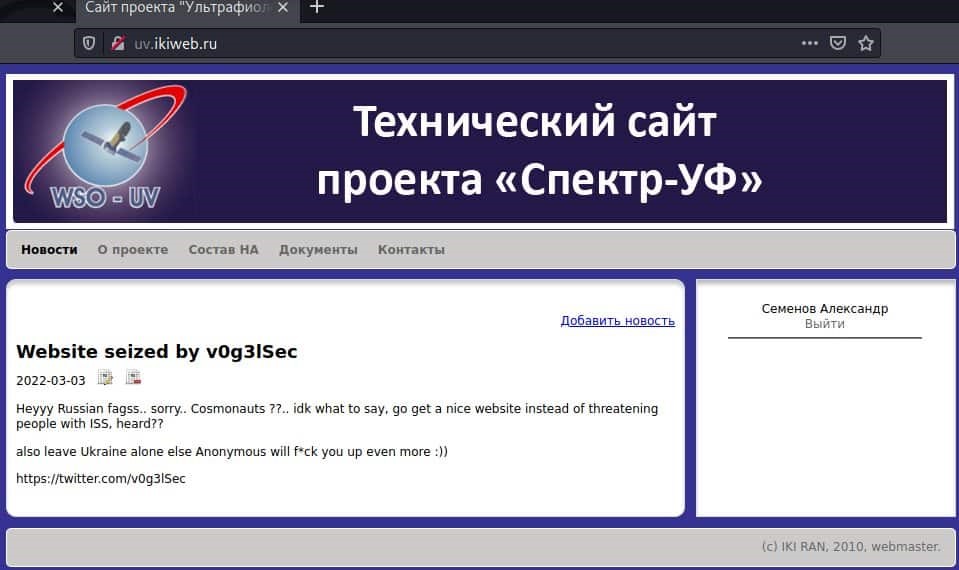
Deface message left by the group on the Institute’s website
- “Russian Camera Dump” Operation
On March 7, Anonymous actors DepaixPorteur declared on Twitter that they hacked 400 Russian surveillance cameras and broadcast them on a website. The group compromise the security cameras and displayed anti-propaganda messages. The point of this hack was to solely spread information to the Russian people.
We are #Anonymous
We have taken control of 400+ of Russian cameras in support of #Ukraine
We compiled about 100 on this website. This is anti-propaganda to open the eyes of Russian civilians. Also potential recon.
WATCH LIVE: https://t.co/95zJ3pNrf8#OpRussia #OpUkraine pic.twitter.com/SRCKZS4bnv
— Anonymous 🍀 (@DepaixPorteur) March 7, 2022
- Roskomnadzor hack (820 GB)
Roskomnadzor is a Russian federal executive agency responsible for monitoring, controlling, and censoring Russian mass media.
On March 10, Anonymous claimed responsibility for the theft and publication of 820 GB worth of documents from Roskomnadzor. It was released by Distributed Denial of Secrets (DDoSecrets), which is a non-profit whistleblower site and is sometimes referred to as a successor to WikiLeaks.
DDoSecrets publicly listed 364,000 files and databases from Roskomnadzor. The leak revealed a new online surveillance system tracking anti-war sentiment and other threats to Russia and Putin’s regime.
- Central Bank of Russia Hacks, leaked 28GB of Data
On March 26, one of the Anonymous affiliate groups going by the Twitter handle @Thblckrbbtworld leaked 28GB worth of data from the Central Bank of Russia. The data were published by DDoSecrets, exposing records that included years’ worth of financial records such as invoices, memos, bank statements, bank shareholders’ names etc.
Screenshot from the leaked records (Image: Hackread.com)
Trending: Digital Forensics Tool: Email Analyzer
- 900,000 emails leaked from VGTRK
On April 4, DDoSecrets published more than 900,000 emails from the All-Russia State Television and Radio Broadcasting Company (VGTRK), which was hacked by Wh1t3Sh4d0w, an Anonymous actor. VGTRK is the largest-state owned media corporation in Russia and it is accused to be the propaganda arm of the Kremlin.
The emails encompass 20 years’ worth of communications discussing daily operation to issues related to international sanctions against Russia.
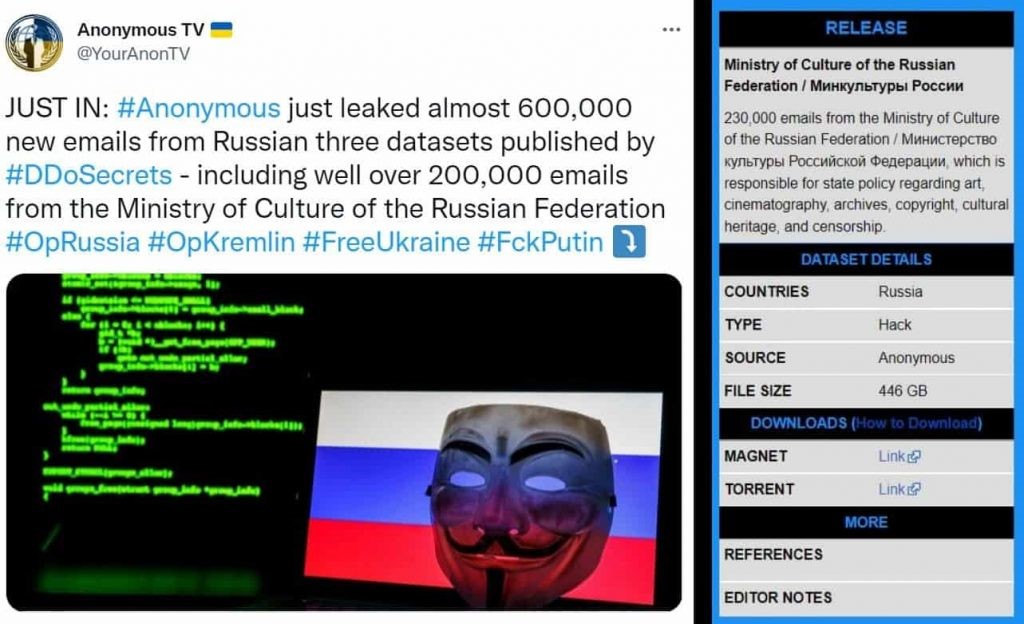
- 446 GB of data leaked from Russian Ministry of Culture
DDoSecrets leaked the 446 GB of data stolen by the Russian Ministry on the 12 of April which was acquired by the Anonymous group. The ministry manages state policy about cinematography, art, copyright, censorship, etc. The data revealed that among other information leaked, included 30,000 emails from the Ministry.
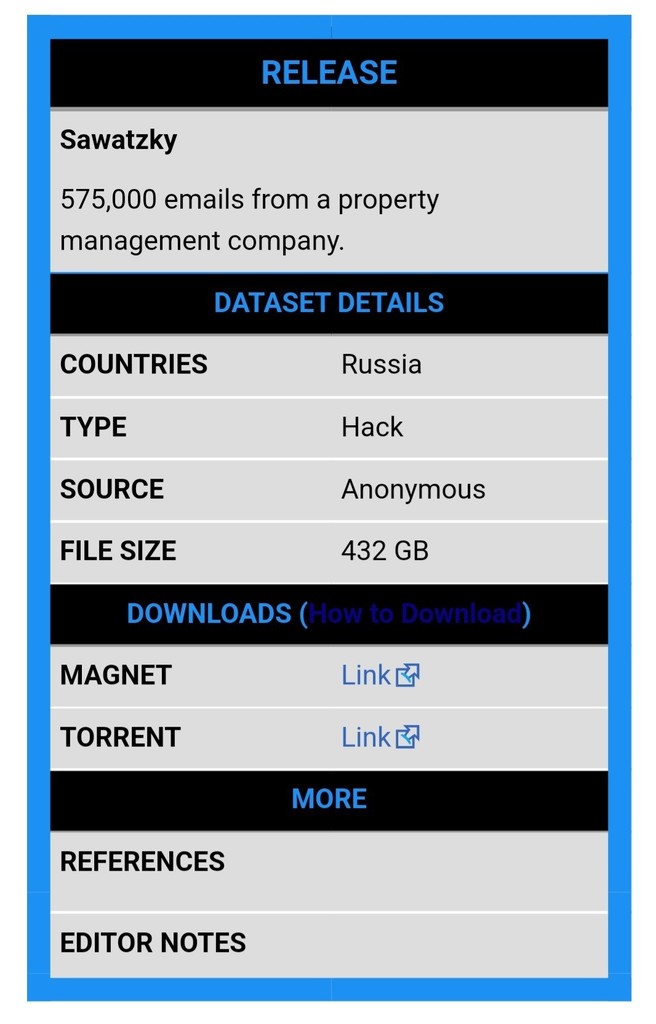
- Over 1 million emails leaked from Worldwide Invest, Sawatzky, Tendertech.
On April 20, DDoSecrets published 250,000 emails leaked from Worldwide Invest and 575,000 emails from Sawatzky. Worldwide Invest is an investment firm with ties to Russian railways and Sawatzky is a property management company.
On the day after, DDoSecrets released 426,000 new emails from Tendertech that was hacked by Anonymous. Tendertech is a firm specializing in processing financial and banking documents on behalf of businesses and entrepreneurs.
JUST IN: #Anonymous released via #DDoSecrets 426,000 new emails (160 GB) from Tendertech, a firm specializing in processing financial and banking documents on behalf of businesses and entrepreneurs. #OpRussia #StandWithUkraine #FckPutin ⤵️ https://t.co/S7AbeScu9N
— Anonymous TV 🇺🇦 (@YourAnonTV) April 19, 2022
- 480 GB of files leaked from CorpMSP
DDoSecrets published 480 GB of files from the Russian government organization CorpMSP on May 5th, 2022. The hack was made by Anonymous Collective @NB65. The leak included 75,000 files, emails, and pictures.
NB65 is a part of a global hacktivist collective and the hack was made because CorpMSP allegedly used as the front for digital espionage in Russia.
- RuTube and Qiwi hacks
On May 9th, which is the victory day in Russia, the video streaming service RuTube was hacked by Anonymous making the streaming service unavailable. Anonymous also claimed that 75% of the databases and 90% of their backup have been significantly damaged. Furthermore, on May 1st, NB65 hacked the Russian payment provider Qiwi.
NB65 claimed to managed to extract 10.5 TB of data that included payment records, credit cards, and personal information about Qiwi customers. They further infected Qiwi with ransomware and threatened to release more customer records after the 3-day ransom contract period expires.
Trending: Offensive Security Tool: Pycrypt
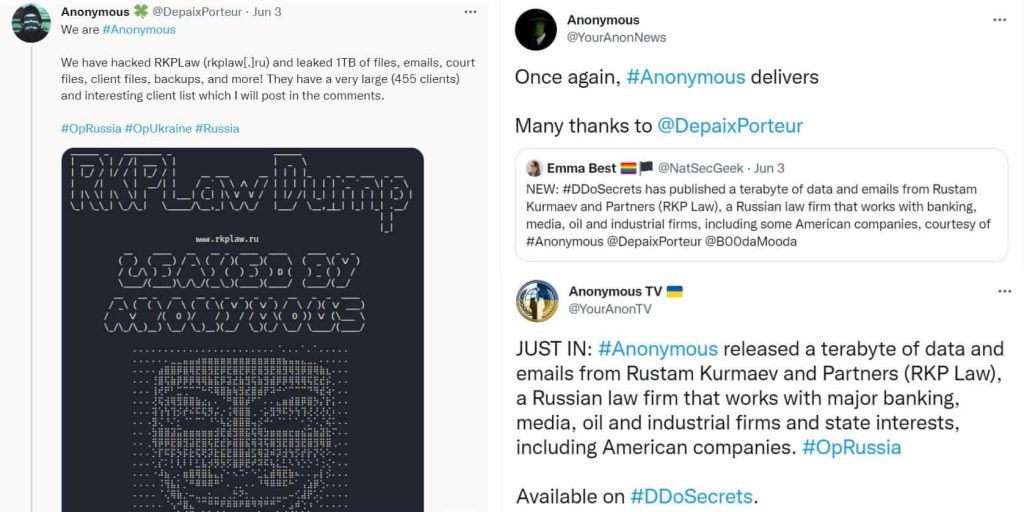
- 1 TB of data leaked from Rustam Kurmaev and Partners (RKPLaw)
Anonymous actors DepaixPorteur and B00daMooda hacked RKPLaw while the DDoSecrets website published the 1TB worth of data. RKPLaw is a Russian kaw company that works with large banking media, energy, and industrial enterprises.
The data contained emails, court files, payment information, backups, classified data, and more.
- Russian taxi service Yandex Taxi hack
Yandex taxi is considered the largest taxi service in Moscow. Anonymous collective hacked the Yandex Taxi servers causing a traffic jam in the center of Moscow when dozens of taxis were sent to the same location, the jam lasted up to three hours.
It isn’t clear why they hacked Yandex but it may be that Yandex Taxi is operated by Russia’s largest IT corporation Yandex, which is equivalent to the Russian Google.
Europe sanctioned the company’s co-founder Arkady Volozh because Yandex was accused of de-ranking and removing content critical of the Kremlin, content related to Russia’s war against Ukraine.
‼️#Moscow had a stressful day yesterday. The largest taxi service in Russia 'Yandex Taxi' was hacked by the #Anonymous collective. A traffic jam took place in the center of Moscow when dozens of taxi were sent by the hackers to the address on Kutuzovsky Prospekt. #OpRussia pic.twitter.com/6fp1hp0f7r
— Anonymous TV 🇺🇦 (@YourAnonTV) September 2, 2022
The aforementioned attacks were only a part of what the Anonymous collective did during the ongoing OpRussia operation.
Lessons to be learned
Operation Russia has already raised global awareness of the dangers of being hacked. Those attacks can no longer be virtual consequences, as online hacking activities can now be linked with real-world effects. As the campaign continues it raises questions about the possibility of similar attacks to other countries, or even worse attacks that may target nuclear power plants as Stuxnet did 12 years ago.
Ransomware attacks becoming more sophisticated than ever, targeting cloud backups, and servers which resulted in targets being unable to restore their data. Offline backups have witnessed a resurgence in case of online backups are compromised.
Furthermore, security companies are advising companies and organizations to schedule server updates as soon as they have been released because of how many attacks have been successful due to outdated systems.
All these come as a reminder of why organizations need more and continuous investing in cyber/offensive security technologies to better protect themselves against such attacks in the future.
See Also: A primer on OS Command Injection Attacks
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]