Optimize your Bug Bounty approach, Key Factors for choosing Ideal Programs

Reading Time: 4 Minutes
Introduction
In the dynamic landscape of bug bounty hunting, success isn’t merely about the quantity of vulnerabilities discovered, but the strategic utilization of time and resources. So, it can be said that success is cultivated by a unique set of qualities that go beyond technical expertise. A bug bounty hunter embodies dedication, persistence, patience, and an immense appetite for curiosity to uncover vulnerabilities.
The ability to choose the right bug bounty program is a critical skill, often ranking among a bug bounty hunter’s most valuable asset. In a landscape where time management and efficiency reign supreme, the strategic selection of programs becomes paramount on every hunter’s list of priorities.
This article serves as a compass in this ever-evolving domain, offering a guide to maximizing one’s potential and efficiency in choosing the right bug bounty program. We’ll explore key topics about the programs such as discerning accepted vulnerabilities, scope challenges, and payout intricacies while also looking into the balance of competition, the charm of new/private programs, and the importance of community engagement.
Triagers Be Kind, Don't close reports duplicate just by reading title of report
"BugHunter's struggle is real" #bugbountylife pic.twitter.com/QwLzY4kVDx
— Bug Bounty – Memes (@bugbounty_memes) September 18, 2023
Attacking the Scope
Most times, organizations and bounty programs have unique threat modeling and tend to follow the basic progression in terms of scope in the beginning. Starting with a narrow scope, such as focusing on a primary domain with limited vulnerability types. As security measures mature, the scope tends to broaden, encompassing additional domains and vulnerability types.
Focusing on your strengths
Identifying organizations with a higher level of security maturity can lead to more fruitful outcomes. A bug bounty program that embraces a wide range of vulnerability types is particularly advantageous. For instance, if your expertise lies in injection attacks such as SQL injection (SQLi) or Blind SQL, dedicating your time to a program that includes these vulnerabilities could be more beneficial. Focusing on specific vulnerability types within a program’s scope can significantly enhance your chances of success. Instead of pursuing more generic vulnerabilities with less specialization, targeting areas where you have expertise, may result in the discovery of 1-2 impactful bugs. Specializing in the types of vulnerabilities a program actively seeks can be a strategic approach, maximizing the efficiency and effectiveness of your bug-hunting efforts.
See Also: The Bug Bounty Hunting Course
A Practical Guide to Hacking Techniques for finding Top Bugs.
A Diverse range of eligible Bug Bounty Targets
A bug bounty hunter benefits significantly from a larger and more expansive scope within a bug bounty program. A broad scope increases the potential surface area for exploration, presenting hunters with a diverse range of targets to attack.

The breadth of the scope encompasses a variety of targets, including web applications, multiple domains/subdomains, mobile applications, APIs, etc.
For example, when a bug bounty program offers eligible bounties on the subdomains of a domain (*.example.com), it becomes significantly more efficient for a hunter to dedicate their time, as the scope broadens, providing ample opportunities to identify and address potential vulnerabilities through the discovery of subdomains linked to a target domain, revealing possible avenues of access for malicious actors.
In general, subdomains frequently bring forth additional avenues for potential attacks that may not be evident within the primary domain, making them valuable focal points for security assessments.
It’s crucial to review the scope and eligible subdomains before initiating any testing. Reporting a vulnerability on an out-of-scope subdomain, even if it impacts the domain, can be a time-consuming effort that yields no results.
Organizations can also gain an advantage by embracing a diverse range of vulnerability types and targets in their bug bounty program. Maximizing effectiveness, and attracting a variety of skill sets in securing their assets.
Payout
VDP issues
Bug bounty programs offer direct financial incentives for discovering vulnerabilities, attracting more attention from skilled researchers due to their competitive nature and specific targets. In contrast, Vulnerability Disclosure Programs (VDPs) focus on providing a structured mechanism for reporting vulnerabilities without guaranteed monetary rewards, often allowing for a broader scope of testing and emphasizing responsible disclosure with legal protections.
VDPs offer a valuable space for novice bug bounty hunters and those testing their automation tools, given the reduced competition and lower bug discovery rates attributed to the absence of financial incentives. However, it is crucial to prioritize engagement with programs that genuinely appreciate your contributions to their security. If a company is not allocating a portion of its revenue to security, it may be wise to steer clear of VDPs, as they do not ensure monetary rewards for the security vulnerabilities you uncover, unlike Bug Bounty Programs.
See Also: Recon Tool: fetchmeurls
High average payouts
Before initiating any form of attack, it’s important to examine the bounty rewards statistics provided by most bug bounty platforms. These statistics vary in depth, with some platforms, such as HackerOne, offering comprehensive analytical insights, while others provide more limited data on payouts. To maximize efficiency and time in terms of payouts, two critical statistics to focus on are the “Average Bounty Range” and “Bounties Paid in the Last 90 Days.” Taking HackerOne as an example, this platform conveniently includes both metrics on the program’s page, facilitating an assessment of the program’s potential value for bug hunters. If a program’s average bounty payout falls below or matches the lowest bounty payout, it often indicates that investing time in that program may not yield significant returns.
Expanding on the significance of the “Average Bounty Range” statistic, it’s crucial to recognize that higher payout programs may not necessarily be more profitable than those with a higher average bounty range. To illustrate this point, let’s consider two comparable bug bounty programs: Coinbase and Paypal.
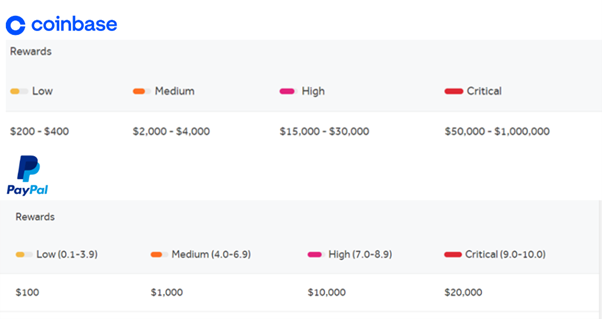
While Coinbase offers substantial payouts for a broad spectrum of vulnerabilities, including low-critical issues, a deeper analysis of the “Average Bounty Range” reveals a notable distinction. The average bounty range for Paypal’s program spans $1900-$4100, whereas Coinbase’s average is merely $200, mirroring its lowest payouts. This discrepancy could result from a variety of factors, such as a de-escalation of bug severity (i.e., critical/high bugs downgraded to medium/low) or simply the absence of critical vulnerabilities.
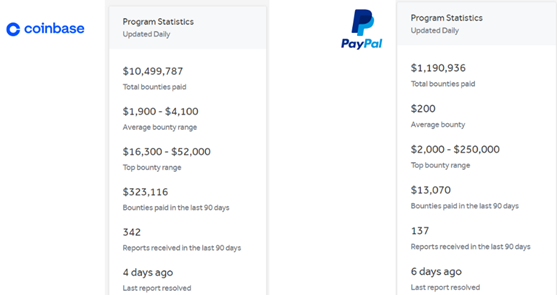
It becomes evident that aiming for programs with higher average payouts, rather than those with the highest individual payouts, is a more strategic approach for bug hunters seeking sustained and more profitable engagements.
It’s worth mentioning the “Bounties Paid in the Last 90 Days” statistic that holds paramount importance as it serves as a real-time indicator of a program’s vitality and engagement with the security research community. A consistently high number of bounties paid over the last 90 days suggests a dynamic and healthy relationship between the bug bounty platform and researchers, instilling confidence in the community.
Given that bug bounty hunting frequently lacks stability as a primary income source for ethical hackers, with 54% of them holding other employment, a significant payout for a single vulnerability may be more appealing to these individuals than the prospect of receiving multiple smaller payouts or, potentially, nothing at all.
See Also: Offensive Security Tool: Nucleimonst3r
Program’s Response Efficiency
Bug bounty hunters waiting to get paid pic.twitter.com/PfMyfegwgY
— Ben Sadeghipour (@NahamSec) September 18, 2023
Numerous platforms, such as HackerOne, Bugcrowd, and YesWeHack, feature a dedicated section highlighting the response efficiency of each program within their platform. It’s a valuable metric to consult before embarking on any testing within a program’s scope. This section provides insights into various aspects, including the number of reports resolved in the current month, average first response times, and the average duration for bug resolution. Analyzing these statistics allows us to gauge the program’s time efficiency in resolving bugs and handling reports.

- Seek out programs with an average time for the first response of less than 24 hours. A program maintaining a consistently swift response time signifies a security team that promptly acknowledges submissions. This not only streamlines the bug reporting process but also aids in effective time management for bug bounty hunters. A quick response informs hunters about the program’s status—whether additional information is required for the report, if the report has progressed to triage, or if it is identified as a duplicate submission.
- An additional measure of a healthy bug bounty program is the average time to bounty, although it can be subject to fluctuations and potential misinterpretation. Given that more intricate vulnerabilities might require extended triage periods, a favorable average time to bounty is generally considered to be less than two weeks. When a program consistently demonstrates the capability to remunerate bug hunters within this timeframe from the creation of the report, it serves as a significant advantage for the hunters. The assurance that the bounty for their efforts will be promptly paid enhances the bug bounty hunter’s overall experience with the process.
It’s essential to recognize that while some programs may offer higher payouts, they could also entail longer average times to payout. The choice between prioritizing faster payouts for a quicker turnaround or opting for larger payouts depends on the individual researcher’s preferences and priorities.
Hack where there’s less competition
Exploring bug bounty programs with less competition presents an intriguing avenue for bug hunters seeking new challenges and increased chances of discovery. Navigating toward lesser-known or recently launched programs offers the advantage of encountering fewer reported vulnerabilities, reducing the likelihood of submitting duplicate reports.
Additionally, targeting private* programs, which are not publicly disclosed and may have a limited pool of researchers, enhances the prospects of finding valid defects that have yet to be identified. Engaging with these newer or private programs not only provides an opportunity to contribute to the security of emerging platforms but also introduces a fresh terrain for bug hunters.
Embracing the less-traveled paths in the bug bounty programs not only diversifies a bug hunter’s portfolio but also opens doors to untapped opportunities.
*Numerous platforms feature exclusive private bug bounty programs, where a select group of researchers is chosen. The selection process often takes into account a researcher’s track record, past contributions, and demonstrated expertise in specific domains.
Last Thoughts
Navigating the bug bounty landscape requires more than technical expertise—it demands dedication, persistence, and strategic program selection. This guide explores key elements like accepted vulnerabilities, scope challenges, and payout intricacies. Prioritizing programs with higher average payouts, responsive handling, and less competition enhances efficiency and profitability for bug hunters. As the cybersecurity landscape evolves, these strategic choices and a commitment to learning remain pivotal for success in bug bounty hunting. Nonetheless, embracing involvement with the hacking community, is also a vital step, sharing your bug-hunting journey, accomplishments, missteps, and problems within the community can yield unexpected but valuable support and mentorship.
Nevertheless, if you are just starting out and you do not have any specialization but is merely a beginner, it’s good to work on any program that is smaller, not for the reward but for practice and experience. The Recon quality of your work plays a very important role in addressing and finding more results than others. If you want to learn more about bug bounty hunting, we offer a lot of videos on our Patreon Page but also a course dedicated to Bug Bounty Hunting here. You can also join our Discord community for real-time discussions, collaboration, and valuable insights from seasoned bug bounty hunters.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]