Steganography – How images can hide secret messages in plain sight
Steganography is the practice of hiding secret messages in otherwise non-secret mediums. It’s different than cryptography where is the idea of encrypting a message…
Gary McKinnon and the “biggest military computer hack of all time”
Gary McKinnon, a 36-year-old computer hacker, was accused of hacking into 97 computers belonging to the U.S. Army, Navy, Air Force, Department of Defense, and NASA.
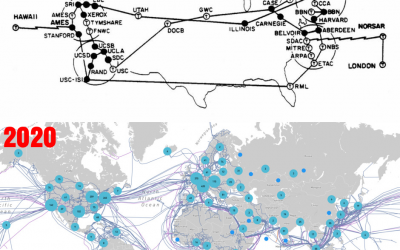
The history of Internet and how it became a worldwide “thing”
Kevin Mitnick – Once the world’s most wanted hacker, now he’s getting paid to hack companies legally
Kevin Mitnick, once called the “Most-Wanted hacker”, is an American security researcher who was born in Los Angeles in 1963.
Reverse Engineering-Hacking Tools
Reverse engineering involves dissecting objects, both physical and digital, to comprehend their inner workings, enabling us to replicate, enhance, or secure them. We’ll explore essential tools such as Ghidra, Binary Ninja, Apktool, and Javasnoop, which empower engineers and security experts to unravel and optimize software.
The Dark Side of IoT: How Cybercriminals Exploit IoT Devices
In this article, we’ll explore the increasing proliferation of IoT (Internet of Things) devices and the associated cyber threats. We’ll discuss underlying vulnerabilities in firmware, including hidden backdoors, unauthenticated access, weak authentication, and the challenges associated with securing update mechanisms.
First steps to take after being infected with a Ransomware
Data Privacy & Data Protection: Interconnected, yet one doesn’t secure your Data
The Evolution of Malware
Malware encompasses a wide range of software designed to inflict damage or gain unauthorized access to computers and networks. Today’s malware landscape has evolved into a complex web of threats that target personal and corporate systems.