Post-Exploitation Techniques: Maintaining Access, Escalating Privileges, Gathering Credentials, Covering Tracks

Reading Time: 6 Minutes
Introduction
Post-Exploitation is a crucial stage in the overall Red Teaming and Pentesting process, where the attacker has already successfully gained access to a target’s system and wants to maintain access, escalate privileges, or gather sensitive information. It involves executing various activities to evade detection and maintain persistence, allowing the attackers to continue their activities within the system.
In this article, we’ll show some of the important different techniques of the post-exploitation phase.
See Also: Write up: Exploiting LFI Vulnerabilities
Prerequisites
Techniques
Maintaining Access
The first step after gaining access to a target system is to ensure that access remains viable even after the initial breach. Attackers do this by creating a backdoor, which is a type of malware that enables them to access the system without having to repeat the original attack.
The backdoor can be a standalone application or a modification to an existing system file, service, or process. Attackers use sophisticated techniques to hide the backdoor from detection, such as using obfuscation, encryption, or polymorphism. Once the backdoor is in place, the attacker can log in to the system whenever they want, exfiltrate data, or execute additional commands.
Escalating Privileges
Escalating privileges is the process of gaining higher levels of access within the target system, which allows the attacker to perform more advanced actions. This can be done by exploiting vulnerabilities in the system’s security or by tricking legitimate users into giving up their credentials.
For example, if the attacker gains access to a system with limited privileges, they may attempt to use a privilege escalation exploit to gain administrator-level access. They may also use social engineering tactics, such as phishing or spear-phishing, to trick users into providing their login credentials. Once the attacker has escalated their privileges, they can perform more advanced attacks, such as installing rootkits, stealing sensitive data, or even taking over the entire system.
Gathering Information
Information gathering is a critical part of post-exploitation. Once the attacker has gained access to a system, they can begin collecting sensitive information, such as user credentials, network topology, system architecture, and security policies. They can also monitor user activity to identify potential targets for future attacks.
The attacker can use various tools and techniques to gather information, such as network scanners, port scanners, password crackers, keyloggers, and packet sniffers. They may also leverage the information they gather to launch more sophisticated attacks, such as lateral movement or data exfiltration through browsers using LaZagne.
See Also: So you want to be a hacker?
Offensive Security Courses
The LaZagne Project

The LaZagne project is an open-source application and is capable of extracting a wide range of credential types, including passwords stored in web browsers, email clients, remote desktop tools, and more on a compromised system that works as a first-level post-exploitation module.
The first level of post-exploitation modules is typically focused on maintaining access and gathering information from the compromised system as quickly as possible. These modules are designed to give the attacker a foothold in the system and enable them to remain undetected for as long as possible.
Mimikatz

Mimikatz is a powerful post-exploitation tool that has been widely used in Penetration testing and red team operations. It is designed to extract sensitive credentials, such as passwords and hashes, from Windows compromised systems. Despite the numerous security improvements made in recent versions of Windows, Mimikatz can still be used to extract credentials from Windows 11 systems. This is because it targets the underlying security architecture of Windows, which has not changed significantly in recent versions.
One of the key features of Mimikatz is its ability to bypass the Windows Credential Guard feature, which was introduced in Windows 10 to protect user credentials from such attacks. However, researchers have found that it can still be used to extract credentials from Windows 11 systems even when Credential Guard is enabled.
Another reason why Mimikatz still works on Windows 11 is that it can take advantage of weaknesses in other security features, such as the Windows Defender Antivirus. For example, it can use a technique called “process injection” to inject its code into trusted system processes, which can help it evade detection by antivirus software.
It’s important to note that Microsoft is constantly working to improve the security of its Windows operating system, and future updates may include new security features that make it more difficult to use tools like Mimikatz to steal credentials.
The idea is not always to use Mimikatz, but to create your own privilege escalation manually, but also extract passwords and steal tokens, because some setups can be different from others, and you have to rely on your expertise to overcome them.
See Also: Offensive Security Tool: Pypykatz
Covering Tracks
Covering tracks is a crucial stage in the post-exploitation process, employed by skilled attackers to meticulously erase any traces of their presence on the target system. By doing so, they aim to elude detection by vigilant system administrators and advanced security software.
To achieve this goal, attackers employ a wide array of sophisticated techniques, each designed to obfuscate their activities and impede forensic analysis. Among the commonly used methods is the deletion of log files, manipulation of system timestamps, alteration of file attributes, and the cunning placement of deceptive artifacts to misdirect investigators. Additionally, attackers may deploy insidious rootkits or elusive backdoors to effectively cloak their actions from security software, further complicating the discovery process.
By executing these intricate cover-up strategies, attackers effectively erase digital footprints, leaving investigators with a formidable challenge in uncovering the true extent of the breach. The ability to cover tracks showcases the expertise and adaptability of red team professionals, as they employ their intricate knowledge of system vulnerabilities to bypass defenses and vanish without a trace.
Technical Part
Using Kiwi: Metasploit’s Post-Exploitation Tool
Kiwi is a powerful tool used in Metasploit to perform post-exploitation tasks on a compromised system.
Once a Meterpreter session has been established on a target system.
To make use of the get system command, if it’s not already loaded, we will need to first load the ‘priv’ extension.
meterpreter > use priv
Loading extension priv...success.
meterpreter >
Kiwi can be used to extract user credentials and manipulate the Windows authentication protocols to escalate privileges or move laterally within the network.
See Also: Offensive Security Tool: SSRFPwned
meterpreter > load kiwi
In the past, Metasploit included a Mimikatz module that enabled penetration testers to execute the tool on compromised systems. However, due to legal and ethical concerns, the Mimikatz module was removed from Metasploit in 2018. As a replacement, the Kiwi module was introduced. Like Mimikatz, Kiwi is capable of extracting credentials from compromised systems, but it is a completely different tool and has a different set of capabilities. Kiwi is also actively maintained and updated by its developers, making it a more reliable and sustainable option for penetration testers. Overall, the switch from Mimikatz to Kiwi in Metasploit was driven by the need for a more legally and ethically sound post-exploitation tool.
The kiwi_cmd sekurlsa::logonpassword command is used with the Kiwi post-exploitation tool to extract password data from the Security Account Manager (SAM) database on a compromised Windows system. The SAM database is where Windows stores user account information, including hashed passwords. When a user logs in to a Windows system, their password is compared to the hashed value in the SAM database to determine if it matches.
The sekurlsa::logonpassword module in Kiwi is designed to extract the hashed password data from the SAM database, and then use various techniques to decrypt and display the password in clear text format. This module can be extremely useful for penetration testers and red team operators who need to escalate their privileges and move laterally within a compromised network. However, it is important to note that the use of such tools should only be performed with appropriate legal and ethical considerations, and with the consent of system owners or authorized personnel.
meterpreter > kiwi_cmd sekurlsa::logonpassword
The kiwi_cmd sekurlsa::logonpassword and kiwi_cmd sekurlsa::msv commands in the Kiwi post-exploitation tool are both used to extract credential data from a compromised Windows system. However, they extract different types of credential data from different sources within the system.
The sekurlsa::logonpassword module is specifically designed to extract password data from the Security Account Manager (SAM) database on a compromised Windows system. The SAM database is where Windows stores user account information, including hashed passwords. When a user logs in to a Windows system, their password is compared to the hashed value in the SAM database to determine if it matches. The sekurlsa::logonpassword module is capable of extracting the hashed password data from the SAM database and then using various techniques to decrypt and display the password in clear text format.
meterpreter > kiwi_cmd sekurlsa::msv
On the other hand, the sekurlsa::msv module is designed to extract MSV (Microsoft Security Account Manager) authentication package data from the memory of a compromised Windows system. MSV is an authentication package that is used by Windows to validate user credentials during the login process. The sekurlsa::msv module is capable of extracting the MSV authentication package data from memory and then using various techniques to display information such as usernames and hashed passwords in clear text format.
So, the main difference between the two modules is that sekurlsa::logonpassword extracts password data from the SAM database, while sekurlsa::msv extracts authentication package data from memory. Both modules can be useful for extracting credential data in different scenarios, and the choice of which module to use will depend on the specific requirements of the penetration testing or red team operation.
meterpreter > kiwi_cmd sekurlsa::kerberos
Kerberos is an authentication protocol used by Windows systems to authenticate users and provide secure communication between applications and services. When a user logs in to a Windows system, their authentication credentials are encrypted and stored in a Kerberos ticket. The sekurlsa::kerberos module in Kiwi is designed to extract the Kerberos ticket data from memory and then use various techniques to display information such as usernames and authentication data in clear text format.
This module can be particularly useful for penetration testers and red team operators who need to escalate their privileges and gain access to sensitive resources within a compromised network. By extracting Kerberos ticket data, an attacker can potentially impersonate a valid user and gain access to resources that are protected by Kerberos authentication.
Using LaZagne: A Python-Based Post-Exploitation Tool
One of the key features of LaZagne is that it is a Python-based tool that is capable of being executed in memory without leaving any traces on the compromised system’s disk. This means that the tool can be used to extract credential data without being detected by traditional antivirus software or other security measures that may be in place on the system.
Another advantage of LaZagne is its cross-platform compatibility. It can be used on both Windows and Linux systems, making it a versatile tool for post-exploitation activities on a variety of different target environments.
LaZagne can be used in conjunction with Metasploit to perform post-exploitation activities on a compromised system. One way to use LaZagne in Metasploit is to first upload the tool onto the compromised system using a Meterpreter session.
Once LaZagne is uploaded, it can be run from within the Meterpreter session to extract credential data from the system.
meterpreter > upload /root/Downloads/LaZagne.exe
To do this, the first step is to use the upload command in Metasploit to upload the LaZagne tool onto the compromised system via the Meterpreter session.
Once the file is uploaded, the next step is to use the shell command to create a shell session from within the Meterpreter session.
meterpreter > shell
From the shell session, the LaZagne tool can then be executed and used to extract credential data from the compromised system.
> LaZagne.exe all
Collecting password credentials from browsers by running LaZagne.exe access to a host via a shell. It is non-interactive and can be run in even the most bare-minimum of shells. Since the focus of this article is the standalone Windows PE. We could specify which module we want to use, but it also includes a convenient all option. Obviously, I want all the passwords I can get my hands on, so I’ll be using LaZagne with all options.
In a Windows system, every interaction is recorded as event logs, which are classified into three categories: application, security, and system logs. These logs serve as a crucial source of information for administrators and investigators, especially in cases of system failures or security breaches.
Consider a hypothetical scenario in which a Windows host has been compromised via a vulnerability. The attacker then leverages Meterpreter to upload new files onto the system, escalates privileges, and attempts to add a new user. However, these actions leave traces in the event logs, which could potentially lead to detection.
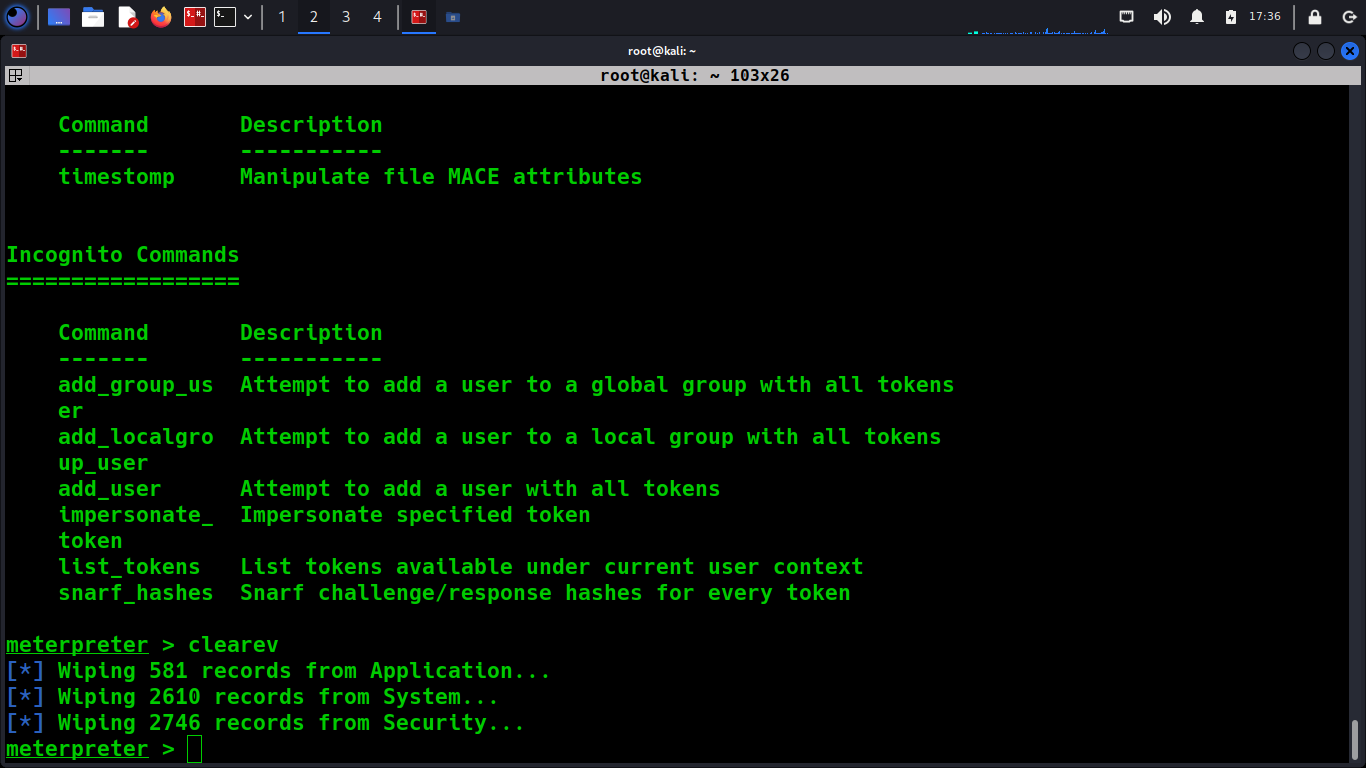
As a malicious actor, it is imperative to remain undetected after gaining unauthorized access to a system using ‘clearev’ command in Metasploit. Hence, it is crucial to avoid leaving a trail of actions in the event logs.
Conclusion
Blue Team’s Perspective
From a defensive standpoint, organizations must proactively fortify their systems against the insidious threats posed by tools like Mimikatz and other post-exploitation activities. By implementing robust access controls, segmenting networks, and maintaining vigilant monitoring practices, they can effectively mitigate the risks of data breaches and safeguard their valuable sensitive information.
First and foremost, enforcing strong access controls is paramount. Organizations should adopt multifactor authentication, strict password policies, and role-based permissions to ensure that only authorized individuals can access critical resources. By limiting privileges to essential personnel and regularly reviewing access rights, organizations can minimize the potential for unauthorized exploitation.
Segmenting networks plays a pivotal role in containing the impact of an attack. By segregating critical systems and sensitive data from the rest of the network, organizations can limit lateral movement and prevent an intruder from gaining widespread access. Network segmentation also enables the implementation of more granular security controls, reducing the attack surface and enhancing overall resilience.
To effectively counter post-exploitation activities, organizations must adopt a proactive and continuous monitoring approach. By deploying robust intrusion detection and prevention systems, security teams can detect and respond swiftly to suspicious activities. Real-time log analysis, anomaly detection, and threat intelligence integration can provide valuable insights into ongoing attacks, enabling organizations to take immediate remedial actions and prevent further compromise.
Regularly conducting comprehensive security audits, vulnerability assessments, and penetration testing is crucial. These proactive measures help identify potential weaknesses in systems and provide an opportunity to address them before malicious actors can exploit them. Additionally, staying abreast of emerging threats and maintaining up-to-date security patches and configurations is imperative to mitigate the risks associated with known vulnerabilities.
Furthermore, investing in employee education and awareness programs is vital. Human error remains a common entry point for attackers. By training employees on secure practices, and promoting a culture of Cyber Security and Offensive Security, organizations can create a resilient human firewall that actively contributes to the overall defense posture and protect the integrity of their sensitive information.
Red Team’s Perspective
Post-exploitation represents a pivotal phase within the Pentesting or Red Teaming process, offering a unique opportunity to identify security vulnerabilities and enhance defensive measures. This stage goes beyond merely breaching the system; it delves into simulating real-world attack scenarios, equipping organizations with invaluable visibility and insights to effectively minimize the risks associated with potential Cyber Attacks.
By engaging in post-exploitation activities, Red teams replicate the tactics, techniques, and procedures (TTPs) employed by malicious actors in a controlled environment. This simulation not only exposes weaknesses in the organization’s defenses but also provides an in-depth understanding of the attacker’s mindset, methodologies, and potential avenues of exploitation.
Furthermore, post-exploitation activities offer a comprehensive evaluation of the organization’s incident response capabilities. By emulating the actions of skilled adversaries, red teams can gauge the effectiveness of detection and response mechanisms, identify gaps in processes, and enhance the overall incident response posture. This invaluable feedback helps organizations refine their incident-handling procedures, implement timely mitigation strategies, and bolster their resilience against emerging threats.
Moreover, post-exploitation exercises deliver novel visibility and insights that may not have been previously apparent. By navigating through the system undetected and escalating privileges, red teams uncover hidden vulnerabilities, misconfigurations, or weak security controls that might have evaded traditional testing methodologies. This newfound knowledge empowers organizations to proactively address these weaknesses, fortify their defenses, and ultimately improve their security posture.
Importantly, the post-exploitation phase serves as a catalyst for organizational growth and continuous improvement. It serves as a proactive approach to identifying and addressing security gaps, providing a platform for ongoing collaboration between the red team, security teams, and key stakeholders. Through the exchange of findings, organizations can adapt their defensive strategies, fine-tune their security policies, and allocate resources effectively to mitigate potential risks.
In essence, post-exploitation activities, from a Red team’s perspective, are not solely focused on breaching systems. They represent a critical component of the overall testing process, enabling organizations to comprehensively evaluate their defenses, gain valuable insights into attack methodologies, and enhance their incident response capabilities.
We hope that this write up has taught you something new. If you enjoyed it, the best way that you can support us is to share it! If you’d like to hear more about us, you can find us on LinkedIn, Twitter, YouTube.
Are you a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]