SolarWinds Supply Chain Hack – The hack that shone a light on the gaps in the cybersecurity of governments and big companies

Reading Time: 3 Minutes
SolarWinds as a company
SolarWinds is a Texas-based IT company that was ranked top in the Forbes’ annual ranking of America’s Best Small Companies in 2012, which highlighted companies that experienced strong growth over the past five years The company now is involved in one of the biggest cyber hacks in recent history. The attack targeted the US government, some of its agencies, and other private companies. The hack even extends into the fields of cyber espionage, geopolitics, national security and it seems to be a global cyberattack.
SolarWinds hack first discovered by FireEye

The FireEye logo is seen outside the company’s offices in Milpitas, California, REUTERS/Beck Diefenbach/File Photo
It was discovered by the cybersecurity company FireEye on December 8, and since then, more developments continue to come to light every day while the sheer scale of the attack remains unknown. More than 40 organizations have been targeted including the US energy defense state, US Department of Justice, and homeland security departments.
SolarWinds Hack and affected agencies and companies.
The sophisticated state-backed attack was taking place undetected for nine months and has exploited vulnerabilities in the SolarWinds software with the main target to spy on government and business networks around the world including the US, UK, Israel, and Canada.
FireEye CEO Kevin Mandia wrote in a post that the company was attacked by a “highly sophisticated threat actor”, thus calling it a state-sponsored attack with many speculations arise that the attack was orchestrated by Russia.
On December 13, FireEye said that the attack likely began in March 2020 and has been ongoing for months and the scale of the attack is still being unknown.
The use of SolarWinds as a medium to attack the government and organization’s network is called a “Supply Chain” attack where the attackers targeted the third-party vendor’s (SolarWinds) IT management software called Orion used by those agencies and organizations, instead of directly attacking them.
Around 18 thousand clients have been impacted according to SolarWinds which incidentally deleted the list of clients from its websites, but the list was scrubbed from web archives and includes around 400 companies in Fortune 500, 10 telecom operators in the US along with parts of the Pentagon, State, and Justice Department.
Microsoft statement has already confirmed that their source code has been affected by the ongoing cyber-attack admitting that hackers accessed some of it.
The US Department of Justice also confirmed that 3% of O365 mailboxes appear to be accessed and have no indication of impacted classified systems.
How the attack happened – timeline of the supply chain attack
According to FireEye, the attackers penetrated their victims’ defenses via trojanized updates of the Orion IT monitoring and management software. They injected a malicious code if (Sunburst malware) into the software updates of the Orion product. The important thing here is that the malware went undetected from the anti-virus of the companies and resulted in as many as 18 thousand SolarWinds clients to update their software and unwittingly installing a hidden backdoor in their systems and networks for the attackers. This had, as a result, to collect all the data on its victims and send them back to the attackers.
Then, depending on the importance of the compromised victim, the attackers deployed a Teardrop backdoor trojan (more powerful than Sunburst) on the victims’ systems and at the same time, instructed the Sunburst malware to delete itself, avoiding detection. CrowdStrike, one of the companies involved with the ongoing investigation said that it identified a third malware strain, named Sunspot. The malware was the first one to be used for the attack, and deployed in September 2019, signaling the first breach in the SolarWinds Network.
The Sunspot malware was installed on SolarWinds build servers and had the purpose to observe the build server to build commands that assembled the Orion software. Once the build command was detected, the malware would replace source code files of the Orion software with the files that loaded the Sunburst malware, which later will be also installed on the victims that will update their Orion platform. On January 11th, 2021, SolarWinds published a timeline of the attack, revealing that before the Sunburst malware was deployed to customers between March and June 2020, that from September to November of 2019 the attackers executed a test run for their attack.
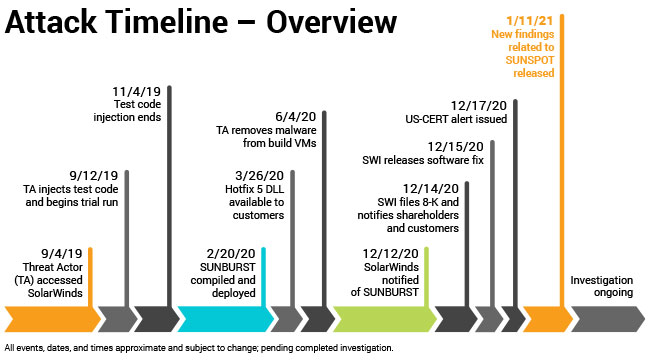
The Timeline of The Attack
Kaspersky which is not part of the investigation on the attack also analyzed the source code of the Sunburst malware and found overlaps with Kazuar malware, which is linked to the Turla Group, a Russian state-sponsored cyber-espionage group. However, Kaspersky used careful language and said that only found code overlaps between Sunburst and Kazuar malware and that they don’t necessarily believe that the Turla group was behind the SolarWinds attack.
An attack of such ingenuity and scale can only be made by a state-backed operation and many US Advisors like Tom Bossert, believe that Russia is behind the wheel of this attack while FireEye has not yet named Russia as being responsible until the ongoing investigation with the help of FBI, Microsoft and other partners conclude. Compromised communications at the US Treasury and other federal agencies where hackers leveraged techniques to impersonate trusted users and access highly sensitive information according to an advisory published by the NSA. Due to the time passed since the attack happened in March 2020, the forensic evidence could be damaged and destroyed making it highly complex for the victims to estimate and eliminate the damages.
SolarWinds Warning by an advisor in 2017
A cybersecurity advisor, Ian Thornton-Trump warned SolarWinds of a potential ‘catastrophic’ hacking attack if the company didn’t increase their internal security measures in 2017 according to a New York Times report.

Ian Thornton-Trump, a former cybersecurity adviser at SolarWinds
Staffers of the newspaper said that the CEO of SolarWinds cut security measures to save costs and moved several engineering offices closer to Easter Europe. The move made the company vulnerable to the breach as some of the compromised software was engineered there and Russian intelligence operatives are rooted in that region of Europe.
The cut of common security practices is said to tripled SolarWinds’ annual profits from 150 mil. in 2010 to 450 mil. in 2019.
SolarWinds also moved much of its engineering offices in the Czech Republic, Poland, and Belarus, where engineers had access to the Orion network management software that was hacked.
Officials stated that the hack began in March of 2020, but SolarWinds revealed after that, that they traced hackers back to October 2019, where it’s believed that hackers tested their ability to insert malicious code into their system.
Russia as the main culprit?
Many experts believe that the attack bears hallmarks of the 2016 US Elections where the Russian interference was unprecedented. Investigators say that found clues in the hackers’ language and coding that pointed to Russian attackers. Some of the investigators also pointed at APT29, a prolific hacker group backed by SVR (Russian’s Foreign Intelligence Service) that has previously linked to the leaked emails ahead of the 2016 US election.
What have SolarWinds and the US government said about the hack?
SolarWinds’ share price has fallen by almost 50% since, and SolarWinds, recommends that all customers should immediately update the existing Orion software.
SolarWinds also added: “If attacker activity is discovered in an environment, we recommend conducting a comprehensive investigation and designing and executing a remediation strategy driven by the investigative findings and details of the impacted environment” Customers unable to update the software should isolate SolarWinds servers and block all internet egress from them, with a bare minimum suggestion to change the passwords for accounts that have access to those servers.
A joint statement from the FBI, CISA, and the US office of Director of National Intelligence issued and stated what is called UCG (Cyber Unified Coordination Group) to coordinate government response to the crisis.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Unanswered Questions
There are no clear answers on how SolarWinds was hacked in the first place, while SolarWinds has not publicly addressed the possibility of an insider being involved in the breach.
The motive and who is behind it, is still unknown, despite the suspicions of Russia’s involvement to boycott Washington DC, a couple of weeks before Biden’s inauguration and to gain leverage against the US before nuclear arms talks take place.
If Russia’s hacker groups are behind the attack, their strategic objectives are still unknown.
Their goal could be beyond reconnaissance, and speculations arise that their goal could be to put Russia in a position to have leverage over the new US administration.
With Microsoft confirming that hackers accessed some of its source code it is still unknown how much and what they accessed which leaves speculations of a modifying source code by the hackers.
It could lead to disastrous consequences to businesses and even individuals given the ubiquity of the Microsoft products, including the Office suite and Windows operating system around the world.
Key lessons from the attack and supply chain risks
Supply chain attacks. Credit: nortonrosefulbright
Organizations and companies are seemingly not paying enough attention to the security of their software suppliers. SolarWinds is just an example of a software supplier that improper security measures can lead to unprecedented damages.
Target, a US retailer, was hit by one of the largest data breaches (40 million customer credit cards) where a supply chain attack circumvented the 1.6 million dollars cybersecurity system of the company that’d been installed a couple of months earlier the breach. The malware was injected into the POS system (Point of sale) in over 1800 stores.
There are multiple examples of supply chain attacks in the past from ATM Malware attacks, where the affected automated teller machines could let attackers remove ATM’s system cash vault, to the British Airways website payment section that contained a code that harvested customer payment data.
However, securing the supply chain is hard due to the lack of globally-recognized security standards.
Among other security experts, Thomas Bossert, a former homeland security adviser to President Donald Trump said that the government needs better tools to carry out “deep inspection of network traffic” to detect suspicious activities.
Many experts of the field call for international agreements around responses to global cyber-attacks as a preventive measure.
As you can see from the overall story of the SolarWinds incident, it is inevitable to rely only on the traditional solutions offered when it comes to Cyber Security.
Conclusion
Such sophisticated attacks take place often on real people using social engineering, and a combination of custom written payloads, that infiltrate source codes from third party software. These coordinated attacks, rely on Antiviruses which hackers know how to bypass, got several warnings from the Cyber Security adviser, cutting costs on security measures, affecting governments and companies like Microsoft by getting partial access to their source code, a Software Company, who has over 75 million customers around the globe.
Do not underestimate the threat – Start Acting now.
To follow the SolarWinds security advisory blog page for the latest updates on the investigation, and recommended actions for their affected software versions, click here.
We hope that this write up has taught you something new. If you enjoyed it, the best way that you can support us is to share it! If you’d like to hear more about us, you can find us on LinkedIn, Twitter, YouTube.
Are you a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
References:
⦿ https://en.wikipedia.org/wiki/Supply_chain_attack
⦿ https://www.bitsight.com/blog/fbi-alerts-companies-of-cyber-attacks-supply-chains
⦿ https://thehackernews.com/2020/12/microsoft-says-solarwinds-hackers.html
⦿ https://www.zdnet.com/article/solarwinds-the-more-we-learn-the-worse-it-looks/
⦿ https://www.wired.com/story/russia-solarwinds-hack-roundup/
⦿ https://www.crowdstrike.com/blog/sunspot-malware-technical-analysis/









