Steganography – How images can hide secret messages in plain sight

Reading Time: 12 Minutes
Introduction
Today’s digital world faces a rise in cyber-attacks and hackers are increasingly using steganography as a technique to trick internet users and bind malicious payloads in seemingly “safe” software, files, etc. to bypass security firewalls and scanners. The root “steganos” is Greek for “hidden/cover” and the root “graph” is Greek for “to write”, where the two roots together combine to give something close to “hidden writing”.
Steganography as a practice
Steganography is the practice of hiding secret messages in otherwise non-secret mediums.
It’s different than cryptography where is the idea of encrypting a message that everyone knows has been sent but they can’t decrypt it to find out what it means, steganography on the other hand is the idea of hiding that the message is being sent at all.
When it was first introduced?
Steganography is an ancient practice, an earlier version of it is coming from Ancient Greece when tyrants found ways to deliver hidden messages, to the American Revolutionary War when spies used to hide messages using the invisible link, to famous artists like Da Vinci who embedded secret meanings into his paintings.
Steganography is one of the oldest methods of concealing secret information and it’s believed to be first introduced back in the 5th century B.C in ancient Greece. The tyrant Histiaeus used the technique to hide a secret message written on the head of a servant who shaved his head for the message to be tattooed on him and then delivered his message after the servant’s hair grown back. His message was revealed when the servant’s head was once more shaved.
Steganography in the digital world
In the digital world, it’s the same too as the old days but now it’s a file like an image that can be used to stealthily to encode information in it. It’s a data hiding technique, which aims at delivering a hidden message where some other kind of information is already being delivered, and is generally used in secret communication between acknowledged parties to establish a secured communication in an unnoticeable manner as well as to avoid drawing suspicion to the transmission of a hidden data.
See Also: Write up: Exploiting LFI Vulnerabilities
Types

Text Steganography
In text steganography formatting or by changing certain characteristics of textual elements can be changed. It contains numerous approaches like syntactical, lexical steganography, line-shift coding, open spaces, feature coding, and word-shift coding.
Audio Steganography
It’s a difficult process where the hidden message is embedded into a digitized audio signal in an imperceptible manner. Some methods used for audio steganography are Echo Hiding, Phase Coding, Least Significant Bit, Parity Coding, etc.
Image Steganography
There are different file formats are available for digital images and for these file formats different algorithms exist such as Least Significant Bit, masking, filtering, redundant Pattern Encoding, etc.
Protocol Steganography
Network steganography is a new, more secure, and advanced type of steganography approach for data hiding. Protocol steganography embeds the information using network control protocols like ssh, HTTP, FTP, TCP, UDP, etc.
Video Steganography
Video files consist of an assortment-flow of images and sound making the previous techniques (audio and image steganography) effective and can be applied on video files too but with a major advantage when it comes to hiding a larger amount of data information, as any video is series audio and images together.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Best file formats in Steganography
The main concept when of steganography is to embed hidden information into a larger file format and making sure that is undetectable by humans. All kinds of file formats can be used but the best formats are those with a higher degree of redundancy, which means that the redundant bits inside of the file format are the bits that can be changed without the change being detected easily. The most popular cover objects in steganography are images, which often carry a large amount of redundant data.
Keys in Steganography
There are three types of keys in steganography:
Pure steganography key
It requires no prior exchange of information between the two parties communicating and depends entirely on its secrecy. The algorithms are not publicly known, meaning that no information is required to start the communication process. In most applications, pure steganography is preferred since no key must be shared between parties, although if an attacker knows the embedding method, the security could be compromised.
Private steganography key
The private key in steganography works like symmetric encryption where the key is needed to both embed and extract the hidden message, the secret message can be extracted only if the key is known to the receiver.
Public steganography key
This is similar to the pubic key infrastructure that works in cryptography, It does not depend on the swapping of the private key. It needs two keys, one private and the other public, the public key is stored in a public database whereas the public key is used in the embedding process and the private key is used to extract the secret message.
Basic Steganographic Model
The steganographic model includes the cover file, where it can be the image that will be used as the cover to send the secret message. The steganographic encoder which uses some sort of steganography method to embed the secret message into the cover file, the stego-key is used to embed and extract the secret message (depending on the stego-key method used) providing extra security. The stego-object now looks exactly like the original file (cover file) and, now the sender sends the stego-object through the network.
Then the receiver uses a steganographic decoder and using the key can retrieve the secret message.
Combining with Encryption
For more secure communication the secret message could be encrypted prior to embedding it into the cover file with an encryption algorithm (using an encryption key) and then the cypher text (encrypted secret message) can be embedded into the cover file with a steganographic encoder. Then the stego-object can be delivered through the network and the only difference is when the cover file is decoded through the steganographic decoder (using the stego-key) is that the secret message is in cypher text that needs to be decrypted using the decryption key.
Techniques of Steganography on digital images
Least Significant Bit (LSB) substitution
In information theory and computer science, a bit is the smallest possible (meaningful) piece of information and it’s often expressed as a digit of the binary system 0 or 1. In steganography one of the most well-known techniques for delivering hidden messages in
images is the LSB.
A byte is represented by a string of 8 bits and any string of data can be sent over a network in two ways, left to right or right to left, the two orderings are commonly referred to as Most Significant Bit First (MSB), and Least Significant Bit First (LSB) respectively.


The most significant bit is the bit in a binary sequence that carries the greatest numerical value, for example, take the decimal number 133, the conversion to binary will be 10000101. The most significant digit of 133 will be the leading 1 that determines the greatest part of the number’s numerical value and signifies the thousands, similar to this the leading 1 in the converted binary it’s the most significant bit.
The least significant bit is the right-most bit in the string and it is named like that because it has the least effect on the value of the binary number in the same way as the unit digit in the decimal number, In the case of 133/10000101 the least significant digit is 3 and the least significant bit is the last 1.
To understand the impact of changing the MSB in relation to changing the LSB let’s experiment with the binary number of 133 which is 10000101:
If the MSB of 133/10000101 changes from 1 to 0 (first bit) it becomes 5/00000101 resulting in a huge change in numerical value, from 133 to 5, around 96% change. Whereas if the LSB of 133/10000101 changes from 1 to 0 (last bit) it becomes 132/10000100 resulting in a minor numerical value change from 133 to 132, around 0.75%.
The LSB technique works by replacing some of the information in a given pixel with information from the data in the image. LSB embedding is performed on the least significant bits, minimizing the variation in colors that the embedding creates making the difference (from the original) unnoticeable.
A digital image is made up of thousands or even million individual pixels, they are dots of illumination that together made up an image, each pixel can be one color at a time.
![]()
![]()
The RGB color model has up to 16.7 million colors where Red Green and Blue colors are combing together in various ways to produce a vast amount of colors. An 8-bit(256 colors) image pixel is represented by one byte (8 bits), and for reference a 24-bit (16.7 million colors) RGB image pixel is encoded by 3 bytes (24bits).
In the RGB color model, by mixing Red, Green, and Blue, the pixel can form any color, the color is determined by the number of bits used to represent it. The number of bits that are going to be used to determine the color this time is 8 bits.
One pixel of an RGB image is 24 bits:
![]()
See Also: Offensive Security Tool: SSRFPwned
Applying LSB technique demo
To apply the LSB technique to each byte of an 8-bit image, only one bit can be encoded into each pixel, therefore only 3 bits can be encoded into each pixel of a 24-bit image.
The target is to hide the letter B inside a pixel of an 24-bit image. The binary value of the letter B is 01000010:
![]()
The RGB image pixel before the embedding, in a total of 24 bits or 3 bytes:
![]()
Pixels after embedding of the secret letter B:
![]()
By replacing the LSB of every pixel to embed the secret letter “B”, the stego-image will be Identical to the cover object. On average LSB technique requires that only half of the bits in an image can be changed. The secret message can be also hidden by changing the second least significant bit without major changes in the final stego-image.
How most of the programs encode text to an image
- The program loads the cover image and looks at each of the pixels in hexadecimal value.
- Convers the secret text into bits and stores them in the Least Significant Bit of the pixel bits.
- The program adds, in the end, a delimiter to determine where the text ends.
- To decode the secret text from the image, the program extracts all the 0’s and 1’s until the delimiter is found and the extracted bits are converted into a string – secret text.
Steghide demo using Kali Linux
Install steghide from terminal
Make sure that the machine is fully updated.
Apt-get install steghide
It will install all the related dependencies also. If a different OS is used to install steghide you will most probably experience problems with dependencies so it is recommended to install Kali Linux on a virtual machine or use WSL (Windows Subsystem for Linux) and use the command line option.
To see how it can be used and the embedding, extracting options:
Steghide --help
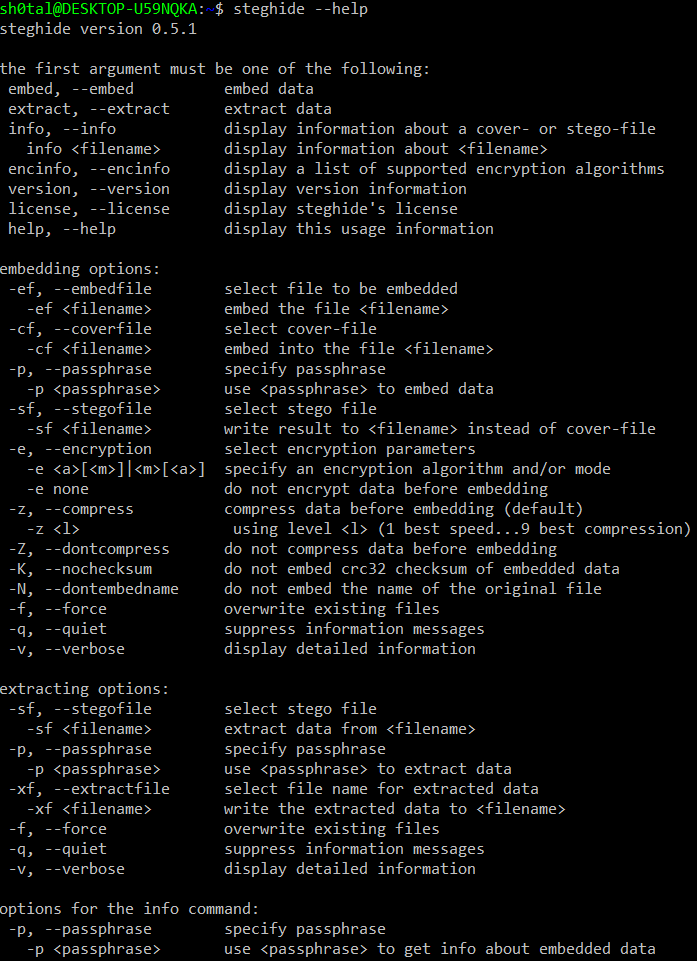
View the description of what the program does:
man steghide

The commands that will be used are embed and extract.
Using the embed command:
-ef, –embedfile: it will specify the file that will be embedded (the file that contains the secret message)
-cf, –coverfile: the file(image) that will have the embedded file(secret message) place into it.
-sf, –stegofile: is the final file where the embedfile is in the coverfile.
-p, –passphrase: the password to embed data
Using the extract command:
-sf, –stegofile: select the stego file to extract the secret message from
-p, –passphrase: the password to extract the hidden message
xf, –extractfile: the extracted file name , the file that secret message from the stego-file will be saved.
Create the secret file
In the terminal type:
nano secretmsg.txt
Type the secret message: e.g. “Secret Message” and save the file.

Download a test picture and save it:
curl https://testimages.org/img/testimages_screenshot.jpg > coverfile.jpg
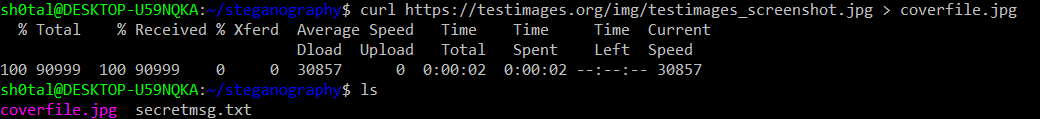
Embed the secret message file into the cover file.
steghide embed -ef /../../secretmsg.txt -cf /../../coverfile.jpg -p testing1
![]()
The coverfile (the file embedded with the secret message) is created and its identical to thecoverfile1 (original coverfile).
The coverfile increased in size by approx. 10Kb more than the original (non stego) coverfile1:
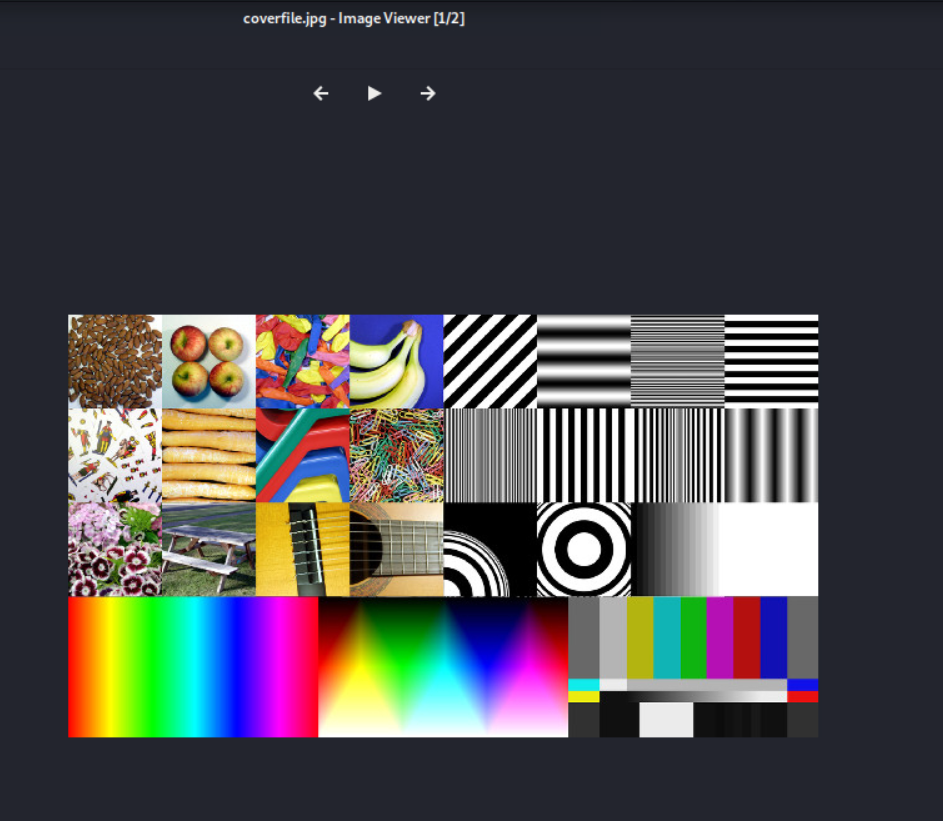
The coverfile now looks the same on the human eye as the original:
Coverfile.jpg
Coverfile1.jpg
It’s worth noting that if the stego-file gets compressed, that may destroy the information hidden inside, if the file is uploaded to a service that compresses it or changes its dimensions for any reason it could result in losing the hidden information.
Extract the hidden message from the coverfile
steghide extract -sf /../../coverfile.jpg -p testing1 -xf /../../secretmsg1.txt
If the xf option is left blank it will by default overwrite the file that it was embedded in the coverfile.jpg, so to view extracted message a different name will be used. (e.g secretmsg1.txt )
![]()
cat the file to cross-check the secret message
cat secretmsg1.txt
![]()
And finally, the secret message is extracted successfully.
List of other tools for Steganography
- OpenStego a straightforward GUI program for data hiding and watermarking.
OpenStego provides two main functionalities:
Data Hiding: It can hide any data within a cover file (e.g. images).
Watermarking: Watermarking files (e.g. images) with an invisible signature. It can be used to detect unauthorized file copying.
- Stegosuite: GUI tool that allows the embedding of text messages and multiple files of any type.
In addition, the embedded data is encrypted using AES.
- Xiao Steganography tool a free Windows software, a hybrid steganography tool that allows users to hide files within image (BMP) or audio (WAV) files.
- Camouflage: a tool that allows any file to be hidden within any other file.
- Ssuite Picsel: a GUI that takes a different approach to image steganography, to embed the secret message the user provides the coverfile and a key image. It requires no password to extract the secret message from the stego-file but it uses the key image to extract it.
Conclusion
Steganography is a proven technique for secret communication and for evading detection while communicating.
LSB embeddings may be detected by using visual inspection of the available image, or with methods which use statistical metrics to identify if the image contains hidden data, however, it can’t be easily decoded and it’s even more difficult to locate stego-files in the billions of files available on the internet.
The power of steganography shown in this article has only scratched the surface of what you can do with it, but as the need to communicate secretly in the future will always be relevant and will play an important role in secret communications, the knowledge of what it can be done and what you may expect can only make us stronger.
A seemingly innocent image can deliver a message without even raising the eyebrows can be beneficial for those who want more privacy from what the encryption gives, but it can also be used with malicious intend by criminals that want to deliver their malware more stealthily than ever like the latest web-based skimming attacks where steganography is used to deliver payloads using the site logos, product images and favicons, but that’s a whole other view of steganography.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]









