Stuxnet – A weapon made out of code that almost started WW3

Reading Time: 7 Minutes
Introduction
It has been 11 years since Stuxnet first made headlines for its destructive capabilities to nuclear power plants and its stealthy nature, making it, the first of its kind.
June 2010, Stuxnet was found lurking in the data-banks of power plants’ traffic control systems and factories all over the world.
It was the most complex malware ever discovered at the time.
The reason for its discovery is attributed to a programming error introduced in an update where it accidentally spread beyond its target (Natanz nuclear plant). The worm spread to an engineer’s computer that had been previously connected to the centrifuges and then spread further when the engineer connected his computer to the internet.
Its development probably began back in 2005 and used an unprecedented four zero-day attacks. It was specifically targeting the centrifuges used to produce the enriched uranium that powers nuclear weapons and reactors while causing no harm to computer systems not involved in uranium enrichment.

Undated satellite image provided by Space Imaging/Inta SpaceTurk
shows the once-secret Natanz nuclear complex in Natanz, Iran, about 150 miles south of Tehran.
AP PHOTO/SPACE IMAGING/INTA SPACETURK, HO - source: wired.com
See Also: Offensive Security Tool: Nucleimonst3r
Complexity at its finest
Stuxnet is an extremely complex, and sophisticated computer worm that also exploits multiple previously unknown (at the time), zero-day vulnerabilities on Windows operating systems.
A typical computer malware or threat is occasionally around 10 KB in size, Stuxnet’s is 500 KB, making it 50 times larger than any typical malware. Its sheer size wasn’t due to graphics or images in the code, but due to its source code logic complexity.
It is written in several different programming languages like C and C++, which is unusual for malware.
Stuxnet stealthy attacks
Stuxnet operates in 3 phases, once on a Windows operating system, it will begin spread on its own continuously, until it discovers the proper types of computers to start the next step, which is to disrupt the nuclear centrifuges by infiltrating the Windows-based Siemens Step7 software.
If the system is not a target, Stuxnet will do nothing, if it is, it will attempt to access the Internet and update itself to a newer version.
Next, when the worm finds a suitable target, it will exploit multiple zero-day vulnerabilities in the Siemens Step7 software.
By infiltrating the Siemens Step7 software, the worm gains access to the industrial program logic controllers, giving the attackers access to crucial industrial information, and also the ability to control various machines at the industrial sites.
Its destructive phase comes next, by using the information gathered to control the centrifuges, making them spin until failure.
In the meantime, it provides false feedback to the outside controllers to go undetected from the operators of the centrifuges until it’s too late to do anything about it.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
The spread through 0-days
Compared to a normal worm that uses 1 distinct mechanism to spread, Stuxnet uses 7 different mechanisms.
Using the LNK Windows Shortcut flaw, which allowed code execution by only opening the folder that contained the malicious LNK file, Stuxnet, initially spread using infected USB flash drives, which contain the Windows shortcut files (.lnk) to initiate the executable code.
The worm then uses other exploits and techniques such as peer-to-peer remote procedure call RPC vulnerability (MS08-67) to infect other computers inside private networks that are not directly connected to the internet and through shared folders over the network.
Another way which the worm can replicate itself is by exploiting the vulnerability in the Windows Spooler (MS10-061). Machines with file and printer sharing turned on are vulnerable to the attack which results in privilege escalation, allowing a user with a Guest account to write into the %SYSTEM% directory of the target machine. A Guest account shouldn’t be able to have access rights to the %SYSTEM% directory.
The fourth zero-day came into use by Stuxnet when it didn’t have enough privileges to install itself in the system. It was able to exploit the previously unknown MS10-73, a zero-day vulnerability in the win32k.sys system module to escalate its privileges and perform any tasks it was meant to do on the local machines. The vulnerable systems are Microsoft Windows 2000 and XP.
Stuxnet attack dissected
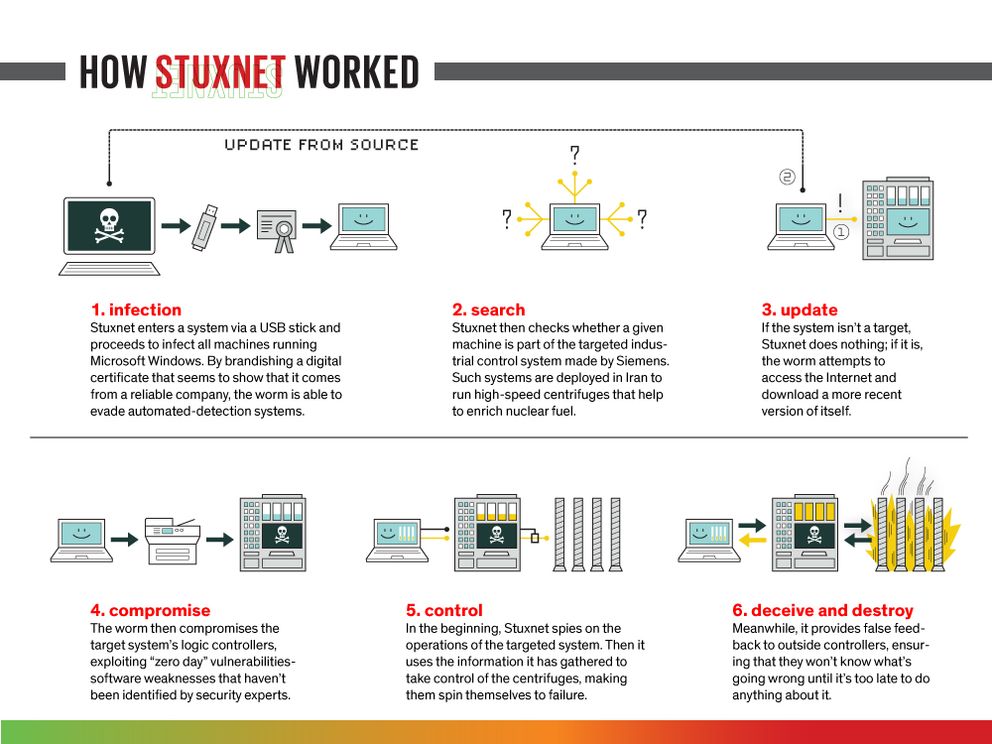
How Stuxnet attacks - source: spectrum.ieee.org
Stuxnet compromising Siemens Step7 software.
After the worm finds itself on a “proper” machine, it elevates its privileges and finds systems that use the industrial control software made by Siemens, Step7, then the compromise of the system begins.
The Siemens Step7 software is used to program industrial control systems, like PLC systems (programmable logic controllers). The software to control the centrifuges is built with the Step7 software, and then, the software is transferred to the PLC systems to run the centrifuges.
Stuxnet exploited the default password that was set by Siemens on Step7 that it was meant to be disabled after testing it. With that, it was able to access the database of the software and then infect the systems by dropping itself into the computer.
It was also able to infect the Siemens PLC data files which contain all the logic for controlling the centrifuges.
See Also: The Evolution of Malware
Targeting Uranium Centrifuges in Iran
After reverse-engineering its code, experts found that Stuxnet was looking for eight or ten arrays of 168 frequency converters each. The reason behind that was that Uranium enrichment facilities are arranged in eight arrays and have 168 centrifuges each. This can be confirmed by the International Atomic Energy Association (AEAI) documentation.
That was the fingerprint used by Stuxnet to reportedly attack the Natanz nuclear facility in Iran.
Stuxnet, behind the scenes.
Once on a Siemens Step7 computer, it downloads malicious logic to the PLC computers.
What made Stuxnet worm unprecedented at the time was that it could work both on a traditional PC and a Programmable Logic Controller. These are two separate computer systems, they speak different machine languages, different operating systems.
Stuxnet will not start destroying the nuclear plants by running the centrifuges to failure, but it will continue with a very meticulous approach.
Its next step it’s to measure the operating speed of the frequency converters for 13 days.
As the systems are sending back telemetry data for the centrifuges, Stuxnet is measuring those data to check how fast these centrifuges are spinning and makes sure that is running at between 800 Hz and 1200Hz, for reference, Frequency converters that are running over 1000Hz are considered bad and are only used in enrichment facilities.
After finding the signature (frequency of converters) that it looks for, the hardware (PLC system) that it needs to be on, and that the centrifuges are running for 13 days straight, Stuxnet begins its real attack.
Malicious PLC logic process
It raises the spin rate of the centrifuges to 1400Hz for 15 minutes only, and then sends it back to its normal spin rate. Then it sleeps for 27 days, and then again manipulates the spin rate and slows it down to 2Hz for 50 minutes.
Then again, sleeps for 27 days and repeats this process over and over again.
Staying undetected
Stuxnet’s malicious logic remained undetected from the monitoring systems of the nuclear plants because when it was manipulating the spin rate of the centrifuges, it was sending back the recorded data (from the data collected during the first 13 days) collected to the monitoring systems instead of showing the real/live data where it would normally alert the systems of the power plant.
Stuxnet’s logic went a step further to ensure that the power plant’s fail-system couldn’t prevent the destruction of the centrifuges. It could disable the emergency button where it can be manually hit and shut down the power plant’s centrifuges in case if something went wrong.
Stuxnet also inhibits different behaviors in the presence of different security vendors’ software. Stuxnet’s authors digitally signed it with stolen digital certificates (certificate of authenticity accomplished with cryptography, e.g. public-key encryption), making it look like it was created by well-known companies such as RealTek, and Jmicron from where the certificates were stolen initially.
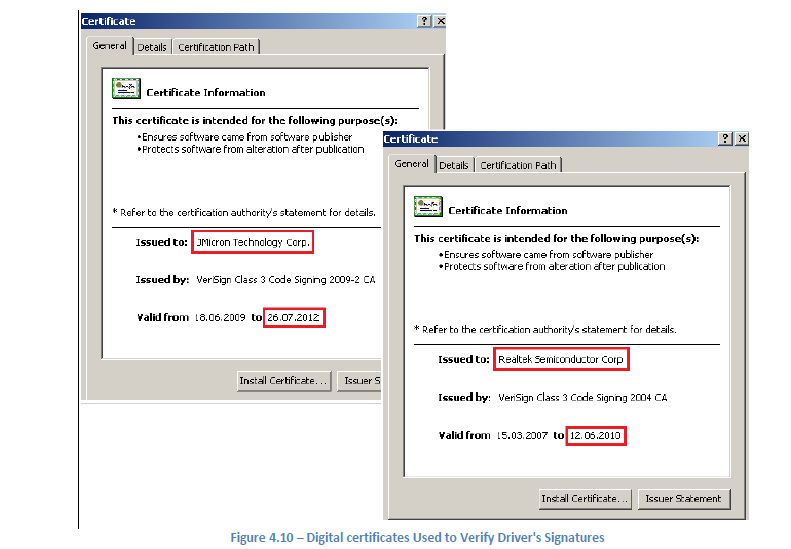
Digital Certificates used by Stuxnet to verify driver’s signatures – source: Eset
Who Created Stuxnet?
It is worldwide accepted that Stuxnet was designed as a cyber weapon to attack Iran’s nuclear development program.
Since the malicious logic that Stuxnet integrates on previously running logic of the PLC systems, whoever wrote Stuxnet understood exactly what the existing Iranian control logic was and integrated it with the malicious logic perfectly.
There is no evidence beyond rumors, to whom it may create it. Some say Israel was behind it because, upon inspection, the virus source code contained references to the Hebrew Bible, which in the end could be there just for confusion and deception.
Many experts agree though, that Stuxnet was a joint operation between Israel and the United States, but there is no concrete evidence beyond speculations.
UPDATED JANUARY 2024: In a recent development regarding the Stuxnet malware, Dutch newspaper De Volkskrant found out that AIVD, the Dutch intelligence, hired Erik van Sabben back in 2005, way before the Stuxnet incident. Sabben, a Dutch citizen residing in Dubai, was singled out. Reasons? His tech skills, connections in Iran, and an Iranian wife. The claim is that Sabben sneaked into the Natanz nuclear factory, and he managed to put the Stuxnet malware in a water pump using a USB flash drive. Whether or not Sabben was conscious about all this is still unclear, but one thing was unusual, as his family was showing signs of distress around Stuxnet attack time. One interesting point though, Michael Hayden, who once headed the CIA, didn’t provide any details on how Stuxnet was delivered, which questions the earlier stories about a USB flash drive. Further, De Volkskrant showed Hayden guessing the cost to develop Stuxnet to be between $1 to $2 billion. Some computer security experts, such as Costin Raiu and Mikko Hypponen, questioned this estimate.
Reported attacks and global infection
Asian countries are the leaders with the largest number of infected machines.
50% of Stuxnet’s distribution was found to be in Iran, Indonesia and India followed by 17% and 11% respectively. The high volume of detection in Iran’s region meant that it was the major target of the attackers. Over fifteen Iranian facilities were attacked and infiltrated by Stuxnet.
According to the Institute for Science and International Security (ISIS), Stuxnet, destroyed about 1000 Iranian centrifuges of about 19000 deployed to the nuclear sites, between late 2009 and early 2010.
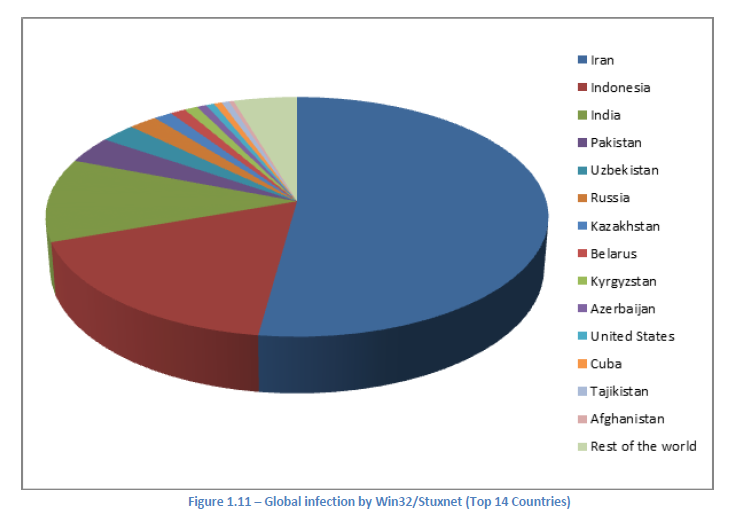
Global infection by Stuxnet chart – source: Eset
Last thoughts
After Iran discovered the virus infection, Iranian officials did an open call to the Iranian hackers to join the Iranian Revolutionary Guard, making it one of the largest army of hackers in the world.
After 9 months of its detection, Stuxnet’s source code was available online for anyone to download, understand its complexity, and experiment with it. A lot of people reverse-engineered Stuxnet and there are a bunch of videos on YouTube for it.
It’s an open-source weapon and there’s no way of knowing who will use it, or for what they will use it for.
These kinds of worries should keep everyone awake and responsible because the next world war can start first with a digital one.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]









