The Evolution of Malware

Reading Time: 12 Minutes
What is Malware ?
Malware or “malicious software” is a broad term to describe any sort of software developed with the intention to cause damage or gain access to a computer or network.
The malicious purpose behind this kind of “software” is often to access corporate & personal computers-devices stealing information available or/and by creating a backdoor so an attacker could steal computer resources, have persistent access, spy, delete-destroy data without any knowledge or permission by the victim.
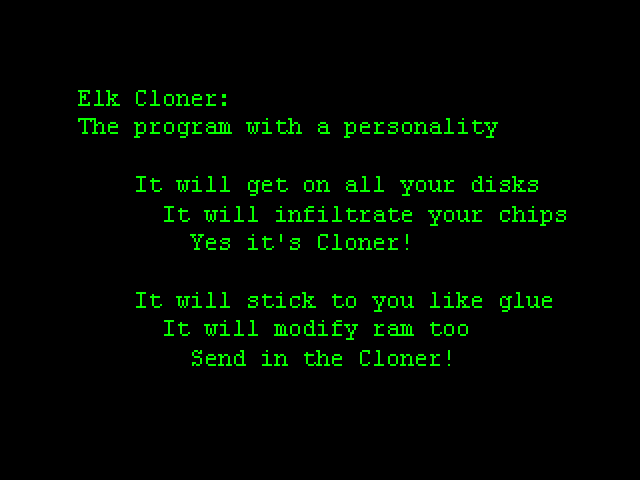
Elk-Cloner. The first ever computer virus.
The evolution through history
First Computer “Program” that could move itself:
The theoretical foundation of self-replicating Automata (“virus”), is a mechanism which can construct copies of itself, dating back in the late 1940s, the model was developed by John Neumann.
The first computer malware is debated. For some, the first computer malware considered to be Creeper, written by Bob Thomas in 1971.A program where without an active user input was able to move between computers using ARPANET.
The program was not designed to be “malicious”, the infected machines would simply display the message: “I’m the creeper: catch me if you can”.
Malware in 80s and 90s:
Most of the malicious programs existed in the late 1980s were simple boot sector and file infectors spread via floppy disk.
Certain types of malware proliferated as technologies standardized.
In the mid-1990s, macro viruses (that were exploiting Microsoft office products and spread via email), gained a distribution boost by the increased adoption of the email service.
Furthermore, the distribution of the malware accelerated by the increase of internet use, and also by the adoption of Web 2.0 technologies where they provided an excellent environment for the malware to grow.
In 1982, Richard Skrenta, fifteen years old then, created what is considered the first computer “virus”,
Elk Cloner
The virus was written for the Apple II operating system, which was stored in floppy discs.
By the time the computer was booted from the floppy discs infected with the “virus”, the virus would subsequently copy itself to an uninfected floppy disk that was accessed(the computers back then had dual floppy disk drives)
Then, every 50th time the machine was booted up, it would display :
Elk Cloner: The program with a personality
It will get on all your disks
It will infiltrate your chips
Yes it's Cloner!
It will stick to you like glue
It will modify ram too
Send in the Cloner!
Causing no damage, the Elk Cloner was created as a practical joke among friends.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Brain: Was the first full stealth virus on MS-DOS, infecting 360KB floppy disks.
When an infected disk is booted the brain virus will run with it, it does not infect hard disk but installs itself into the memory of the disk. It will infect any other floppy disk accessed while it is in memory.
Anytime infected sectors are accessed, the accessing program will be redirected to the stored original boot sector, making it the reason behind its stealth capabilities.
Jerusalem: Discovered in Israel In late 1987, it is an early DOS file infector virus.
Infecting any executable under DOS, on execution the virus becomes inhabitant and by staying in memory, infects all the programs that run after the first infected file is run.
The Morris Worm: Considered the first internet worm, the worm infects Sun microsystems Sun 3 systems, and VAX computers running variants of BSD Unix.
By exploiting vulnerabilities in the debug mode of the operating systems Sendmail program, if the worm determines that the new machine is capable of infection, it will send files to the new machine that downloads the main worm to it.
Michelangelo: Discovered in Feb. 1991, and designed to infect DOS systems (not engaging with the operating system), Michelangelo was a boot sector virus, operated at BIOS level.
Gained its name due to the reason that the virus remained asleep until March 6th, the birthday of Renaissance artist Michelangelo.
On March 6th the virus overwrites the first one hundred sectors of the hard disk with nulls, even though all the users’ data would still be on the hard disk, it would be irretrievable for the average user.
CIH: A dangerous Microsoft Windows virus, that infects Windows 95,98 and ME only machines.
Known as Chernobyl the name of it derived from a comment in the code.
It was first discovered in June 1998, in Taiwan.
Upon infection the virus becomes inhabitant and It is capable of infecting every executable file that is accessed.
Melissa: Is a very dangerous macro virus discovered in 1999.
Arriving in an email, with a body message “Here is that document you asked for … don’t show anyone else ;-)”, the attachment named list.doc contains a list of porn websites with the respective login credentials.
When opened, the virus performs a check if the Microsoft Office registry key has a subdirectory named “Melissa?” exists with ” .. by Kwyjibo” set as its value.
If the value has been set, the virus remains inactive. If the value is not set, the virus then mails itself to fifty email addresses from the user’s address book.

The Morris Worm source code. Computer History Museum.
Malware in 2000s
Early 2000s
At the start of the new millennium, an increase in the use of exploit kits led to an explosion of malware delivered online.
In 2007, automated SQL injection and other forms of mass website attacks, increased in distribution in 2007, resulting in an exponential growth in the number of malware attacks.
ILOVEYOU: A computer Worm for Windows, that infected millions of personal computers on and after May 5th,2000.
The virus arrives in an email with a subject line “ILOVEYOU” and an attachment “LOVE-LETTER-FOR-YOU.TXT.vbs” thus taking its name from the subject line.
Anna Kournikova: A computer worm, designed in 2001 with the purpose to trick email users into opening a mail message purportedly containing a picture of the tennis player Anna Kournikova, while hiding a malicious program.
Upon opening the attachment, the worm launches a Visual Basic Script that forwards itself to any user of the victims’ address book in Microsoft Outlook.
Code Red: A computer worm that caused damages over a billion US dollars in the summer of 2001.
The worm arrives at a server as a GET /default.ida request on TCP port, exploiting a known buffer overflow vulnerability in the indexing software in Microsoft’s Internet Info. Server (IIS), allowing it to run code from within the server. Running entirely in memory the worm cannot be found on the disk.
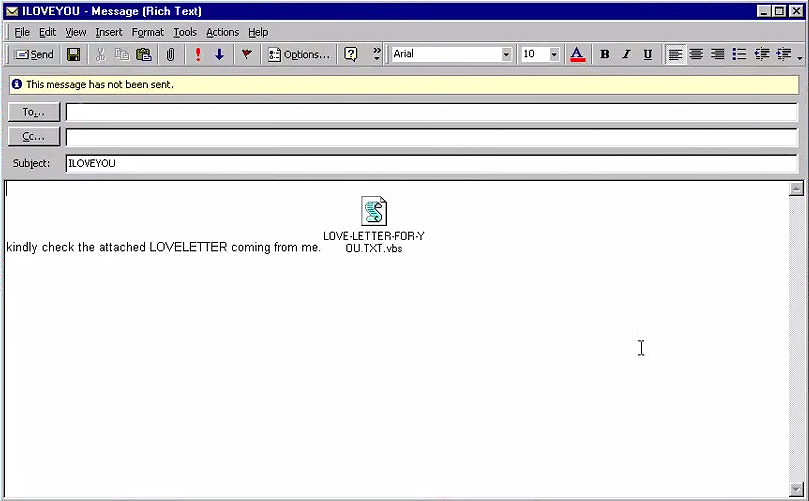
ILOVEYOU worm.
2002-2005:
About this time internet users were being attacked by the socially engineered worms and spam proxies that began to appear.
Newly registered, cloned domains of eBay and PayPal appear in the late 2003s, where phishing took off and worms like Slammer (was the fastest spreading worm of its time), Mybloom 2004, were released and caused around 40 billion combined in damages.
This lead to an increase in awareness of the danger in email attacks and many adopted improved email filtering and scanning which resulted in the mitigation of the fast-spreading worms delivered via email.
2006-2010
2006
Mpack: a PHP based malware kit escalated, which using evasion techniques infected thousands of pcs exploiting their system.
The Russian owners were charging 1000$ for its source code and additional fees for updates and new features.
In 2007 and 2008, SQL injection attacks begun to rise.
Attackers using the iFrame tag were able to inject malware contain website(links) using Cross-site Scripting in popular websites.
Automated SQL injections attacks were facilitated by Asprox botnet in 2008, infecting as many as 15000 websites, Sony Ps. Us and Adobe Serious Magic websites were compromised by the botnet.
In 2009 and 2010,
Gumblar, a Javascript trojan that started targeting older Windows versions, its infection manifests first on compromising sites by acting as actual malware host, and in another way by injecting iFrames that point to the malware host.
In 2010 Stuxnet, a malicious worm that its development started in 2005, and started targeting Iran’s nuclear facilities.
Then it spread to other industrial entities, such as power plants, and gas lines.
It was specifically targeting the supervisory control and data acquisition (SCADA) systems and it is thought to be the cause of the destruction of several of Iran’s uranium nuclear programs.
2011 – 2015
2011
A record-breaking year for malware in general, 2011, saw an 81% increase in cyber-attacks, and around 5.5 billion malicious attacks last year alone.
Duqu
Similar to Stuxnet, Duqu is a worm running on Windows.
Arrives in a crafted Microsoft Word document where it contains undisclosed Zero-day kernel exploit that allows the attackers to install Duqu onto the computer of the unsuspected user.
ZeroAccess is a Trojan horse computer malware that affects Microsoft Windows operating systems. Infected systems with the ZeroAccess rootkit will eventually start one of the two main botnet operations: bitcoin mining or Click fraud.
2012
The year that people understood that no OS is completely safe, with the Flashback virus infecting Mac OS across the globe.
It was appeared late 2011s but got popular In the first months of 2012, due to the reason that over 600 thousand Mac’s were infected.
Demolishing the myth around the invulnerability around Mac OS, the Flashback virus is a trojan that exploits a vulnerability(CVE-2012-0507) in the Java Runtime Environment (JRE) component in Oracle Java SE 7 Update 2 and earlier.
Flame was a computer malware for Microsoft Windows.
Discovered in 2012, It was a highly complex malware that existed undetected for many years(5 years).
Performing a wide array of functions and having 20MB of modules, Flame was able to intercept audio, take screenshots, record keyboard activity and more.
Flame malware.
2013
Ransomware: being a type of malware (ransom and malware) that locks down computer systems and files in order to pay money in Bitcoin in order to unlock the system with the “key” provided by the attacker.
Ransomware can be spread with the help of exploit kits that can be purchased online.
This year ransomware attacks posed as government agencies, police, FBI accusing victims of committing a crime.
Reveton: Appeared in many countries, the malware did go with many names depending on the user’s location, examples: FBI MoneyPak (United States), Metropolitan Police (United Kingdom), Celas (Russia), and Canada Police Association (Canada).
After infecting the machine, it will prevent the user from accessing the Desktop, displaying a message that the system was locked by a local law enforcement authority.
Cryptolocker
A ransomware Trojan on Microsoft Windows OS where it is considered to be the first ransomware malware.
The malware was spread mainly via emails pretending to be customer support related to FedEx, UPS, DHS, etc.
Since Microsoft does not show extensions by default, Cryptolocker looking like a normal PDF file, (it was disguised as PDF, with a PDF icon and typically name like FORM_101513.pdf.exe) was executed by its victims with no suspicion at all.
Cryptolocker was able to double encrypt the user’s personal files with both a local AES key as well as remotely created and remotely stored RSA-2048 key.
2014
While it began in June 2013 the revelations of Edward Snowden and the leaked NSA documents arrived in the first half of 2014.
UK and US governments accused of espionage and mass surveillance programs like AURORAGOLD, MUSCULAR, etc.
Shellshock: is a family of security bugs in the Unix Bash Shell.
Known as Bashdoor, it caused Bash to unintentionally execute commands when the commands are concatenated to the end of function definitions stored in the values of environment variables.
Multiple vulnerabilities were discovered after its publication, within hours attackers exploited Shellshock by creating botnets of compromised machines to perform DDoS attacks and vulnerability scanning.
Heartbleed:
SSL/TLS vulnerability n the popular OpenSSL cryptographic software library.
The weakness allows stealing the info. protected under normal conditions by the SSL/TLS encryption used to secure the Internet.
Allowing anyone to read the memory of the systems protected by the OpenSSL software, the attacker can steal the secret keys used to identify the service providers and to encrypt traffic, usernames, and passwords.
Attackers were able to steal data directly from the services and users, and then impersonate services and users.
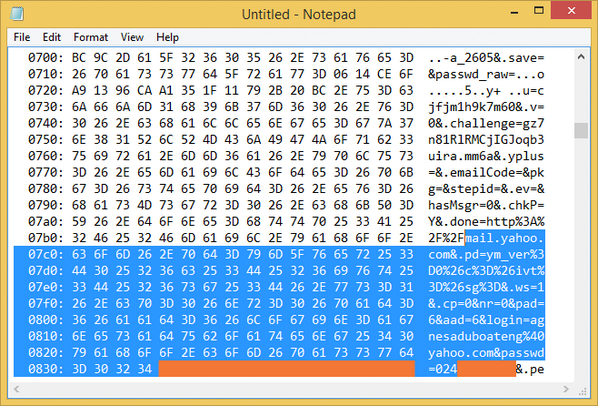
Alleged Yahoo user credentials visible due to Heartbleed (source: Mark Loman).
2015
The threat landscape in 2015 had similarities with 2014, but with some differences.
A surprise was the reappearance of the macro malware, malware that was active in the 2000s.
Worms had a greater percentage than previous years as of overall malware detections, which is attributed to the new families appeared in certain parts of the globe.
Njw0rm is the most well-known of those families, a VBS(visual basic script) worm that spreads through removable drives, malicious email attachments, and drive-by downloads.
Njw0rm was mainly detected more often in the last six months of the year 2015.
The worm designed to steal information from its victims while also having backdoor capabilities.
The malware aims to steal user information, execute commands, while also having backdoor capabilities.
Exploits were a notable threat in 2015 and were observed to be active in many different countries, including the UK, US Sweden, and Australia.
The Angler exploit kit was particularly noticeable in the detection reports in the year 2015.
The Angler exploit kit demonstrated the most comprehensive arsenal of exploits last year, but part of its success appeared to be the increasingly efficient use of different attack vectors.
This kit had an arsenal of the most diversified exploits and its success comes In the efficient use of different attack vectors.
Trojans like Trojan:JS/Redirector are insinuated onto legitimate websites by attackers to redirect website visitors to sites hosting exploit kits, including Angler and Nuclear.
2016-2019
2016
Locky
Originated from Russia, with source language C++, the ransomware email worm and macro trojan virus was designed for Microsoft Windows.
The ransomware upon installation would check if the machine of the user had the Russian language as default and if it did, it will not continue with the encryption.
Reports say that the ransomware was infecting around 100 thousand machines per day, with most of them happening in Germany and the Netherlands. (around 5 million computers)
The attacks were happening either via malicious doc. attachments spread via email or when a user actually visited a hacked site that had an exploit kit containing the ransomware.
Mirai
With estimated infections to be around 9 million machines, Mirai is a malware that uses computers running Linux operating systems as bots, controlling them remotely to create a botnet to use in large scale attacks such as DDoS attacks.
Infected machines with Mirai malware will continuously scan the internet for IoT devices.
Then identifies the vulnerable IoT devices and using a table of common factory credentials, attempts to log into them and infect them as well.
Mirai can launch both HTTP flood and network-level attacks.
Mirai storing itself in memory can get purged upon rebooting the device, but as long as the password of the machine remains the same, it will get infected again.
Mirai. photo credit: Obsydistone / Wikia
2017
Ransomware attacks were increased by 90 % and 93% in business customers and in consumers respectively over the year 2016.
Attackers also focused on deploying banking Trojans, Spywares and browser hijackers.
These types of malware are used to steal data, credentials, contact lists as well as credit card data.
WannaCry
With reported costs around 4 billion and 250 thousand infected computers around the world, there is a little chance not knowing this malware worm.
Infection occurs in various ways, including Trojan-style and Worm-style attack vectors.
It uses the NSA exploit EternalBlue exploit kit leaked by The Shadow Brokers.
After the infection, the EternalBlue exploit is used along with other leaked NSA exploits, to travel across through the network connected to the victim system encrypting files and then demanding ransom in Bitcoin.
Microsoft released patches for the vulnerable Windows versions(Win 8, Win Server 03, Win XP) which all were no longer supported at the time.
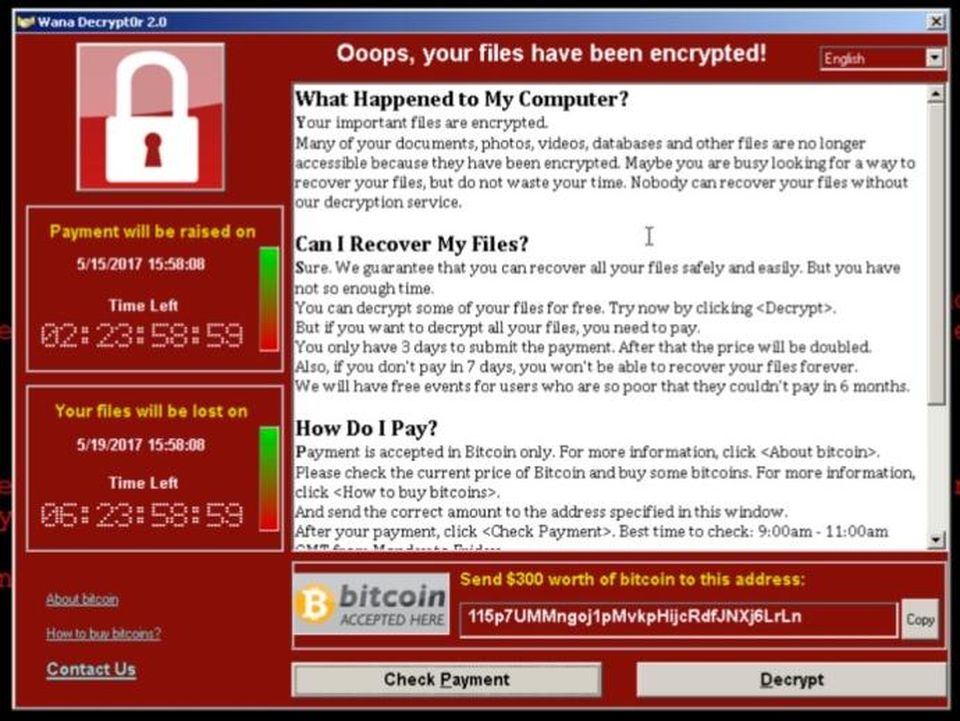
The WannaCrypt ransom screen/Image: Microsoft
Petya
A ransomware family that affects Windows OS.
Among the variants, Red, Green, and Yellow Petya considered as the original ones.
The target of this ransomware is HR staff in German-Speaking languages.
Petya is distributed mainly via spam emails containing a Dropbox download link that is a Zip archive,with a trojan exe. file appearing with a PDF icon.
Initially, It was targeting HR staff in German-Speaking languages
The famous NotPetya is a wiper and actually considered to be a destructive malware because there is no way to retrieve the ransomware’s ID key( was essentially ineffective at collecting its ransom), thus the users’ data are not retrievable in any way unless a backup of that data exists.
NotPetya exploits EternalBlue and EternalRomance, two (SMB)-Server Message Block vulnerabilities and also destroys the computers (MFTs)-Master File Table and (MBRs)Master Boot Record.
2018
In the first of half 2018, Ransomware attacks decreased, making way to a huge wave of crypto miners due to the spike of Bitcoin value at the end of 2017.
2018 was the year of mega-breach, hundreds of millions of customers affected because major business were penetrated like Exactis, Facebook, Starwood, Quora, and several others.
Crypto miners
A variety of crypto miners detected in the first half, even loading several on the same user via exploit kits.
Unlike other treats like ransomware and malware, crypto miners want to remain silent while using the victim’s resources to benefit from the mining of mainly bitcoin and several other crypto coins.
Often the first sign of something going wrong on the machine is the high CPU usage while becoming slower and cooling fans working non-stop.
Information stealers
Two of the biggest Trojan type threats of this year were Trickbot & Emotet, information-stealing malware.
Emotet is a Trojan that affects the Microsoft Windows operating systems.
First identified in 2014, Emotet continues to infect systems and hurt users to this day.
The business and consumer side were plagued by this information-stealing spammer in 2018.
The primary distribution method for Emotet is through the mail.
Emotet rob your contacts list and sends itself to your contacts. Since these emails are coming from a familiar hijacked account, it looks less like spam, resulting in the victims to download the infected files or visit the bad URLs.
Version one of Emotet was designed to steal bank accounts and intercept internet traffic.
The new version came packed with more modules, including a money transfer system, malspam module, etc.
Trickbot
Trickbot is a Trojan trojan-type malware designed to steal users’ private data often spread by Emotet, using the EternalBlue exploit to spread itself across a given network.
Distributes also by using spam emails and fake Adobe Flash player updates.
Trickbot is considered an information stealer and can download other malicious features that include keyloggers and lateral network movement.
It was first discovered in late 2016 targeting various financial institutions, banks, and credit card providers and didn’t start making waves until the end of 2017 where it was pushed by Emotet.
Some of its other capabilities include harvesting credentials and emails using Mimkatz, and can also steal from Bitcoin wallets while targeting international banks via its webinjects.
Affected up to 3 million business and consumers endpoints as of 2018.
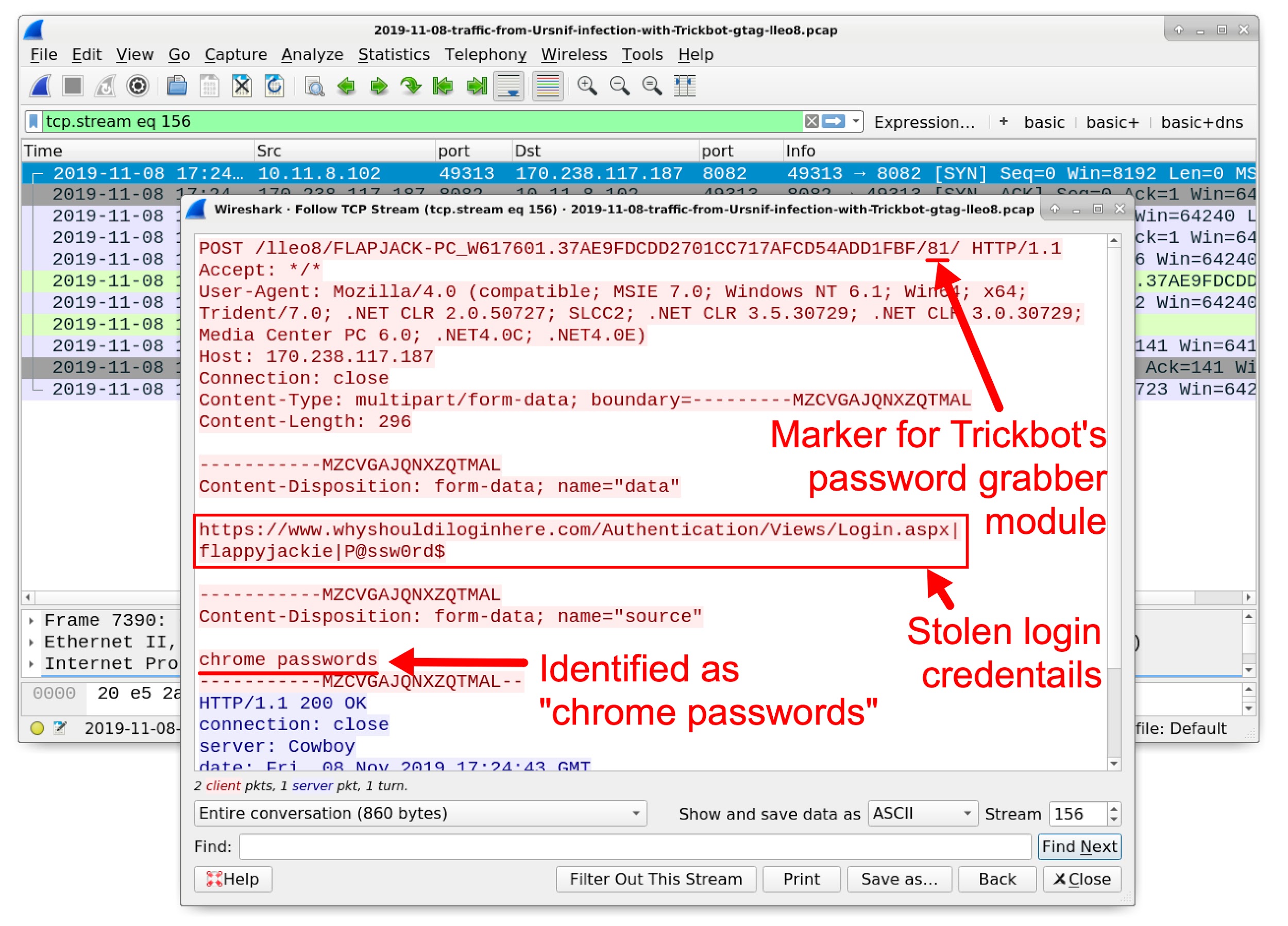
Login credentials stolen from an infected user’s Chrome browser cache. credit:paloaltonetworks
2019
Ransomware detections have slightly declined from 2018.
Organizations were once again hammered with Emotet and TrickBot, two Trojan families that started out as simple bank trojans & info-stealers then evolved into downloaders and botnets.
Emotet and Trickbot both saw an increase in detections placing into the top 5 threads in 2019 (Emotet was second).
Criminals in 2019, return their attention away from consumers and focused on bigger targets such as schools, universities, and hospitals attacking them with ransomware families like Ryuk and Maze.
Next are some notable malware and spyware programs affecting Android and IOS devices that throve in 2019.
XHelper
A detection name was given from Malwarebytes for a Trojan.Dropper targeting Android devices that uses persistent re-infection tactics. It can be re-installed even after a factory reset.
Spreading most likely from web-redirects that sent users to websites hosting apps for Android devices, the trojan infected around 45 thousand devices by the end of October 2019.
The fact that this malware was able to re-infect after a factory reset marks a new era in mobile malware.
It has the ability to re-infect using a hidden directory containing an APK that can evade detection.
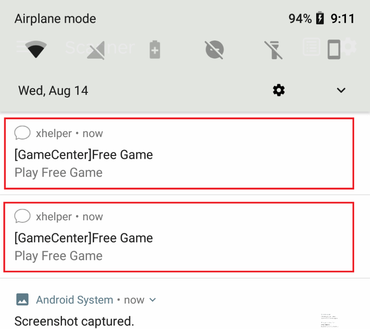
Xhelper. Image: Malwarebytes
HiddenWasp
A new malware targeting Linux systems, using a code from Mirai and Winnti.
Researchers believe that the malware is being used as a second stage targeted attack that is designed to remotely control already compromised systems.
Its rootkit capabilities enable the malware to avoid detection.
Attackers can perform various operations when it is successfully deployed to an already compromised system including:
Retrieving system and file information while listing files stored in the system.
Can copy, upload, download move and delete files into the system.
And can also execute files or scripts and run commands.
It demonstrates the constant evolution of Linux threats showing that many of today’s Linux malware is combining or embedding other payloads.
Pegasus
A spyware that is capable of hacking iOS and android devices(Chrysaor for android, is quite similar to Pegasus in term of capabilities but different in terms of the techniques needed to exploit the device), harvesting data about the victim such as messages, emails, passwords, browser history, address lists.
It installs the required modules to perform eavesdropping on phone calls, making and sending audio recordings, while tracking the location of the compromised device.
Pegasus depended on three zero-day (previously unknown) vulnerabilities in iOS devices that allowed to jailbreak the device and then installing the spyware.
Pegasus can delete itself if it does receive a response from the command server (that is controlled by the attacker) for more than 60 days or if it detects the wrong OS of the infected device.
The android version named Chryasor does not rely on the three 0day vulnerabilities but uses a rooting method called Framaroot.
The main difference with Pegasus is that even if Chryasor malware fails to obtain the necessary root access to install the spyware, it will still directly ask the victim for permissions to exfiltrate at least some data, while in Pegasus attacks if the malware fails to jailbreak the device the whole attack fails.
See Also: Reverse Engineering-Hacking Tools
Today
The malware of today has nothing to do with the malware at the beginning of the internet, in the 80s Elk Cloner was created as a joke among friends, infecting floppy disks for fun, and now we have thousands of different malware strains that have the intention to steal information, do damage, steal banking accounts, encrypt data and many more.
Since the start of the worldwide web in 1990, internet users increased exponentially from 16 million in 1995 to reach 2 billion in 2010 and 5.2 billion users in 2023.
This alone lets attackers create more and more malware because of the simple reason that almost everyone has access to a device connected to the internet.
At the end of 90s “Melissa” was a mass-mailing macro virus with no intention to harm and by the end of the decade,
Stuxtnet, a malicious worm was targeting power plants, this alone shows how the malware changed in 10 years.
At the start of 2010s, internet users were starting to embraced social media, smart devices, IoT, and all the good that the evolution of technology has given to us. Remote work and data breaches were unheard of and cybercrime was beginning to unfold in front of our eyes.
Security, data privacy and policies are just starting to adopt, because people and organizations realized how dangerous could be to be unaware and unsecure in today’s world.
Every new malware or a new data breach is a reminder of how seriously we should take the cybersecurity practices.
References:
- https://searchsecurity.techtarget.com/definition/Elk-Cloner
- https://www.trendmicro.com/vinfo/us/security/news/cyber-attacks/hiddenwasp-malware-targets-linux-systems-borrows-code-from-mirai-winnti/
- https://malware.wikia.org/wiki/XHelper
- https://blog.malwarebytes.com/android/2020/02/new-variant-of-android-trojan-xhelper-reinfects-with-help-from-google-play/
- https://resources.malwarebytes.com/files/2020/02/2020_State-of-Malware-Report.pdf
- https://malware.wikia.org/wiki/XHelper
- https://malware.wikia.org/wiki/Pegasus
- https://fossbytes.com/top-malware-2019/
- https://www.lastline.com/blog/lateral-movement-what-it-is-and-how-to-block-it/
- https://www.theguardian.com/technology/2009/oct/23/internet-history
- https://www.pcworld.com/article/244383/report_2011_is_the_year_of_mobile_malware.html
- https://venturebeat.com/2012/04/30/over-403m-malware-strings-found-in-2011-says-symantec/
- https://securelist.com/kaspersky-security-bulletin-2012-malware-evolution/36732/
- https://www.f-secure.com/documents/996508/1030743/Threat_Report_2015.pdf
- https://www.malwarebytes.com/pdf/white-papers/CTNT-Q4-17.pdf
- https://malware.wikia.org/wiki/Petya
- https://www.malwarebytes.com/malware/
- https://www.zdnet.com/article/what-is-malware-everything-you-need-to-know-about-viruses-trojans-and-malicious-software/
We hope that this write up has taught you something new. If you enjoyed it, the best way that you can support us is to share it! If you’d like to hear more about us, you can find us on LinkedIn, Twitter, YouTube.
Are you a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]









