The first botnet hijacker aka the Zombie King

Reading Time: 5 Minutes
Hacking Alias: ir Resilient
Jeanson Ancheta didn’t have the typical path many hackers did, but he carved his own way by building a botnet army. This is the story of the first person to plead guilty to federal charges for hijacking computers for profit.
Early Life
Jeanson James Ancheta was born in Downey, California, in 1985. In 2001, he decided to drop out of Downey High School in California and later entered an alternative program for students with academic or behavioral issues, eventually earning a high school equivalency certificate. Ancheta worked at an internet café at the time but originally wanted to join the military, according to his family. However, his life took a different direction when he discovered the world of botnets.

Jeanson James Ancheta mugshot – source: theregister.com
Discovering Botnets
In June 2004, while browsing the internet, Ancheta discovered the rxbot computer worm. This malware was designed to spread widely across the Internet and could be customized easily. Intrigued, Ancheta began secretly hijacking tens of thousands of computers across the United States, including two military servers. He set up a channel on IRC called “botz4sale” to rent out his botnet for profit. He even created a manual detailing how many “zombie” machines would be needed to crash websites and set rental rates, with a minimum of 10,000 infected machines at four cents each. By the end of July, he controlled at least 100,000 bots. Between June and September 2004, he rented his botnet to 10 clients, earning around $3,000 through PayPal.
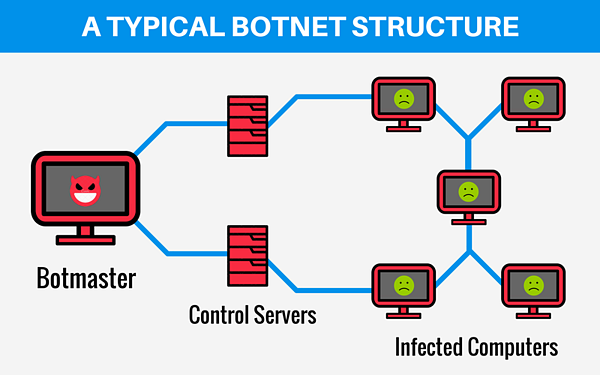
Botnet diagram – source: anura.io
SoBe: A Partner in crime
Ancheta met a 16-year-old hacker from Boca Raton, Florida, who went by the nickname “SoBe.” SoBe had quit school and spent most of his days coding in C++ and chatting with hackers in IRC rooms. They connected in August 2004 in an IRC channel called “bottalk.” SoBe, who was impressed by Ancheta’s proof of botnet control, noticed that Ancheta was one of the few in the chat with substantial proof of his claims. Screenshots showed that Ancheta controlled tens of thousands of computers. Their partnership extended beyond business, they would often leave their digital signatures via “graffiti” on vulnerable servers before leaving.

Graffiti of SoBe and Ancheta on a compromised website – source: theregister.com
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Building the Bot business
Their botnet army grew to over 400,000 computers as they launched a new scheme. Ancheta and SoBe signed up with multiple online advertising agencies, including Gamma Entertainment of Montreal and Loudcash, to install adware on their botnet army and generate pay-per-click affiliate fees.
This new business model was highly profitable, netting them over $60,000 in about 13 months, despite an initial FBI raid on Ancheta’s home in December 2004. “It’s immoral, but the money makes it right,” Ancheta told SoBe during one online chat.
The First FBI Raid
The FBI discovered Ancheta’s activities by monitoring the chat room where he advertised his botnet. Posing as potential clients, FBI agents purchased bots and began tracking him. In December 2004, they raided Ancheta’s home, confiscating his computer.
Back to Business
Despite the raid, Ancheta was back online within a day, continuing his botnet activities with SoBe. The FBI continued to monitor them closely, as Ancheta still advertised on the “bot4sale” channel, keeping himself high on their radar.
Mistake and Backdoors
Their chosen software, rxbot, was filled with bugs, which caused their zombie machines to aggressively spread to nearby networks, sometimes beyond their intended targets. As a result, their botnet compromised computers belonging to sensitive institutions, including Sandia National Labs, China Lake Naval Air Facility, and the Defense Information Security Agency. Because this evidence came from military computers, it gave the FBI a crucial break in their case, allowing them to dig deeper into the pair’s activities.
Both hackers failed to realize the consequences of these breaches and ignored warnings they had received back in August 2004 to filter out government domains like “.gov” and “.mil” from their botnet’s targets. Additionally, SoBe made a rookie mistake by leasing a server using his real identity. They used these servers to host an IRC daemon (IRCd), which the bots reported to, allowing them to control the botnet remotely. By changing the topic in their IRC channels, they could command their bots to connect to other servers under their control and install any software they hosted there.
SoBe later admitted that he was convinced the IRC daemon had a built-in backdoor, having obtained the program from hacker Jonathan Hall, who had been charged in a separate botnet investigation. Hall confirmed that he’d spotted a backdoor in the daemon’s source code, allowing anyone with knowledge of this feature to gain access by typing commands like “/system foo foo” or “/system bar bar.” Although the FBI never confirmed this, it’s likely that these careless oversights played a part in Ancheta and SoBe’s eventual downfall.
See Also: The Evolution of Malware
The Final raid and arrest
IIn May 2005, the FBI raided both hackers’ homes. FBI agents stormed the SoBe family’s three-story house in Boca Raton, Florida, while SoBe was recovering from a recent motorcycle accident. They seized thousands of dollars worth of computers, video games, and other electronics as his parents watched, unaware of their son’s activities.
Simultaneously, agents raided Ancheta’s home in the Los Angeles suburb of Downey, California, for the second time in six months. After disabling the servers that SoBe and Ancheta were using, the FBI gathered enough evidence to arrest Ancheta in November 2005. SoBe, being a minor at the time the crimes were committed, was not arrested, but he remained on probation until the case was fully resolved.

FBI report for SoBe’s home raid – source: theregister.com
Sentencing
In November 2005, Ancheta faced 17 counts of conspiracy, fraud, and related crimes connected to a 14-month hacking spree that began in June 2004 and continued even after the FBI’s initial raid on his house in December 2004. Ancheta’s attorneys negotiated a guilty plea after the FBI’s report estimated that his botnet’s use of worms and trojans caused $12 billion in damages to U.S. organizations. The indictment provided an unusually detailed look into the world of hackers who boasted in online chat groups about commandeering large botnets for spam and DDoS attacks.
On May 9, 2006, Ancheta pleaded guilty to four felony charges, including violations of United States Code Section 1030, Fraud and Related Activity in Connection with Computers. He was sentenced to 57 months in prison, forced to forfeit his BMW, over $60,000 in profits, and ordered to pay $15,000 in restitution to the U.S. federal government for infecting military computers.
Aftermath
Ancheta’s arrest shocked online hacker communities. SoBe was also surprised by the severity of Ancheta’s sentence, feeling it was excessive. “It’s not going to stop anyone from doing bots,” he commented. “There are hackers out there making more than Ancheta in one month, but they’ve never been caught.” Over the following year and a half, SoBe worried about the possibility of being indicted, while Ancheta served his sentence in federal facilities, first in California and later at the federal correctional institution in Allenwood, Pennsylvania.
SoBe did not contact Ancheta while he was in prison and continued living with his parents. After an extended investigation, the FBI connected more hackers to the botnet crimes, including SoBe. In February 2008, he pleaded guilty to delinquency charges related to installing adware on hundreds of thousands of computers. His real name remains unknown due to his age at the time of the crimes.
Final Thoughts
The story of Ancheta and SoBe stands out, as both were very young when they committed these crimes, and Ancheta was the first person indicted for profiting from botnets. Lessons from this story include, of course, not becoming a botnet “zombie king,” but also the importance of securing devices against unauthorized access.
Keep your machine updated, install security patches for your OS, and avoid clicking on unfamiliar attachments or links in messages. You can also monitor your network for suspicious activity using analytics solutions. Although these steps don’t guarantee complete protection, they’re essential defenses against potential botnet attacks.
We hope that this write up has taught you something new. If you enjoyed it, the best way that you can support us is to share it! If you’d like to hear more about us, you can find us on LinkedIn, Twitter, YouTube.
Are you a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]









