Unlocking Windows System Resource Utilization for Digital Forensics Analysis with SRUM Dump

Introduction
In numerous incident response scenarios, it is often necessary to collect evidence of program executions.
System Resource Utilization Management (SRUM) is a database introduced in Windows 8 and later versions of the Windows operating system that stores information about the usage of system resources, such as CPU, memory, and network utilization and it enables the examination of them by the applications running on the system. The SRUM database can be parsed (it is an ESE database) and searched for things like data exfiltration, command and control traffic, malware, and poorly behaving applications. This information can be useful in digital forensics investigations to determine the activity on a computer, identify potential security threats, and reconstruct the events leading up to an incident.
Mark Baggett’s srum-dump is a forensics tool that extracts the data stored in the SRUM database and converts it into a spreadsheet with detailed information on all processes that have run in the last 30 days on Windows computers, specifically in the .xlsx format. This tool allows investigators to analyze the resource utilization information of a Windows machine and can provide valuable insights into the activity of the computer.
The value of SRUM Dump in Digital Forensics
The information stored in the SRUM database can be used to answer important questions in digital forensics investigations, such as:
- Which applications have been running on the system and how many system resources were utilized by each application?
- When was a specific application launched and for how long was it running?
- What was the network utilization of the system and which applications were using the network?
By analyzing the SRUM database, investigators can gain a deeper understanding of the activity on the computer and can use this information to piece together the events leading up to an incident. This information can also be used to identify potential security threats, such as malware or unauthorized access to the system.
Some examples of how it can be used:
Timeline reconstruction: By analyzing the SRUM-DUMP data, investigators can reconstruct a timeline of events leading up to and during an incident. This can help them understand the sequence of events, identify the root cause of the incident, and determine the scope and impact of the attack.
Detection of anomalies: The SRUM-DUMP data can be used to detect anomalies or suspicious patterns of activity that may indicate a security breach. For example, if an unknown process is found to be consuming a significant amount of system resources, it may be a sign of a malware infection.
Performance analysis: The SRUM-DUMP data can be used to analyze system performance and identify potential performance issues that may have contributed to the incident. For example, if a system slowdown occurred during the attack, the SRUM-DUMP data can be used to identify the cause of the slowdown.
Identification of IOCs: The SRUM-DUMP data can be used to identify potential indicators of compromise (IOCs) that may be related to the incident. For example, if a particular process or application is found to be communicating with a known malicious IP address, it may be a sign of a security breach.
See Also: So you want to be a hacker?
Offensive Security Courses
SRUM Dump: Beyond Digital Forensics – Utilizing SRUM for Information Security and Red Team Operations
The use of SRUM Dump is not limited to digital forensics investigations, as the information stored in the SRUM database can also be leveraged by Information Security professionals. For example, Red Teams can use this information to identify weaknesses in a system and determine the most effective methods of attack.
By understanding the resource utilization of the system, red teams can determine which applications are most critical to the system and which are most vulnerable to attack.
How to use SRUM Dump
Using SRUM Dump is a straightforward process that can be done in a few steps:
- Download and install the tool from the official website (https://github.com/markbaggett/srum- dump).
- Open the command prompt and navigate to the directory where the tool is
- Use the following command to extract the SRUM data:
srum-dump.py -i srum.dat -o output.xlsx
The -i option is used to specify the input file, which is the SRUM database file, and the -o option is used to specify the output file, which will be the .xlsx spreadsheet. Once the command is executed, the tool will extract the data from the SRUM database and generate a spreadsheet with the information.
To use the tool you will need a copy of the SRUM (located in c:\\\\\\\\windows\\\\\\\\system32\\\\\\\\sru\\\\\\\\srudb.dat but locked by the OS). This tool also requires an SRUM_TEMPLATE that defines table and field names. You can optionally provide the SOFTWARE registry hive and the tool will tell you which wireless networks were in use by applications. If you are looking for a version of this tool that creates CSV files instead of an Excel spreadsheet, dumps targeted tables, or processes any ese then check out ese2csv ese2csv.exe is designed specifically for csv files with the CLI user in mind.
See Also: Offensive Security Tool: Pypykatz
Program Features
You may provide all of the options from the command line. If the name of a srum file is not passed then the GUI will launch. There are some features like live acquisition that are only available in the GUI when running as an administrator.
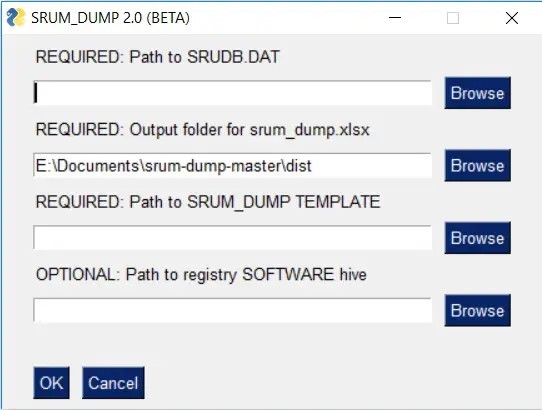
Enhancements of the latest version of GUI srum-dump
In addition, the GUI srum-dump’s latest version has the following enhancements over the original version:
- Dump all field tables including those that are not defined in the template XLSX.
- LIVE System Acquisition when running as an administrator
- Speed Improved
The live acquisition warning dialog box will appear if you select the file c:\\\\\\\\Windows\\\\\\\\system32\\\\\\\\sru\\\\\\\\srudb.dat. This file is locked by the OS and can not be directly accessed. From here you can easily download a copy of FGET to acquire an unlocked copy of the file. If, and only if, you are an administrator a button will appear that says “AUTO EXTRACT”.
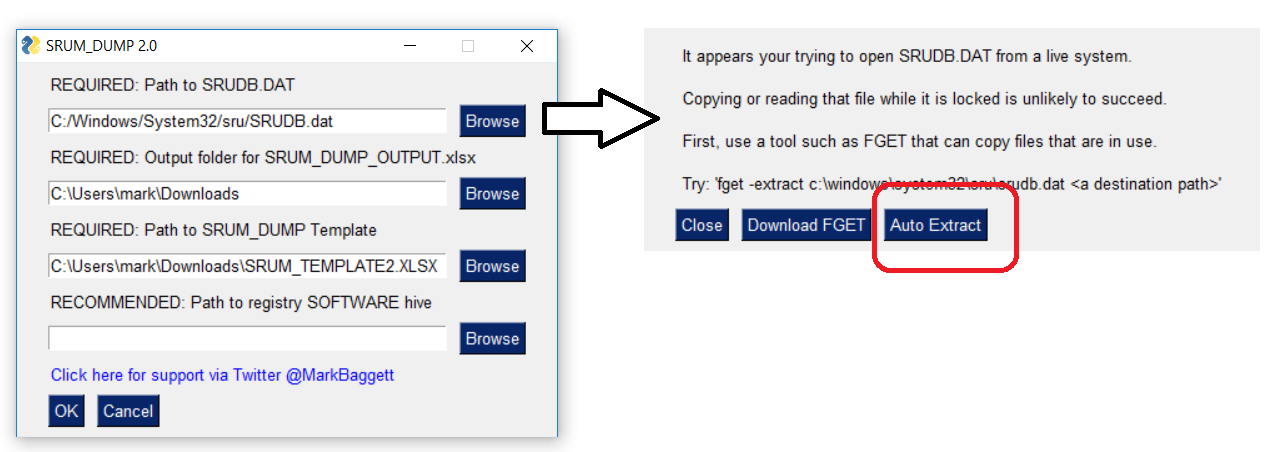
If you click this button then it will download FGET from Mark’s Git Hub and acquire a copy of both the SRUDB.DAT file and the associated SOFTWARE registry hive. Then it will set the paths in the GUI so that points to the acquired copies in a temporary directory.
To understand its power try to dump your srum with BLANK_TEMPLATE.XLSX and compare the results. The formatted row in the template tells the srum to process fields and resolve their values. Some formats such as “lookup_SID” and “lookup_LUID” are hardcoded functions in srum_dump. You can supplement the built-in known SIDS with those from your investigation by adding them to the lookup- Known Sids sheet.
ESE fields can be resolved dynamically when the format row contains “lookup-xlssheet-name”. You can Add XLS tabs containing lookup tables, then add srum-dump will use them to resolve values in ese tables if their table has the name of the lookup table in the format row.
See Also: Offensive Security Tool: SecretOpt1c
Conclusion
SRUM Dump is a powerful tool that can provide valuable insights into the usage of system resources on a Windows computer. Whether you are a digital forensics investigator or an information security professional, this tool can help you better understand the duration of process execution and identify the user account responsible for launching it. Adittionally, the ability to pinpoint data exfiltration within an hour provides invaluable information in forensic investigations. The inclusion of SRUM data offers valuable insights into process histories and network usage, significantly enhancing the depth and effectiveness of forensic investigations, particularly in incident response scenarios.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]



















