
Digital Forensics Tool: MemProcFS-Analyzer
MemProcFS-Analyzer is a PowerShell script designed to streamline memory forensics by integrating with MemProcFS (Memory Process File System).

MemProcFS-Analyzer is a PowerShell script designed to streamline memory forensics by integrating with MemProcFS (Memory Process File System).

Penelope is a shell handler designed to be easy to use and intended to replace netcat when exploiting RCE vulnerabilities.
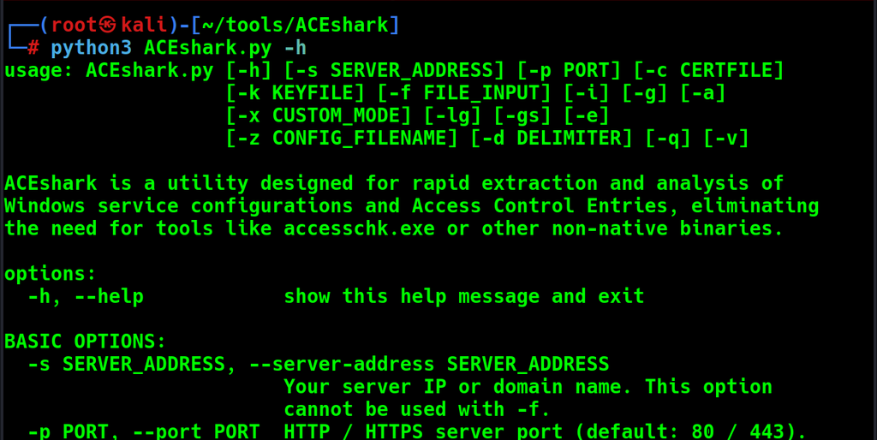
ACEshark is a Python-based utility that facilitates the rapid extraction and analysis of Windows service configurations and Access Control Entries (ACEs). It removes the dependency on external tools like accesschk.exe or other non-native binaries.

XSRFProbe is a tool designed to detect, audit, and exploit Cross-Site Request Forgery (CSRF/XSRF) vulnerabilities. It combines a robust crawling engine with systematic checks to identify vulnerabilities, assess related bypasses, and generate exploitative proof-of-concept scripts.

Sara is an autonomous security auditing tool designed specifically for analyzing RouterOS configurations on MikroTik hardware. This tool uses regular expressions to scan and identify potential vulnerabilities in configuration files.
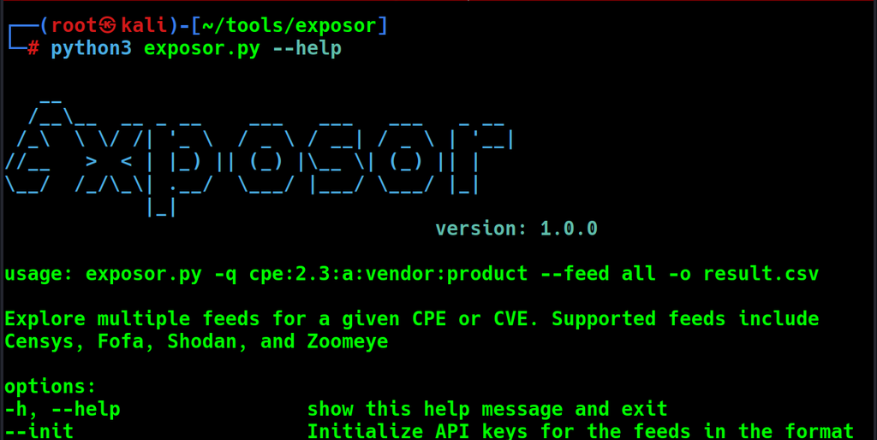
Exposor is a tool using internet search engines to detect exposed technologies with a unified syntax.