GDPR Compliance Solutions
What is the General Data Protection Regulation?
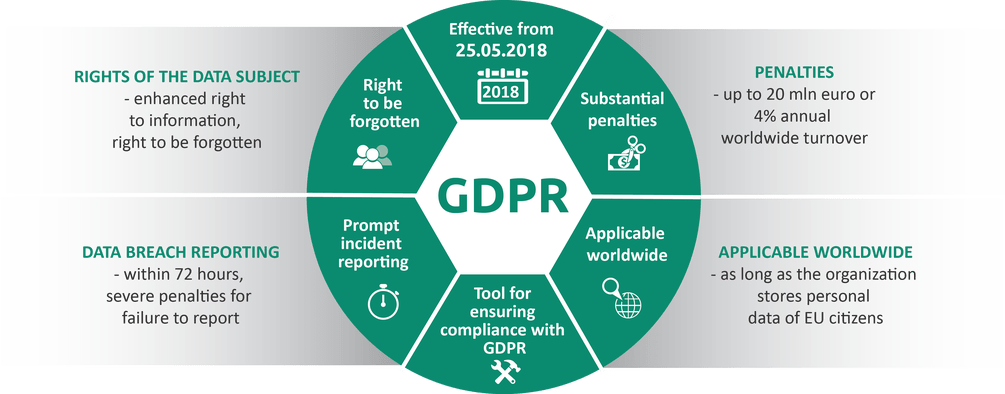
The General Data Protection Regulation (GDPR compliance) protects the personal data of EU citizens regardless of the geographical location of the organization of the data. Every Organization, small, medium, or large must be compliant with GDPR. Changes to people, processes, and technology are required to ensure that personal data is correctly controlled, processed, maintained, retained, and secured. The Training, and the mindset needed to perform such a way of work, in the digital world that we are living in, has to be implemented by law. Penalties for infringement of the General Data Protection Regulation can be up to €20,000,000 or 4% of worldwide annual turnover, whichever is the greater amount.
Article 5 of the GDPR mandates six principles related to the processing of Personal Data. Personal Data shall be:
- Processed lawfully, fairly, and in a transparent manner
- Collected for specified, explicit, and legitimate purposes
- Adequate, relevant, and limited to what is necessary
- Accurate and, where necessary, kept up to date
- Retained only for as long as is necessary
- Processed appropriately to maintain security
- Article 32: “… the controller and the processor shall implement appropriate technical and organizational measures to ensure a level of security appropriate to the risk, including inter alia as appropriate…”
After you set up your infrastructure, and adjusted and/or modified an application or a new hardware device, you need to check how they stand against attacks, you need to assess them before you go online.
- Article 33 & 34: Incident Response Program: “…In the case of a personal data breach, the controller shall without undue delay and, where feasible, not later than 72 hours after having become aware of it, notify the personal data breach to the supervisory authority competent by Article 55, unless the personal data breach is unlikely to result in a risk to the rights and freedoms of natural persons. Where the notification to the supervisory authority is not made within 72 hours, it shall be accompanied by reasons for the delay…”
Risk For Rights And Freedoms
- The processor shall notify the controller without undue delay after becoming aware of a personal data breach.
- The notification referred to in paragraph 1 shall at least:
(a) Describe the nature of the personal data breach including where possible, the categories and the approximate number of data subjects concerned and the categories and the approximate number of personal data records concerned.
(b) Communicate the name and contact details of the data protection officer or another contact point where more information can be obtained. (DPO)
(c) Describe the likely consequences of the personal data breach.
(d) Describe the measures taken or proposed to be taken by the controller to address the personal data breach, including, where appropriate, measures to mitigate its possible adverse effects.
- Where, and in so far as, it is not possible to provide the information at the same time, the information may be provided in phases without undue further delay.
- The controller shall document any personal data breaches, comprising the facts relating to the personal data breach, its effects, and the remedial action taken. That documentation shall enable the supervisory authority to verify compliance with this Article.
Throughout our solutions range from Vulnerability Assessments leading to Penetration Testing internal or external and Digital Forensics in case you already have been breached, we will help you accomplish that and earn the ISO 27001 certification.
Microsoft 365 Security Assessment
- Is our information secure in your Office 365 Setup?
- Who has access, both internally and externally to your network?
- What happens if your employees get their credentials compromised by hackers?
- How can you detect ransomware and other malware in Office 365?
- What do you need to do to maintain compliance and data privacy policies?
Office 365 is highly targeted due to its popularity and the important data that is hosted.
How can threat actors exploit or compromise your Office 365?
- Weak or legacy authentication mechanisms are weak when they perform recon
- Security controls that have not been optimally configured
- Accounts with privileged access levels
- Accounts with weak passwords or those that do not require multifactor authentication
Is a Microsoft Office 365 Security Assessment right for you?
Black Hat Ethical Hacking will assess your Office 365 going through the traditional penetration testing steps against your mail server. Depending on where you host your data, we will review your configuration from server to client using a series of attack vectors that are specifically designed to test your Office 365 Setup, and will send you a report of remediation that will help you set and harden your installation, which is a core component of your business.
Payment Card Industry (PCI) Security Assessment
The PCI Security Standards Council’s mission is to enhance global payment account data security by developing standards and supporting services that drive education, awareness, and effective implementation by stakeholders.
Keep your systems secure, and customers can trust you with their sensitive payment card information. When you stay compliant, you are part of the solution.
Why Perform the PCI Security Assessment?
Criminal Hackers want your cardholder data. By obtaining the Primary Account Number (PAN) and sensitive authentication data, a thief can impersonate the cardholder, use the card, and steal the cardholder’s identity.
The breach or theft of cardholder data affects the entire payment card ecosystem. Customers suddenly lose trust in merchants or financial institutions, and their credit can be negatively affected. Credibility is an important aspect in today’s digital era. Liabilities also are subject to numerous factors, and in turn, businesses would be affected risking serious downfalls.
These are some of the important aspects to consider, should you not take the PCI:
- Confidence is affected by your existing clients
- Reduced sales
- Cost of transitioning to a new payment system
- Legal costs, settlements, and judgments
- Fines and penalties
- Termination of the ability to accept payment cards
- Closing down your business
Ransomware Resiliency Assessment
Ransomware is a type of malicious software, or malware, designed to deny access to a computer system or data until a ransom is paid. Ransomware typically spreads through phishing emails or by a victim unknowingly visiting an infected website. A successful ransomware attack can result in:
- Freezing your business operations: Such attacks bring work to halt, preventing organizations from accessing critical data and keeping vital operations on pause.
- Exposing confidential records: Ransomware endangers the reputation and security of a company and exposes the confidential information of anyone in the system including social security numbers, credit card information, and health records.
- Financially impacting your organization: According to data compiled by the Cybersecurity and Infrastructure Security Agency, the average cost to mitigate a ransomware attack is $761,106.
What will I achieve by performing a Ransomware assessment?
A Ransomware assessment helps organizations strengthen their processes and technology to mitigate the threat of ransomware. Black Hat Ethical Hacking will help you reduce the risk to your critical infrastructure and protect your sensitive information.
You will be able to determine what layers of protection are already implemented, testing their capabilities and your response time to such attacks. Downtime is very important for a business and affects clients tremendously.
We will review the components of your security measures implemented, using Social Engineering techniques, and testing specific Payloads, that would allow us to identify what sort of mechanisms will be bypassed, and executed, simulating a real attack.
With ransomware on the rise, the question isn’t whether you’ll be targeted, it’s whether you have the right security controls in place to prevent your data from being locked down, published, or both, by attackers.
Check out our Solutions to get a quote
