10-Year-Old Windows vulnerability still being exploited in the 3CX attacks

A 10-year-old Windows vulnerability is still being exploited in attacks
A 10-year-old Windows vulnerability is still being exploited by cybercriminals to make it appear that executables are legitimately signed, with the fix from Microsoft still “opt-in” after all these years. Even worse, the fix is removed after upgrading to Windows 11, leaving devices vulnerable to supply chain attacks.
On Wednesday night, VoIP communications company 3CX confirmed that it was compromised to distribute trojanized versions of its Windows desktop application in a large-scale supply chain attack. The company urged all users of the Windows desktop application to uninstall it immediately and perform a malware scan.
According to 3CX, two DLLs used by the Windows desktop application were replaced with malicious versions that download additional malware to computers, such as an information-stealing trojan. One of the malicious DLLs used in the attack is usually a legitimate DLL signed by Microsoft named d3dcompiler_47.dll. However, the threat actors modified the DLL to include an encrypted malicious payload at the end of the file.
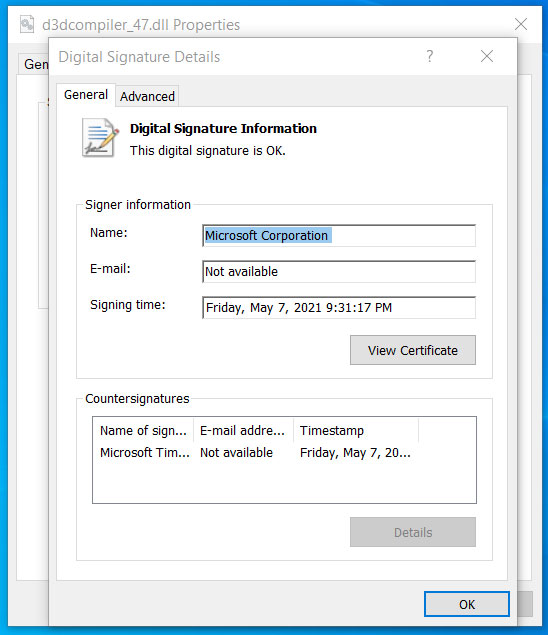 Modified DLL seen as having a valid signature
Modified DLL seen as having a valid signature
Source: BleepingComputer
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Signed Windows DLL Exploits CVE-2013-3900 Flaw, Allowing Modifications to Appear Authentic
As first noted by security researcher Will Dormann, even though the file was modified, Windows still showed it as correctly signed by Microsoft. Code signing an executable, such as a DLL or EXE file, is meant to assure Windows users that the file is authentic and has not been modified to include malicious code. When a signed executable is modified, Windows will display a message stating that the “digital signature of the object did not verify.” However, even though we know that the d3dcompiler_47.dll DLL was modified, it still showed as signed in Windows.
After contacting Dormann about this behavior and sharing the DLL, BleepingComputer was told that the DLL is exploiting the CVE-2013-3900 flaw, a “WinVerifyTrust Signature Validation Vulnerability.” Microsoft first disclosed this vulnerability on December 10th, 2013, and explained that adding content to an EXE’s authenticode signature section (WIN_CERTIFICATE structure) in a signed executable is possible without invalidating the signature.
Microsoft ultimately decided to make the fix optional, likely because it would invalidate legitimate, signed executables that stored data in the signature block of an executable. “This change can be enabled on an opt-in basis,” explains Microsoft’s disclosure for the CVE-2013-3900. “When enabled, the new behavior for Windows Authenticode signature verification will no longer allow extraneous information in the WIN_CERTIFICATE structure, and Windows will no longer recognize non-compliant binaries as signed.”
It is now close to ten years later, with the vulnerability known to be exploited by numerous threat actors. Yet, it remains an opt-in fix that can only be enabled by manually editing the Windows Registry. To enable the fix, Windows users on 64-bit systems can make the following Registry changes:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\Software\Microsoft\Cryptography\Wintrust\Config]
“EnableCertPaddingCheck”=”1”
[HKEY_LOCAL_MACHINE\Software\Wow6432Node\Microsoft\Cryptography\Wintrust\Config] “EnableCertPaddingCheck”=”1”
 |  |
Trending: Offensive Security Tool: Nginxpwner
Once these Registry keys are enabled, you can see how differently Microsoft validates the signature in the malicious d3dcompiler_47.dll DLL used in the 3CX supply chain attack. However, even if you add the Registry keys to apply the fix, they will be removed once you upgrade to Windows 11, making your device vulnerable again.
PSA: Upgrading to #Windows11 wipes out security mitigations for CVE-2013-3900, meaning that if you upgrade you must re-apply said mitigations.
— Matty (@ThePhoenixVents) January 5, 2023
As cybercriminals have recently exploited this vulnerability in attacks, such as the 3CX supply chain and a Zloader malware distribution campaign in January, it has become clear that the flaw needs to be fixed, even if it inconveniences developers.
The problem is that many people are unaware of this flaw, and they may assume that a malicious file is trustworthy because Windows reports it as being so.
Will Dormann, a security researcher, warned that “when a fix is optional, the masses aren’t going to be protected.”
To test the optional fix, I enabled it and used my computer as usual throughout the day without encountering any issues that made me regret my decision.Although some installers, such as Google Chrome, may not show as signed due to the fix, the added protection is worth the inconvenience.
BleepingComputer has contacted Microsoft regarding the continued abuse of this vulnerability and the fact that the fix is optional, but no response has been received yet.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












