Abyss Locker: New Linux Encryptor Targets VMware’s ESXi Virtual Machines

The notorious Abyss Locker operation joins the ranks of cybercriminals developing Linux encryptors to target the widely-used VMware ESXi virtual machines platform. With enterprises increasingly adopting virtual machines for better resource management, performance, and disaster recovery, ransomware gangs are turning their attention to these virtual environments.
VMware ESXi, being one of the most popular virtual machine platforms, has become a prime target for cybercriminals seeking to exploit its vulnerabilities. Numerous ransomware operations, including Akira, Royal, Black Basta, LockBit, BlackMatter, AvosLocker, REvil, HelloKitty, RansomEXX, and Hive, have already released Linux encryptors tailored to target VMware ESXi servers.
Abyss Locker
Abyss Locker, a relatively new ransomware operation believed to have emerged in March 2023, has swiftly adopted this strategy. Like its counterparts, the Abyss Locker gang gains access to corporate networks, steals valuable data for double extortion purposes, and encrypts devices across the network. The threat actors then use the stolen data as leverage, threatening to leak sensitive files if the ransom is not paid. To facilitate the data leaks, the criminals have set up a Tor data leak site known as ‘Abyss-data,’ which currently lists fourteen victims, with data theft ranging from 35 GB to a staggering 700 GB.
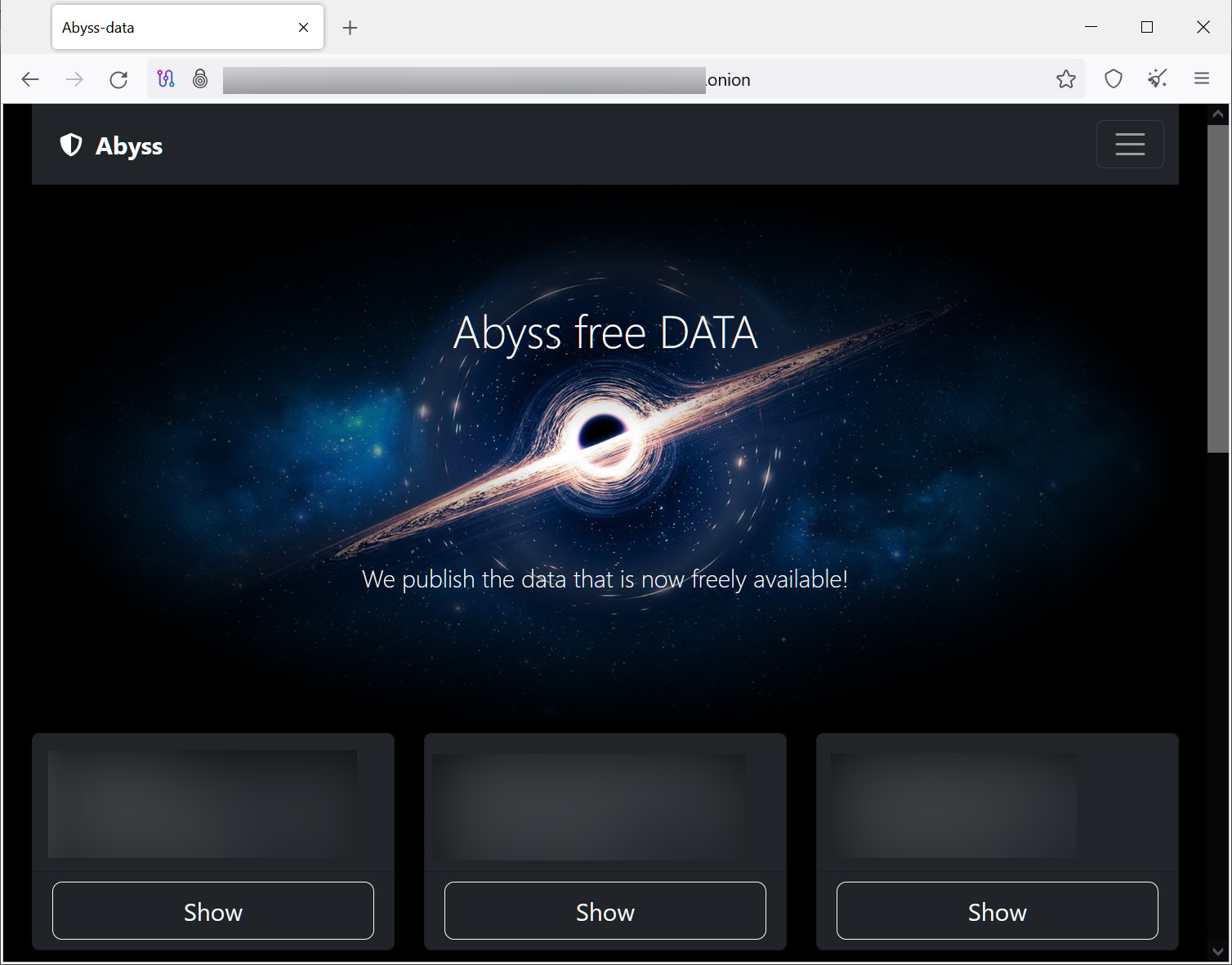 Abyss Locker data leak site
Abyss Locker data leak site
Source: BleepingComputer
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The latest development in Abyss Locker’s arsenal is the discovery of a Linux ELF encryptor specifically designed to target VMware ESXi servers. Security researchers have identified the use of the ‘esxcli’ command-line tool for VMware ESXi management to list and terminate all available virtual machines. The encryptor employs various options, including soft, hard, and force, to gracefully shut down, terminate, or forcefully shut down VMs, respectively.
esxcli vm process list
esxcli vm process kill -t=soft -w=%d
esxcli vm process kill -t=hard -w=%d
esxcli vm process kill -t=force -w=%d
This orchestrated shutdown allows the ransomware to encrypt associated virtual disks, metadata, and snapshots by encrypting files with specific extensions, including .vmdk (virtual disks), .vmsd (metadata), and .vmsn (snapshots).
However, the scope of the attack extends beyond virtual machines, as the ransomware encrypts all other files on the infected device and appends the .crypt extension to their filenames.
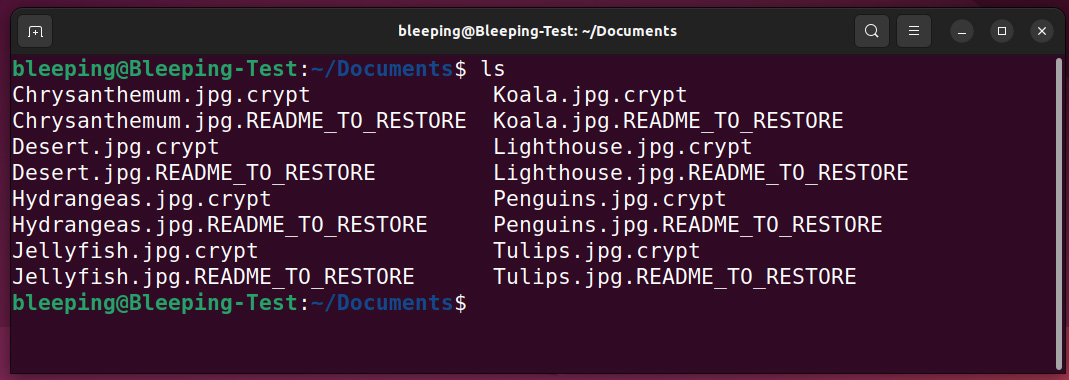 Encrypted files and ransom notes
Encrypted files and ransom notes
Source: BleepingComputer
Each encrypted file is accompanied by a ransom note file with a .README_TO_RESTORE extension, providing information on the encryption and a unique link to the threat actor’s Tor negotiation site, where victims can potentially negotiate with the attackers.
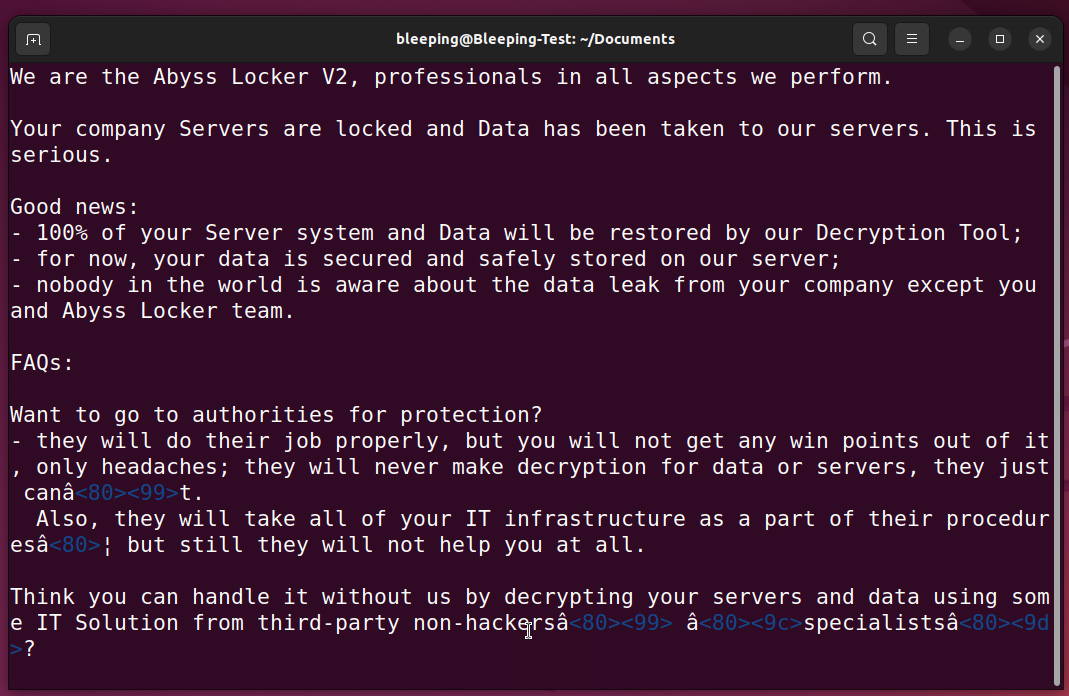 Abyss Locker ransom note
Abyss Locker ransom note
Source: BleepingComputer
Trending: Offensive Security Tool: Nucleimonst3r
Ransomware expert Michael Gillespie has noted that the Abyss Locker Linux encryptor is based on Hello Kitty, but utilizes ChaCha encryption instead. It remains uncertain whether this marks a rebranding of the HelloKitty operation or if another ransomware group gained access to the encryptor’s source code, as previously seen with Vice Society.
HelloKitty has a reputation for being highly secure, making file recovery without payment a challenging endeavor for victims.
As the Abyss Locker operation embraces this formidable encryptor, enterprises must remain vigilant and take necessary precautions to safeguard their virtual environments from ransomware threats.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












