Accellion FTA Zero-Day Attacks Show Ties to Clop Ransomware, FIN11

Reading Time: 2 Minutes
The threat actors stole data and used Clop’s leaks site to demand money in an extortion scheme, though no ransomware was deployed.
Multiple Accellion FTA customers, including the Jones Day Law Firm, Kroger and Singtel, have all been attacked by the group, receiving extortion emails threatening to publish stolen data on the “CL0P^_- LEAKS” .onion website, according to an investigation from Accellion and FireEye Mandiant. Around 100 companies have been victims of the attack, analysts found, with around 25 suffering “significant data theft.” No ransomware was used in the attacks.
“Notably, the number of victims on the “CL0P^_- LEAKS” shaming website has increased in February 2021 with organizations in the United States, Singapore, Canada and the Netherlands recently outed by these threat actors,” according to the Mandiant findings, issued on Monday.
4 Accellion FTA Zero-Days
As noted, the point of entry for the attacks was Accellion FTA, a 20-year-old legacy product used by large corporations around the world. Accellion said that it became aware of a zero-day security vulnerability in FTA in mid-December, which it scrambled to patch quickly. But that turned out to be just one of a cascade of zero-days in the platform that the company discovered only after they came under attack from cyber-adversaries.
“This initial incident was the beginning of a concerted cyberattack on the Accellion FTA product that continued into January 2021,” the company explained. “Accellion identified additional exploits in the ensuing weeks, and rapidly developed and released patches to close each vulnerability.”
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
Four zero-day security holes were exploited in the attacks, according to the investigation:
- CVE-2021-27101 – SQL injection via a crafted Host header
- CVE-2021-27102 – OS command execution via a local web service call
- CVE-2021-27103 – SSRF via a crafted POST request
- CVE-2021-27104 – OS command execution via a crafted POST request
And, the published victim data appears to have been stolen using a distinct “DEWMODE” web shell, according to Mandiant, which added, “The exfiltration activity has affected entities in a wide range of sectors and countries.”
DEWMODE Web Shell for Stealing Information
Mandiant found that a specific web shell, which it calls DEWMODE, was used to exfiltrate data from Accellion FTA devices. The adversaries first exploited one of the zero-days, then used that access to install DEWMODE.
“Across these incidents, Mandiant observed common infrastructure usage and TTPs [tactics, techniques and procedures], including exploitation of FTA devices to deploy the DEWMODE web shell,” Mandiant determined. “A common threat actor we now track as UNC2546 was responsible for this activity. While complete details of the vulnerabilities leveraged to install DEWMODE are still being analyzed, evidence from multiple client investigations has shown multiple commonalities in UNC2546’s activities.”
The firm is still analyzing the zero-day exploitation, but it did say that in the early attacks in December, UNC2546 leveraged an SQL injection vulnerability in the Accellion FTA as its primary intrusion vector. SQL injection was then followed by subsequent requests to additional resources.
“UNC2546 has leveraged this SQL injection vulnerability to retrieve a key which appears to be used in conjunction with a request to the file sftp_account_edit.php,” according to the analysis. “Immediately after this request, the built-in Accellion utility admin.pl was executed, resulting in an eval web shell being written to oauth.api. Almost immediately following this sequence, the DEWMODE web shell is written to the system.”
DEWMODE, once embedded, extracts a list of available files from a MySQL database on the FTA and lists those files and corresponding metadata—file ID, path, filename, uploader and recipient—on an HTML page. UNC2546 then uses the presented list to download files through the DEWMODE web shell.
In a subset of incidents, Mandiant observed UNC2546 requesting a file named cache.js.gz – an archive that likely contained a dump of a database.
See Also: Offensive Security Tool: ScareCrow
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
Extortion via Clop Leaks Site
Once DEWMODE was installed, victims began to receive extortion emails from an actor claiming association with the Clop ransomware team gang.
These are tailored to each victim and sent from a free email account, to a small number of addresses at the victim organization. If the victim did not respond in a timely manner, more emails are sent, this time to hundreds or thousands of different email accounts, using varied SMTP infrastructure.
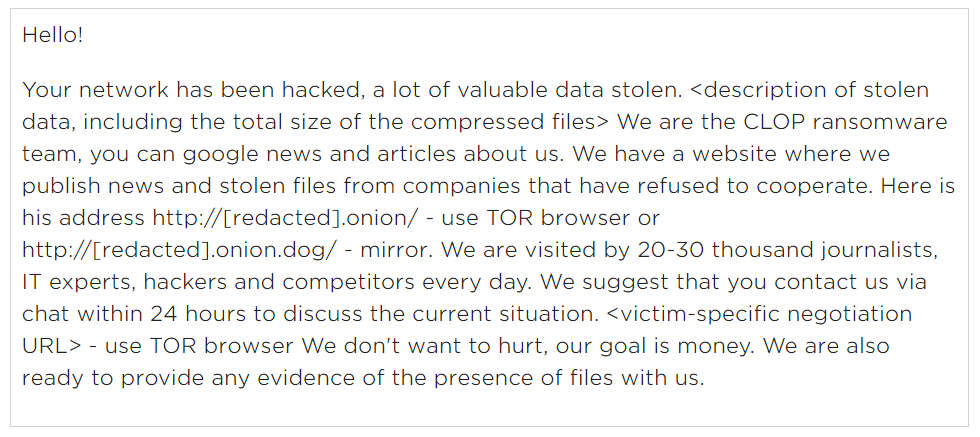
The initial extortion note sent to victims of the Accellion FTA attacks. Source: FireEye Mandiant.
“In at least one case, UNC2582 also sent emails to partners of the victim organization that included links to the stolen data and negotiation chat,” according to Mandiant.
The firm also found through monitoring the CL0P^_- LEAKS shaming website that UNC2582 has followed through on threats to publish stolen data.
“Several new victims have appeared on the site in recent weeks, including at least one organization that has publicly confirmed that their Accellion FTA device had been recently targeted,” according to Mandiant.
FIN11, Clop and UNC2546
FIN11 is a financially motivated group that has been around for at least four years, conducting widespread phishing campaigns. However, it continues to evolve. It added the use of Clop (which emerged in February 2019) and double extortion in October; and added point-of-sale (POS) malware to its arsenal in 2018. In 2019, it started conducting run-of-the-mill ransomware attacks.
Mandiant has previously found that FIN11 threatened to post stolen victim data on the same .onion site used in the Accellion FTA attacks, usually in a double-extortion demand following the deployment of Clop ransomware. However, researchers found that the cybercriminals involved in these latest attacks are likely distinct from FIN11 itself despite sharing some overlaps.
“We are currently tracking the exploitation of the zero-day Accellion FTA vulnerabilities and data theft from companies running the legacy FTA product as UNC2546, and the subsequent extortion activity as UNC2582,” according to Mandiant. “We have identified overlaps between UNC2582, UNC2546 and prior FIN11 operations, and we will continue to evaluate the relationships between these clusters of activity.”
Some of the overlaps between UNC2582’s data-theft extortion activity and prior FIN11 operations include common email senders.
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
See Also: SolarWinds Supply Chain Hack – The hack that shone a light on the gaps in the cybersecurity of governments and big companies
“Some UNC2582 extortion emails observed in January 2021 were sent from IP addresses and/or email accounts used by FIN11 in multiple phishing campaigns between August and December 2020, including some of the last campaigns that were clearly attributable to the group,” according to the analysis.
FIN11 has also used same the CL0P^_- LEAKS shaming site and is known for deploying Clop ransomware.
“The UNC2582 extortion emails contained a link to the CL0P^_- LEAKS website and/or a victim specific negotiation page,” according to Mandiant. “The linked websites were the same ones used to support historical Clop operations, a series of ransomware and data theft extortion campaigns we suspect can be exclusively attributed to FIN11.”
When it comes to the zero-day cluster of activity, attributed to UNC2546, there are also limited overlaps with FIN11. Specifically, many of the organizations compromised by UNC2546 were previously targeted by FIN11.
And, “an IP address that communicated with a DEWMODE web shell was in the ‘Fortunix Networks L.P.’ netblock, a network frequently used by FIN11 to host download and FRIENDSPEAK command-and-control (C2) domains.”
There’s also a connection between UNC2546 and UNC2582, the firm found: In at least one case, the UNC2546 attackers interacted with DEWMODE from a host that was used to send UNC2582-attributed extortion email.
“The overlaps between FIN11, UNC2546 and UNC2582 are compelling, but we continue to track these clusters separately while we evaluate the nature of their relationships,” Mandiant concluded. “One of the specific challenges is that the scope of the overlaps with FIN11 is limited to the later stages of the attack life cycle. UNC2546 uses a different infection vector and foothold, and unlike FIN11, we have not observed the actors expanding their presence across impacted networks.”
Also, using SQL injection to deploy DEWMODE would represent a significant shift in FIN11 TTPs, “given the group has traditionally relied on phishing campaigns as its initial infection vector and we have not previously observed them use zero-day vulnerabilities,” Mandiant added.
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
Source: https://threatpost.com
(Click Link)



