Android malware apps with 2 million installs spotted on Google Play

Reading Time: 3 Minutes
A new set of Android malware, phishing, and adware apps have infiltrated the Google Play store, tricking over two million people into installing them.
The apps were discovered by Dr. Web antivirus and pretend to be useful utilities and system optimizers but, in reality, are the sources of performance hiccups, ads, and user experience degradation.
One app illustrated by Dr. Web that has amassed one million downloads is TubeBox, which remains available on Google Play at the time of writing this.
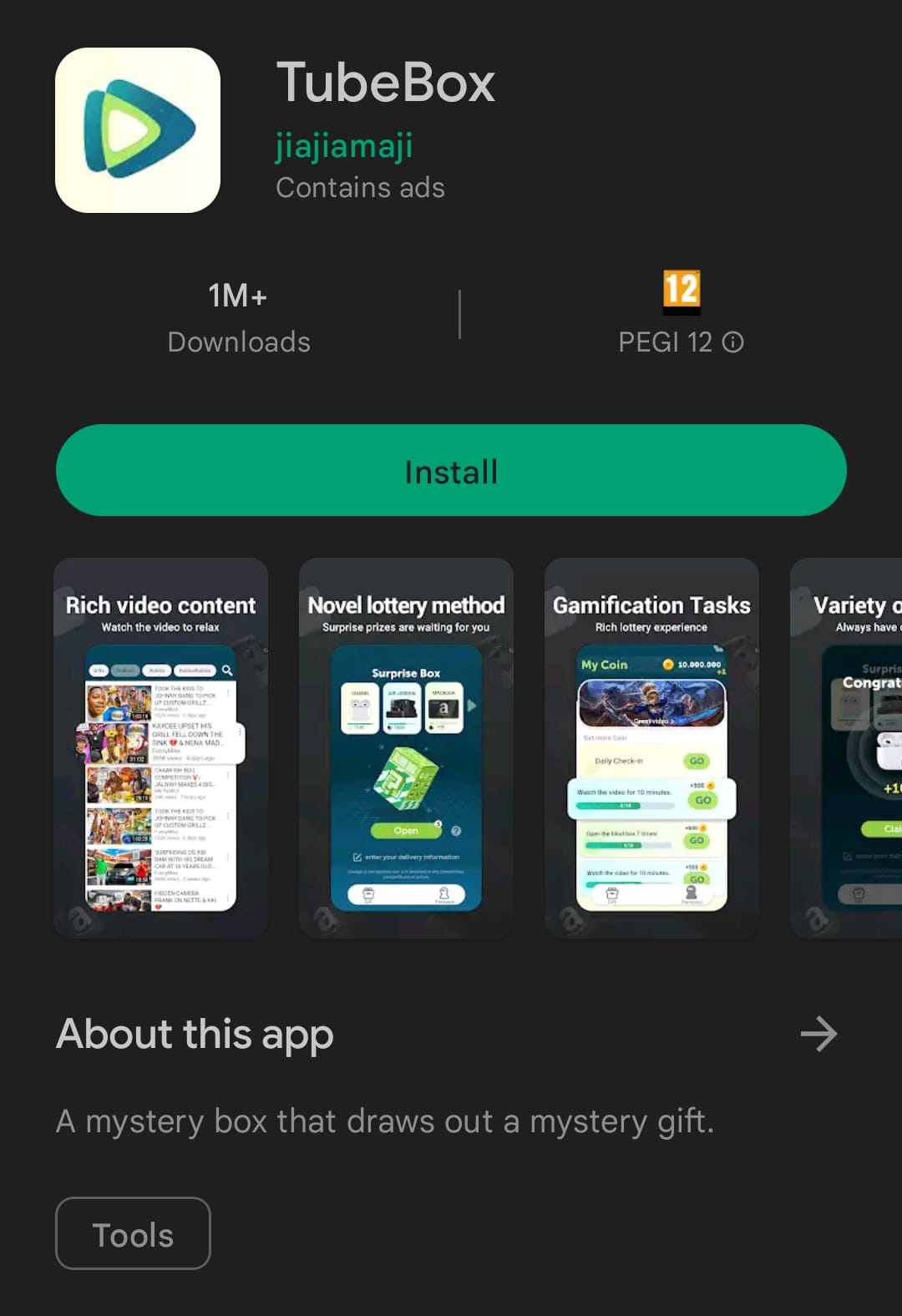
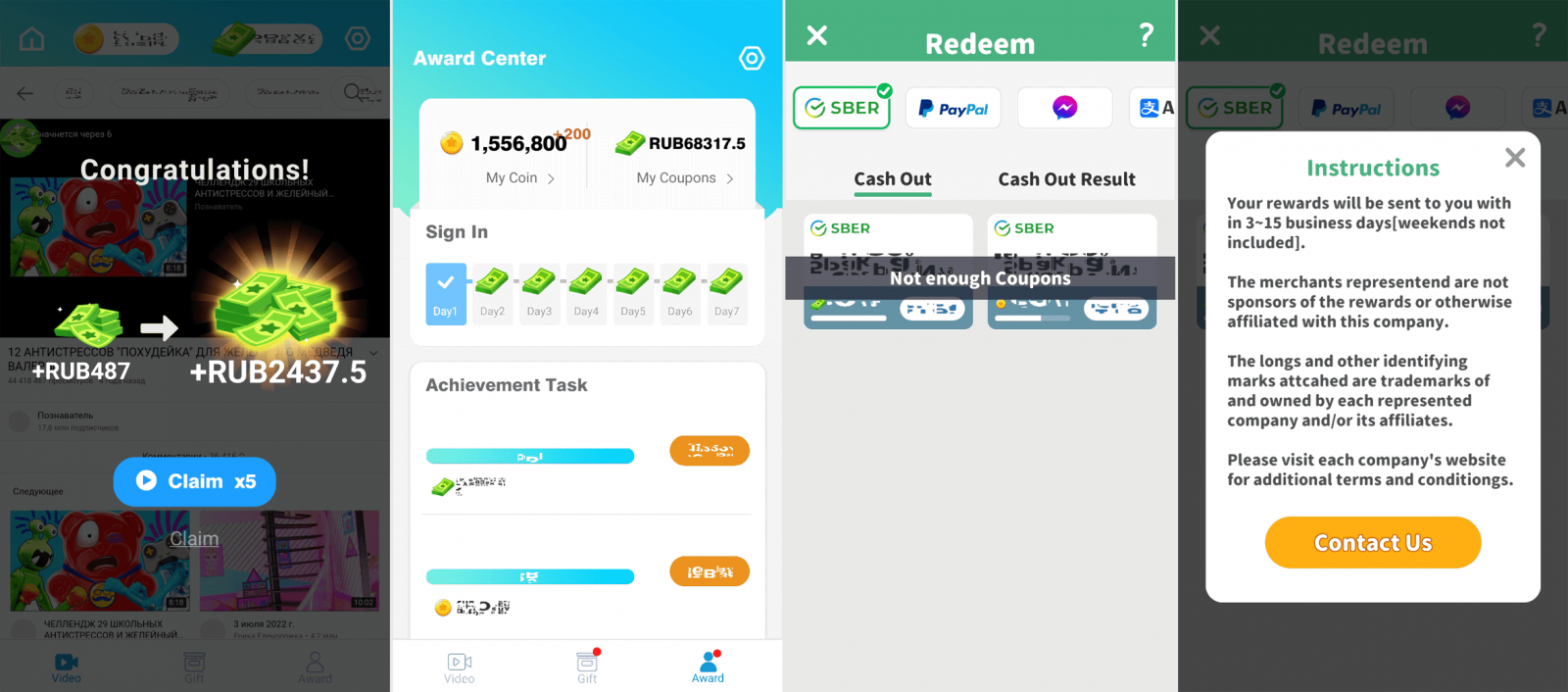
TubeBox promises monetary rewards for watching videos and ads on the app but never delivers on its promises, presenting various errors when trying to redeem the collected rewards.
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
Even users who get to complete the final withdrawal step never really receive the funds, as the researchers say it’s all a trick to try and keep them on the app for as long as possible, watching ads and generating revenue for the developers.
Other adware apps that appeared on Google Play in October 2022 but have since been removed are:
- Bluetooth device auto connect (bt autoconnect group) – 1,000,000 downloads
- Bluetooth & Wi-Fi & USB driver (simple things for everyone) – 100,000 downloads
- Volume, Music Equalizer (bt autoconnect group) – 50,000 downloads
- Fast Cleaner & Cooling Master (Hippo VPN LLC) – 500 downloads
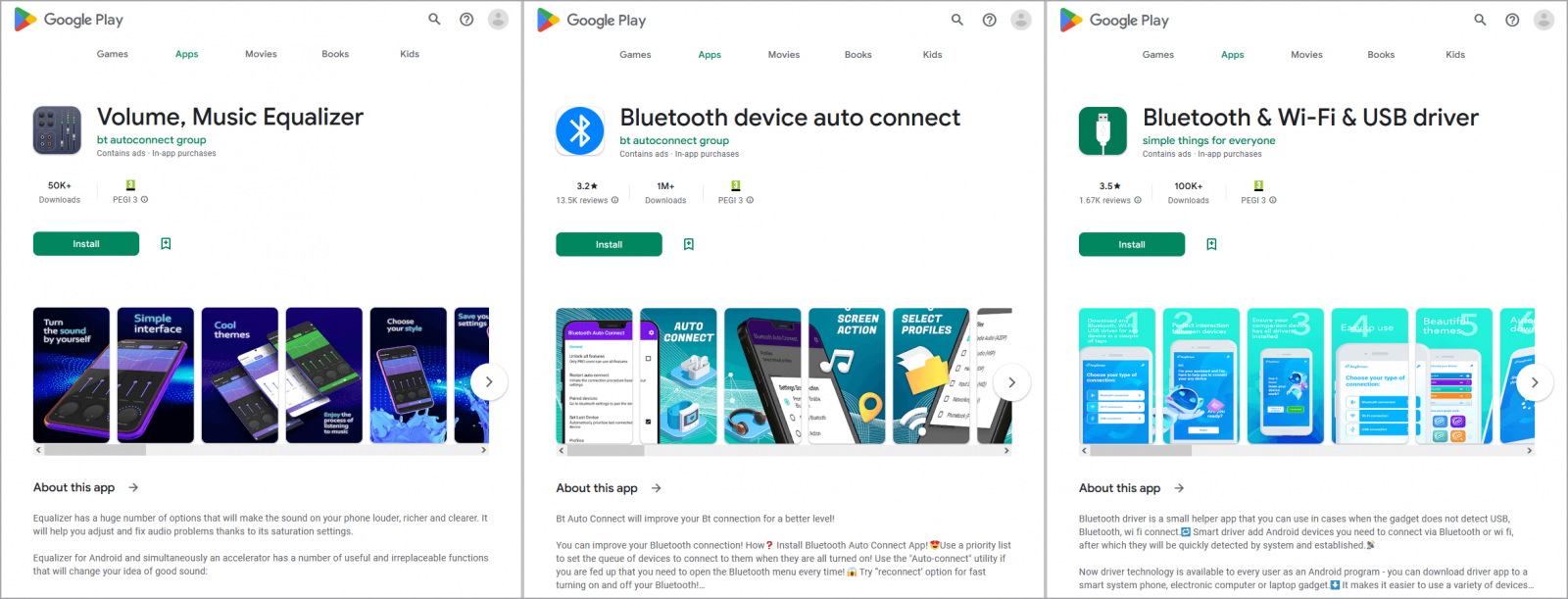
The above apps receive commands from Firebase Cloud Messaging and load the websites specified in these commands, generating fraudulent ad impressions on the infected devices.
In the case of Fast Cleaner & Cooling Master, which had a low download volume, the remote operators could also configure an infected device to act as a proxy server. This proxy server would allow the threat actors to channel their own traffic through the infected device.
Finally, Dr. Web discovered a set of loan scam apps claiming to have a direct relationship with Russian banks and investment groups, each having an average of 10,000 downloads on Google Play.
Trending: Exploiting LFI Vulnerabilities
Trending: Offensive Security Tool: Villain
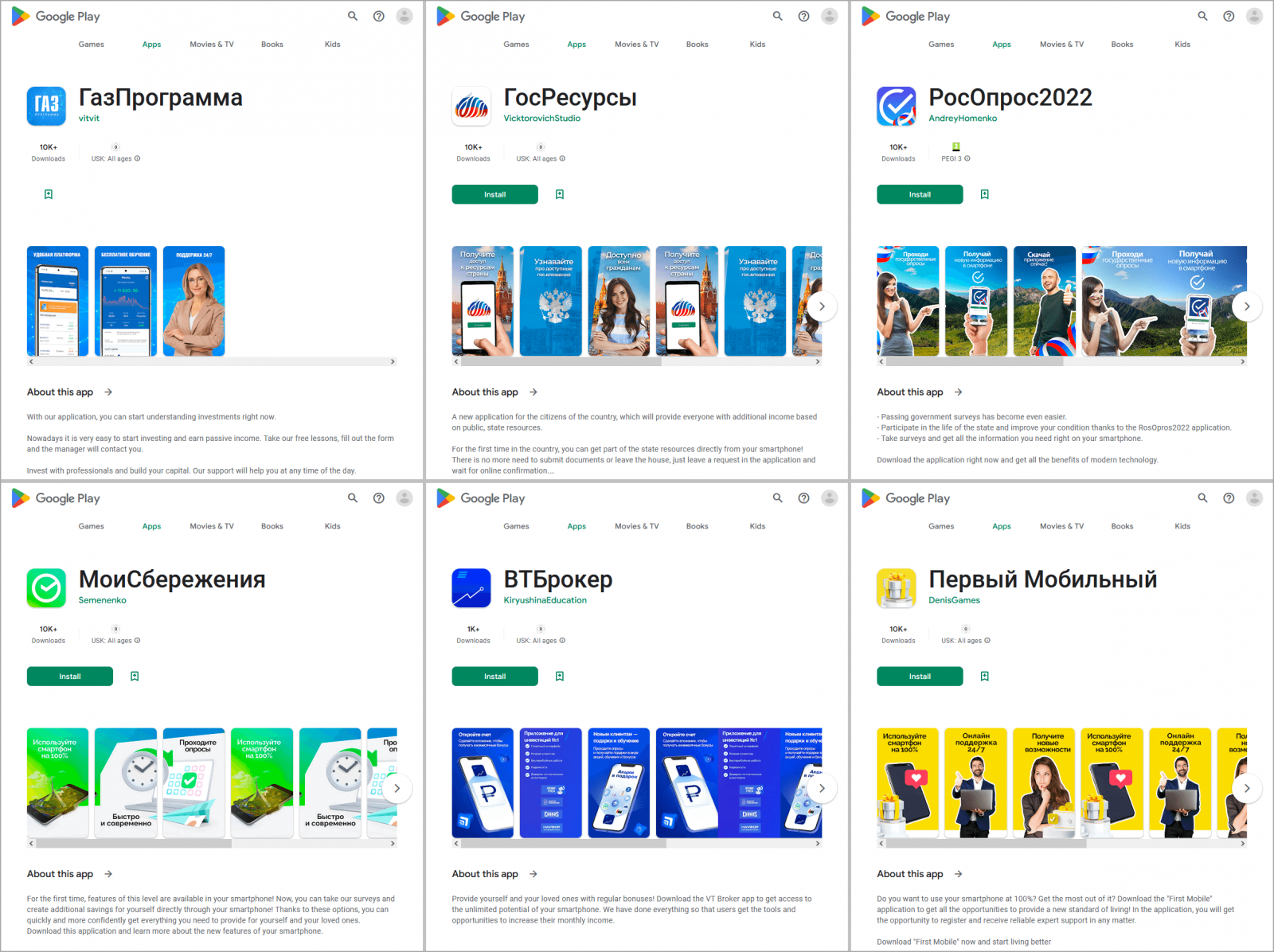
These apps were promoted via malvertizing through other apps, promising guaranteed investment profits. In reality, the apps take the users to phishing sites where their personal information is collected.
To protect yourself from fraudulent apps on Google Play, always check for negative reviews, scrutinize the privacy policy, and visit the developer’s site to evaluate its authenticity.
In general, try to keep the number of installed apps on your device at a minimum and periodically check and ensure that Google’s Play Protect feature is active.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












