Apple Under Attack: New GoFetch Exploit Targets Secret Keys in M-Series Processors

A side-channel attack dubbed “GoFetch” has emerged, posing a significant threat to the security of Apple’s M-Series processors, including the M1, M2, and M3 chips. This sophisticated attack method has the capability to stealthily extract secret cryptographic keys from data residing in the CPU’s cache.
Developed by a team of seven researchers from various U.S. universities, GoFetch leverages a weakness in constant-time cryptographic implementations utilizing data memory-dependent prefetchers (DMPs) present in modern Apple CPUs. By exploiting this vulnerability, attackers can reconstruct private cryptographic keys for various algorithms, including OpenSSL Diffie-Hellman, Go RSA, CRYSTALS Kyber, and Dilithium, directly from the CPU’s cache.
Gofetch Attack
The crux of the GoFetch attack lies in the manipulation of data memory-dependent prefetchers, a CPU feature designed to enhance performance by predicting and fetching data from memory into the CPU cache. Specifically, the attack targets a newer prefetcher variant known as the DMP, which can be trained based on memory access patterns and data values. However, a flaw in Apple’s implementation of the DMP system violates the constant-time programming paradigm, enabling attackers to craft inputs that trigger the prefetcher to inadvertently disclose sensitive data.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
While Intel’s 13th Gen Raptor Lake CPUs also feature the DMP prefetcher, the researchers note that Intel’s implementation is more restrictive and less susceptible to the GoFetch attack.
Moreover, the attack is contingent on cryptographic implementations exhibiting constant-time execution, which is essential for preventing sensitive data leaks.
The ramifications of GoFetch extend beyond theoretical speculation, with the researchers confirming its susceptibility on M1 processors and suggesting similar vulnerabilities in M2 and M3 variants due to analogous prefetching behavior. While potential defense mechanisms such as input blinding and DMP activation masking may offer some respite, mitigating the threat through software patches would inevitably result in performance degradation, as witnessed in previous attempts to address side-channel attacks.
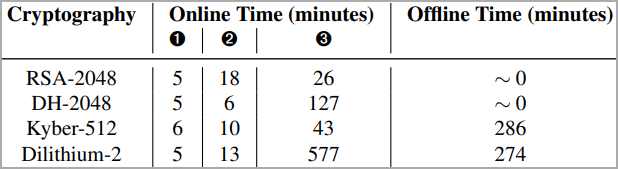 Time to derive full keys (online – live attack, offline – post-processing)
Time to derive full keys (online – live attack, offline – post-processing)
Apple owners are urged to remain vigilant in the face of this threat, as the hardware-based nature of the vulnerability renders it immune to traditional software fixes. Although it may be possible to disable DMP on certain CPUs, such as the M3, to mitigate the risk, this option is unavailable for M1 and M2 processors.
As a proactive measure, developers are advised to implement defense mechanisms such as input blinding and DMP activation masking to obscure the attacker’s input results. However, any potential software patches from Apple to address the vulnerability may come at the cost of performance, as observed with previous side-channel attack mitigations.
Trending: Digital Forensics Tool: mailMeta


