APT-C-60 Exploits Zero-Day Vulnerabilities in WPS Office to Install SpyGlace Backdoor

The South Korea-aligned cyberespionage group, APT-C-60, has been actively exploiting a zero-day code execution vulnerability in WPS Office to install the SpyGlace backdoor on targets in East Asia. The productivity suite, developed by the Chinese firm Kingsoft, is highly popular in Asia and has over 500 million active users worldwide.
Key Details
Zero-Day Vulnerability (CVE-2024-7262):
- Discovered: Exploited in the wild since at least late February 2024.
- Affected Versions: Versions from 12.2.0.13110 (August 2023) to 12.1.0.16412 (March 2024).
- Patched: Silently patched by Kingsoft in March 2024 without informing customers.
- Discovery: ESET discovered the campaign and published a detailed report.
Second Severe Flaw (CVE-2024-7263):
- Discovery: Found during investigation of APT-C-60 attacks.
- Patched: Kingsoft patched this flaw in late May 2024 with version 12.2.0.17119.
- Nature: Emerged as an incomplete patch of CVE-2024-7262, leaving some parameters like ‘CefPluginPathU8’ inadequately secured.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Exploit Details
- Vulnerability Mechanism: CVE-2024-7262 involves improper validation and sanitization of custom protocol handlers, specifically ‘ksoqing://,’ allowing execution of external applications via crafted URLs within documents.
- Attack Method: APT-C-60 embedded malicious hyperlinks in spreadsheet documents (MHTML files) hidden under decoy images. Clicking these images triggers the exploit, processing URL parameters that include a base64-encoded command.
- Execution Flow:
- Command executes a specific plugin (promecefpluginhost.exe).
- Plugin loads a malicious DLL (ksojscore.dll) containing the attacker’s code.
- DLL acts as a downloader for the final payload (TaskControler.dll), the SpyGlace backdoor.
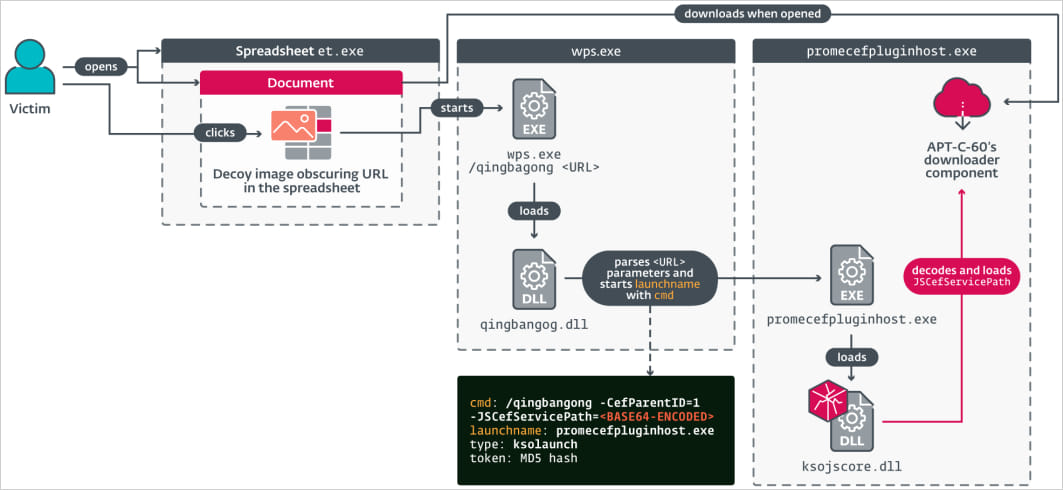 APT-C-60’s attack overview
APT-C-60’s attack overview
Source: ESET
SpyGlace Backdoor
- Previous Use: Analyzed by Threatbook; used by APT-C-60 in attacks on human resources and trade-related organizations.
- Functionality: SpyGlace enables remote access and control, allowing data exfiltration and further compromise of the infected systems.
Trending: Digital Forensics Tool: Horus
Bad Patch Vulnerability (CVE-2024-7263)
- Nature: Incomplete patch of CVE-2024-7262.
- Mechanism: Added validation missed some parameters, allowing continued exploitation.
- Exploit Potential: Can be exploited locally or through a network share to host malicious DLLs.
Recommendations
- Update WPS Office: Users are urged to update to the latest release, or at least version 12.2.0.17119, to address both CVE-2024-7262 and CVE-2024-7263.
- Awareness and Caution: Users should be cautious about opening documents from unknown sources, especially those with embedded images or links.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













