APT hacking group uses double DLL sideloading to bypass security

Using Complex Variations of DLL Sideloading to Evade Detection
An APT hacking group, known as “Dragon Breath,” “Golden Eye Dog,” or “APT-Q-27,” is demonstrating a new trend of using complex variations of the classic DLL sideloading technique to evade detection. According to Sophos analysts who followed the recent attacks of this group, the targeting scope of this campaign is focused on Chinese-speaking Windows users in China, Japan, Taiwan, Singapore, Hong Kong, and the Philippines.
The campaign leverages a clean application, most often Telegram, that sideloads a second-stage payload, sometimes also clean, which in turn, sideloads a malicious malware loader DLL.
The group has been able to achieve evasion, obfuscation, and persistence using the “double DLL sideloading” technique, which is making it harder for defenders to adjust to specific attack patterns and effectively shield their networks.
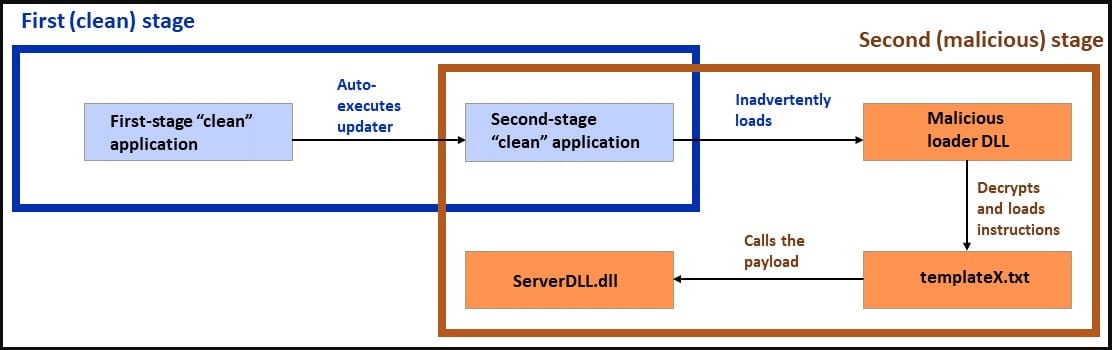 General attack diagram (Sophos)
General attack diagram (Sophos)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Double DLL sideloading technique
DLL sideloading is a technique that attackers have been exploiting since 2010 by taking advantage of the insecure way Windows loads DLL (Dynamic Link Library) files required by an application. The attacker places a malicious DLL with the same name as the legitimate, required DLL in an application’s directory. When the user launches the executable, Windows prioritizes the local malicious DLL over the one in the system folders. The attacker’s DLL contains malicious code that loads at this stage, giving the attacker privileges or running commands on the host by exploiting the trusted, signed application that is loading it.
The group’s attack begins when the victims execute the installer of the mentioned apps, which drops components on the system and creates a desktop shortcut and a system startup entry. If the victim attempts to launch the newly created desktop shortcut, instead of launching the app, a command is executed on the system that runs a renamed version of ‘regsvr32.exe’ (‘appR.exe’) to execute a renamed version of ‘scrobj.dll’ (‘appR.dll’) and supplies a DAT file (‘appR.dat’) as input to it. The DAT contains JavaScript code for execution by the script execution engine library (‘appR.dll’).
The JavaScript code launches the Telegram app user interface in the foreground while installing various sideloading components in the background.
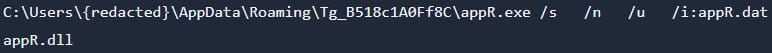 Command executed on the breached system (Sophos)
Command executed on the breached system (Sophos)
Trending: Offensive Security Tool: Go365
In all observed attack variations, the final payload DLL is decrypted from a txt file (‘templateX.txt’) and executed on the system. This payload is a backdoor that supports several commands.
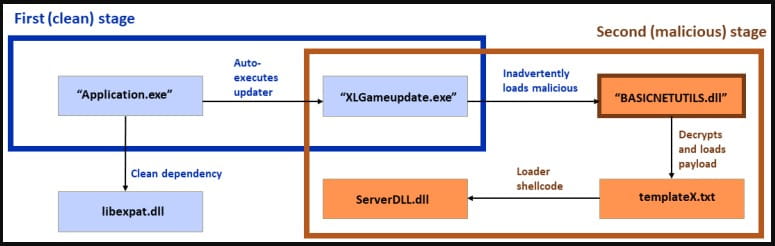 First attack variant diagram (Sophos)
First attack variant diagram (Sophos)
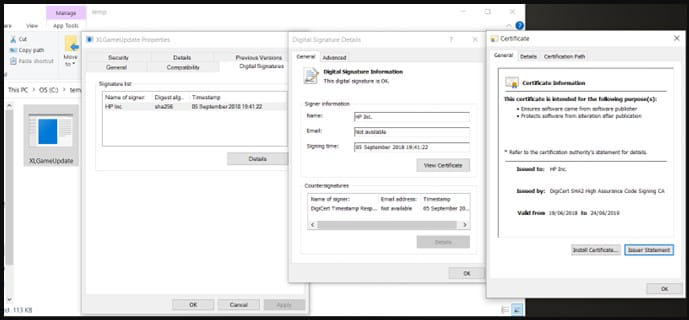 Executable signed by HP – Third Variation of the attack (Sophos)
Executable signed by HP – Third Variation of the attack (Sophos)
The group has trojanized Telegram, LetsVPN, or WhatsApp apps for Android, iOS, or Windows that have been supposedly localized for people in China. The trojanized apps are believed to be promoted using BlackSEO or malvertizing.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












