Attackers Could Exploit Flaw in WiFi Protocol to Hijack TCP Connections

Vulnerability in the IEEE 802.11 WiFi protocol standard
Cybersecurity researchers have found a significant vulnerability in the IEEE 802.11 WiFi protocol standard, which can be exploited by hackers to trick access points into leaking network frames in plaintext form. WiFi frames are data containers that contain information such as the source and destination MAC address, control, and management data. The researchers discovered that queued or buffered frames are not adequately protected from attackers, who can manipulate data transmission, client spoofing, frame redirection, and capturing.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
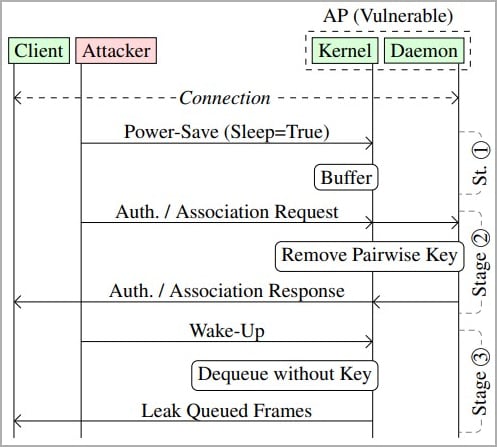
Power-saving flaw
The IEEE 802.11 standard includes power-save mechanisms that allow WiFi devices to conserve power by buffering or queuing frames destined for sleeping devices. However, the standard does not provide explicit guidance on managing the security of these queued frames and does not set limitations on how long the frames can stay in this state. An attacker can spoof the MAC address of a device on the network and send power-saving frames to access points, forcing them to start queuing frames destined for the target.
Attack diagram (papers.mathyvanhoef.com)
The researchers warn that these attacks could be used to inject malicious content, such as JavaScript, into TCP packets.
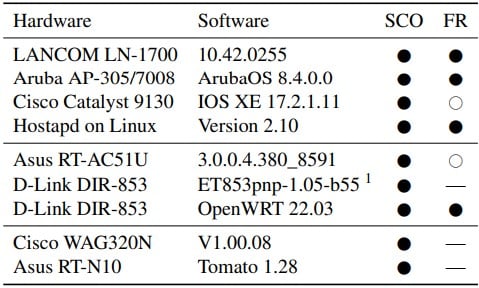
Tested devices found vulnerable (papers.mathyvanhoef.com)
The flaw impacts devices and operating systems across various models, including Cisco, Asus, D-Link, and Aruba. While no instances of malicious use have been reported, experts warn that attackers could exploit the vulnerability to inject malicious content, such as JavaScript, into TCP packets, which could be used to exploit vulnerabilities in a victim’s browser
Trending: Offensive Security Tool: OpenRediWrecked
Cisco acknowledges vulnerability
Cisco has acknowledged the vulnerability and recommends mitigation measures, including implementing policy enforcement mechanisms and transport layer security.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












