Azure’s New Feature Opens Doors for Lateral Attacks, Microsoft Tenants at Risk

In a bid to enhance collaboration and automate lifecycle management, Microsoft introduced the Azure Active Directory Cross-Tenant Synchronization (CTS) feature in June 2023. However, cybersecurity researchers are now raising concerns about this new capability, as it has opened up a potential attack surface that could be exploited by threat actors to facilitate lateral movement between connected Azure tenants.
Large organizations often divide their operations into multiple tenants within Azure Active Directory for organizational purposes. The CTS feature allows administrators to synchronize users and groups across these authorized tenants, streamlining collaboration and project management. When configured, users from a source tenant can be automatically synchronized to a target tenant, creating a one-sided synchronization process.
Despite the potential benefits, improper configuration of CTS could introduce security risks. If a threat actor successfully compromises a privileged account within a tenant, they may exploit CTS to move laterally to other connected tenants and even establish persistence on those networks.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The cybersecurity firm Vectra has provided insights into how attackers could abuse this feature for lateral movement and persistence, stressing the importance of detecting and mitigating such threats.
Vectra outlines two techniques that attackers could employ. The first involves identifying target tenants connected through CTS policies with ‘Outbound Sync’ enabled, allowing syncing to other tenants. The attacker then modifies the configuration of the app used for CTS syncing to add the compromised user into its sync scope, gaining unauthorized access to the target tenant’s network.
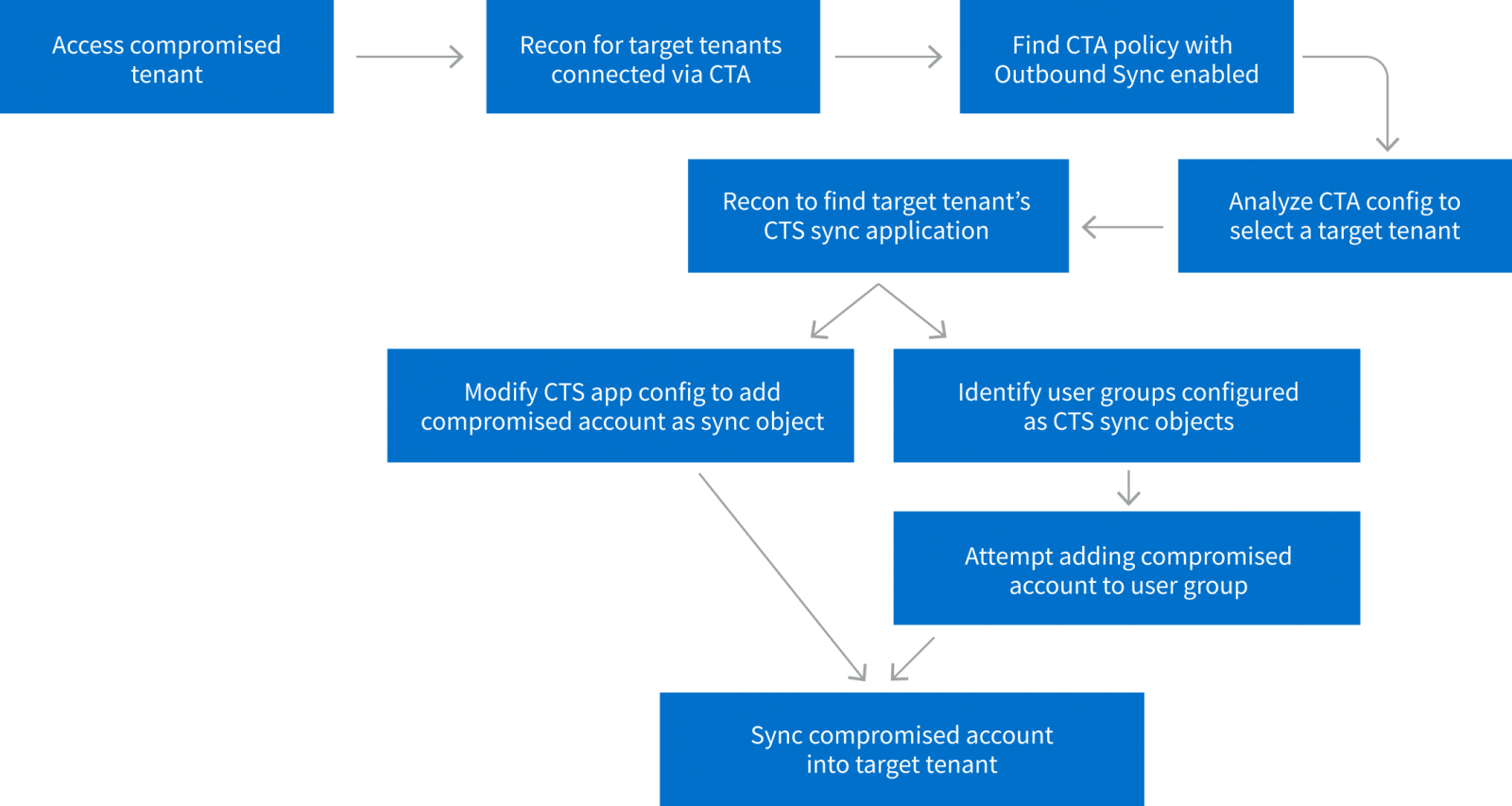 The lateral movement attack logic (Vectra)
The lateral movement attack logic (Vectra)
The second technique revolves around deploying a rogue CTS configuration to maintain persistent access to a target tenant. Again, this requires compromising a privileged account within the tenant. By enabling ‘Inbound Sync’ and ‘Automatic User Consent,’ the attacker can push new users from their external tenant to the target tenant at will, even if rogue accounts are removed, effectively creating a “backdoor.”
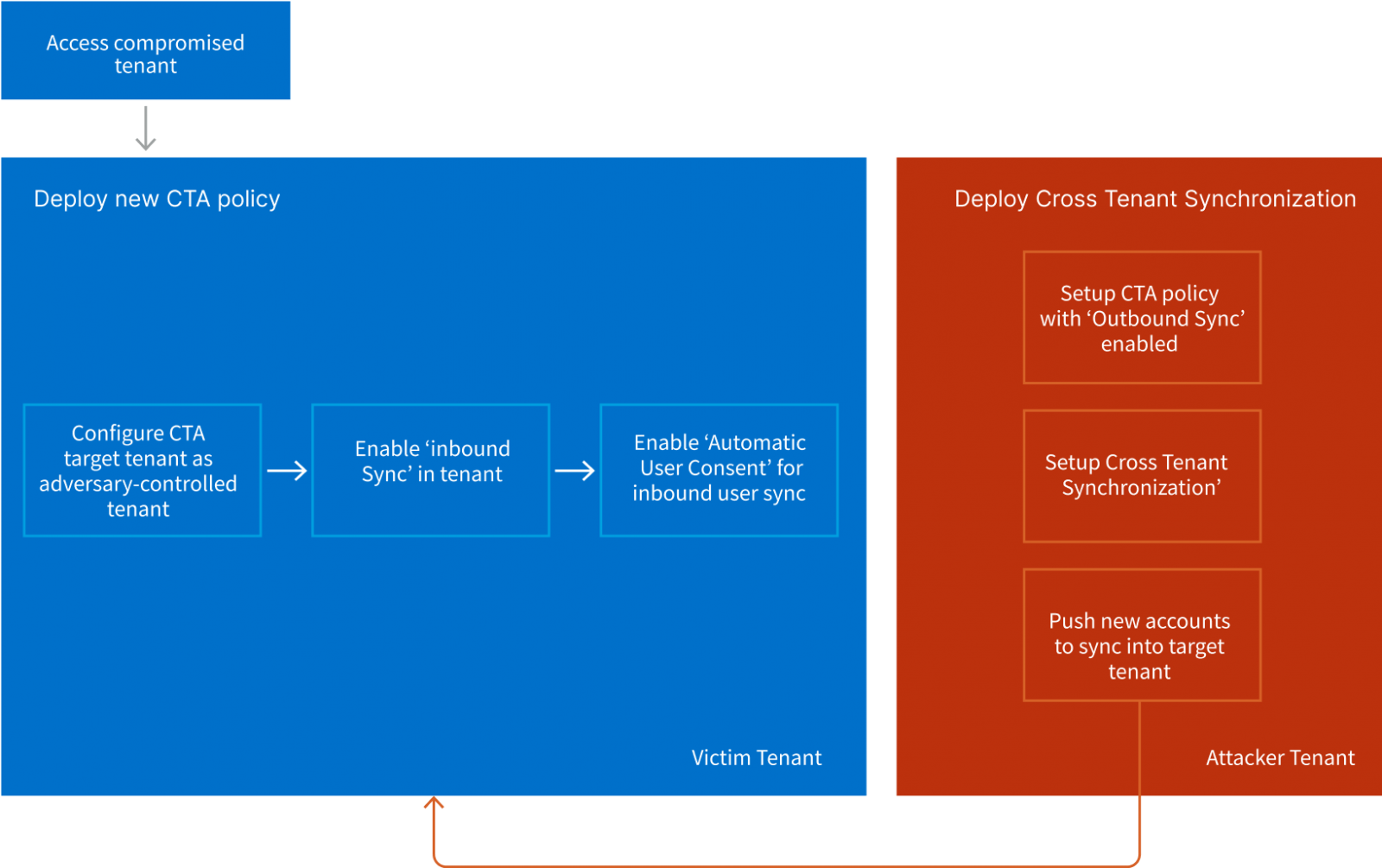 The backdoor attack logic (Vectra)
The backdoor attack logic (Vectra)
Trending: Offensive Security Tool: Nucleimonst3r
While no known attacks have exploited this feature yet, it’s essential for organizations to take preventive measures. Vectra recommends hardening the CTS configuration to prevent abuse, setting limits on user and group access, and monitoring all privileged users for suspicious activity.
For Microsoft tenants, understanding and addressing the potential risks associated with CTS is vital to maintaining a secure cloud environment and preventing unauthorized lateral movement.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












