BASICSTAR: Charming Kitten’s Latest Cyberweapon

A cyber threat group originating from Iran, known as Charming Kitten, has resurfaced with a fresh wave of attacks targeting experts in Middle East policy using a newly identified backdoor named BASICSTAR. This latest campaign involves the creation of a deceptive webinar portal to lure unsuspecting victims into their trap.
The Tactics of Charming Kitten
Charming Kitten, also recognized by aliases such as APT35, CharmingCypress, Mint Sandstorm, TA453, and Yellow Garuda, has a well-documented history of executing sophisticated social engineering schemes. Their targets often include think tanks, non-governmental organizations (NGOs), and journalists, indicating a strategic focus on entities involved in geopolitical affairs.
According to researchers at Volexity, Charming Kitten’s modus operandi includes engaging targets in prolonged email conversations before directing them to malicious content. This tactic serves to establish trust before launching the attack.
Recent findings from Microsoft highlight that high-profile individuals engaged in Middle Eastern affairs have been specifically targeted by Charming Kitten. The group employs malware such as MischiefTut and MediaPl (also known as EYEGLASS) to infiltrate systems and extract sensitive information.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Attributed to Iran’s Islamic Revolutionary Guard Corps (IRGC), Charming Kitten has deployed various backdoors, including PowerLess, BellaCiao, POWERSTAR (also known as GorjolEcho), and NokNok, demonstrating their persistent efforts to refine their tactics and evade detection.
The phishing campaigns observed between September and October 2023 involved Charming Kitten posing as the Rasanah International Institute for Iranian Studies (IIIS) to establish credibility with their targets. They utilize compromised email accounts and a technique called Multi-Persona Impersonation (MPI) to enhance the authenticity of their communications.
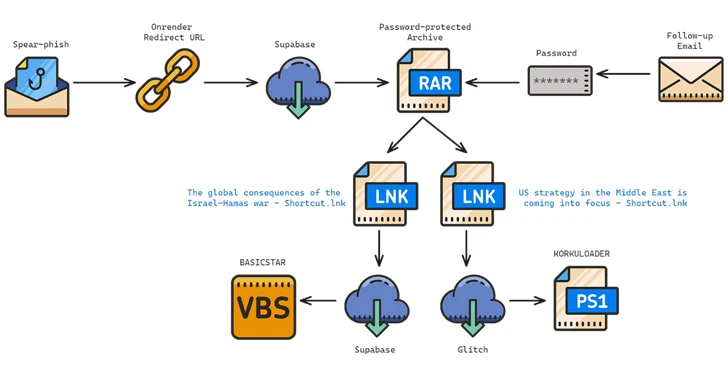
These attacks typically initiate with RAR archives containing LNK files, leading to the deployment of malware. One notable infection sequence involves BASICSTAR and KORKULOADER, a PowerShell downloader script, showcasing the group’s technical sophistication.
BASICSTAR, a Visual Basic Script (VBS) malware, possesses capabilities for gathering system information, executing remote commands, and displaying decoy PDF files. Moreover, Charming Kitten tailors its attacks based on the target’s operating system, utilizing different backdoors for Windows and macOS systems.
Trending: Major Cyber Attacks that shaped 2023
Trending: Offensive Security Tool: SmuggleFuzz


