Beware of Phishing: Namecheap Email Breach Impersonates DHL and MetaMask

Reading Time: 3 Minutes
Namecheap Email Account Breached in Phishing Campaign
Namecheap, a well-known domain registrar, suffered a security breach on Sunday night when their email account was compromised. The result was a flood of phishing emails sent from the platform, attempting to steal recipients’ personal information and cryptocurrency wallets.
The phishing campaigns started around 4:30 PM ET and originated from SendGrid, an email platform used historically by Namecheap to send renewal notices and marketing emails.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Namecheap CEO Confirms Compromised Email Account
Namecheap CEO Richard Kirkendall confirmed the breach after recipients began complaining on social media.
Kirkendall stated that they have disabled email through SendGrid while they investigate the issue and that the breach may be related to a December CloudSek report on the API keys of Mailgun, MailChimp, and SendGrid being exposed in mobile apps.
Beware of DHL and MetaMask Phishing Emails
The phishing emails in this campaign are impersonating either DHL or MetaMask. The DHL phishing email pretends to be a bill for a delivery fee required to complete the delivery of a package, while the MetaMask phishing email pretends to be a required KYC (Know Your Customer) verification.
Both emails contain links that lead to phishing pages attempting to steal the target’s information.
The MetaMask phishing email contains a link from Namecheap that redirects the user to a phishing page pretending to be MetaMask. This page prompts the user to enter their ‘Secret Recovery Phrase’ or ‘Private key,’ which the threat actors can use to import the wallet and steal all the funds and assets.
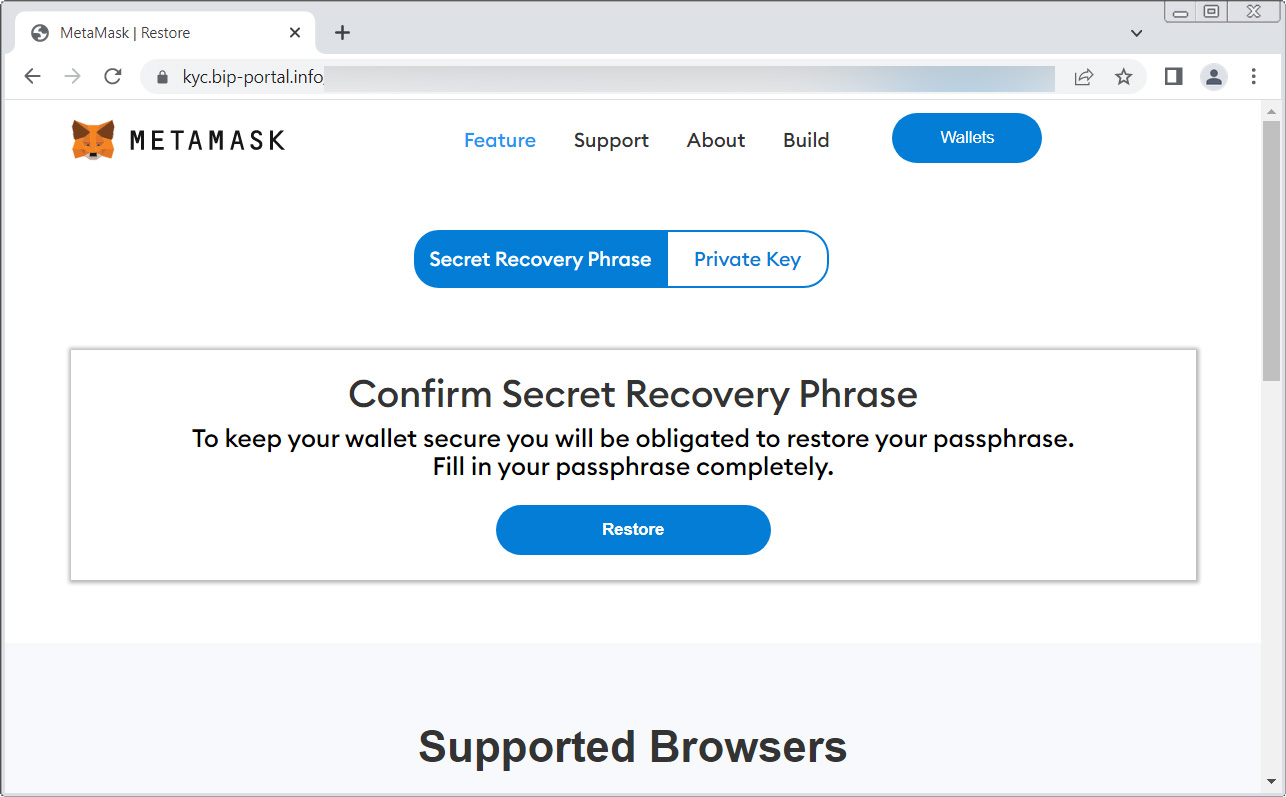 MetaMask phishing page
MetaMask phishing page
Source: BleepingComputer
If you received either a DHL or MetaMask phishing email from Namecheap, it is recommended to immediately delete it and not click on any links.
Beware of phishing emails coming out of @Namecheap’s @SendGrid account. DHL, MetaMask, digitally signed with DKIM. Looks like low level hackers were able to get into their systems. PII looks to be exposed. pic.twitter.com/IuLE8mo2w6
— Kathy Zant (@kathyzant) February 12, 2023
Trending: Major Cyber Attacks of 2022
Trending: Recon Tool: SauronEye
Namecheap Blames Upstream System, Services Restored
Namecheap published a statement Sunday night claiming that their systems were not breached and that it was an issue at an upstream system used for email.
After the phishing incident, Namecheap stopped all emails and began investigating the attack with their upstream provider. Services were restored later that night at 7:08 PM EST. However, the name of the upstream system was not stated, and Twilio SendGrid denied that the incident was the result of a hack or compromise of their systems.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












