Bizarro Banking Trojan Sports Sophisticated Backdoor

Reading Time: 1 Minute
A never-before-documented Brazilian banking trojan, dubbed Bizarro, is targeting customers of 70 banks scattered throughout Europe and South America, researchers said.
According to an analysis from Kaspersky released Monday, Bizarro is a mobile malware, aimed at capturing online-banking credentials and hijacking Bitcoin wallets from Android users. It spreads via Microsoft Installer packages, which are either downloaded directly by victims from links in spam emails or installed via a trojanized app, according to the analysis.
Once installed, it kills all running browser processes to terminate any existing sessions with online banking websites — so, when a user initiates a mobile banking session, they have to sign back in, allowing the malware to harvest the details. To maximize its success, Bizarro disables autocomplete in the browser, and even surfaces fake popups to snatch two-factor authentication codes, researchers added.
Bizarro also has a screen-capturing module.
“It loads the magnification.dll library and gets the address of the deprecated MagSetImageScalingCallback API function,” explained Kaspersky researchers. “With its help, the trojan can capture the screen of a user and also constantly monitor the system clipboard, looking for a Bitcoin wallet address. If it finds one, it is replaced with a wallet belonging to the malware developers.”
And finally, Bizarro also has a main backdoor module that is capable of carrying out more than 100 commands, according to the analysis.
See Also: ‘Scheme Flooding’ Allows Websites to Track Users Across Browsers
A Fully Functional Backdoor
“The core component of the backdoor doesn’t start until Bizarro detects a connection to one of the hardcoded online banking systems,” researchers explained. “The malware does this by enumerating all the windows, collecting their names. Whitespace characters, letters with accents (such as ñ or á) and non-letter symbols such as dashes are removed from the window name strings. If a window name matches one of the hardcoded strings, the backdoor continues starting up.”
The commands fall into a few main camps:
- Commands that allow the command-and-control (C2) operators to get data about the victim and manage the connection status; for instance, one asks for Bizarro’s version, OS name, computer name, Bizarro’s unique identifier, installed antivirus software and the codename used for the bank that has been accessed.
- Commands that allow attackers to search for and steal the files located on the victim’s hard drive, and those that allow adversaries to install files on the victim device.
- Commands that allow attackers to control the user’s mouse and keyboard.
- Commands that allow the attackers to control the backdoor operation, shut down, restart or destroy the operating system, and limit the functionality of Windows.
- Commands that log keystrokes.
- Commands that display various messages that trick users into giving attackers access to bank accounts, including fake popup windows (i.e., messages like “the data entered is incorrect, please try again”; error messages asking the user to enter a confirmation code; and those that tell the user that their computer needs to be restarted in order to finish a security-related operation).
- Commands that enable Bizarro to mimic online banking systems. According to Kaspersky, “To display such messages, Bizarro needs to download a JPEG image that contains the bank logo and instructions the victim needs to follow. These images are stored in the user profile directory in an encrypted form. Before an image is used in a message, it is decrypted with a multi-byte XOR algorithm. As the messages are downloaded from the C2 server, they can be found only on the victims’ machines.”
- Commands that enable custom messages.
See Also: Offensive Security Tool: EyeWitness
“The custom messages that Bizarro may show are messages that freeze the victim’s machine, thus allowing the attackers to gain some time,” according to the analysis. “When a command to display a message like this is received, the taskbar is hidden, the screen is greyed out and the message itself is displayed. While the message is shown, the user is unable to close it or open Task Manager. The message itself tells the user either that the system is compromised and thus needs to be updated or that security and browser performance components are being installed. This type of message also contains a progress bar that changes over time.”
Joining the Tétrade, Going Global
Bizarro is active in Argentina, Chile, France, Germany, Italy, Portugal and Spain, researchers said. This global spread is typical of a group of banking malware strains originating in Brazil, consisting of Grandoreiro, Guildma, Javali and Melcoz.
Collectively known as “the Tétrade” (translated as “a group of four”) these families employ a range of innovative and sophisticated techniques on the technical side as well. Bizarro is the latest to join the club (which, incidentally, makes the collective group name a bit of a misnomer).
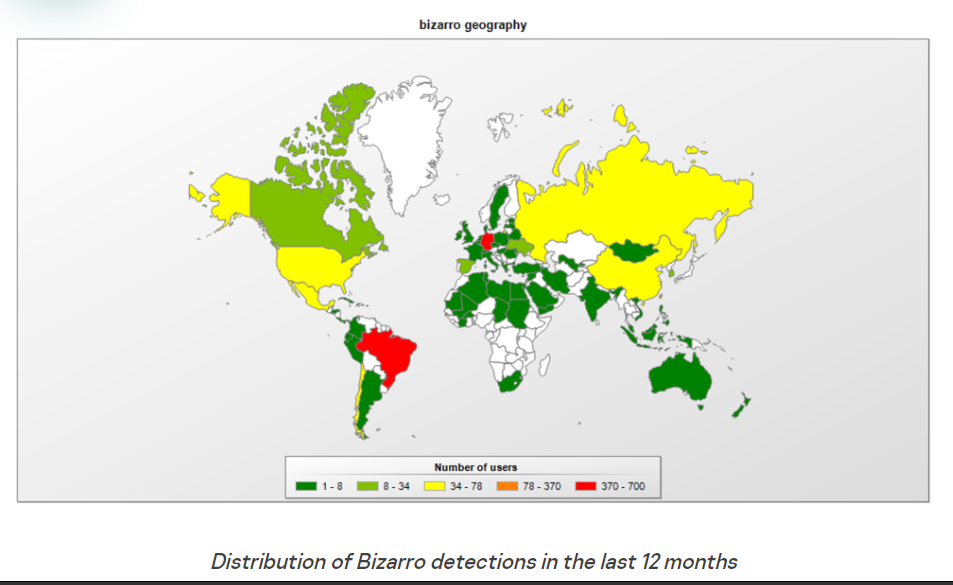
Source: Kaspersky
Researchers said that Bizarro is supported by a fairly extensive operation, which includes using affiliates and recruiting money mules to perform a variety of functions. The various duties include carrying out initial attacks to gain a foothold on victim devices; helping with cashouts to launder ill-gotten funds; and even translation help.
See Also: Hacking Stories: Xbox Underground
“Cybercriminals are constantly looking for new ways to spread malware that steals credentials for e-payment and online banking systems,” said Fabio Assolini, security expert at Kaspersky, in a statement. “Today, we witness a game-changing trend in banking malware distribution – regional actors actively attack users, not only in their region but also around the globe. Implementing new techniques, Brazilian malware families started distributing to other continents, and Bizarro, which targets users from Europe, is the clearest example of this. It should serve as a sign for greater emphasis on the analysis of regional criminals and local threat intelligence, as soon enough it could become a problem of global concern.”
Source: threatpost.com



