BlackCat Ransomware Evades Security Software with Signed Malicious Windows Kernel Drivers

The ALPHV ransomware group, also known as BlackCat, has recently been observed employing signed malicious Windows kernel drivers to evade detection by security software during their attacks.
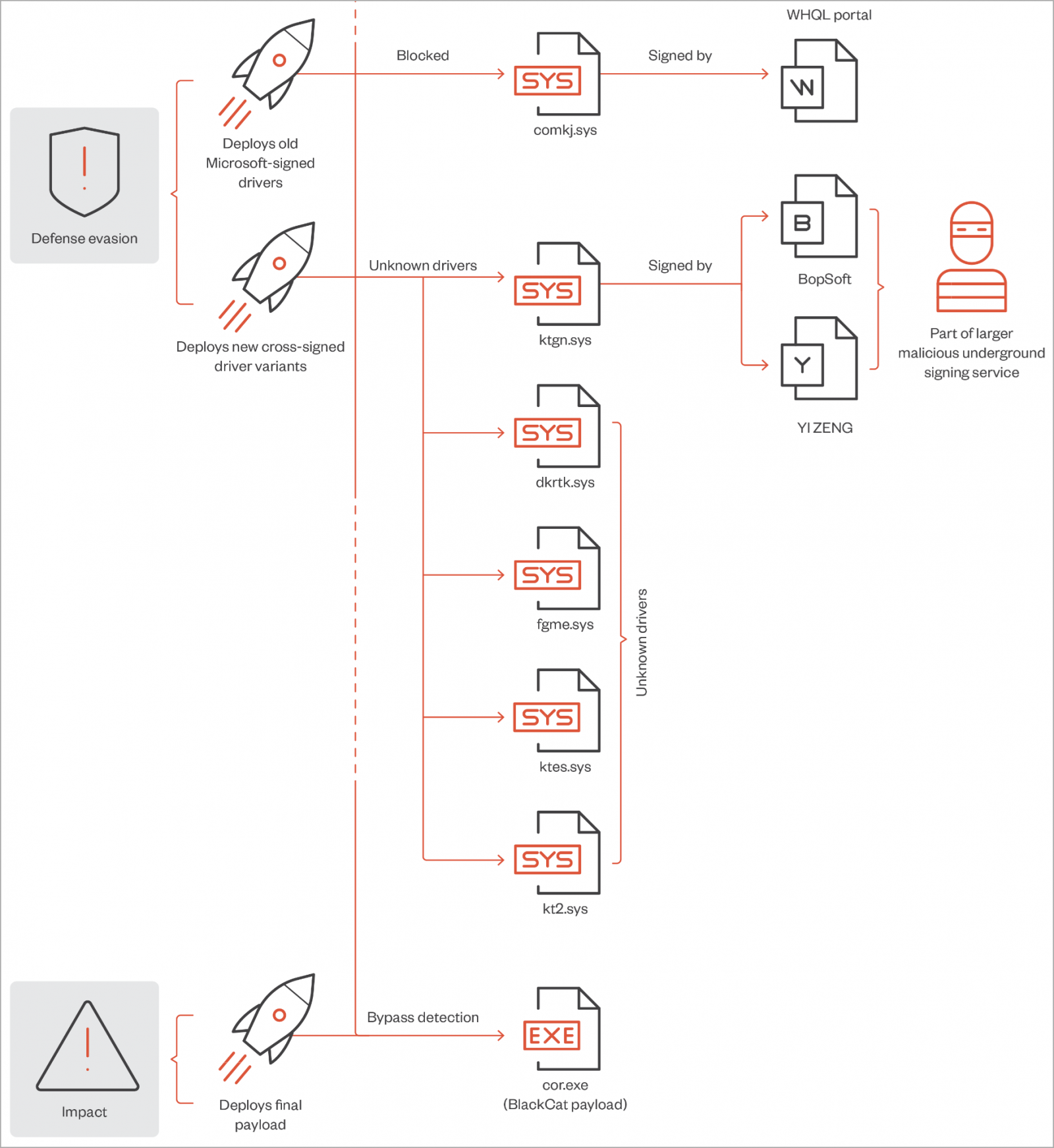
This particular driver, discovered by Trend Micro, is an enhanced version of the malware known as ‘POORTRY,’ which was previously identified in ransomware attacks late last year by Microsoft, Mandiant, Sophos, and SentinelOne.
POORTRY is a Windows kernel driver that has been signed using stolen keys from legitimate accounts within Microsoft’s Windows Hardware Developer Program.
The UNC3944 hacking group, also known as 0ktapus and Scattered Spider, utilized this malicious driver to terminate security software running on Windows devices, enabling them to evade detection.
While security software is typically protected from termination or tampering, Windows kernel drivers operate with the highest privileges in the operating system, granting them the capability to terminate almost any process.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Evading Detection with Upgraded Kernel Driver
Trend Micro reports that the ransomware actors initially attempted to use the Microsoft-signed POORTRY driver. However, its detection rates increased following public exposure and the subsequent revocation of the code-signing keys.
As a result, the hackers deployed an updated version of the POORTRY kernel driver, this time signed using a stolen or leaked cross-signing certificate.
The new driver utilized by the BlackCat ransomware operation allows them to elevate their privileges on compromised machines and terminate processes associated with security agents.
Furthermore, it establishes a potential connection between the ransomware gang and the UNC3944/Scattered Spider hacking groups.
The malicious Windows kernel driver, named ‘ktgn.sys,’ was observed by Trend Micro during the BlackCat attacks in February 2023. It is dropped onto the victim’s filesystem in the %Temp% folder and loaded by a user mode program called ‘tjr.exe.’
Although the digital signature of ktgn.sys has been revoked, the driver can still load on 64-bit Windows systems with enforced signing policies.
The malicious kernel driver exposes an IOCTL interface, allowing the user mode client, tjr.exe, to issue commands that the driver executes with Windows kernel privileges.
According to the Trend Micro report, the driver primarily utilizes the ‘Kill Process’ IOCTL code, which terminates security agent processes installed on the system.
 Malicious drivers used in BlackCat attacks (Trend Micro)
Malicious drivers used in BlackCat attacks (Trend Micro)
Trend Micro’s analysts have identified several commands that can be issued to the driver, including activating and deactivating the driver, killing user-mode processes, deleting specific file paths, copying files, registering and unregistering process/thread notification callbacks, and rebooting the system.
Trending: Recon Tool: Dome
Mitigating Risks of Malicious Kernel Drivers
While some commands are functional, the ones related to process/thread notification callbacks are currently not working, indicating that the driver may still be under development or in a testing phase.
To mitigate the risks associated with these malicious drivers, system administrators are advised to utilize the indicators of compromise provided by Trend Micro and add the identified drivers to the Windows driver blocklist. Additionally, enabling ‘Driver Signature Enforcement’ will block the installation of any drivers without a valid digital signature, further enhancing security measures.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












