BlackCat Ransomware Uses ‘Munchkin’: A Stealthy New Tool to Target Network Devices

BlackCat/ALPHV Ransomware Operation Deploys ‘Munchkin’ to Stealthily Encrypt Network Devices
The infamous BlackCat/ALPHV ransomware operation has introduced a potent new tool known as ‘Munchkin.’ This tool utilizes virtual machines to discreetly deploy encryptors on network devices, enhancing the ransomware-as-a-service (RaaS) offering and making it a more attractive prospect for cybercriminal affiliates.
Munchkin operates as a customized Alpine OS Linux distribution bundled as an ISO file. When a device is compromised, threat actors install VirtualBox and create a new virtual machine using the Munchkin ISO. This virtual machine comes equipped with a suite of scripts and utilities that offer several capabilities, including password extraction, lateral movement across the network, payload creation for the BlackCat ‘Sphynx’ encryptor, and program execution on network computers.
Upon booting, Munchkin modifies the root password, known exclusively to the attackers, and utilizes the ‘tmux’ utility to initiate a Rust-based malware binary called ‘controller.’ The controller loads scripts crucial to the attack, guided by the bundled configuration file.
These scripts are listed below:
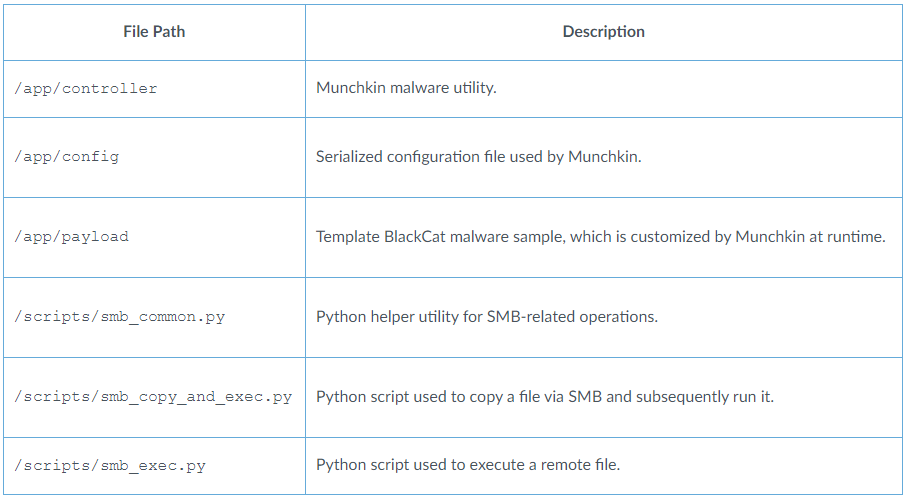 Structure of the image’s filesystem
Structure of the image’s filesystem
Source: Unit 42
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
This configuration file contains access tokens, victim credentials, authentication secrets, as well as directives for configuring tasks, blocklists for folders and files, and a list of hosts to target for encryption.
Using this configuration, custom BlackCat encryptor executables are generated in the /payloads/ directory and pushed to remote devices for file encryption or the encryption of SMB and CIFS network shares.
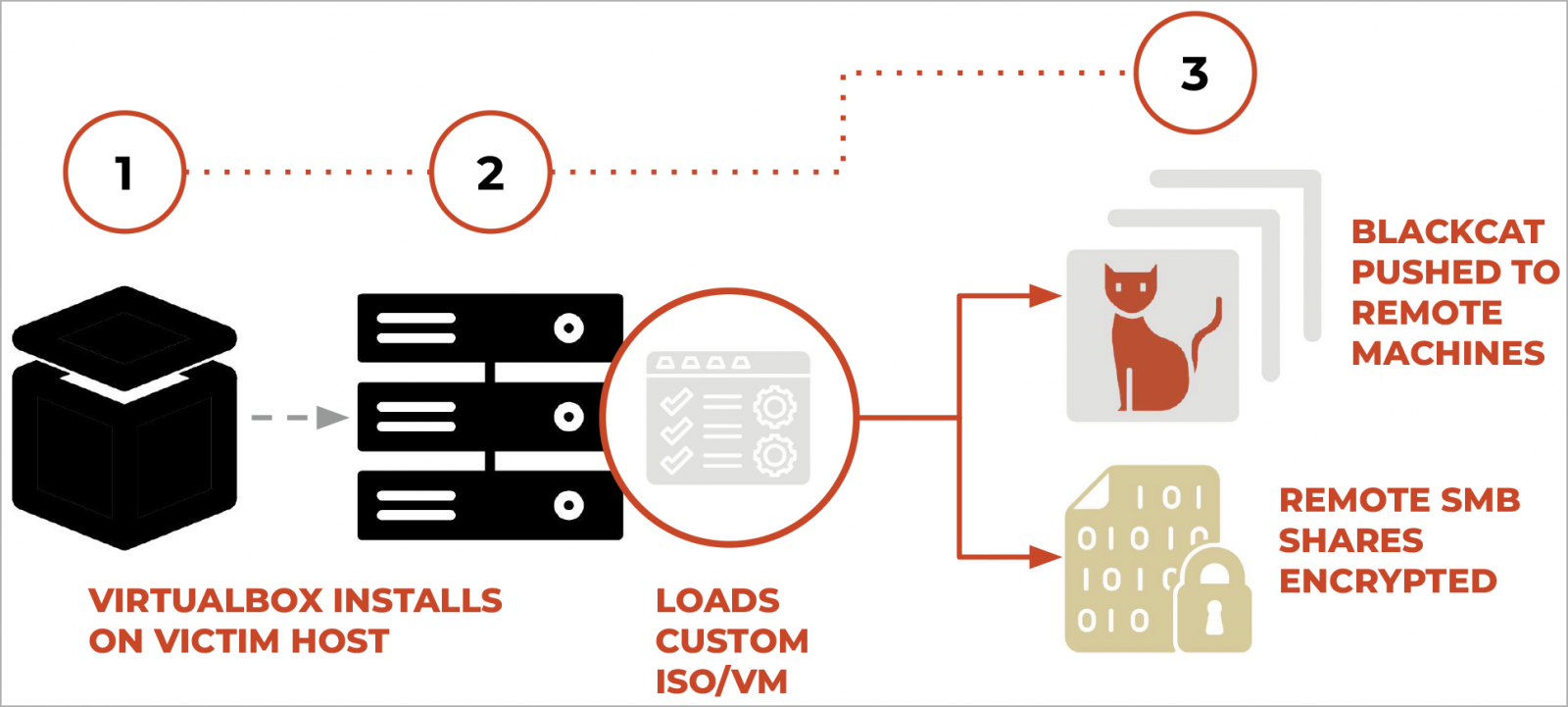 Munchkin attack diagram
Munchkin attack diagram
Source: Unit 42
Remarkably, the malware’s code includes a message from BlackCat’s authors to their partners, warning against leaving the ISO on target systems due to the unencrypted configuration. These affiliates provide Tor negotiation site access tokens at run-time, ensuring the security of the negotiation chat between the ransomware gang and its victims. The threat actors urge affiliates to delete the Munchkin virtual machines and ISOs to prevent these access tokens from leaking.
The developers have also provided comprehensive instructions and tips for utilizing the ‘Controller’ tool to oversee the attack’s advancement and initiate tasks.
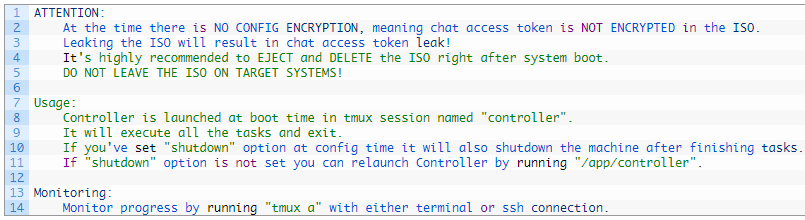 Note contained in the malware
Note contained in the malware
Source: Unit 42
Munchkin streamlines various tasks for BlackCat ransomware affiliates, including bypassing security solutions. Virtual machines offer an additional layer of isolation from the host operating system, making detection and analysis more challenging for security software. The choice of the Alpine OS ensures a small digital footprint, while the tool’s automation reduces the need for manual intervention, minimizing noise from command feeds.
Trending: Recon Tool: fetchmeurls
Moreover, Munchkin’s modularity, featuring a range of Python scripts, configurable parameters, and the ability to swap payloads as needed, enhances its adaptability to specific targets or campaigns.
BlackCat, emerging in late 2021 as a sophisticated Rust-based ransomware operation, has continued to evolve, regularly introducing advanced features, including highly configurable intermittent encryption, data leak APIs, Impacket and Remcom embedding, encryptors with support for custom credentials, signed kernel drivers, and data exfiltration tool upgrades.
Among the notable victims targeted by BlackCat in 2023 are the Florida Circuit Court, MGM Resorts, Motel One, Seiko, Estee Lauder, HWL Ebsworth, Western Digital, and Constellation Software.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












