BLUFFS- New Bluetooth Attacks Open Path to Device Impersonation

Eurecom researchers have uncovered a series of six new Bluetooth attacks collectively named ‘BLUFFS.’ These exploits capitalize on two previously unknown flaws in the Bluetooth standard, affecting the derivation of session keys and compromising forward and future secrecy in Bluetooth sessions.
Daniele Antonioli, the mind behind these attacks, emphasizes that BLUFFS targets architectural flaws rather than specific hardware or software configurations. This means that the vulnerabilities strike at the core of Bluetooth technology, impacting versions 4.2 through 5.4 of the Bluetooth Core Specification.

SALE: Benefit from discounted prices on our Courses from 24/11 to 06/12.
Offensive Security, Bug Bounty Courses
BLUFFS in Action
BLUFFS works by exploiting four flaws in the session key derivation process, leading to the generation of a weak and predictable session key. This allows attackers within Bluetooth range to impersonate devices, negotiate weak session keys, and compromise the confidentiality of past and future communications between devices.
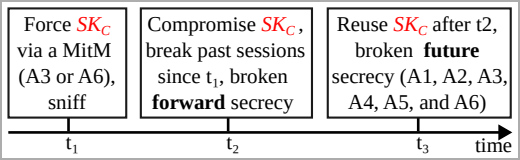 Attack steps (dl.acm.org)
Attack steps (dl.acm.org)
The attacks assume proximity to the targets exchanging data and involve impersonation to force weak session key derivation.
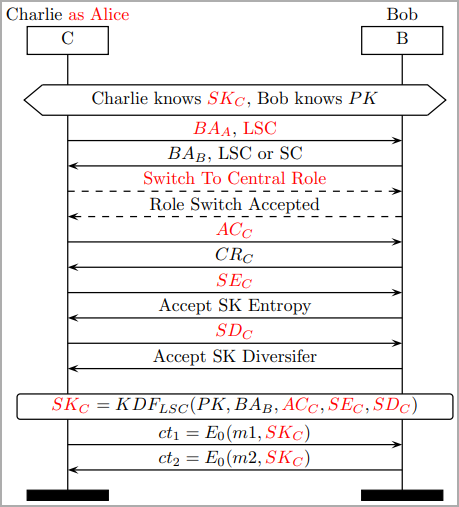 Negotiating a session key while spoofing a legitimate party
Negotiating a session key while spoofing a legitimate party
(dl.acm.org)
The researchers have shared a toolkit on GitHub demonstrating the effectiveness of BLUFFS, including Python scripts, ARM patches, parsers, and captured PCAP samples.
Impact and Mitigations
The impact of BLUFFS extends across billions of devices, including smartphones, laptops, and other Bluetooth-enabled devices. The vulnerabilities affect Bluetooth versions from 4.2 to the latest 5.4.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com



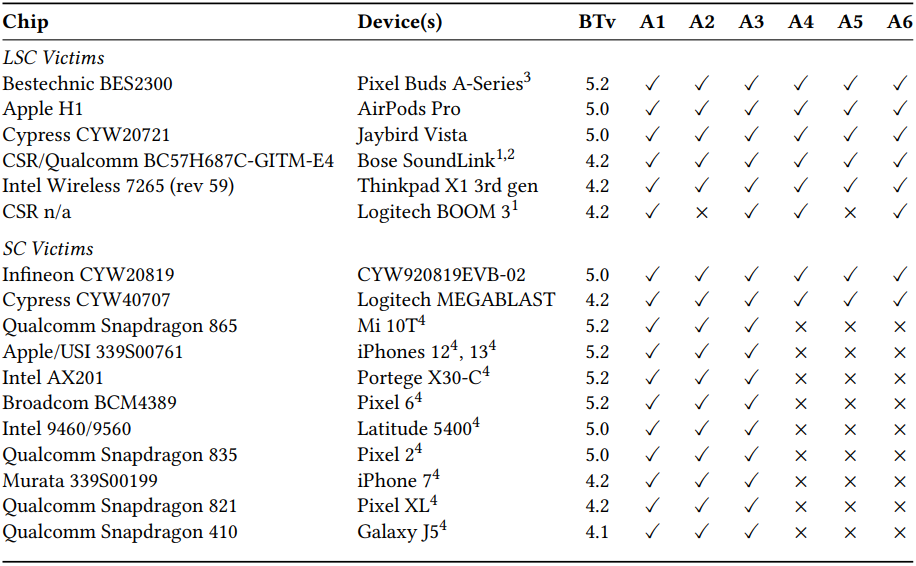 BLUFFS tested against a gamut of devices (dl.acm.org)
BLUFFS tested against a gamut of devices (dl.acm.org)









