Brute-Force Attack on Linux SSH Servers Unleashes Tsunami DDoS Bot

An unidentified threat actor is carrying out brute-force attacks on Linux SSH servers, aiming to install various types of malware, including the Tsunami DDoS bot, ShellBot, log cleaners, privilege escalation tools, and an XMRig coin miner.
SSH (Secure Shell) is a secure network communication protocol used for remote management of Linux devices, allowing administrators to execute commands, modify configurations, update software, and troubleshoot issues.
However, poorly secured SSH servers are susceptible to brute-force attacks, where threat actors attempt multiple username-password combinations until they find a match.
Tsunami bot, SSH servers
A recent campaign discovered by AhnLab Security Emergency Response Center (ASEC) highlights this threat. The attackers scan the internet for publicly-exposed Linux SSH servers and use brute-force techniques to gain unauthorized access.
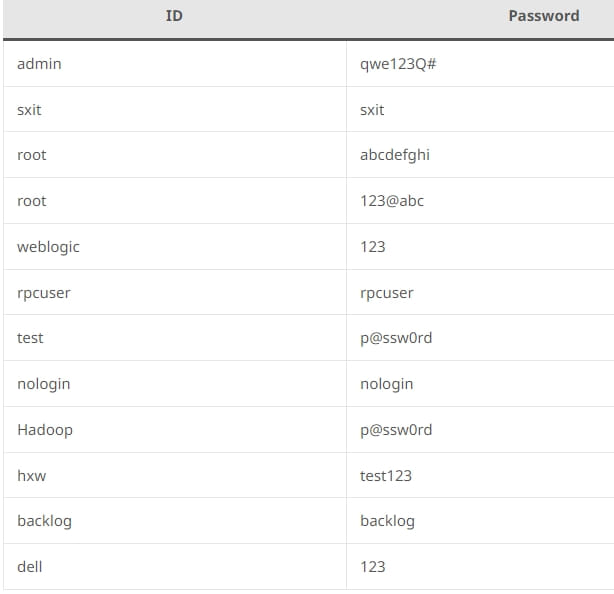 Credentials tried out in the observed attack (ASEC)
Credentials tried out in the observed attack (ASEC)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Once inside as an admin user, they execute a Bash script that fetches and runs a collection of malware. To maintain access, the intruders generate a new pair of SSH keys for the compromised server, ensuring persistence even if the user password is changed.
![]() Command executed on freshly breached servers (ASEC)
Command executed on freshly breached servers (ASEC)
The malware downloaded onto compromised hosts includes DDoS botnets, log cleaners, cryptocurrency miners, and privilege escalation tools.
ShellBot, a Perl-based DDoS bot that utilizes the IRC protocol for communication, supports various attack methods such as port scanning, UDP, TCP, and HTTP flood attacks. It can also establish a reverse shell.
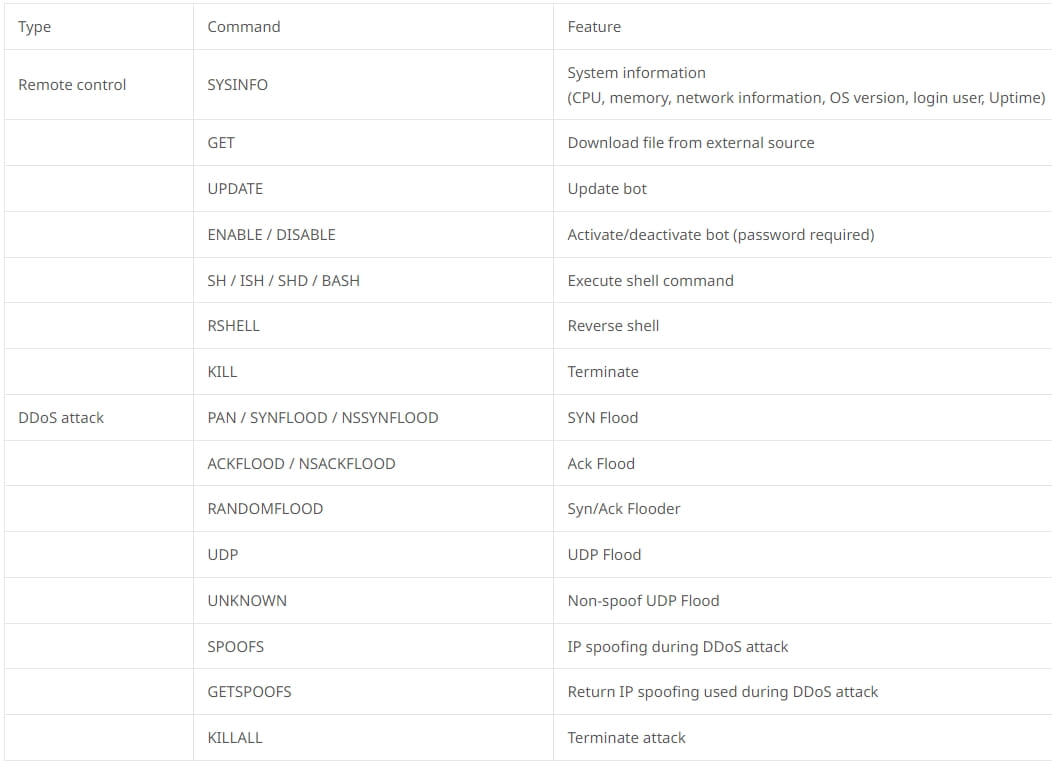 Complete list of commands supported by Tsunami (ASEC)
Complete list of commands supported by Tsunami (ASEC)
Another DDoS botnet observed in these attacks is Tsunami, which also employs the IRC protocol for communication. The specific variant seen is called “Ziggy,” a Kaiten variant. Tsunami hides itself using system process names and persists between reboots by writing itself to “/etc/rc.local.”
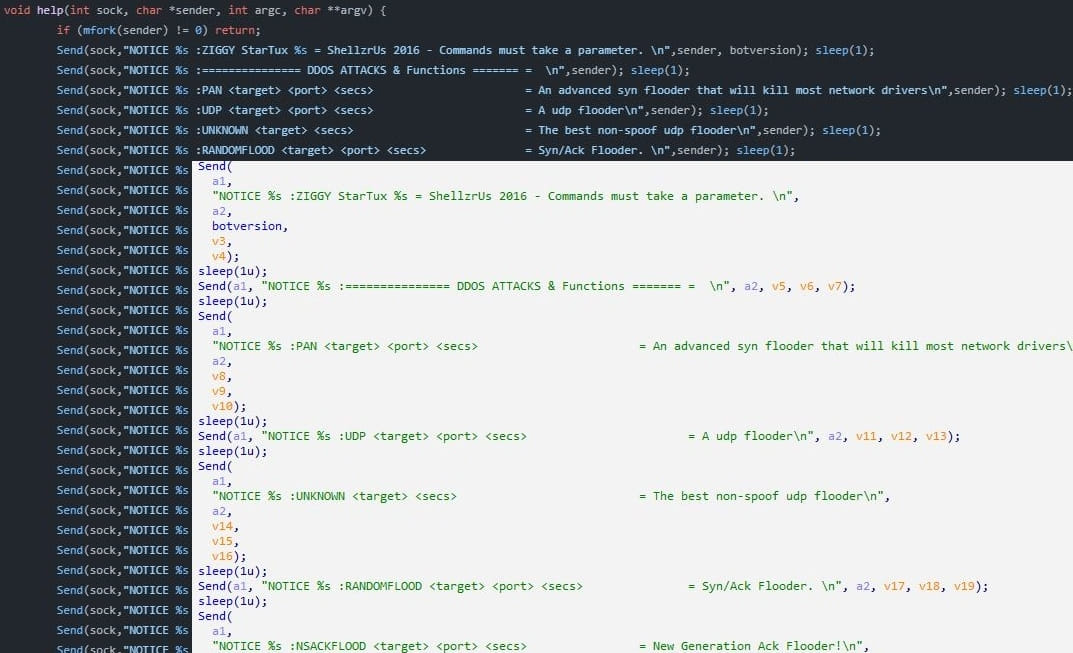 Tsunami botnet’s source code (ASEC)
Tsunami botnet’s source code (ASEC)
In addition, the attackers utilize log cleaners, including MIG Logcleaner v2.0 and Shadow Log Cleaner, to erase evidence of the intrusion on compromised computers, making it more difficult for victims to detect the infection.
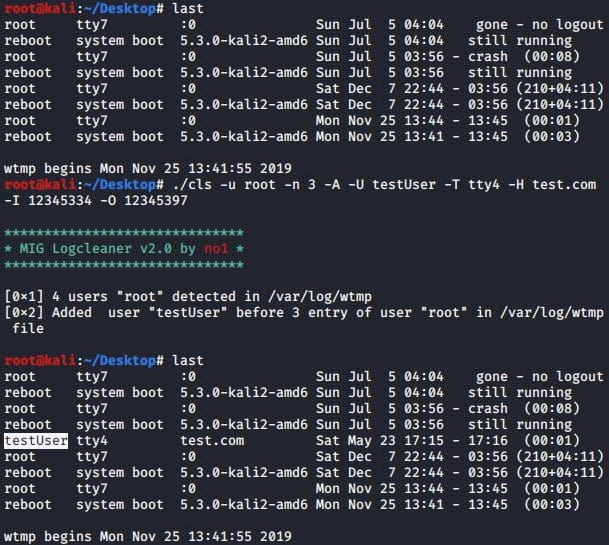 Adding a fake login event on the server (ASEC)
Adding a fake login event on the server (ASEC)
Trending: Offensive Security Tool: PhoneSploit Pro
Privilege escalation malware in the form of an ELF file is used to elevate the attacker’s privileges to root user status.
Lastly, the threat actors deploy an XMRig coin miner to hijack the computational resources of the compromised server for mining Monero on a specified pool.
To defend against these attacks, Linux users should employ strong account passwords or, for enhanced security, require SSH keys for authentication. Disabling root login via SSH, restricting access to the server by IP address, and changing the default SSH port to a non-standard value can also help thwart automated bots and infection scripts.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












