BrutePrint Attack: Researchers Unveil New Technique to Bypass Smartphone Fingerprint Authentication

Researchers from Tencent Labs and Zhejiang University have recently introduced a novel attack named ‘BrutePrint,’ designed to exploit fingerprint authentication on modern smartphones. This attack leverages brute-force techniques to bypass user authentication and gain control of the device.
Brute-force attacks involve multiple trial-and-error attempts to crack passwords, codes, or keys to gain unauthorized access to accounts, systems, or networks. In this case, the Chinese researchers discovered two zero-day vulnerabilities called Cancel-After-Match-Fail (CAMF) and Match-After-Lock (MAL), which allowed them to surpass existing security measures like attempt limits and liveness detection.
The researchers discovered that biometric data stored on fingerprint sensors’ Serial Peripheral Interface (SPI) were inadequately protected, making them susceptible to man-in-the-middle (MITM) attacks, enabling attackers to intercept and hijack fingerprint images.
Ten popular smartphone models were tested for BrutePrint and SPI MITM attacks, demonstrating unlimited attempts on Android and HarmonyOS (Huawei) devices, and additional attempts on iOS devices.
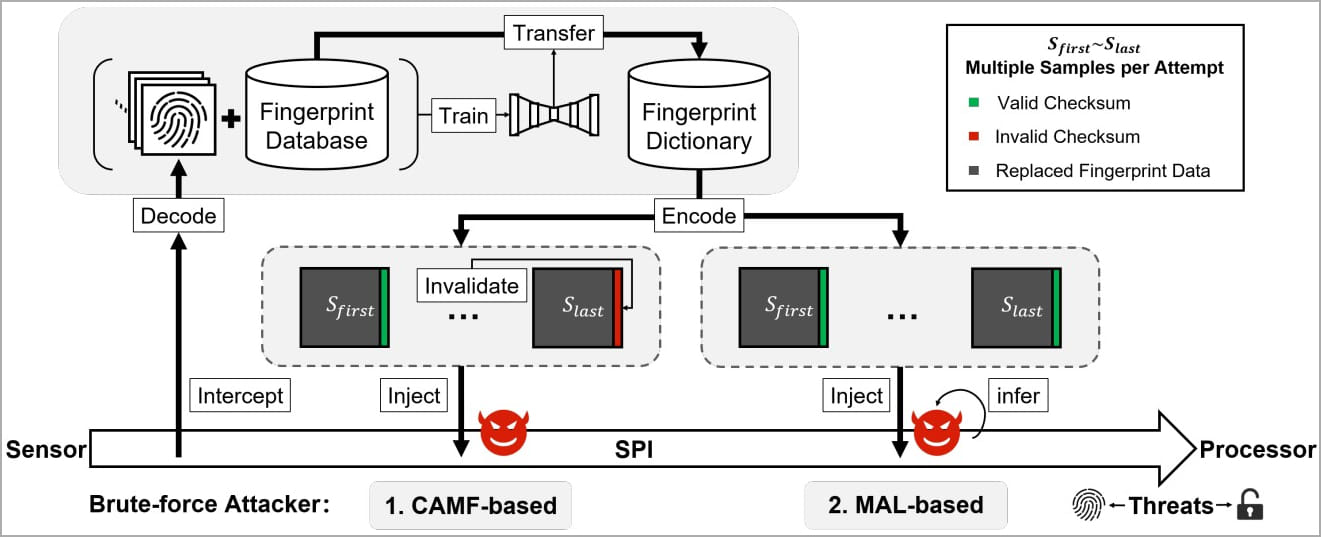 BrutePrint attack diagram (arxiv.org)
BrutePrint attack diagram (arxiv.org)
Offensive Security, Bug Bounty Courses
How BrutePrint attack works
To execute a BrutePrint attack, the attacker needs physical access to the target device, access to a fingerprint database, and equipment costing approximately $15. By manipulating the False Acceptance Rate (FAR), attackers can increase the acceptance threshold, facilitating easier matches.
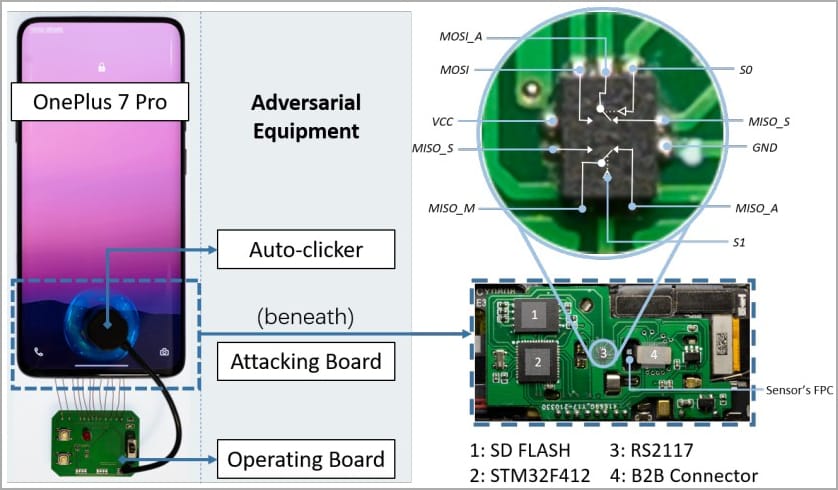 Equipment required for launching BrutePrint (arxiv.org)
Equipment required for launching BrutePrint (arxiv.org)
The BrutePrint attack interferes between the fingerprint sensor and the Trusted Execution Environment (TEE) by exploiting the CAMF vulnerability, manipulating fingerprint authentication’s multi-sampling and error-canceling mechanisms. This flaw injects a checksum error to prematurely halt the authentication process, allowing attackers to make unlimited attempts without triggering failed attempt notifications.
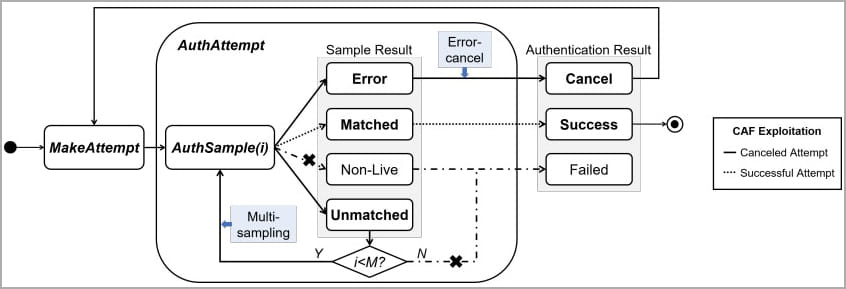 CAMF vulnerability attack logic (arxiv.org)
CAMF vulnerability attack logic (arxiv.org)
The MAL vulnerability enables attackers to deduce authentication results for fingerprint images, even when the device is in “lockout mode.” This mode is activated after a series of failed unlock attempts, but MAL bypasses this restriction.
Trending: Recon Tool: Dome
A “neural style transfer” system is utilized in the BrutePrint attack to transform fingerprint images in the database to resemble the target device’s sensor scans, increasing the chances of successful matches.
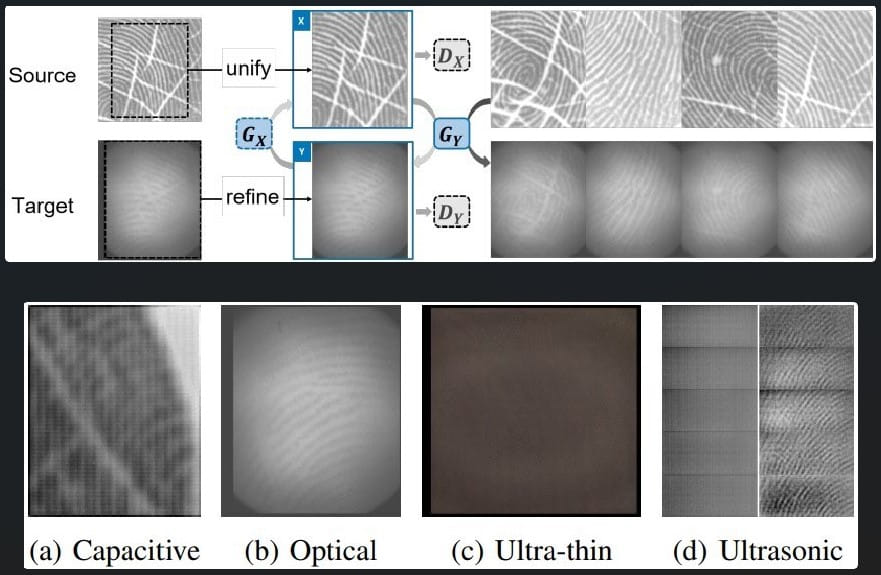 Refining the images (top) based on the sensor type (bottom) (arxiv.org)
Refining the images (top) based on the sensor type (bottom) (arxiv.org)
The researchers conducted experiments on ten Android and iOS devices, revealing vulnerabilities in all devices to varying degrees. While Android devices were susceptible to unlimited fingerprint tryouts, iOS devices demonstrated stronger authentication security, effectively preventing brute-forcing attacks.
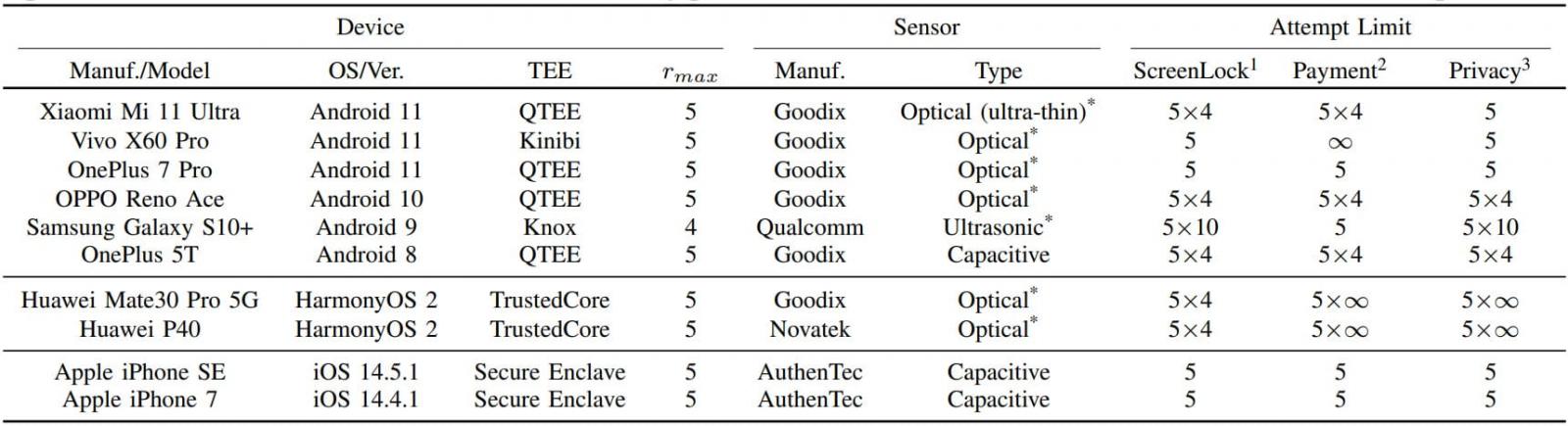 Details of tested devices (arxiv.org)
Details of tested devices (arxiv.org)
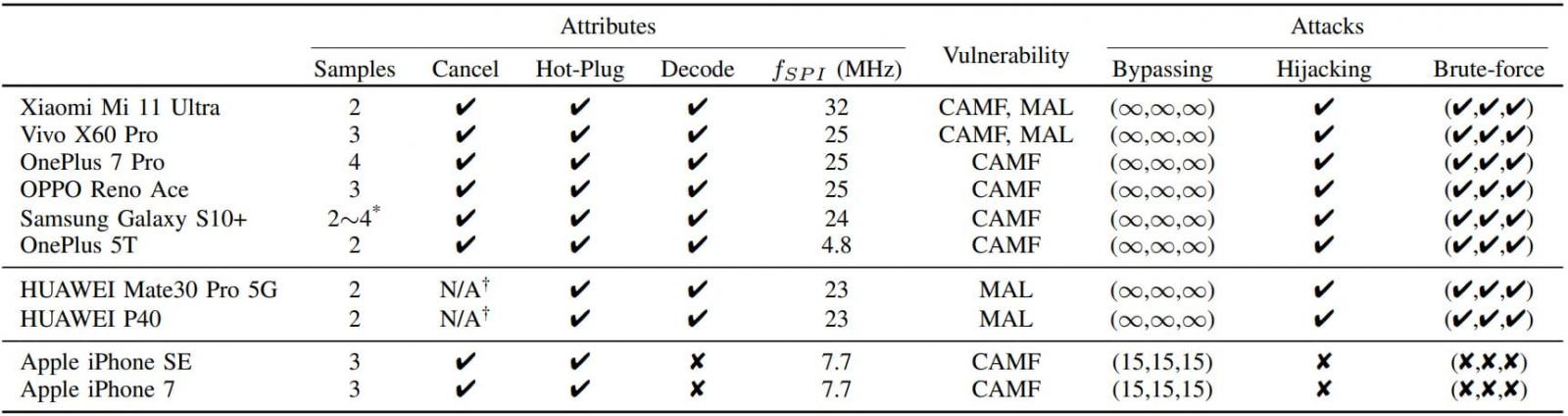 Test results table (arxiv.org)
Test results table (arxiv.org)
While the BrutePrint attack may seem limited due to requiring extended access to the target device, its implications are significant. For criminals, it provides a means to unlock stolen devices and access sensitive data. However, its use by law enforcement raises ethical questions and privacy concerns, potentially violating rights in certain jurisdictions and compromising the safety of individuals in oppressive regimes.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












