Camaro Dragon – Chinese State-Sponsored Hackers Target European Organizations via Infected TP-Link Routers

Chinese state-sponsored hacking group “Camaro Dragon” has been discovered infecting residential TP-Link routers with a custom malware named “Horse Shell.” The targeted victims of these attacks are European foreign affairs organizations. This latest cyber campaign indicates a concerning shift in focus towards the exploitation of TP-Link routers by cybercriminals.
The attackers employ a custom and malicious firmware designed exclusively for TP-Link routers. By using this firmware, they can launch attacks that appear to originate from residential networks, rather than targeting sensitive networks directly. Check Point, the cybersecurity firm that uncovered the campaign, emphasizes that homeowners whose routers are infected are not necessarily specific targets but unwitting contributors to the attackers’ objectives.
TP-Link firmware implant
The deployed Horse Shell malware provides the threat actors with complete control over the compromised device. They can execute shell commands, transfer files, and use the router as a SOCKS proxy to facilitate communication between devices. Check Point Research first discovered the Horse Shell TP-Link firmware implant in January 2023. Interestingly, the activity of the “Camaro Dragon” group overlaps with another Chinese hacking group called “Mustang Panda,” as revealed in reports by Avast and ESET.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Check Point has attributed the attacks to “Camaro Dragon” based on various indicators. These include the IP addresses of the attackers’ servers, HTTP headers found on Chinese websites, coding errors suggesting a non-native English speaker, and functional similarities between the Horse Shell trojan and the APT31 “Pakdoor” router implant.
The method by which the attackers infect TP-Link routers with the malicious firmware remains undetermined. It is speculated that vulnerabilities are exploited or administrator credentials are brute-forced to gain admin access to the router’s management interface. Once access is obtained, the attackers remotely update the device with the custom firmware image.
 Standard firmware (left), and trojanized (right) preventing firmware updates (Check Point)
Standard firmware (left), and trojanized (right) preventing firmware updates (Check Point)
The Horse Shell backdoor
Check Point’s investigation discovered two samples of trojanized firmware images for TP-Link routers. Extensive modifications and file additions were made to these firmware images. While the kernel and uBoot sections remained the same as the legitimate version, the trojanized firmware contained a custom SquashFS filesystem housing additional malicious file components that comprise the Horse Shell backdoor implant.
When the Horse Shell backdoor implant is activated, it instructs the operating system not to terminate its process when certain commands are issued. It then operates as a daemon in the background. The backdoor establishes a connection with a command and control (C2) server to send the victim’s machine profile, including user information, OS version, device details, IP address, MAC address, and supported implant features.
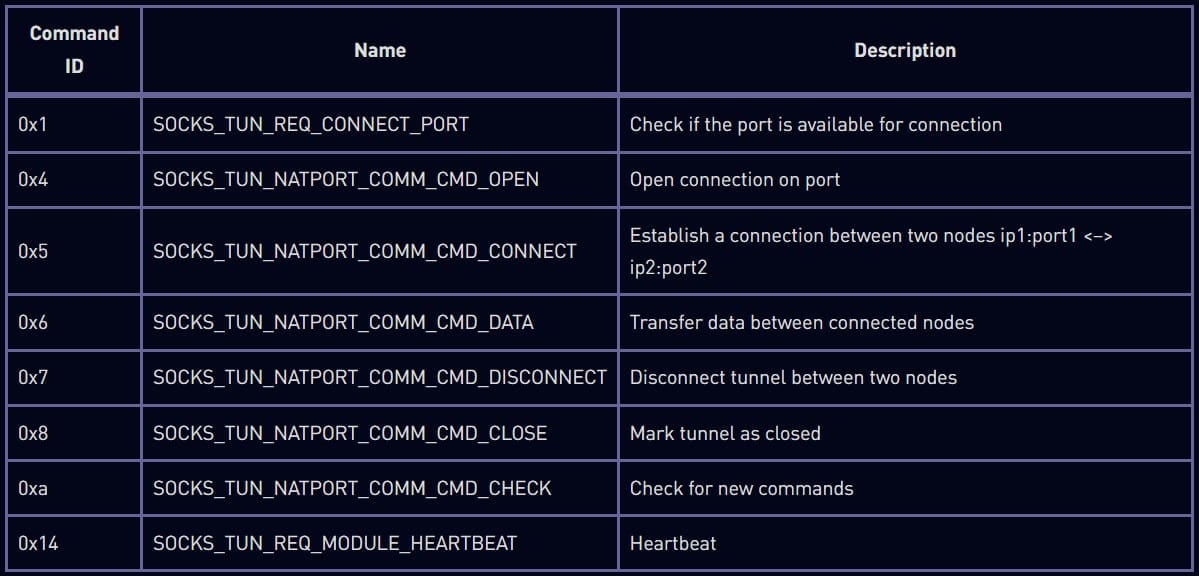 Supporting tunneling sub-commands (Check Point)
Supporting tunneling sub-commands (Check Point)
Trending: OSINT Tool: GooFuzz
The Horse Shell implant supports three main functionalities. First, it provides remote shell access to the compromised device, granting the threat actors full control. Second, it facilitates file transfer activities, enabling the uploading, downloading, manipulation, and enumeration of files. Lastly, it supports tunneling capabilities, allowing the obfuscation of network traffic origin and destination, effectively hiding the C2 server address.
The Horse Shell firmware implant is not limited to TP-Link routers and can potentially work in firmware images for routers from other vendors.
Targeting poorly secured routers has become a common tactic for state-sponsored hackers, who exploit them for DDoS attacks or crypto-mining operations. Routers are often overlooked when implementing security measures, making them a stealthy launching pad for attacks that obfuscate the attackers’ origins.
To mitigate the risks associated with these attacks, users are advised to apply the latest firmware updates for their router models, change the default admin password to a strong one, and disable remote access to the admin panel, restricting it to the local network only.
Recurring targets
The focus of state-sponsored threat actors on edge network devices has become increasingly evident. Previous instances have seen Chinese hackers targeting Fortinet VPN and SonicWall SMA routers with custom firmware implants. Recently, both the UK NCSC and US CISA cybersecurity agencies warned about Russian state-sponsored actors breaching Cisco routers to install custom malware.
As these devices often lack support for Endpoint Detection and Response (EDR) security solutions, they provide a gateway for threat actors to steal data, spread laterally, and conduct further attacks with minimal detection opportunities.
“It’s a recurring theme of continued China-nexus cyber espionage focus on network appliances, IoT devices, etc., that don’t support EDR solutions,” commented Mandiant CTO Charles Carmakal.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













