Charming Kitten APT Group Unleashes New NokNok Malware, Targeting macOS Systems

Security researchers have detected a new campaign attributed to the Charming Kitten APT group, in which hackers employed a new strain of malware called NokNok to target macOS systems. Unlike previous attacks by the group, this campaign utilized a different infection chain, using LNK files instead of the typical malicious Word documents.
Charming Kitten, also known as APT42 or Phosphorus, has been involved in at least 30 operations across 14 countries since 2015, according to Mandiant. Google has linked this threat actor to the Iranian state, specifically the Islamic Revolutionary Guard Corps (IRGC).
The recent campaign by Charming Kitten marks a shift away from macro-based infection methods using Word documents, now favoring the deployment of LNK files to deliver their payloads.
In this campaign, the hackers posed as U.S. nuclear experts and approached targets with offers to review drafts on foreign policy topics. They even created additional personas to enhance their legitimacy and establish rapport with the targets.
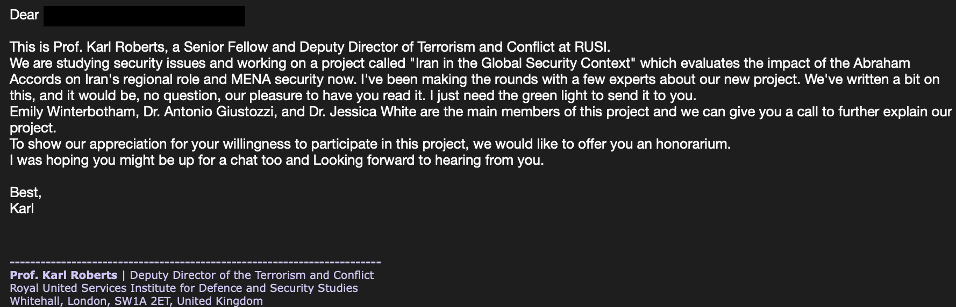 Email sampled from the latest Charming Kitten campaign (Proofpoint)
Email sampled from the latest Charming Kitten campaign (Proofpoint)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Windows Attacks
For attacks on Windows systems, Charming Kitten sends a malicious link containing a Google Script macro that redirects the victim to a Dropbox URL. The Dropbox source hosts a password-protected RAR archive containing a malware dropper that utilizes PowerShell code and an LNK file to stage the malware from a cloud hosting provider.
The final payload, known as GorjolEcho, is a backdoor that executes commands received from remote operators. To avoid suspicion, GorjolEcho opens a relevant PDF document related to previous discussions with the target.
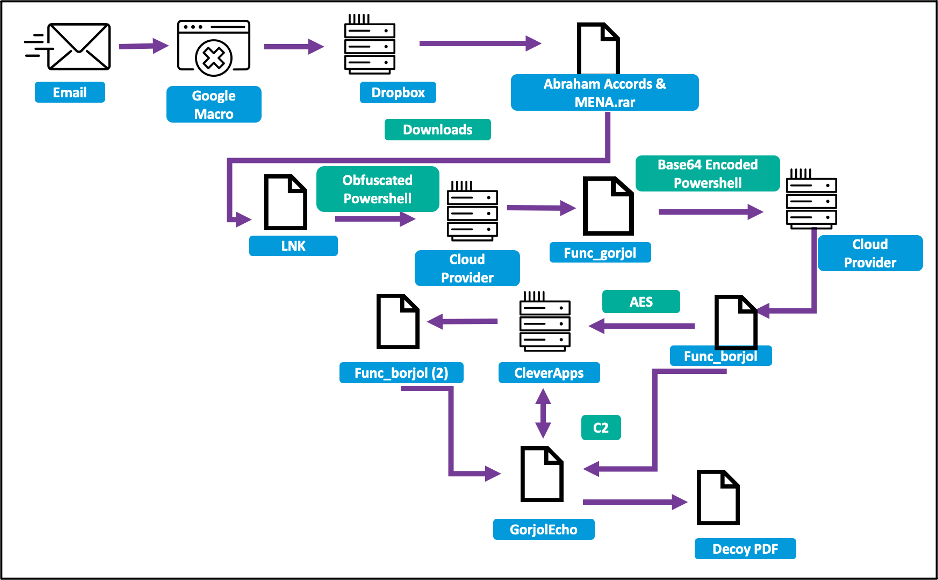 GorjolEcho infection chain (Proofpoint)
GorjolEcho infection chain (Proofpoint)
MacOS Attacks
In the case of macOS users, Charming Kitten employs a different approach. After realizing the target is using macOS, they send a link to a site hosting a ZIP file disguised as a RUSI (Royal United Services Institute) VPN app.
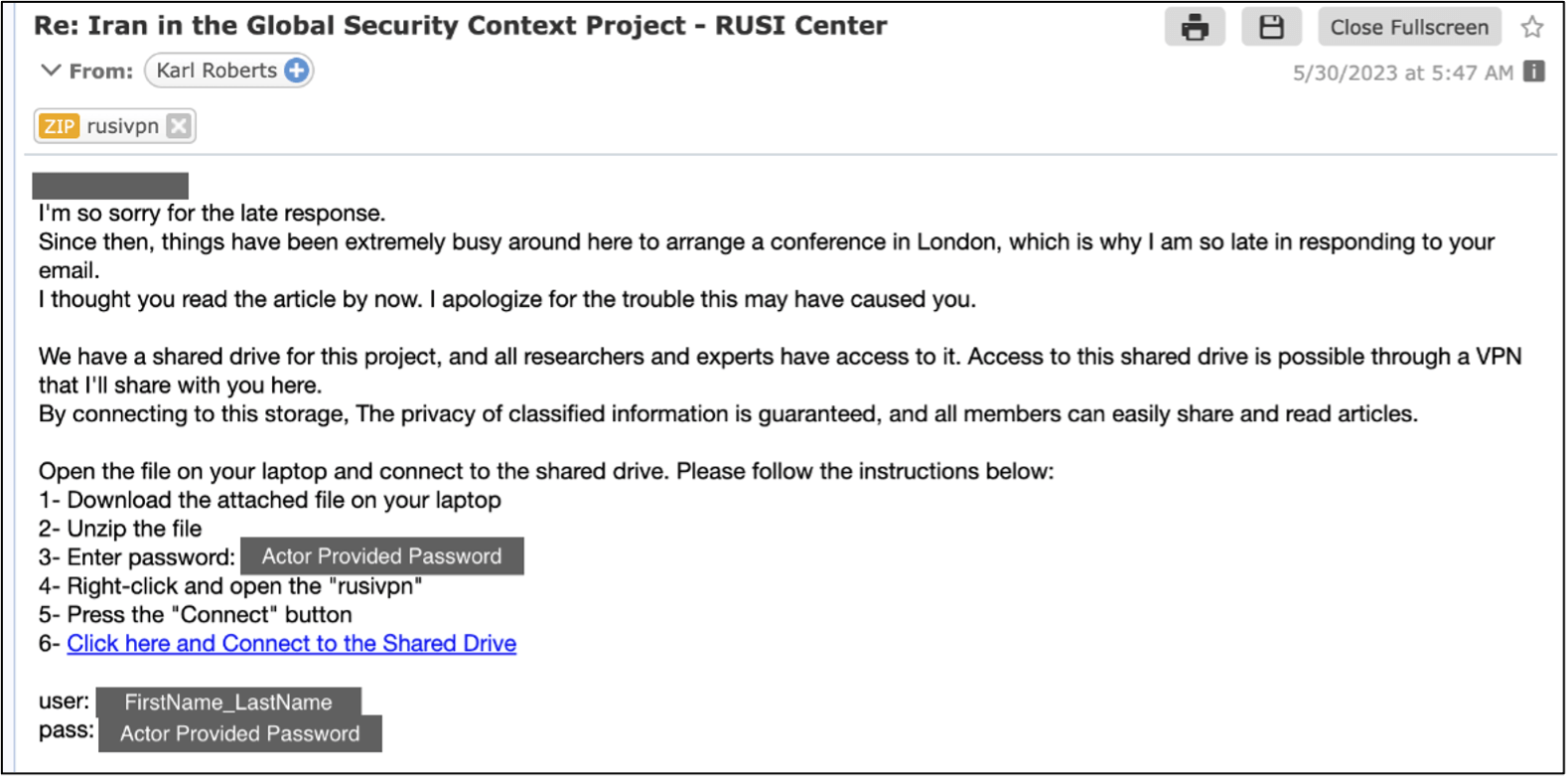
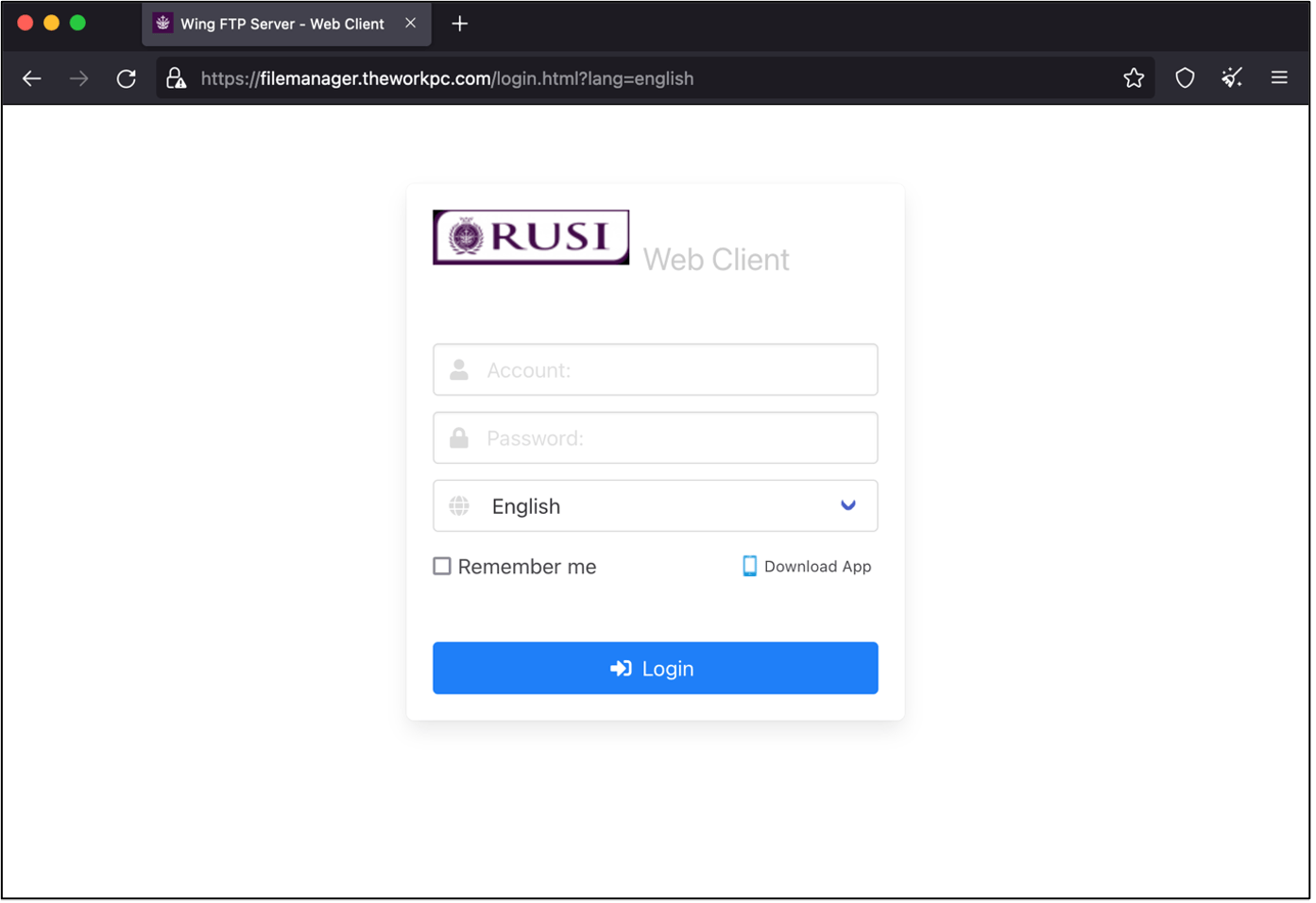
Upon executing the Apple script file within the archive, a curl command retrieves the NokNok payload, establishing a backdoor on the victim’s system.
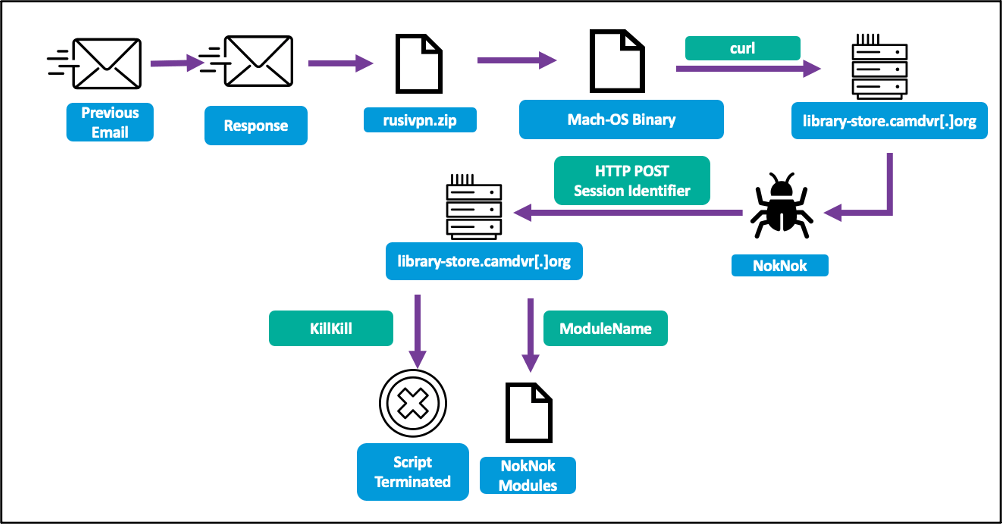 NokNok infection chain (Proofpoint)
NokNok infection chain (Proofpoint)
Trending: Recon Tool: Logsensor
NokNok collects system information, encrypts it, encodes it in base64 format, and exfiltrates it. It is suspected that NokNok may possess additional espionage-related functionality based on similarities to previously analyzed GhostEcho malware.
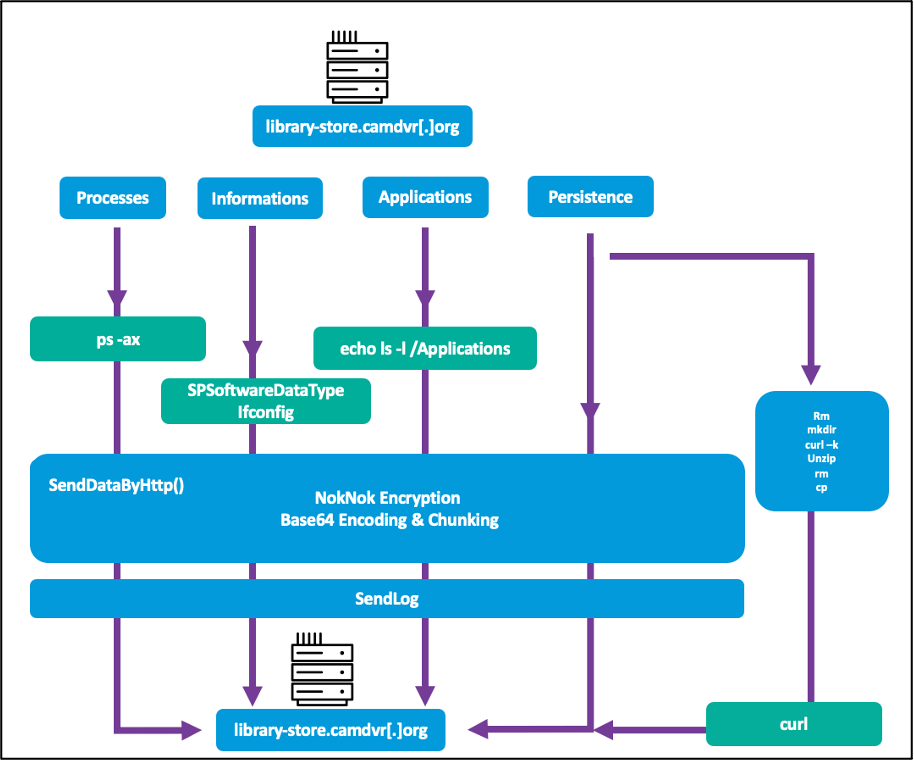 NokNok modules (Proofpoint)
NokNok modules (Proofpoint)
This campaign showcases Charming Kitten’s adaptability and capability to target macOS systems when necessary. It underscores the growing threat of sophisticated malware campaigns targeting macOS users and highlights the need for increased vigilance and security measures in defending against such attacks.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












