ChatGPT Vulnerability Exploited in Over 10,000 Attacks Within a Week

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
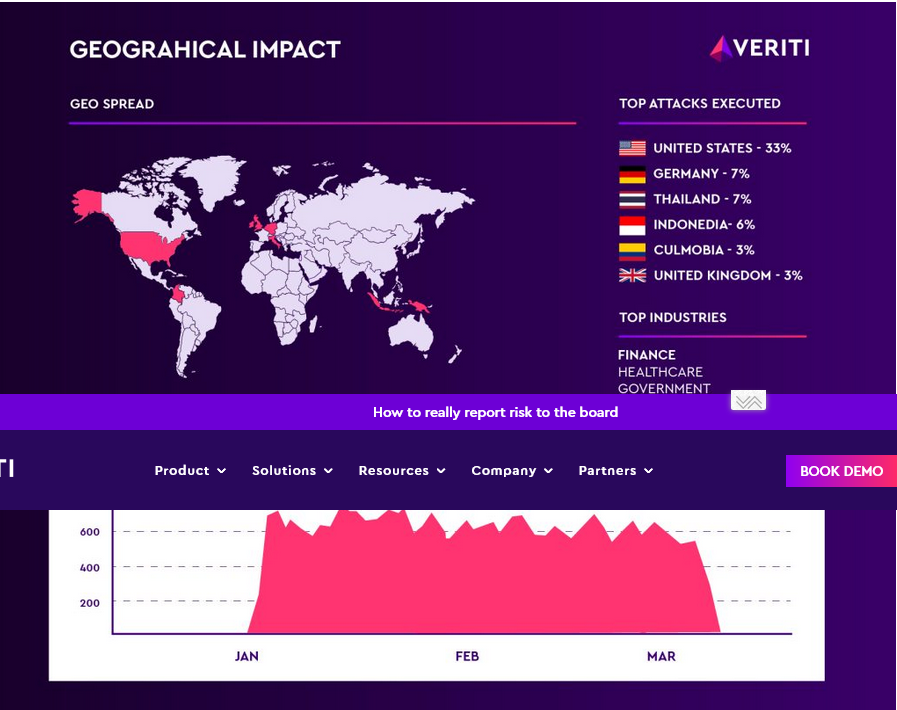
Global Attack Distribution
The attacks have a global reach, with the highest concentration of incidents recorded in:
- United States – 33%
- Germany – 7%
- Thailand – 7%
- Indonesia, Colombia, and the United Kingdom also affected
Veriti’s data also shows a surge in attack activity during January, followed by a gradual decline in February and March.
Financial Sector at High Risk
Banks and fintech companies are the primary targets due to their reliance on AI-driven services and API integrations. The potential consequences of these attacks include:
- Data breaches
- Unauthorized transactions
- Regulatory penalties
- Severe reputational damage
Cybersecurity experts stress that no vulnerability is too small to be ignored. Attackers will exploit any weakness they find, even those classified as medium-severity threats.
POC of the Attack
Trending: Major Cyber Attacks that shaped 2024
Why Medium-Severity Vulnerabilities Matter
Organizations typically focus on critical and high-severity vulnerabilities, but Veriti’s findings reinforce that attackers are opportunistic. What may seem like a low-priority issue can quickly become a favored attack vector if left unpatched.
Mitigation and Security Recommendations
To defend against CVE-2024-27564, Veriti recommends immediate action:
- Review and update security configurations for IPS, WAF, and firewalls.
- Monitor logs for attack attempts from known malicious IP addresses.
- Assess AI-related security gaps in risk management strategies.
Veriti has also identified IP addresses actively exploiting this flaw, providing crucial intelligence for security teams to enhance their defenses.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: hackread.com