Chinese Hackers Exploit Zero-Day in FortiClient VPN with ‘DeepData’ Toolkit

Chinese threat actor BrazenBamboo has been exploiting a previously undisclosed zero-day vulnerability in Fortinet’s FortiClient Windows VPN client using a modular post-exploitation toolkit named DeepData. This flaw enables the attackers to extract VPN credentials directly from memory after users authenticate.
Key Details of the Exploit
- Zero-Day Vulnerability: The zero-day, discovered by Volexity in mid-July 2024, allows attackers to dump usernames, passwords, and VPN server details from FortiClient’s memory. Despite being reported to Fortinet on July 18, 2024, no patch or CVE has been issued.
- Exploitation Method:
- The attackers utilize the DeepData toolkit, a sophisticated malware platform with plugins tailored for data theft.
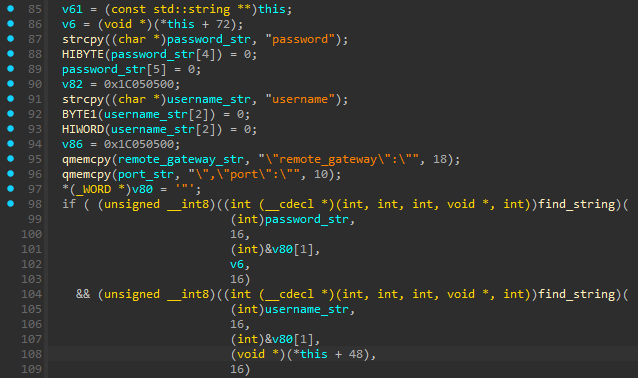
- The FortiClient plugin in DeepData identifies and decrypts sensitive JSON objects stored in memory, including credentials.
- Credentials are then exfiltrated to attacker-controlled servers using another malware called DeepPost.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Implications of the Attack
- Targeting VPN Credentials: By compromising VPN accounts, BrazenBamboo gains access to corporate networks, enabling lateral movement, access to sensitive systems, and espionage campaigns.
 Information in memory (orange) targeted by DeepData
Information in memory (orange) targeted by DeepData
Source: Volexity
- Memory Persistence: The flaw is tied to FortiClient’s failure to clear sensitive information from memory, even after authentication.
- Affected Versions: The vulnerability impacts recent versions of FortiClient, including v7.4.0, suggesting it is tied to recent software changes.
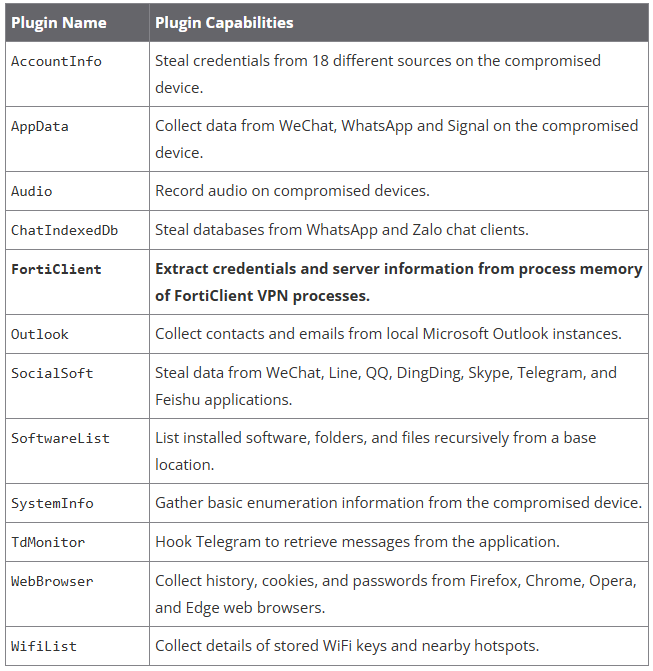
Plugins seen in the latest DeepData version Source: Volexity
BrazenBamboo Operations
- Threat Actor Profile: BrazenBamboo specializes in surveillance and espionage, targeting multiple platforms such as Windows, macOS, iOS, and Android.
- Malware Arsenal: In addition to DeepData, BrazenBamboo employs:
- LightSpy: Spyware for credential theft, keylogging, and communication monitoring.
- DeepPost: Used to exfiltrate data from compromised systems.
Trending: Offensive Security Tool: emp3r0r
Fortinet’s Response and Recommendations
- No Patch Yet: Fortinet acknowledged the issue on July 24, 2024, but has not released a fix. The company has also not assigned a CVE to the vulnerability.
- Mitigation Steps:
- Restrict VPN access to only trusted IPs.
- Monitor VPN activity for unusual or unauthorized logins.
- Apply endpoint monitoring to detect the presence of DeepData or related malware.
Indicators of Compromise (IoCs)
Volexity has published IoCs associated with this campaign to assist organizations in detecting potential threats.
Note: It is critical for organizations using FortiClient to implement these mitigations immediately while awaiting a security update from Fortinet.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













