Chinese Hacking Group Exploits VMware ESXi Vulnerability to Backdoor Windows and Linux VMs

VMware has released a patch to address a zero-day vulnerability in VMware ESXi that was exploited by a Chinese-sponsored hacking group. The group, known as UNC3886 and discovered by cybersecurity firm Mandiant, used the CVE-2023-20867 VMware Tools authentication bypass flaw to backdoor Windows and Linux virtual machines hosted on compromised ESXi hosts. Through privilege escalation to root, the attackers were able to deploy VirtualPita and VirtualPie backdoors on the guest VMs and exfiltrate data.
VMware has highlighted that a fully compromised ESXi host can manipulate VMware Tools to fail in authenticating host-to-guest operations, thereby impacting the confidentiality and integrity of the guest virtual machine. The attackers employed specially crafted vSphere Installation Bundles (VIBs) as a delivery method for installing the backdoor malware. VIBs are packages designed to assist administrators in creating and maintaining ESXi images
Mandiant’s investigation also identified a third malware variant, named VirtualGate, which acted as a memory-only dropper. This malware deobfuscated second-stage DLL payloads on the compromised VMs. The unique communication channel between the guest and host allowed for persistence, enabling the attacker to regain access to a backdoored ESXi host as long as a backdoor was deployed and initial access to any guest machine was gained.
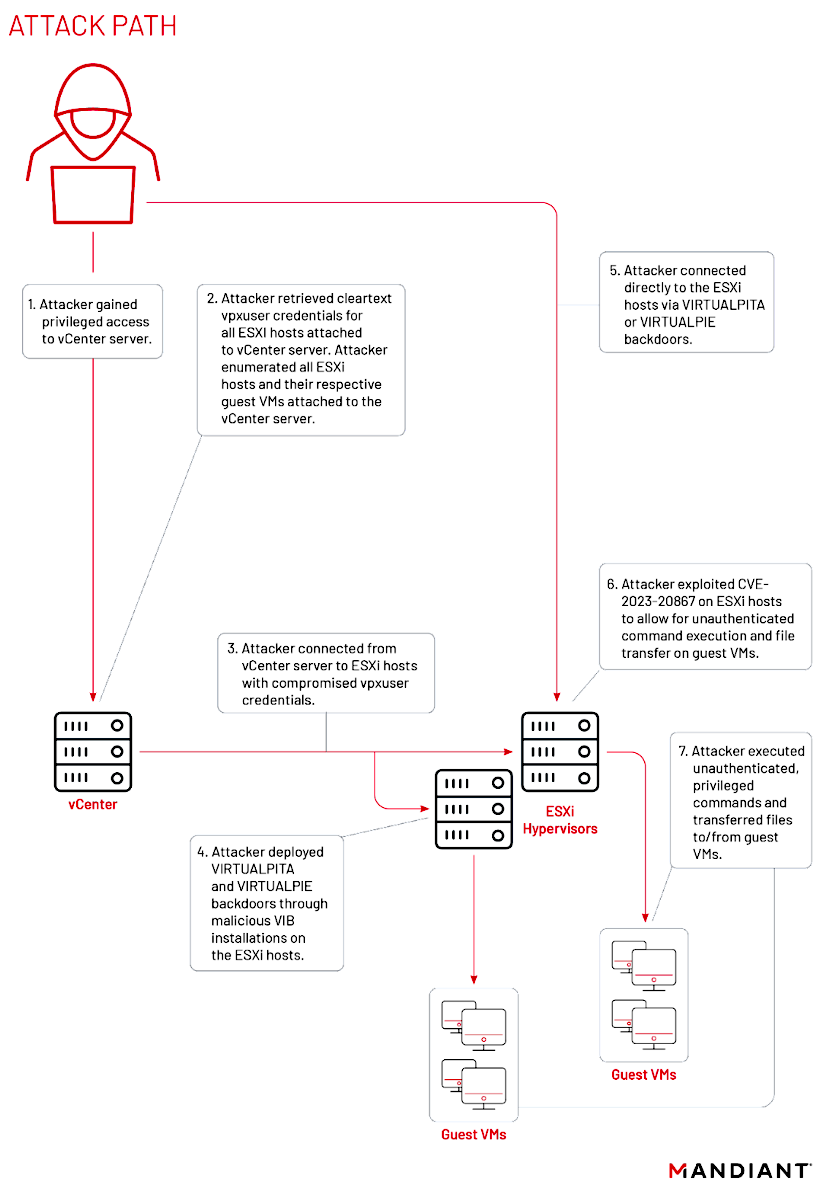 UNC3886 VMware zero-day attack (click to see full size)—Mandiant
UNC3886 VMware zero-day attack (click to see full size)—Mandiant
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
This recent attack adds to UNC3886’s history of targeting devices and platforms lacking Endpoint Detection and Response (EDR) solutions, exploiting zero-day vulnerabilities. In a previous campaign, the group used a different zero-day (CVE-2022-41328) to compromise FortiGate firewall devices and deploy Castletap and Thincrust backdoors. They leveraged their access to Fortinet devices to move laterally within the victims’ network and ultimately backdoor ESXi and vCenter machines using VirtualPita and VirtualPie malware.
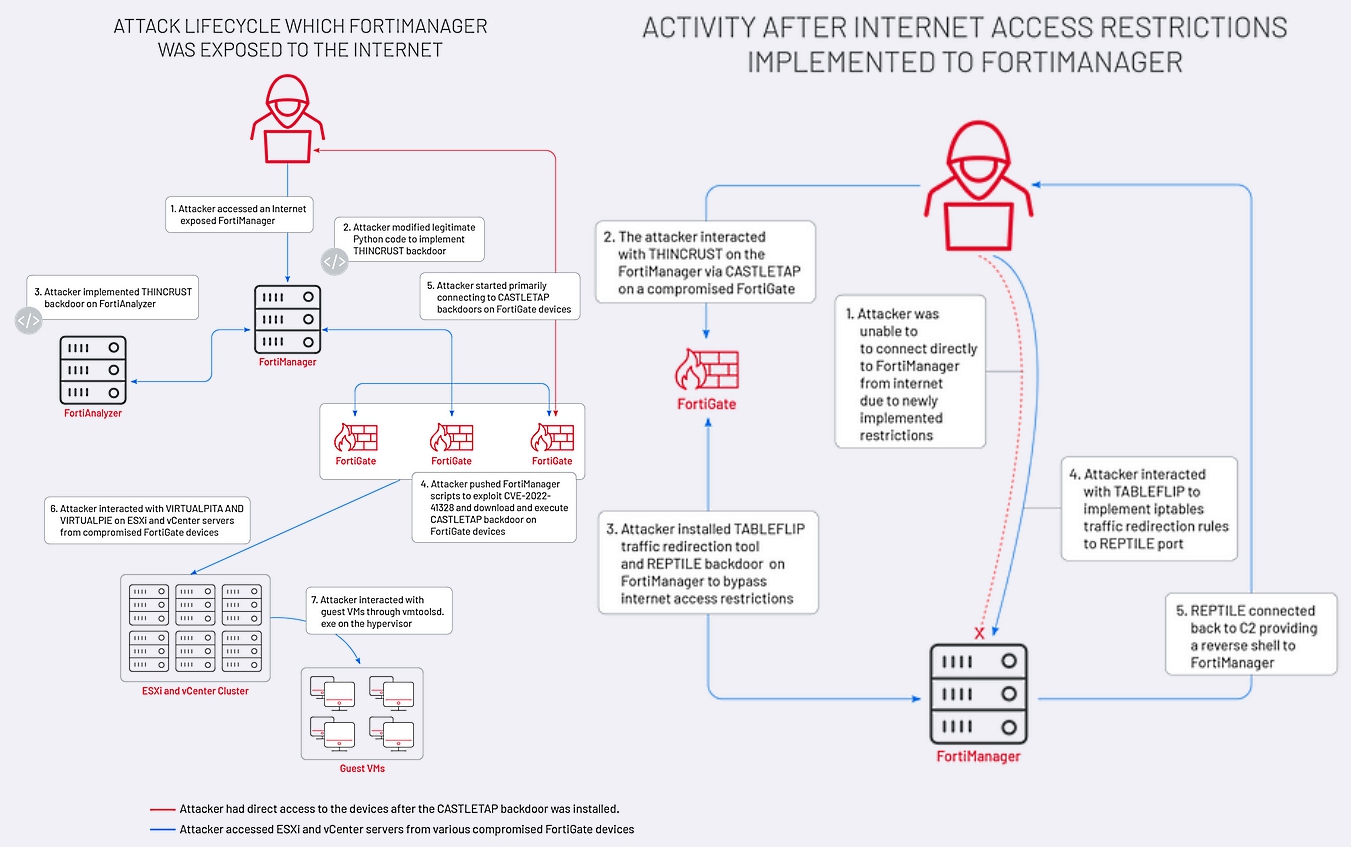
Fortimanager attack flow (click to see full size)—Mandiant
UNC3886 focuses its cyber-espionage efforts on defense, government, telecom, and technology organizations in the U.S. and APJ regions. Their proficiency in developing tailored malware and tools for specific platforms demonstrates their advanced capabilities and deep understanding of the complex technologies employed by the targeted appliances. Mandiant stressed the sophistication and difficulty in detecting this type of Chinese espionage, cautioning that there may be additional victims yet to discover the compromise.
Trending: Offensive Security Tool: Pypykatz
Charles Carmakal, CTO of Mandiant, commented on the cleverness and persistence of the Chinese hackers, stating that they have successfully compromised organizations with mature security programs in place, including those in the defense, technology, and telecommunications sectors.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












