Chrome Users at Risk: Zero-Day Vulnerability Exploited in Phishing Campaign

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Zero-Day Used to Deploy Malware in Operation ForumTroll
While Google has yet to disclose full details of the attacks, Kaspersky’s analysis revealed that CVE-2025-2783 was used in a sophisticated cyber-espionage campaign dubbed Operation ForumTroll.
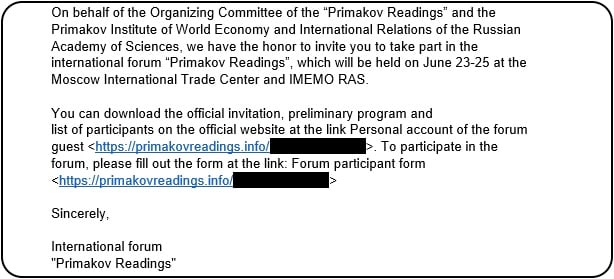 Operation ForumTroll phishing email (Kaspersky)
Operation ForumTroll phishing email (Kaspersky)
Attackers exploited the Chrome zero-day to bypass sandbox protections and infect victims with advanced malware. The campaign relied on phishing emails impersonating invitations from a Russian scientific and expert forum, Primakov Readings. These fraudulent emails targeted media outlets, educational institutions, and government organizations across Russia.
Victims who clicked on malicious links in these emails were redirected to the primakovreadings[.]info domain, where the exploit was triggered, allowing attackers to gain remote control of compromised systems.
Second Exploit Discovered in the Attack Chain
During their investigation, Kaspersky researchers also discovered that attackers used a second exploit in conjunction with the Chrome zero-day. While details of this additional exploit remain undisclosed, Kaspersky confirmed that patching Chrome will disable the entire exploit chain and prevent further infections.
“While research is still ongoing, judging by the functionality of the sophisticated malware used in the attack, the attackers’ goal was likely espionage,” Kaspersky said.
Trending: Major Cyber Attacks that shaped 2024
Trending: Offensive Security Tool: DS Viper
First Chrome Zero-Day of 2025 – More to Come?
CVE-2025-2783 marks the first Chrome zero-day patched in 2025. Last year, Google fixed 10 Chrome zero-days, many of which were either actively exploited in the wild or demonstrated at hacking contests like Pwn2Own.
With cyber-espionage groups continuously targeting Chrome vulnerabilities, users are strongly advised to keep their browsers up to date and remain cautious of phishing emails distributing exploits.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com